On September 12th, 2015, a bug bounty hunter called Mahmoud Gamal discovered a reflected XSS in Google image search.
He discovered that when a user opens an image in Google with the option Open in new tab, Google launched a link with a vulnerable parameter, imgurl. An example of the link generated by Google is the next line:
http://www.google.com.eg/imgres?imgurl=https://lh3.googleusercontent.com/-jb45vwjUS6Q/Um0zjoyU8oI/AAAAAAAAACw/qKwGgi6q07s/w426-h425/Skipper-LIKE-A-BOSS-XD-fans-of-pom-29858033-795-634.png&imgrefurl=https://plus.google.com/103620070950422848649&h=425&w=426&tbnid=ForZveNKPzwSQM:&docid=OEafHRc2DBa9eM&itg=1&ei=9ID8VZufMYqwUfSBhKgL&tbm=isch
Mahmoud Gamal injected the code directly into the imgurl parameter, like this:
http://www.google.com.eg/url?sa=i&source=imgres&cd=&ved=0CAYQjBwwAGoVChMIjsP-48OByAIVxNMUCh3pSQ98&url=javascript:alert(1)&psig=AFQjCNGcADmmDJe6-BWjcDAJ1pV84euDZw&ust=1442698210302078
As he explained in the report, the exploitation of the XSS was strange. When the string was injected, the XSS was not launched. But if the user pressed the tab, after a little period of time, the browser executed the XSS:
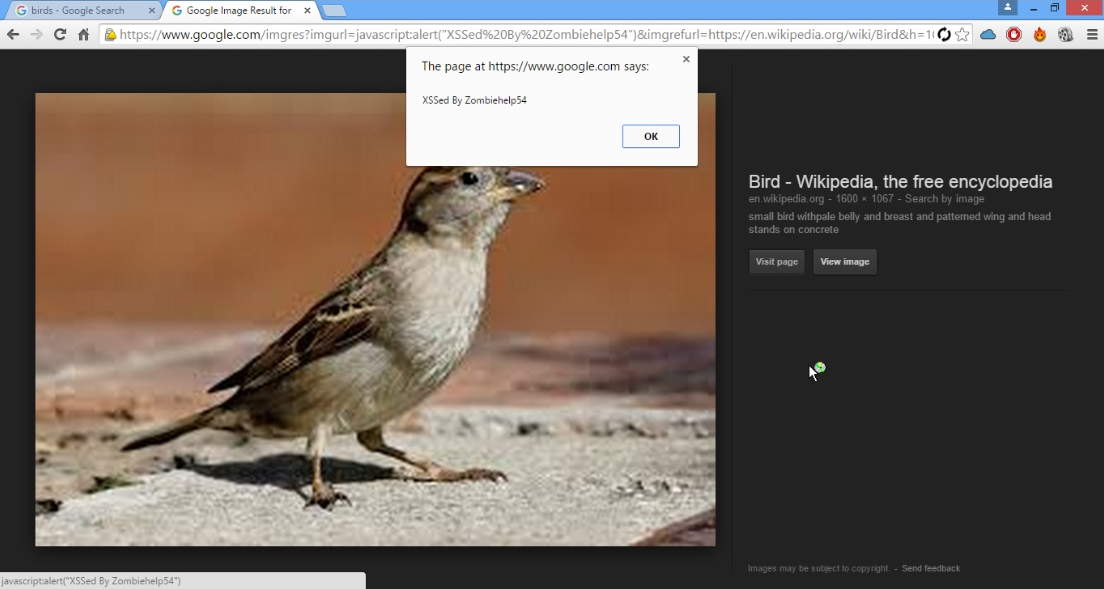
If you want to read the complete report, you can find the original post here: https://mahmoudsec.blogspot.com/2015/09/how-i-found-xss-vulnerability-in-google.html.
