Signal Processing and Optimal Resource Allocation for the Interference Channel
Mingyi Hong and Zhi-Quan Luo, Department of Electrical and Computer Engineering, University of Minnesota, Minneapolis, MN 55455, USA, [email protected], [email protected]
Abstract
In this article, several design and complexity issues of the optimal physical layer resource allocation problem for generic interference channels are surveyed. The computational complexity, the convexity as well as the duality of the optimal resource allocation problem is discussed. Various existing algorithms for resource allocation are presented and compared. Open research problems are discussed throughout the article.
Keywords
Interference channel; Resource allocation; Computational complexity; Interference alignment; Game theory
2.08.1 Introduction
2.08.1.1 Resource allocation in communication networks
Resource allocation is a fundamental task in the design and management of communication networks. For example, in a wireless network, we must judiciously allocate transmission power, frequency bands, time slots, and transmission waveforms/codes across multiple interfering links in order to achieve high system performance while ensuring user fairness and quality of service (QoS). The same is true in wired networks such as the Digital Subscriber Lines (DSL).
The importance of resource allocation can be attributed to its key role in mitigating multiuser interference. The latter is the main performance limiting factor for heterogeneous wireless networks where the number of interfering macro/pico/femto base stations (BS) can be very large. In addition, resource allocation provides an efficient utilization of limited resources such as transmission power and communication spectrum. These resources are not only scarce but also expensive. In fact, wireless system operators typically spend billions of dollars to acquire licenses to operate certain frequency bands. Moreover, the rising cost of electricity for them to operate the infrastructure has already surpassed the salary cost to employees in some countries. Thus, from the system operator’s perspective, efficient spectrum/power utilization directly leads to high investment return and low operating cost (see e.g., [1,2]). The transmission power of a mobile terminal is another scarce resource. In this case, careful and efficient power allocation is the key to effectively prolong the battery life of mobile terminals.
Current cellular networks allocate orthogonal resources to users. For example, in a time-division multiplex access (TDMA) or a frequency-division multiplex access (FDMA) network, users in the same cell transmit in different time slots/frequency bands, and users in the neighboring cells transmit using orthogonal frequency channels. Although the interference from neighboring cells is suppressed, the overall spectrum efficiency is reduced, as each BS only utilizes a fraction of the available spectrum. According to a number of recent studies [3,4] current spectrum allocation strategies are not efficient, as at any given time and location, much of the allocated spectrum appears idle and unused. Moreover, users in cell edges still suffer from significant interference from non-neighboring cells, or pico/femto cells. In addition, for cell edge users the signal power from their own cells are typically quite weak. All of these factors can adversely affect their service quality.
To improve the overall system performance as well as user fairness, future wireless standards [5] advocate the notion of a heterogeneous network, in which low-power BSs and relay nodes are densely deployed to provide coverage for cell edge and indoor users. This new paradigm of network design brings the transmitters and receivers closer to each other, thus is able to provide high link quality with low transmission power [6,7]. Unfortunately, close proximity of many transmitters and receivers also introduces substantial in-network interference, which, if not properly managed, may significantly affect the system performance. Physical layer techniques such as multiple input multiple output (MIMO) antenna arrays and multiple cell coordination will be crucial for effective resource allocation and interference management in heterogeneous networks.
An effective resource allocation scheme should allow not only flexible coordination among BS nodes but also sufficiently distributed implementation. Coordination is very effective for interference mitigation among interfering nodes (e.g., Coordinated Multi-Point (CoMP)), but is also costly in terms of signaling overhead. For example, CoMP requires full BS coordination as well as the sharing of transmit data among all cooperating BSs. In contrast, a distributed resource allocation requires far less signaling overhead and no data sharing, albeit at the cost of possible performance loss. For in-depth discussions of various design issues in heterogenous networks, we recommend the recent articles and books including [7–13].
In this article, we examine several design and complexity aspects of the optimal physical layer resource allocation problem for a generic interference channel (IC). The latter is a natural model for multi-user communication networks. In particular, we characterize the computational complexity, the convexity as well as the duality of the optimal resource allocation problem. Moreover, we summarize various existing algorithms for resource allocation and discuss their complexity and performance tradeoff. We also mention various open research problems throughout the article.
2.08.1.2 Notation
Throughout, we use bold upper case letters to denote matrices, bold lower case letters to denote vectors, and regular lower case letters to denote scalars. For a symmetric (or Hermitian) matrix ![]() , the notation
, the notation ![]() (or
(or ![]() ) signifies X is positive semi-definite (or definite). User indices are denoted by subscripts, while frequency tone indices are denoted by superscripts. Zero mean normalized complex Gaussian distributions are denoted by
) signifies X is positive semi-definite (or definite). User indices are denoted by subscripts, while frequency tone indices are denoted by superscripts. Zero mean normalized complex Gaussian distributions are denoted by ![]() .
.
2.08.1.3 Interference channels
An interference channel (IC) represents a communication network in which multiple transmitters simultaneously transmit to their intended receivers in a common channel. See Figure 8.1 for a graphical illustration of the IC. Due to the shared communication medium, each transmitter generates interference to all the other receivers. The IC model can be used to study many practical communication systems. The simplest example is a wireless ad hoc network in which transmitters and their intended receivers are randomly placed. When all these nodes are equipped with multiple antenna arrays, the channel becomes a MIMO IC. See Figure 8.2 for a graphical illustration of a 2-user MIMO IC. If each transmitter and receiver pair communicates over multiple parallel subchannels, the resulting overall channel model becomes a parallel IC. This parallel IC model can be used to describe communication networks employing Orthogonal Frequency Division Multiple Access (OFDMA) where the available spectrum is divided into multiple independent tones/channels. Networks of this kind include the DSL network or the IEEE 802.11![]() networks.
networks.

