MODULE 3
The Basics of Security
In this module, we’ll introduce you to the fundamentals of security. These are the basics that every security person should be familiar with, particularly early in their career before progressing on to more advanced knowledge and studies. We’re going to cover a lot of definitions and concepts in this module to give you a solid look at the foundations of security. Most of the topics we discuss here will be discussed repeatedly throughout the book, as they relate to everything we do in security, including advanced tasks and functions, and security technologies.
A few decades ago, the primary security concern was protecting equipment, facilities, and people. To a large degree, this involved physical security, since computers were few and far between, and those few mainframes and computers that existed were housed in secure facilities. The only real concern was keeping unauthorized personnel out of those facilities and away from those machines, and keeping people safe.
Of course, all that has changed now, since the information and data processed on those machines are probably more valuable and important to an organization than the machines themselves. Protecting the equipment, facilities, and people are still equally as important, but with the widespread use of computing equipment and the mobile nature of devices these days, computer security has taken a new turn. Information and data are now easily accessible from anywhere, not simply from a secure facility in the middle of nowhere. This has changed computer security theory and practice significantly, adding new dimensions and considerations beyond mere physical security. There is now more focus on protecting data, regardless of physical boundaries, in addition to guarding facilities and machines.
In this module, we’ll cover some of the basic concepts of computer security theory. We’ll define and explain many different concepts that you need to know before you proceed with your Security+ studies. Each of these terms and concepts will be used widely throughout this book, and you’ll gain a basic understanding of many of them in this module, and a more in-depth understanding as you read through the rest of this book. We’ll start with the basic goals of computer security, as well as supporting elements and other important concepts.
The Goals of Security
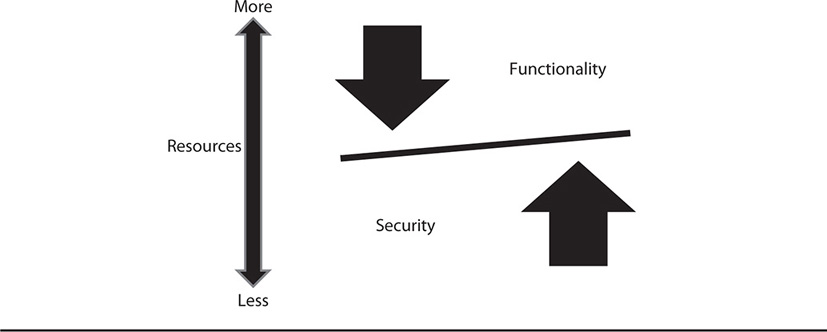
Traditional computer security theory has developed over the past several decades as we’ve learned more and more about the characteristics of information and data, the nature of attacks and defenses, and how all of these are balanced among three critical elements: functionality, security, and the resources available to ensure both. From a functionality standpoint, systems must function as we need them to, in order to process the data we need. We also want users and other systems to interface with our systems and data seamlessly, in a way that is easy to work with. However, allowing users to do whatever they wish with systems and data may result in loss, theft, or destruction of systems and data. That’s why we must add security into this equation.
From the security standpoint, however, increasing the levels of protection for systems and data usually reduces functionality, because we introduce security mechanisms and procedures into the mix that don’t always allow users to “see” or interact with data and systems the way they would like. This usually means a reduction in functionality to some degree. Finally, the resources that we must expend toward functionality, security, and the balance between them are finite. No one has all the money or resources they’ll ever need or have as much functionality or security as they’d really like. So keep in mind that the relationship between functionality and security is inversely proportional; that is to say, the more security we have, the less functionality, and vice versa. Also, the fewer resources we have, the less of either functionality or security we can afford. Figure 3-1 illustrates this careful balancing act among the three elements of functionality, security, and resources.
