Burp Suite is an HTTP proxy, developed by PortSwigger (https://portswigger.net/). I think this HTTP proxy is more often used by security guys, despite being a private tool and not free; however, there is a free edition available too. The difference between the free and the private editions is the vulnerability scanner included in the private edition, which is great.
As Burp Suite is the basic tool for all bug bounty hunters focused on web applications, I will take more time explaining it.
Firstly, let's take a look at Burp's main screen:
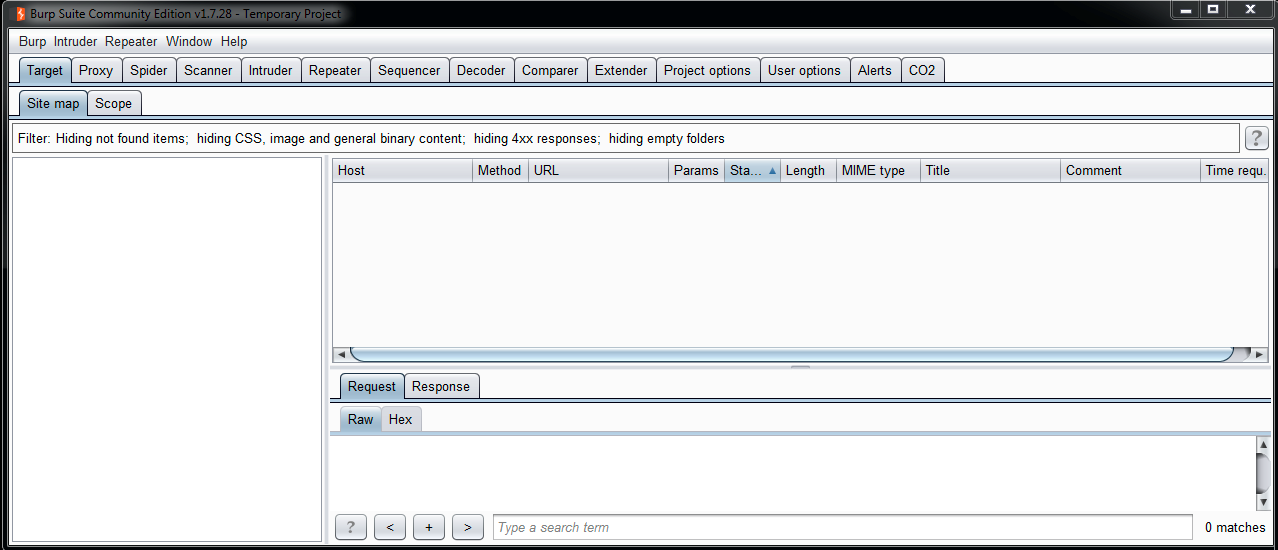
In my opinion, Burp's interface is a little confusing at first, because of the large number of options it has. Burp divides its capabilities into tools; and also let's you add new tools as plugins. You can see in the preceding screenshot that there are tabs; each tab is a tool consisting of configuration options.