Figure 8.1 The Interference Channel model. The solid lines represent the direct channels, while the dotted lines represent the interfering channels.
Another practical network is the multi-cell heterogenous wireless network. In the downlink of such network a set of interfering transmitters (BSs) simultaneously transmit to their respective groups of receivers. This channel is hitherto referred as an interfering broadcast channel (IBC). The uplink of this network can be modeled as an interfering multiple access channel (IMAC). See Figures 8.3 and 8.4 for graphical illustrations of these two channel models. Note that both IMAC and IBC reduce to an IC when there is only a single user in each cell.

Figure 8.3 The Interfering Broadcast Channel model. The solid lines represent the direct channels, while the dotted lines represent the interfering channels.

Figure 8.4 The Interfering Multiple Access Channel model. The solid lines represent the direct channels, while the dotted lines represent the interfering channels.
Our ensuing discussions will be focussed on these channel models. We will illustrate key computational challenges associated with optimal resource allocation and suggest various practical resource allocation approaches to overcome them.
2.08.1.4 System model
We now give mathematical description for three types of IC model—the scalar, parallel and MIMO IC models. Let us assume that there are K transmitter and receive pairs in the system, and we refer to each transceiver pair as a user. Let ![]() denote the set of all the users.
denote the set of all the users.
2.08.1.4.1 Scalar IC model
In a scalar IC model each user transmits and receives a scalar signal. Let ![]() denote user k’s transmitted signal, and let
denote user k’s transmitted signal, and let ![]() denote its power. Let
denote its power. Let ![]() denote user k’s power constraint:
denote user k’s power constraint: ![]() . Let
. Let ![]() denote user k’s normalized complex Gaussian noise with unit variance. Note that we have normalized the power of the noise to unity. Let
denote user k’s normalized complex Gaussian noise with unit variance. Note that we have normalized the power of the noise to unity. Let ![]() denote the channel between transmitter l and receiver k. Then user k’s received signal
denote the channel between transmitter l and receiver k. Then user k’s received signal ![]() can be expressed as
can be expressed as
 (8.1)
(8.1)
The signal to interference plus noise ratio (SINR) for user k is defined as
 (8.2)
(8.2)
We denote the collection of all the users’ transmit powers as ![]() .
.
2.08.1.4.2 Parallel IC model
In a parallel IC model, the spectrum is divided into N independent non-overlapping bands, each giving rise to a parallel subchannel. Let ![]() denote the set of all subchannels. Let
denote the set of all subchannels. Let ![]() denote the transmitted signal of user k on channel n, and let
denote the transmitted signal of user k on channel n, and let ![]() denote its power. We use
denote its power. We use ![]() to denote user k’s power budget so that
to denote user k’s power budget so that ![]() . Let
. Let ![]() denote the channel coefficient between the transmitter of user l and the receiver of user k on channel n. Let
denote the channel coefficient between the transmitter of user l and the receiver of user k on channel n. Let ![]() denote the Gaussian channel noise. The received signal of user k on subchannel n, denoted as
denote the Gaussian channel noise. The received signal of user k on subchannel n, denoted as ![]() , can be expressed as
, can be expressed as
 (8.3)
(8.3)
We define the collection of user k’s transmit power as ![]() , and define all the users’ transmit powers as
, and define all the users’ transmit powers as ![]() .
.
2.08.1.4.3 MIMO IC model
In a MIMO IC model the receivers and transmitters are equipped with ![]() and
and ![]() antennas, respectively. Let
antennas, respectively. Let ![]() and
and ![]() denote the transmitted and received signal of user k. Let
denote the transmitted and received signal of user k. Let ![]() represent the channel gain coefficient matrix between transmitter l and receiver k.
represent the channel gain coefficient matrix between transmitter l and receiver k.
Suppose each user k transmits/receives ![]() data streams, and let
data streams, and let ![]() and
and ![]() denote the transmitted symbols and the received estimated symbols, respectively. Assume that the data vector
denote the transmitted symbols and the received estimated symbols, respectively. Assume that the data vector ![]() is normalized so that
is normalized so that ![]() , and that the data signals for different users are independent from each other. Throughout this article, we will focus on linear strategies in which users use beamformers to transmit and receive data symbols. Let
, and that the data signals for different users are independent from each other. Throughout this article, we will focus on linear strategies in which users use beamformers to transmit and receive data symbols. Let ![]() and
and ![]() denote the transmit and receive beamformers, respectively. Let
denote the transmit and receive beamformers, respectively. Let ![]() denote the normalized complex Gaussian noise vector at receiver k, where
denote the normalized complex Gaussian noise vector at receiver k, where ![]() is the
is the ![]() identity matrix. Then the transmitted and received signal for user k can be expressed as
identity matrix. Then the transmitted and received signal for user k can be expressed as
![]() (8.4)
(8.4)
 (8.5)
(8.5)
![]() (8.6)
(8.6)
Let ![]() denote the covariance matrix of the transmitted signal of user k. We assume that each transmitter has an averaged total power budget of the form
denote the covariance matrix of the transmitted signal of user k. We assume that each transmitter has an averaged total power budget of the form
![]() (8.7)
(8.7)
When we have a single stream per user, ![]() and
and ![]() reduce to vectors
reduce to vectors ![]() and
and ![]() . In this case the SINR for user k’s stream can be defined as
. In this case the SINR for user k’s stream can be defined as
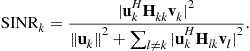 (8.8)
(8.8)
Multiple Input Single Output (MISO) IC is a special case of MIMO IC in which the receivers only have a single antenna. In this case each user can only transmit a single stream (![]() ,
, ![]() ), and the beamforming matrix
), and the beamforming matrix ![]() reduces to a beamforming vector
reduces to a beamforming vector ![]() . The channel coefficient matrix
. The channel coefficient matrix ![]() becomes a row vector
becomes a row vector![]() , the received signal
, the received signal ![]() reduces to a scalar, which can be expressed as
reduces to a scalar, which can be expressed as
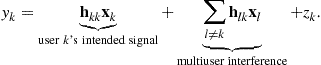 (8.9)
(8.9)
The SINR for each user k can be expressed as
 (8.10)
(8.10)
The power budget constraint becomes
![]() (8.11)
(8.11)
2.08.2 Information-theoretic results
2.08.2.1 Capacity results for IC model
In this subsection we briefly review some information theoretical results related to the capacity of the interference channel.
Consider a single user point to point additive white Gaussian noise (AWGN) scalar channel in the following form
![]() (8.12)
(8.12)
where ![]() are the transmitted signal, the received signal, the channel coefficient, and the Gaussian noise, respectively. Assume that the noise is independently distributed as
are the transmitted signal, the received signal, the channel coefficient, and the Gaussian noise, respectively. Assume that the noise is independently distributed as ![]() , and that the signal has a power constraint
, and that the signal has a power constraint ![]() . An achievable transmission rate R for this channel is defined as the rate that can be transmitted and decoded with diminishing error probability. The capacity of a channel C is the supremum of all achievable rates. Let us define the signal to noise ratio (SNR) of the channel as
. An achievable transmission rate R for this channel is defined as the rate that can be transmitted and decoded with diminishing error probability. The capacity of a channel C is the supremum of all achievable rates. Let us define the signal to noise ratio (SNR) of the channel as ![]() , then the capacity of the Gaussian channel is given by