Figure 3-1 Balancing functionality, security, and resources
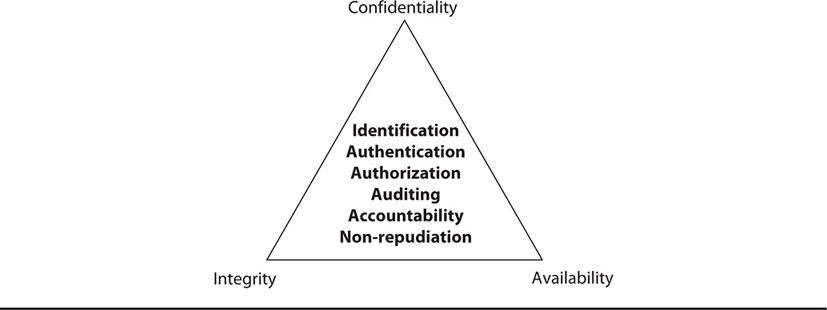
Over time, security theory has produced three “goals” of information security that are widely considered the foundations of our trade: confidentiality, integrity, and availability. These goals are what we as security professionals want to see from our overall security program, our technologies, and all of our security efforts. We want to see these three goals met for all of our data and the systems that process it.
We often refer to these three goals of security as the “CIA triad.” In some texts, you will also see the “AIC triad.” Figure 3-2 illustrates the three goals of confidentiality, integrity, and availability.
Figure 3-2 The CIA (or AIC) triad
![]()
The CIA triad is put into practice through various security mechanisms and controls. Understand that every security technique, practice, and mechanism we put into place to protect systems and data relates in some fashion to ensuring confidentiality, integrity, and availability.
Confidentiality
Confidentiality is the goal we are trying to meet by keeping systems and data from being accessed, seen, read, or otherwise interacted with by anyone who is not authorized to do so. Confidentiality is a characteristic that we meet by keeping data secret from people who aren’t allowed to have it or interact with it in any way, while making sure that only those people who do have the right to access it are able to do so. Confidentiality is met through various means, including the use of permissions to data, encryption, and so on.
Integrity
To meet the goal of integrity, we want to ensure that data and systems are maintained in a pristine, unaltered state when they are stored, transmitted, processed, and received, unless the alteration is intended due to normal processing. In other words, we want no unauthorized modification, alteration, creation, or deletion of data. Any changes to data must be done only as part of authorized transformations in normal use and processing. Integrity can be maintained by the use of a variety of checks and other mechanisms, including data checksums, comparison with known or computed data values, and cryptographic means. We’ll discuss these means as we progress through the book.
Availability
To maintain availability, we must ensure that systems and data are available for authorized users to perform authorized tasks, whenever they need them. Availability is really one of the key bridges between security and functionality, because it ensures that users have a secure, functional system at their immediate disposal. An extremely secure system that is not really functional is an availability issue at its core. Availability is ensured in various ways, including system redundancy, data backups, business continuity, and other means.
Other Elements of Security
Beyond the three goals of security are several other elements that directly support these goals. These elements interact with one another and the CIA goals to achieve an integrated approach to securing people, data, and equipment. These elements are not tied solely to any one of the three goals; they support each of them to varying degrees. Some tend to support confidentiality more so than integrity or availability, for example, but all of them support all three in some way. These elements are discussed in the following sections.
Identification
Before a person or an entity (system or process) can access the system, they must identify themselves to the system. Most of us are accustomed to presenting user credentials, such as typing a username and password combination or inserting a smart card, to the system before we log in. Presenting user credentials is known as identification, and this is the first step in the authentication process. At this step, the user has asserted that they are who they say they are. Identification is a necessary first step in accessing not only systems, but also data and facilities. The next step is authentication.
Authentication
Authentication is the next step in the process of gaining access to a system or facility. Once you’ve identified yourself by presenting valid credentials, these credentials must be validated. In other words, there must be a system in place to examine the credentials you’ve presented, confirm that they are valid credentials, and verify that they represent the user who is requesting access. Authentication is the validation of those credentials. Without authentication, a user could present any credentials, even a false driver’s license or access card, for example. Authentication is often performed by looking up credentials in a user database, or an access list.
Authorization
Authorization is the next step. Even if you have been confirmed as a valid user through the identification and authentication process, you won’t necessarily have free rein in the system or in the building. Authorization is the process of granting a user or entity the appropriate permissions, rights, and privileges to the system. Even valid users may not have authorization to access particular systems or data or enter into restricted areas. In some cases, authorization may occur at the time a user is validated through authentication. A user’s access rights may be attached to a token and passed on to the system when they are initially authenticated. In other instances, a user’s access rights for a particular system or data only be passed on to the system at the time they attempt to access it. The system may look up the user’s access permissions or rights in a table or database at that time. In either case, authorization to access the system must have been previously granted and configured before the user attempts access.
