On April 11th, 2014, researchers from the Detectify security team reported a vulnerability in the Google search engine.
The reasons they selected the Google search engine to look for vulnerabilities were as follows:
- They thought Google is such a big platform that it might have old or deprecated software.
- It's a challenge to assess unknown and hardly accessible software.
- They had access to proprietary software that only some people can access.
- They had access to alpha and beta releases by Google.
So, they started to doing searches using Google Search:

Using searching techniques, they found some interesting systems and software. But they put their attention to the Google Toolbar button gallery. This was a personalized toolbar to manage Google buttons; the users could personalize it with new buttons or edit the existing ones. The Detectify team considered it a very good opportunity to find a vulnerability.
Reading the API documentation provided by Google, the team discovered XML entities in the toolbar. They saw that the title and descriptions fields were printed out, depending on the button search. So they determined it was a potential vector for an XXE vulnerability.
They uploaded an XML file to be parsed and found the vulnerability:

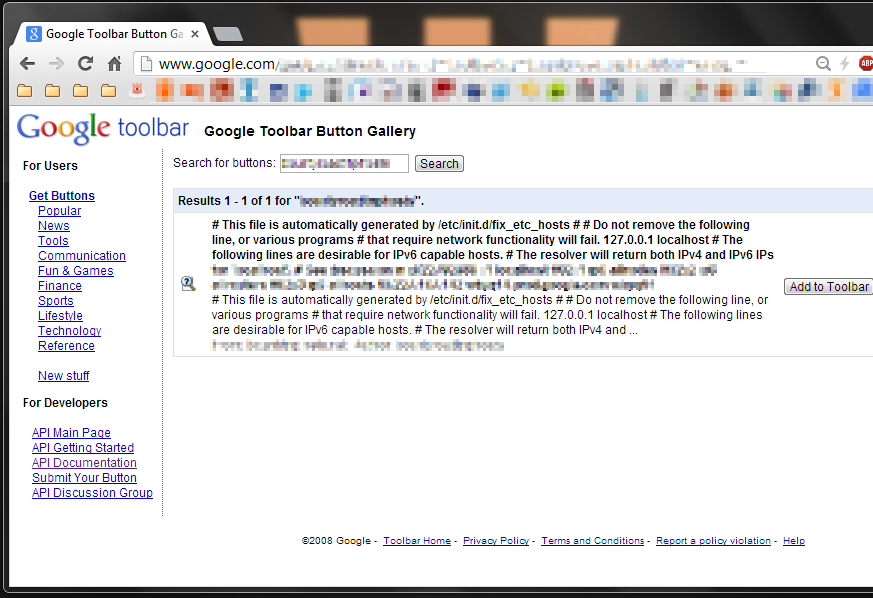
The file they uploaded extracted the /etc/passwd file from Google's server. This file contains the password hashes stored in the server. These hashes can be broken using cracking attacks such as brute force or rainbow table to get access to the servers.
The trick to find this kind of vulnerability is to be aware when actions in an application change something in the response to the user. In this case, when the user searched in the toolbar, two fields got changed; so, the team concluded it was the vector for a vulnerability.
If you want to read more about this bug, visit the following link: https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/.