, then the capacity of the Gaussian channel is given by
![]() (8.13)
(8.13)
We refer the readers’ to the classic books such as Cover Thomas [14] and the online course for an introductory treatment of information theory.
Now consider a 2-user interference channel
![]() (8.14)
(8.14)
The capacity region of this channel is the set of all achievable rate pairs of user 1 and user 2. Unlike the previous point to point channel, the complete characterization of the capacity region in this simplest 2-user IC case is an open problem in information theory. The largest achievable rate region for the interference channel is the Han-Kobayashi region [15], and it is achieved using superposition coding and interference subtraction. Recently, Etkin et al. [16] showed that this inner region is within one bit of the capacity region for scalar ICs. The capacity of the scalar interference channel under strong or very strong interference has been found in [15,17,18]. In particular, in the very strong interference case, i.e., ![]() and
and ![]() , the capacity region is given as
, the capacity region is given as
![]() (8.15)
(8.15)
where ![]() is the transmission rate for user k. This result indicates that in very strong interference case the capacity is not reduced. The references [19,20] include recent results that establish the capacity region for more general MIMO and parallel ICs in the strong interference case. However, for the general case where the interference is moderate, the capacity region remains unknown.
is the transmission rate for user k. This result indicates that in very strong interference case the capacity is not reduced. The references [19,20] include recent results that establish the capacity region for more general MIMO and parallel ICs in the strong interference case. However, for the general case where the interference is moderate, the capacity region remains unknown.
The capacity of a communication channel can be approximated by the notion of degrees of freedom. Recall that in the high SNR regime the capacity of a point to point link can be expressed as
![]() (8.16)
(8.16)
In this case we say the channel has d degrees of freedom. In a 2-user interference channel, the degrees of freedom region can be characterized as follows. Let the sum transmit power across all the transmitters be ![]() , and let
, and let ![]() denote the transmission rate achievable for user k. Then the capacity region
denote the transmission rate achievable for user k. Then the capacity region ![]() of this 2-user channel is the set of all achievable rate tuples
of this 2-user channel is the set of all achievable rate tuples ![]() . The degree of freedom region
. The degree of freedom region ![]() for this channel approximates the capacity region, and is defined as (see [21])
for this channel approximates the capacity region, and is defined as (see [21])
 (8.17)
(8.17)
The goal of resource allocation is to achieve the optimal performance established by information theory, subject to resource budget constraints. Unfortunately, optimal strategies for achieving the information theoretic limits are often unknown, too difficult to compute or too complicated to implement in practice. For practical considerations, we usually rely on simple transmit/receive strategies (such as linear beamformers) for resource allocation, with the goal of attaining an approximate information theoretic performance bound. The latter can be in terms of the degrees of freedom or some approximate capacity bounds which we describe next.
2.08.2.2 Achievable rate regions when treating interference as noise
Due to the difficulties in characterizing the capacity region and the optimal transmit/receive strategy for a general interference channel, many works in the literature study simplified transmit/receive strategies and the corresponding achievable rate regions. One such simplification, which is well motivated from practical considerations, is to assume that low-complexity single user receivers are used and that the multiuser interference is treated as additive noise. The authors of [22,23] show that treating interference as noise in a Gaussian IC actually achieves the sum-rate channel capacity if the channel coefficients and power constraints satisfy certain conditions. These results serve as a theoretical justification for this simplification. In the rest of this article we will treat interference as noise at the receivers. Let us first review some achievable rate region results for different IC models with this simplified assumption.
2.08.2.2.1 Definition of rate region
Consider the 2-user scalar IC (8.14). The users’ transmission powers are constrained by ![]() and
and ![]() , respectively. The following rates are achievable when the users treat their respective interference as noise
, respectively. The following rates are achievable when the users treat their respective interference as noise
![]()
where the term ![]() has been defined in (8.2). The directly achievable rate region
has been defined in (8.2). The directly achievable rate region ![]() is defined as the union of the achievable rate tuples
is defined as the union of the achievable rate tuples ![]()
![]() (8.18)
(8.18)
The directly achievable rate region represents the set of achievable rates when the transmitters are not able to synchronize with each other [24]. If transmitter synchronization is possible, time-sharing among the extreme points of the directly achievable rate region can be performed. In this case, the achievable rate region becomes the convex hull of the directly achievable rate region (8.18). Sometimes for convenience, we will refer the directly achievable rate regions simply as rate regions. The exact meaning of the rate region should be clear from the corresponding context.
For a parallel IC model, user k’s achievable rate on channel n, ![]() , can be expressed as
, can be expressed as
 (8.19)
(8.19)
User k’s achievable sum rate is the sum of the rates achievable on all the channels
 (8.20)
(8.20)
The directly achievable rate region ![]() in this case can be expressed as
in this case can be expressed as
 (8.21)
(8.21)
For a MIMO IC model, user k’s achievable rate when treating all other users’ interference as noise is
 (8.22)
(8.22)
The directly achievable rate region ![]() can be expressed as
can be expressed as
![]() (8.23)
(8.23)
2.08.2.2.2 Characterization of the directly achievable rate regions
Resource allocation requires a good understanding of the achievable rate regions. The (directly achievable) rate regions of the 2-user and the more general K-user scalar IC have been recently characterized in [25,26]. We briefly elaborate the 2-user rate region and its properties. Let ![]() denote a point in the rate region with
denote a point in the rate region with ![]() coordinates representing
coordinates representing ![]() and
and ![]() , respectively. Let
, respectively. Let ![]() . Define two functions
. Define two functions ![]() and
and ![]() . Then the boundary of the 2-user rate region consists of the union of two axis and the following two curves
. Then the boundary of the 2-user rate region consists of the union of two axis and the following two curves
 (8.24)
(8.24)
 (8.25)
(8.25)
Each of the above two curves consists of the set of rates achievable by one transmitter using its full power, while the other transmitter sweeping over its range of transmit powers. The convexity of this 2-user directly achievable rate region is studied in [25]. The following two conditions are sufficient to guarantee the convexity of the directly achievable rate region
 (8.26)
(8.26)
 (8.27)
(8.27)
In particular, a necessary condition for (8.26) and (8.27) is
![]() (8.28)
(8.28)
which requires that the maximum possible interference to be sufficiently small. As the interference increases, the directly achievable rate regions become nonconvex. Figure 8.5 shows the transition of the directly achievable rate regions as well as the time-sharing regions when the interference levels change from strong to weak. Clearly, when the interference is strong (![]() in this figure), orthogonal transmission such as TDMA or FDMA is optimal.
in this figure), orthogonal transmission such as TDMA or FDMA is optimal.