Auditing and Accountability
Even when users are authenticated to the system and have certain permissions to perform specified actions with systems or data, they may sometimes attempt, intentionally or accidentally, to perform actions they are not authorized to perform. Additionally, sometimes users who are not authorized to interact with the system attempt to do so. In these cases, security administrators want to know when these instances occur, since it can point to potential attempts to unauthorized access data or systems, which may result in data loss or theft. Any unauthorized access would violate the goal of confidentiality, of course, and may also result in unauthorized modification to data. Security personnel are made aware of unauthorized access attempts through auditing. Auditing is implemented by recording the actions of users or other entities when they interact with systems or data. We’ll cover auditing much more in depth in later modules, but for now you should know that auditing is a way of preventing data loss or modification, as well as detecting when it has occurred.
Accountability, on the other hand, is the process of holding users accountable for their actions. Accountability serves two important functions. First, it can deter otherwise honest users from committing security policy violations, if they know that their actions are being audited and monitored. It is also used to punish or sanction users who attempt to or successfully violate security policies. Auditing and accountability often go hand-in-hand, as it is difficult to maintain accountability for actions in the system without auditing mechanisms in place.
Non-repudiation
Non-repudiation means that users cannot deny that they have performed an action with regard to the system or data. Non-repudiation is a function of auditing and accountability, since it allows security administrators not only to detect when unauthorized actions have occurred, but to trace those actions conclusively to an individual. If an individual has been positively identified and authenticated, and they perform an action they are not authorized to perform, and then auditing detects this action, they cannot deny that they performed it. Non-repudiation is also used in communications, particularly e-mail, to ensure that a user cannot deny that they sent a particular message. Figure 3-3 illustrates how the all of these elements support the three security goals.
Figure 3-3 The supporting elements of security
![]()
Understand the definitions of the supporting elements of security and how they support all three of the security goals.
Security Concepts
Now that we’ve covered the three security goals and some of their supporting elements, we should introduce you to several other concepts that will help us progress to more advanced topics. Some of these will be covered lightly in this module, with more in-depth coverage later in the book. The following definitions and basic concepts will give you the necessary foundation for understanding more complex concepts that you’ll learn later.
Controls
A control is a security mechanism that is implemented either to increase security or to make up for a shortfall in security. Controls can be technical solutions, such as firewalls, but they can also be processes, procedures, policies, or physical controls. Let’s say, for example, that anyone can walk up to the entrance of a supposedly secure facility. That means that there is a shortfall in physical security that should be remedied by constructing a secure fence around the building. The fence would be considered a physical control. Likewise, a lack of appropriate access permissions to a file or folder could be a security issue that may be corrected by assigning restrictive permissions to that data. Security controls can not only make up for shortfalls, but they can serve to strengthen security even when other controls are already in place.
In security theory, we normally categorize controls into three broad areas: administrative controls (also known as managerial controls), technical controls (also known as logical controls), and physical controls (also known as operational controls). Administrative controls are normally applied through policy, procedures, and so on. For example, a policy on proper care and use of computer systems would be considered an administrative control. Technical controls are what we normally think of in terms of technical security measures, such as firewalls, file and folder permissions, encryption, and so on. Physical or operational controls are implemented to address physical security issues, which could include controls that are implemented through the proper practice of processes and procedures. For example, the correct procedure for performing a backup of system data while ensuring availability would be considered an operational control.
You’ll find that it can be difficult to distinguish among the different categories of controls. For instance, a firewall is considered a technical control, but there’s also usually a related written policy involved that dictates how the firewall will be configured and which network traffic should be allowed or blocked, and this policy would be considered an administrative control. We will discuss these different types of controls, along with some more detailed descriptions and examples, in Module 32.
In addition to categorizing controls as administrative, technical, or physical, we can also categorize controls from a functional perspective as preventive, deterrent, detective, corrective, compensating, and recovery. We will discuss more about these functional categories in Module 32, but for now, some examples of detective controls include facility alarms or network intrusion detection systems, as well as system auditing. Preventive controls include security fences, guards, and firewalls. Corrective controls could be controls that are put into place to correct a weakness in an existing control.
![]()
Understand the three categorizations of controls: administrative (managerial), technical (logical), and physical (operational).