Let me explain the basic use of Burp Suite. If you go to the Proxy tab, you will see something like the Paros screen:
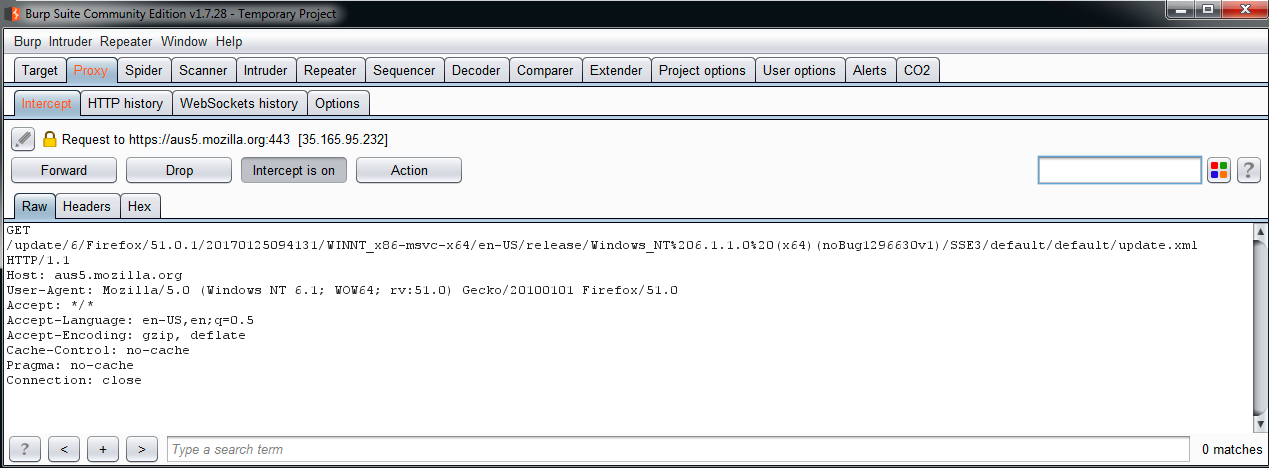
On this screen, we have four buttons (Forward, Drop, Intercept is on, and Action), to control the requests: send and receive. With these buttons, you can catch a request from your web browser, analyze the content, modify it, and send it to the application. These are the most basic options, but the most frequently used buttons in an HTTP proxy. All proxies and also some add-ons and plugins can do this, but have a look at the great things that make Burp Suite so amazing:
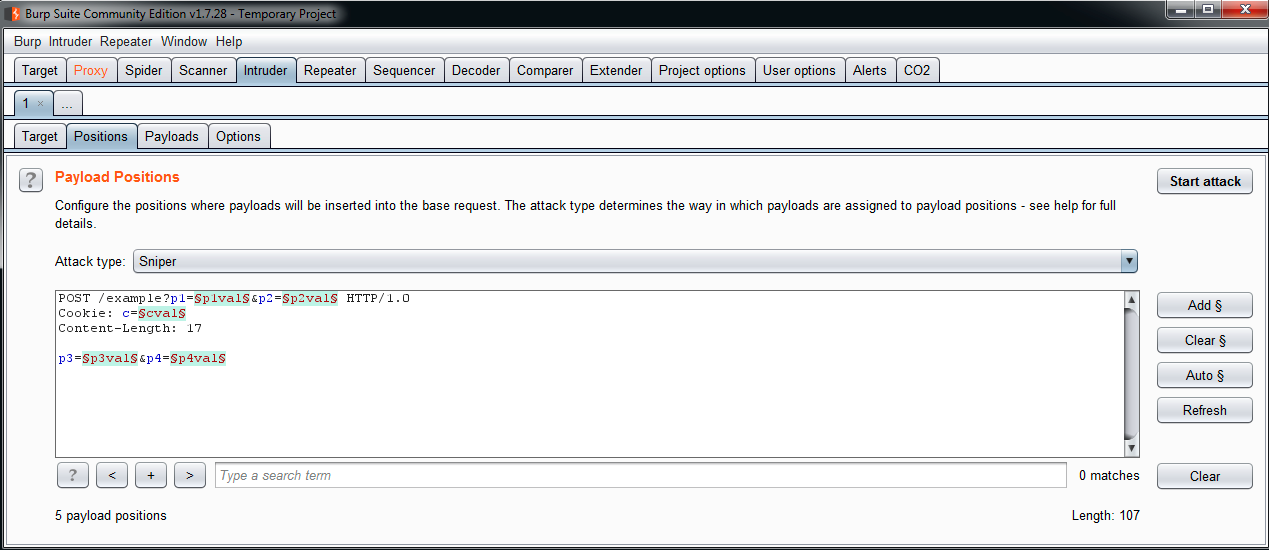
In the preceding screenshot, we can see the Intruder tab. This is a tool that automates the sending of modified requests. With this tool, it is possible to send a large number of requests with testing strings, lists of numbers, and real values. You can also choose how the tool inserts the different values and where. Then you can analyze the responses, looking for specific behaviors that could signal a vulnerability.