Figure 8.5 The rate regions for a 2-user IC with different interference conditions. ![]()
![]() ,
, ![]() . At point A and C, a single user transmits using full power. The solid lines are the directly achievable rate frontier. The dotted lines represents the rate boundary that can be achieved by time sharing. Note that the time sharing boundary for
. At point A and C, a single user transmits using full power. The solid lines are the directly achievable rate frontier. The dotted lines represents the rate boundary that can be achieved by time sharing. Note that the time sharing boundary for ![]() is the same as the rate region frontier.
is the same as the rate region frontier.
The same authors also characterize the achievable rate regions for the general K-user case. However the conditions for the convexity of the K-user regions are not available and deserve investigation. These conditions can be useful in solving resource allocation problems for an interference network.
More generally, it remains an open problem to derive a complete characterization of the (directly achievable) rate region for a parallel IC. The exact conditions for its convexity (or the lack of) are still unknown, although it is clear that the rate region will be convex if the interference coefficients are sufficiently small.
Several efforts have been devoted to characterizing certain interesting points (such as sum-rate optimal point) on the Pareto boundary of the rate region. Hayashi and Luo [27] have shown that in a parallel IC model with channel gains satisfying the following strong interference conditions
![]() (8.29)
(8.29)
where ![]() is the minimum number of subchannels used by any user, then the sum rate maximization point can only be achieved using an FDMA strategy. In the special case of 2-user N channel model, the following condition is sufficient for the optimality of FDMA strategy
is the minimum number of subchannels used by any user, then the sum rate maximization point can only be achieved using an FDMA strategy. In the special case of 2-user N channel model, the following condition is sufficient for the optimality of FDMA strategy
![]() (8.30)
(8.30)
The MIMO IC model is even more general than the parallel IC, hence its achievable rate region is also difficult to characterize. To see this, assuming that ![]() ; let all the channel matrices be diagonal:
; let all the channel matrices be diagonal: ![]() ,
, ![]() ; let all the transmission covariances be diagonal as well:
; let all the transmission covariances be diagonal as well: ![]() . In this simplified model, user k’s transmission rate reduces to
. In this simplified model, user k’s transmission rate reduces to
 (8.31)
(8.31)
which is exactly the rate expression for the N channel K user parallel IC as expressed in (8.19) and (8.20).
Larsson and Jorswieck [28,29] have characterized the achievable rate region of a 2-user MISO IC. In this case, user k’s achievable transmission rate reduces to
![]() (8.32)
(8.32)
where the SINR for user k is defined in (8.10).
Define the maximum-ratio transmission (MRT) and the zero forcing (ZF) beamformers for both users as
 (8.33)
(8.33)
where ![]() represents the orthogonal projection onto the complement of the column space of
represents the orthogonal projection onto the complement of the column space of ![]() . The authors show that any point on the Pareto boundary is achievable with the beamforming strategy
. The authors show that any point on the Pareto boundary is achievable with the beamforming strategy
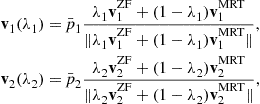 (8.34)
(8.34)
where ![]() . Intuitively, it is clear that
. Intuitively, it is clear that ![]() should stay in the subspace spanned by the channel vectors
should stay in the subspace spanned by the channel vectors ![]() . Since this subspace is spanned by the MRT and ZF beamformers, it is no surprise that
. Since this subspace is spanned by the MRT and ZF beamformers, it is no surprise that ![]() can be written as linear combinations of the MRT and ZF beamformers. The novelty of (8.34) lies in the claim that the parameters
can be written as linear combinations of the MRT and ZF beamformers. The novelty of (8.34) lies in the claim that the parameters ![]() are real numbers and lie in the interval
are real numbers and lie in the interval ![]() . Similar to the characterization (8.24) and (8.25) for the rate region of a scalar IC, the characterization (8.34) of optimal beamforming strategy can be used to computationally determine the rate region for a 2-user MISO IC.
. Similar to the characterization (8.24) and (8.25) for the rate region of a scalar IC, the characterization (8.34) of optimal beamforming strategy can be used to computationally determine the rate region for a 2-user MISO IC.
In [30], the authors extend their 2-user MISO channel work to a general K-user MISO IC. In particular, any point in the achievable rate region can be achieved using a set of beamformers ![]() that is characterized by
that is characterized by ![]() complex numbers
complex numbers ![]() as
as