Defense-in-Depth
Many uninformed people think that one or two security mechanisms, such as a firewall, for instance, are all that is needed to be secure. What would happen, however, if a hacker successfully attacked the firewall and was able to get past it? How would your data and systems be secure then? That’s where the concept of defense-in-depth comes in. You may also hear this referred to as layered defense or security.
This security technique relies on multiple levels of defense within your network and host environments, rather than relying on only one or two security mechanisms to protect the environment. For instance, having a firewall is certainly an advisable thing to do, but you also want to add other mechanisms and controls to protect your systems and data at other points in the environment. You would want to encrypt data from your hosts to the Internet and back, for example. You may also want to use strong identification and authentication mechanisms, in case someone infiltrates your firewall. Additionally, firewalls aren’t really designed to combat computer viruses and other malicious software, so you would need to add an antivirus solution to account for those issues. The key to defense-in-depth is that you don’t rely on one single security control; you have several controls in place at different levels and points to ensure that if one control were circumvented or disabled, the other controls would still prevent unauthorized access, damage to systems, or loss of data.
Data Sensitivity and Classification
You might be wondering, how much security is enough? How many security layers and mechanisms do you need for your network, computer systems, and data? Well, the answer to those questions might seem simple, in that you need only as much as it takes to protect your systems and data adequately. However, this statement is deceptive, because you probably have different types of data or systems to which you want to apply different levels of protection. If you protected everything to the most restrictive, highest levels you possibly could, it would be quite expensive, and you would likely lose some functionality in the process. You’d also wind up protecting some data at much higher levels than is necessary. Think about that: You could spend more money to protect the data than the data is actually worth. That’s not necessarily a smart way to apply security, since you have to balance security with functionality and resources available. You want to spend money on controls and protections for only the most important data in your network. So how would you decide what’s important and what’s not? That’s where data sensitivity and classification comes in.
Data sensitivity relates to the importance, criticality, and sensitivity of the data stored on your systems. For example, company proprietary data such as trade secrets, formulas, and manufacturing processes would be considered very sensitive. You wouldn’t want just anyone to have access to that data, and you would want to keep it within the confines of your organization. You would not want that data released to the world for a competitor to steal and use to compete against you in the market. On the other end of the spectrum is data that’s not critical or sensitive, such as the season statistics of the company baseball team. Obviously these examples represent two different levels of sensitivity. It’s not very effective to declare arbitrarily that some data is sensitive and some is not; instead, you should carefully think about it, decide upon different levels of sensitivity or data classification, and put this in writing so that everyone can apply data sensitivity rules consistently across the organization. One advantage to creating such data classification is that you create a standardized way of determining what data is sensitive and requires protection and what data is not sensitive and does not need to be protected. That way, you can spend your money and resources on protecting the data that means more to you.
Different organizations use a variety of data sensitivity levels and classifications. For instance, the federal government typically uses three main levels of data classification: Top Secret, Secret, and Confidential. What distinguishes these data sensitivity classifications from one another is the amount of damage that would be inflicted if data from these different levels were to be inadvertently disclosed to unauthorized persons. For example, disclosing Top Secret data such as military secrets to unauthorized persons could result in exceptionally grave damage to national security. Confidential data, on the other hand might cause only minor damage to national security if it were disclosed. So not only do you need to determine the different data sensitivity classification levels for your organization, you also have to determine the basis on which you assign those different levels to data and systems.
Typical data sensitivity levels often found in companies or private organizations include company sensitive, proprietary, for public release, privacy data, and so on. These describe the different sensitivity levels, and, of course, the levels of protection they require. We’ll discuss policy and governance in Module 4, but for now you should know that data sensitivity and classification should definitely be part of your organization’s written policies.
Principle of Least Privilege
Another cornerstone of information security is the principle of least privilege, which states that all users, whether they be worker bees or senior executives, should be granted only the level of privileges they need to do their jobs, and no more. For instance, a normal user in the accounting department really has no business having administrator privileges over the network. They don’t need those privileges to do their job and could either inadvertently or intentionally cause damage to the network or data by misusing these privileges.
Closely related to principle of least privilege is need-to-know. Need-to-know means that users should get access only to data and systems that they need to do their job, and no other. For example, managers and supervisors might need access to salary data for their own direct reporting employees, but no others. A midlevel manager doesn’t need access to salary data for the company president, of course. And she probably doesn’t need access to salary data for employees who report to other managers. The same is true throughout the organization: accountants don’t need access to engineering data, engineers don’t need access to human resources data, and regular employees don’t necessarily need access to sensitive financial data. We’ll discuss the principle of least privilege throughout this book; it is related to many of the advanced concepts that you’ll learn as we go.