After you launch an Intruder attack, it is possible to see the results as HTTP responses, in a new window, as shown in the following screenshot:
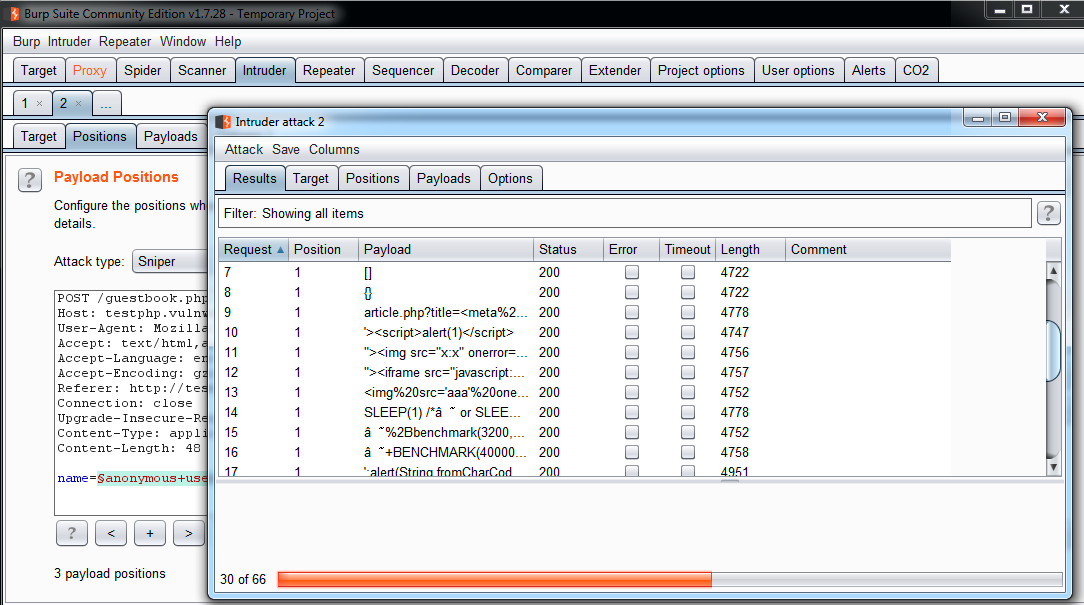
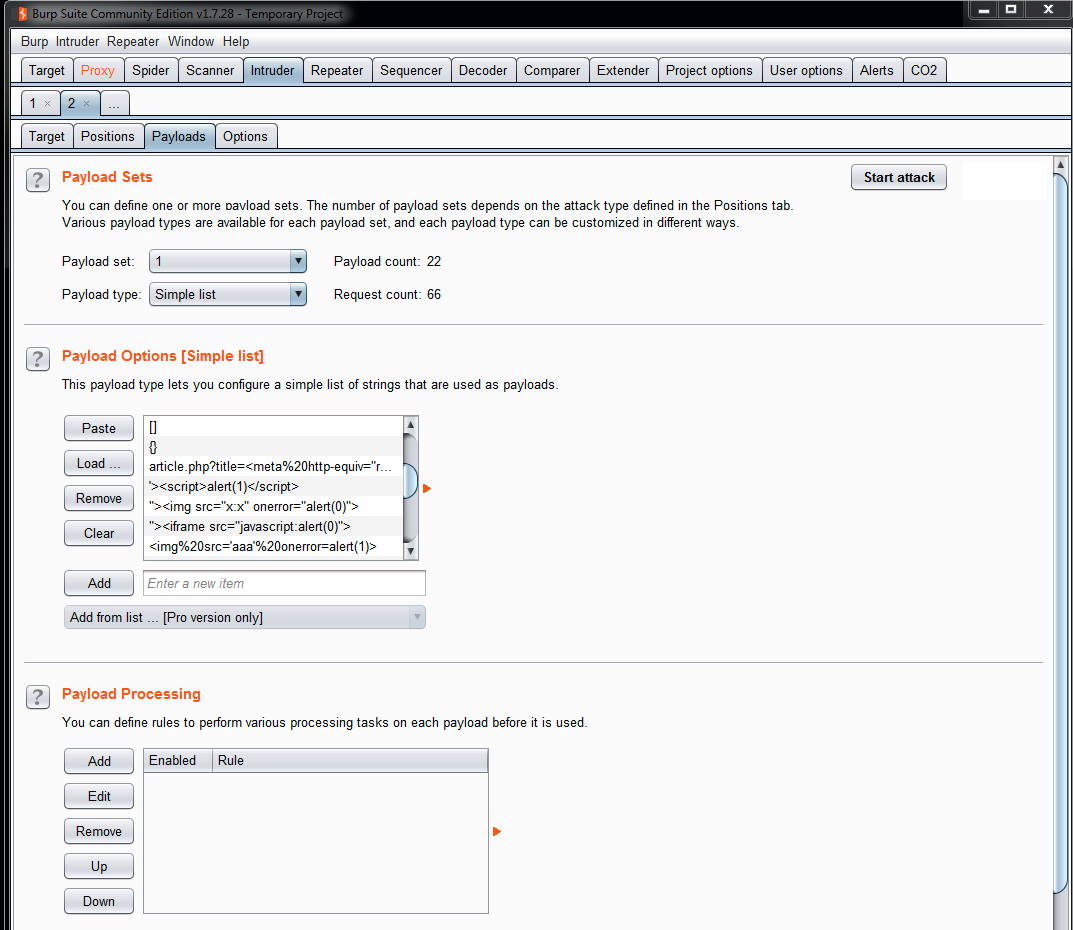
As a tip, it is recommended to create a list with all the different types of testing string to load in Intruder, as shown in the following screenshot:
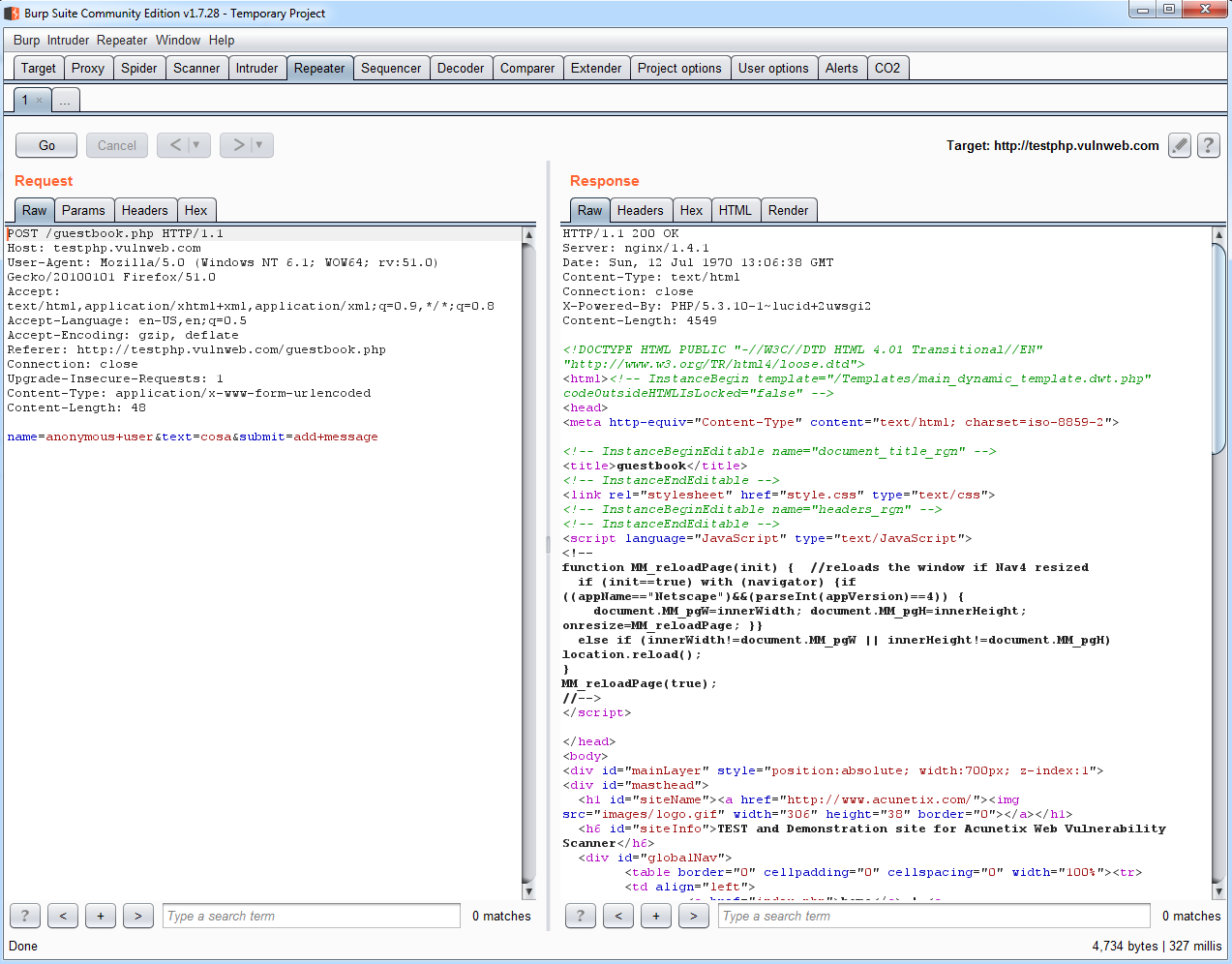