However, because of the large number of (complex) parameters involved, this characterization appears less useful computationally in the determination of the rate region. We refer the readers to the web pages of Jorswieck and Larsson for more details. We emphasize again that except for these limited results, the structure of a general MIMO IC rate region is still unknown when the interference is treated as noise.
2.08.3 Optimal resource allocation in interference channel
As is evident from the discussions in Section 2.08.2, the most interesting points on the boundaries of the rate regions can only be achieved by careful resource allocation. In this section we discuss optimal resource allocation schemes for the general IC models. Such optimality is closely related to the choice of a performance metric for the communication system under consideration.
2.08.3.1 Problem formulations
A communication system should provide users with QoS guarantees, and fairness through efficient resource utilization. Mathematically, the resource allocation problem can be formulated as the problem of optimizing a certain system level utility function subject to resource budget constraints.
A popular family of utility functions is the so called “![]() -fair” utility functions, which can be expressed as
-fair” utility functions, which can be expressed as
 (8.35)
(8.35)
where ![]() denotes the transmission rate of user k. As pointed out in [31], different choices of the parameter
denotes the transmission rate of user k. As pointed out in [31], different choices of the parameter ![]() give different priorities to user fairness and overall system performance. We list four commonly used utility functions that belong to the family of
give different priorities to user fairness and overall system performance. We list four commonly used utility functions that belong to the family of ![]() -fair utility functions:
-fair utility functions:
a. The sum rate utility:![]() , obtained by setting
, obtained by setting ![]() ;
;
b. The proportional fair utility:![]() , obtained by letting
, obtained by letting ![]() ;
;
In terms of overall system performance, these utility functions can be ordered as
![]() (8.36)
(8.36)
In terms of user fairness, the order is reversed. We note that except for the case in which the interference is weak, these utility functions are nonconcave in general. For example, in Figure 8.6 we plot the sum rate utility for a 2-user scalar IC in cases where the interference is either weak or strong. Moreover, in most cases, it is not possible to represent these utility functions as concave ones via a nonlinear transformation. See [32] for an impossibility result in scalar interference channel. This is consistent with the complexity status (NP-hard) of the utility maximization problems [33–35] (see discussions in Section 2.08.3.2).

