SSTIs can appear in two different contexts:
- Plaintext context: It means that you can directly input HTML into the application, for example, in a text editor. Some examples of them are as follows:
smarty=Hello {user.name}
Hello user1
freemarker=Hello ${username}
Hello newuser
any=<b>Hello</b>
<b>Hello<b>
- Code context: This means that you enter values that are processed by the application and return a result. Some examples of them are as follows:
personal_greeting=username
Hello user01
personal_greeting=username<tag>
Hello
personal_greeting=username}}<tag>
Hello user01 <tag>
Usually these kind result in XSS attacks, due to the evaluated input, so, if you enter an alert() function, it will be shown.
Once you detect that there's SSTI, using an invalid input and getting a result, it's important to try to determine which template engine is used. Why? Because despite all of them working in similar ways, they have important differences that we need to keep in mind while exploiting the bug.
Depending on the input, it's possible to determine which is the template engine used. See the next diagram:
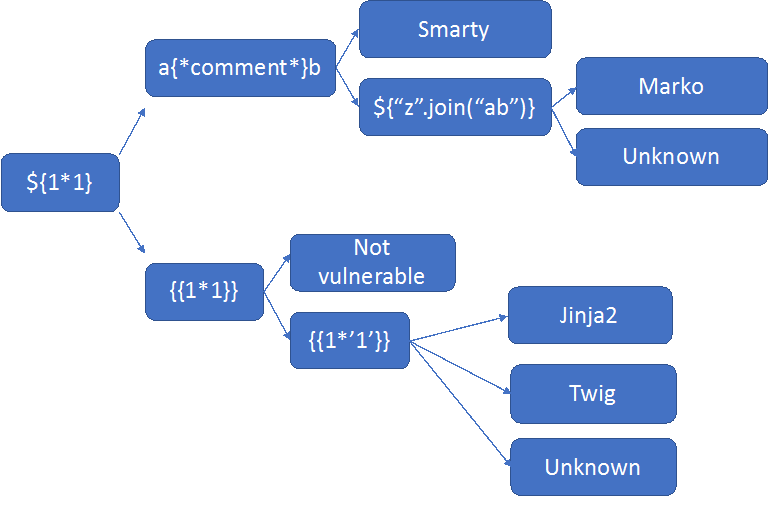
Based on the input and by following it, you can determine which is the engine used by the application in some cases.