Separation of Duties
Separation of duties would be considered an administrative control, because it’s related to policy. In the separation of duties concept, a single individual should not perform all critical or privileged level duties. These types of important duties must be separated or divided among several individuals. Separation of duties ensures that no single individual can perform sufficiently critical or privileged actions that could seriously damage a system, operation, or the organization. These critical or privileged actions can be split among two or more people, requiring some level of checks and balances. For example, security auditors are responsible for reviewing security logs but should not necessarily have administrative rights over systems. Likewise, a security administrator should not have the ability to review or alter logs, because he could perform unauthorized actions and then delete any trace of them from the logs. Two separate individuals are required to perform such activities to ensure verifiability and traceability. Closely related to the concept of separation of duties is the technique of using multi-person control to perform some tasks or functions.
Multi-person Control
Multi-person control means that more than one person is required to accomplish a specific task or function. We might implement multi-person controls to ensure that one person, by herself, could not initiate an action that would cause detrimental consequences for the organization, resulting in loss of data, destruction of systems, or theft. We do this by dividing up critical tasks to require more than one person to accomplish them. For example, in a banking environment, one person may be authorized to sign negotiable instruments, such as checks, for up to $10,000. Beyond the limit of $10,000, two signatures are required for the transaction to be processed. This would help prevent one malicious person from stealing more than $10,000. Although it’s conceivable that two people could conspire to use their assigned abilities to commit an unauthorized act, fraud in this case, separation of duties and multi-person control makes this more difficult. In this case, counter-signing a check is a multi-person control. In an information security environment, multi-person control could be used to access sensitive documents, recover passwords or encryption keys, and so on.
Mandatory Vacations
A mandatory vacation is a concept that few organizations actually implement to its fullest. This concept involves requiring individuals to take vacations at various times of the year, so that another individual can fulfill the vacationers’ responsibilities and their duties can be audited. This administrative control is used to detect fraud or unauthorized activity; if individuals who are perpetrating fraud are never away from their work center, it can be difficult to audit what they are doing. Again, most organizations probably don’t implement this concept fully, simply because it requires that people be cross-trained on others’ duties to the extent that someone can immediately take over a critical position when another person is absent. Additionally, most organizations rarely audit individual positions unless there is a reason to suspect unauthorized actions by the individual; instead, they perform auditing across all systems on a continual basis to detect anomalies.
Job Rotation
Job rotation is an interesting concept, because it involves periodically switching people around to work in different positions. This practice enables different people to become proficient in a variety of positions, so that the organization doesn’t have to depend solely on one person to perform certain critical functions or tasks. If something were to happen to an individual occupying a critical position, another person could step in to do the job. When people become too comfortable with a job, they might believe that they can get away with performing actions they are not authorized to perform. Rotating people into different positions increases the potential to detect fraud or misuse in that position and can discourage or prevent nefarious activities. Job rotation is difficult for many organizations, for the same reasons that organizations don’t always implement mandatory vacations. A shortage of trained personnel, positions that require a lot of training and commitment, and a tendency to audit on a broader basis are all reasons why job rotation isn’t always performed.
Due Diligence and Due Care
Due diligence and due care are two very important concepts you need to be aware of in security. They mean two separate things, but they’re often used interchangeably, even by security professionals.
You could think of due diligence as “thinking responsibly” and due care as “acting responsibly.” When an organization has performed the research and investigated issues that could cause security or safety problems, it has performed due diligence. The organization is being proactive and preventative, and it has “done its homework” before making critical security decisions. An organization performs due care when it has done all that it reasonably can to prevent security incidents. It has put controls in place, such as enacting security policies, installing protective equipment, monitoring for security issues, and actively taking action to mitigate damage from incidents. Due care is also a proactive approach that occurs both before and after an incident; an organization that has practiced due care has acted responsibly and proactively in preventing security issues or reducing their impact on people and the organization.