Figure 8.6 The sum rate utility for a 2-user scalar IC with different interference conditions. ![]() ,
, ![]() . In the left panel,
. In the left panel, ![]() . In the right panel,
. In the right panel, ![]() .
.
If we wish to find a resource allocation scheme that maximizes the system level performance, then we need to determine the conditions under which the system level problem is easy to solve. Whenever such conditions are met, efficient system level resource allocation decision can be carried out by directly solving a convex optimization problem. Intuitively, when the crosstalk coefficients are zero or sufficiently small (low interference regime), the utility functions should be concave. It will be interesting to analytically determine how small the crosstalk coefficients need to be in order to preserve concavity.
From a practical perspective, the conditions for the concavity of the utility function (in terms of the crosstalk coefficients) are valuable because they can be used to find high quality approximately optimal resource allocation schemes. In particular, we can use these conditions to partition the users into small groups within which the interference is less and resource allocation is easy. Different groups can be put on orthogonal resource dimensions, because the groups cause too much interference to each other. Ultimately a good resource allocation scheme in an interference limited network will likely involve a hybrid scheme whereby some small groups of users share resources, while different groups are separated from competition.
The lack of concavity (or more generally, the lack of concave reformulation/transformation) has made it difficult to numerically maximize these utility functions for resource allocation. To circumvent the computational difficulties, and to reduce the amount of channel state information required for practical implementation, some researchers have proposed to use alternative utility functions for resource allocation. For example, both the mean squared error (MSE) and the leakage power cost functions have been proposed as potential substitutes for the rate-based utility functions listed above [36–39]. Recently, a number of studies [32,40–42] have characterized a family of system utility functions that, under appropriate transformations, admit concave representations. Such transformations allow the associated utility maximization problems to be easily solvable. We refer the readers to Holger Boche’s web page for details on this topic. Unfortunately these utility functions are not directly related to individual users’ transmission rates, hence the solutions of the associated optimization problems tend to give suboptimal system performance (in terms of the users’ achievable rates). We shall not further elaborate on these resource allocation approaches in this article. Instead, we will focus on the use of above listed rate-based utility functions for resource allocation.
Let us describe several utility maximization problems to be considered in this article.
1. Utility maximization for the scalar IC model:
![]() (8.37)
(8.37)

2. Utility maximization for the parallel IC model:
![]() (8.38)
(8.38)

3. Utility maximization for the MISO IC model:
![]() (8.39)
(8.39)

4. Utility maximization for the MIMO IC model:
![]() (8.40)
(8.40)
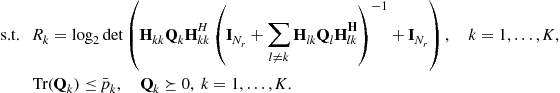
5. Utility maximization for the MIMO IC model (single stream per user):
![]() (8.41)
(8.41)

A “dual” paradigm for the design of the resource allocation algorithm is to provide QoS guarantees to all the users while minimizing the total power consumption. This formulation traditionally finds its application in voice communication networks where it is desirable to maintain a minimum communication rate (or SINR level) for each user in the system. Define ![]() as the set of SINR targets. We list several QoS constrained min-power problem to be considered in this article.
as the set of SINR targets. We list several QoS constrained min-power problem to be considered in this article.
6. Power minimization for the scalar IC model:
 (8.42)
(8.42)

7. Power minimization for the MISO IC model:
 (8.43)
(8.43)

8. Power minimization for the MIMO IC model (single stream per user):
 (8.44)
(8.44)

A hybrid formulation combines the above two approaches. It aims to provide QoS guarantees while at the same time maximizing a system level utility function. This hybrid formulation is useful in data communication networks where besides the minimum rate constraints, it is preferable to deliver high system throughput. We list two such formulations to be considered later in this article.
9. Hybrid formulation for the scalar IC model:
![]() (8.45)
(8.45)
![]()
10. Hybrid formulation for the parallel IC model:
![]() (8.46)
(8.46)

where ![]() is a set of rate targets.
is a set of rate targets.
We note that for the latter two formulations, the minimum rate/SINR requirements provide fairness to the users, while the optimization objectives are aimed at efficient utilization of system resource (e.g., spectrum or power). For both of these two problems, the feasibility of the set of rate/SINR targets needs to be carefully examined, as the rate/SINR requirements may not be simultaneously satisfiable.
2.08.3.2 Complexity of the optimal resource allocation problems
The aforementioned optimal resource allocation problems are nonconvex. However, the lack of convexity does not necessarily imply that the problem is difficult to solve. In some cases, it may be possible for a nonconvex problem to be appropriately transformed into an equivalent convex one and solved efficiently. A principled approach to characterize the intrinsic difficulty of an utility maximization problem is by way of the computational complexity theory [43].
In the following, we summarize a number of recent studies on the computational complexity status of these resource allocation problems. These complexity results suggest that in most cases solving the utility maximization problems to global optimality is computationally intractable as the number of users in the system increases.
Table 8.1 lists the complexity status for resource allocation problems with specific utility functions for the parallel and MISO IC models. Note that the scalar IC model is included as a special case.
Table 8.1
Complexity Status of Utility Maximization Problems for the Parallel and MISO IC Models [33,34]