Burp Suite has a tool called Repeater, which can be useful when interacting with the application's backend, modifying a certain request, as shown in the following screenshot. In this screenshot, you can see two sections: Request, where you can see the original HTTP request, extracted from the history, and Response, where you can get a different result by modifying the request, without the need to catch a new request each time:
And finally, I want to mention the great capability to add plugins and extensions, as shown in the following screenshot:
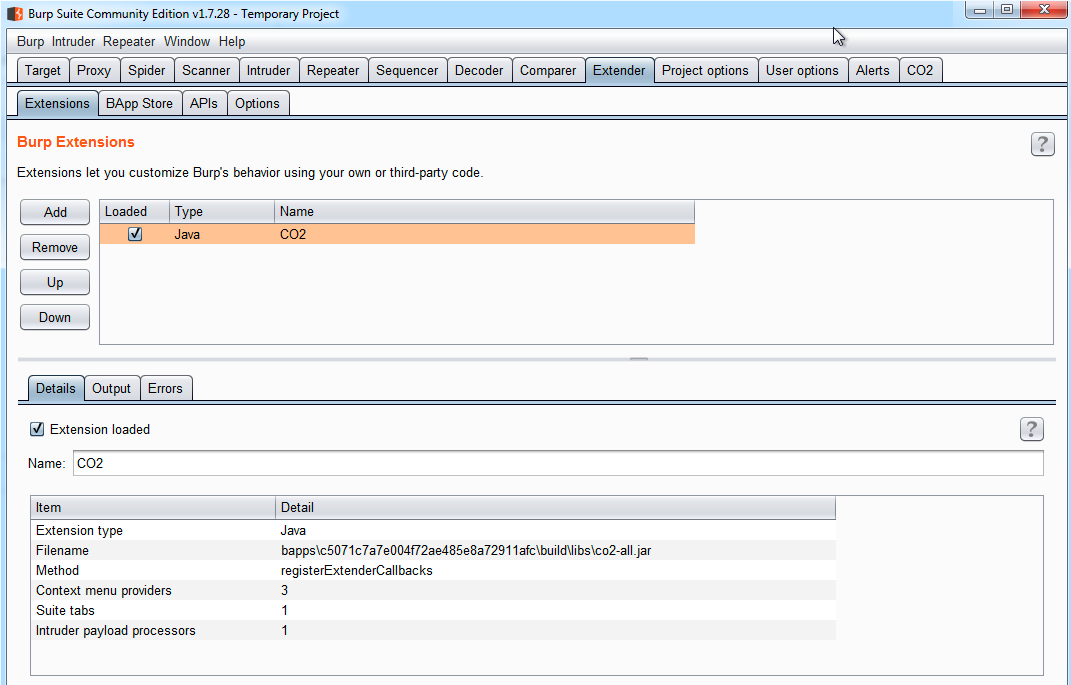
These extensions can be added just like a JAR file, which provides more capabilities to Burp Suite. Most of them are free. If you want to see a list of some of them, visit the following link: https://portswigger.net/bappstore.