Both of these concepts are important with regard to liability and negligence. From a legal perspective, organizations can legally be held liable if a security incident occurs, such as a large data breach, for example, that results in the loss of sensitive or private data. If the organization has done all it can to research weaknesses that could have caused the breach, and taken steps to prevent or mitigate the breach, then it has performed its due diligence and due care satisfactorily. If it has not done these things, it could be considered negligent in its duties and responsibilities toward protecting and securing the data. Due diligence and due care are subjective in nature; to prove that the organization has performed both satisfactorily, it must engage in risk management activities (covered later in the book) and document the actions it has taken to prevent and mitigate security incidents.
Module 3 Questions and Answers
Questions
1. Which of the following two relationships are inversely proportional? (Choose two.)
A. Functionality
B. Confidentiality
C. Security
D. Availability
2. Which of the three security goals is most concerned with ensuring that data is not subject to unauthorized modification or alteration?
A. Availability
B. Integrity
C. Confidentiality
D. Non-repudiation
3. Which of the following supporting elements concerns the inability of the user to deny that he or she has performed an action with regard to data or on the system?
A. Confidentiality
B. Authentication
C. Authorization
D. Non-repudiation
4. Mark is attempting to log on to a computer system. He successfully presents his user credentials, but the system continually denies his logon attempts and will not allow him to access the system. Which of the following steps in the logon process is failing?
A. Identification
B. Authorization
C. Authentication
D. Auditing
5. Which of the following supporting elements of security relates to the correct level of permissions, rights, and privileges that a person may have with respect to what actions they may take with data or on a system?
A. Non-repudiation
B. Authorization
C. Confidentiality
D. Authentication
6. An organization decides to split the ability to perform security-related tasks among several different people. Which of the following concepts is the organization practicing?
A. Non-repudiation
B. Administrative control
C. Job rotation
D. Separation of duties
7. The company policy requires that two people be present in order to witness and verify that highly sensitive information that is no longer needed has been properly destroyed. What practice is the company adhering to by requiring two people to perform this task?
A. Multi-person control
B. Separation of duties
C. Non-repudiation
D. Job rotation
8. The company suspects that Mike, a system administrator, is performing unauthorized actions on the network. Mike has not taken any significant time off in several years. Which of the following practices should the company consider in order to audit the activities Mike has performed while in his position?
A. Separation of duties
B. Job rotation
C. Mandatory vacation
D. Multi-person control
9. Jessica, who works in the accounting department, was discovered to have been performing administrative level actions on the accounting servers during a recent audit. While these actions were not malicious in nature, Jessica does not work at a level that would typically require server administration duties. Which of the following is not being properly implemented in the scenario?
A. Separation of duties
B. Principle of least privilege
C. Technical control
D. Accountability
10. The company was recently subject to a hacking attack that resulted in the breach of several thousand records containing consumer financial data. All the following are examples of actions the company took to prevent such an attack, demonstrating due care, except:
A. Allowing all employees, regardless of duties, to access the data
B. Installing and securely configuring a firewall
C. Enabling encryption for all data
D. Requiring strong authentication methods
Answers
1. A, C. Functionality and security are inversely proportional to each other; that is, as one increases, the other decreases.
2. B. Integrity is the security goal that security personnel want to achieve by preventing unauthorized data modification or alteration.
3. D. Non-repudiation means that a user cannot deny that he or she performed an action with regard to data or on a system.
4. C. Mark has successfully identified himself, but the system refuses to authenticate him and does not validate the credentials he has supplied. The system has not even proceeded to the authorization and auditing steps at this point.
5. B. Authorization relates to the level of rights, privileges, and permissions the user has with respect to data and systems.
6. D. The organization is practicing separation of duties because it has separated the ability to perform critical or sensitive tasks among several different people, thereby reducing the risk of fraud or unauthorized activity by a single person.
7. A. The company is engaging in multi-person control by requiring two people to be present to witness and verify the destruction of the sensitive information.
8. C. The organization should consider implementing a mandatory vacation in order to audit Mike’s activities while working in his position.
9. B. Since Jessica’s duties do not require her to have administrative control over the accounting server, the principle of least privilege is being violated in this scenario.
10. A. Allowing any employee, regardless of need-to-know, to access financial data does not demonstrate an example of due care. Allowing only those particular employees with a definite need-to-know based upon their daily duties, and restricting access from all other employees, would have demonstrated due care. All other choices are examples of the company fulfilling its due care responsibilities.