Table 8.2 summarizes the complexity status for the minimum rate utility maximization problem and the sum power minimization problem with the QoS constraint in MIMO IC model (i.e., problem (8.41) with min-rate utility and problem (8.44)). Note that the results in Table 8.2 are based on the assumption that all transmitters and receivers use linear beamformers and that each mobile receives a single data stream.
Recall that the MIMO IC is a generalization of the Parallel IC (see Section 2.08.2.2). It follows that the complexity results in Table 8.1 hold true for the MIMO IC model with an arbitrary number of data streams per user. We refer the readers to the author’s web page for recent developments in the complexity analysis as well as other resource allocation algorithms.
2.08.3.3 Algorithms for optimal resource allocation
We now describe various utility maximization based algorithms for resource allocation. These algorithms will be grouped and discussed according to their main algorithmic features. Since the min-rate utility function is non-differentiable, it requires a separate treatment that is different from the other utility functions. We begin our discussion with resource allocation algorithms based on the min-rate utility maximization.
2.08.3.3.1 Algorithms for min-rate maximization
Early works on resource allocation aimed to find optimal transmission powers that can maximize the min-SINR utility. In case of the scalar IC, this problem can be formulated as
![]() (8.47)
(8.47)
![]()
In [46–48], the authors studied the feasibility of this problem and proposed optimal power allocation strategies for it. For randomly generated scalar interference channels, they showed that with probability one, there exists a unique optimum value to the above problem. This optimal value, denoted as ![]() , can be expressed as
, can be expressed as
![]() (8.48)
(8.48)
where ![]() represents the maximum eigenvalue of the matrix
represents the maximum eigenvalue of the matrix ![]() ;
; ![]() is a matrix with its
is a matrix with its ![]() th element defined as
th element defined as ![]() . Distributed power allocation algorithms for this problem were also developed. For example, Foschini Miljanic [46] proposed an autonomous power control (APC) algorithm that iteratively adjusts the users’ power levels as follows
. Distributed power allocation algorithms for this problem were also developed. For example, Foschini Miljanic [46] proposed an autonomous power control (APC) algorithm that iteratively adjusts the users’ power levels as follows
 (8.49)
(8.49)
where ![]() is a small positive constant and t is the iteration index. We refer the readers to [49] and the web page of Hanly for further discussion of power control techniques for a scalar IC.
is a small positive constant and t is the iteration index. We refer the readers to [49] and the web page of Hanly for further discussion of power control techniques for a scalar IC.
For a MISO IC model, the problem of finding optimal transmit beamformers for the maximization of the min-SINR utility has been considered by Bengtsson Ottersten [50] and Wiesel et al. [51]. The corresponding resource allocation problem can be equivalently formulated as
![]() (8.50)
(8.50)

This optimization problem (8.50) is nonconvex, but can be relaxed to a semidefinite program (or SDP; see [52] for an introduction to the related concepts and algorithms). Surprisingly, [50] established that the SDP relaxation for (8.50) is tight; see the subsequent section “Algorithms for QoS Constrained Power Minimization” for more discussions. Later, Wiesel et al. [51] further showed that this nonconvex optimization problem can be solved via a sequence of second order cone programs (SOCP); see [52] for the definition of SOCP. The key observation is that for a fixed ![]() , checking the feasibility of (8.50) is an SOCP, which can be solved efficiently by the standard interior point methods. Let
, checking the feasibility of (8.50) is an SOCP, which can be solved efficiently by the standard interior point methods. Let ![]() denote the optimal objective for problem (8.50), this max-min SINR problem can be solved by a bisection technique:
denote the optimal objective for problem (8.50), this max-min SINR problem can be solved by a bisection technique:
More recently, the max-min fairness resource allocation problem has been considered by Liu et al. [44] for the MIMO IC model. Unfortunately, the problem becomes NP-hard in this case (see Table 8.2).
The joint transceiver beamformer design for the min-SINR maximization problem in a MIMO IC (i.e., problem (8.41) with min-rate utility) has recently been considered in [44]. As shown in Section 2.08.3.2, this problem is in general NP-hard. Consequently, they proposed a low-complexity algorithm that converges to a stationary point of this problem. A key observation is that when the receive beamformers ![]() are fixed, the considered problem can be written as
are fixed, the considered problem can be written as
![]() (8.51)
(8.51)

which has the same form as the MISO min-SINR problem in (8.50), and thus can be solved using bisection and SOCP. As a result, the authors proposed to alternate between the following two steps to solve the min-rate maximization problem:
Unlike the MISO min-SINR case, only local optimal solutions can be found in the MIMO case. Extending the above algorithm to the MIMO IC/IBC/IMAC case with multiple data streams per user is not a trivial task. For a MIMO IC model, the feasibility problem becomes

This problem is nonconvex and there is no known convex reformulation for it. Finding efficient and preferably distributed algorithms for these channel models is a challenging problem which deserves investigation.
2.08.3.3.2 Algorithms for weighted sum-utility maximization
In addition to the min-rate (min-SINR) utility, we can use other utility functions to allocate resources. For instance, let ![]() denote a set of positive weights that represent the relative priorities of the users in the system. Then the weighted sum-rate maximization (WSRM) problem for a parallel IC can be formulated as
denote a set of positive weights that represent the relative priorities of the users in the system. Then the weighted sum-rate maximization (WSRM) problem for a parallel IC can be formulated as
 (8.52)
(8.52)

This simply corresponds to the problem (8.38) with ![]() as the objective function. WSRM is a central problem for physical layer resource allocation. Many sum-utility maximization problems can be reduced to solving a sequence of WSRM problems for the single channel
as the objective function. WSRM is a central problem for physical layer resource allocation. Many sum-utility maximization problems can be reduced to solving a sequence of WSRM problems for the single channel ![]() case, see [53]. Unfortunately, the complexity results in Section 2.08.3.2 indicate that WSRM is in general a hard problem which can not be solved to global optimality by a polynomial time algorithm (unless NP = P). As a result, many works are devoted to finding high quality locally optimal solutions for the WSRM problem.
case, see [53]. Unfortunately, the complexity results in Section 2.08.3.2 indicate that WSRM is in general a hard problem which can not be solved to global optimality by a polynomial time algorithm (unless NP = P). As a result, many works are devoted to finding high quality locally optimal solutions for the WSRM problem.
2.08.3.3.3 Algorithms based on Lagrangian dual decomposition
The linear additive structure of the power budget constraints in the weighted sum-utility maximization problem (8.38) can be exploited by Lagrangian dualization. In particular, [54] (see also [34,53]) considered the Lagrangian dual relaxation of the utility maximization problem (8.38) for the parallel IC model. Let us define the dual function of the primal problem (8.38) as
 (8.53)
(8.53)
where ![]() is the set of dual variables associated with the sum power constraints. Then the dual problem of the utility maximization problem can be expressed as follows
is the set of dual variables associated with the sum power constraints. Then the dual problem of the utility maximization problem can be expressed as follows
![]() (8.54)
(8.54)
![]()
Denote the optimal objective values of the primal problem (8.38) and the dual problem (8.54) with N channels as ![]() and
and ![]() , respectively. By the standard duality theory in optimization [55], we have that the duality gap
, respectively. By the standard duality theory in optimization [55], we have that the duality gap![]() satisfies
satisfies
![]() (8.55)
(8.55)
When the primal problem is convex, strong duality holds and the inequality becomes equality. When restricted to the FDMA (Frequency Division Multiple Access) solutions, the Lagrangian dual problem decomposes across tones and is efficiently solvable [27,53]. However, when the dual optimal solutions are not unique, it is difficult to construct a primal optimal solution for the problem (8.38). Luo and Zhang [53] proposed to use an additional randomized step to generate a primal feasible solution from the dual optimal solution.
When the primal problem is not restricted to the FDMA solutions, the Lagrangian dual function is difficult to compute, let alone optimize (see the complexity results in Section 2.08.3.2). Yu Liu [54] proposed an iterative spectrum balancing (ISB) algorithm that alternates between the following two steps to solve the WSRM problem (8.52):
Due to the inexactness of step 1, this algorithm is not guaranteed to converge to a global optimal solution of the WSRM problem (8.52).
A surprising observation in [54] is that when N (the number of channels) goes to infinity, the duality gap vanishes. Luo and Zhang [34,53] rigorously proved this result using Lyapunov theorem in functional analysis. In particular, Lyapunov’s theorem implies that for the continuous formulation of the WSRM problem (infinite number of channels), the rate region is actually convex. With additional steps to estimate of the approximation of Lebesque integrals, Luo and Zhang [53] showed that for some constant L, an estimate of the duality gap is bounded by
![]() (8.56)
(8.56)
Clearly the gap vanishes as N goes to infinity. Using this estimate, Luo Zhang [53] further developed a polynomial time approximation scheme to find an optimal FDMA solution for the continuous version of the WSRM problem (8.52).
Algorithms based on interference pricing
In a number of related works [56–59], the authors proposed a modified iterative water-filling (M-IWF) algorithm that iteratively solves K subproblems. The subproblem related to user k can be expressed as
 (8.57)
(8.57)
 (8.58)
(8.58)
![]()
 (8.59)
(8.59)
This term can be viewed as the interference price that user k needs to pay on channel n for the unit of interference it causes to all other users in the system. In other words, the price ![]() corresponds to the marginal decrease in the sum-rate utility per unit increase in interference power
corresponds to the marginal decrease in the sum-rate utility per unit increase in interference power ![]() . If the interference price is set to zero, then we are led to the standard iterative water-filling algorithm [60]. The M-IWF algorithm works by iteratively performing the following steps:
. If the interference price is set to zero, then we are led to the standard iterative water-filling algorithm [60]. The M-IWF algorithm works by iteratively performing the following steps:
We note that the overall computational complexity of step 1 is ![]() , where T is the total number of iterations needed for convergence. It was conjectured that this algorithm converges at least to a stationary point of the WSRM problem, but no formal proof was given. In [61], the authors successfully established the convergence (to the stationary point) of this type of pricing algorithm under the condition that the users act sequentially, i.e., in step 1 of M-IWF, only a single user solves its optimization problem (8.57). They interpreted this sequential M-IWF as a successive linear approximation of the WSRM problem, and showed that the term
, where T is the total number of iterations needed for convergence. It was conjectured that this algorithm converges at least to a stationary point of the WSRM problem, but no formal proof was given. In [61], the authors successfully established the convergence (to the stationary point) of this type of pricing algorithm under the condition that the users act sequentially, i.e., in step 1 of M-IWF, only a single user solves its optimization problem (8.57). They interpreted this sequential M-IWF as a successive linear approximation of the WSRM problem, and showed that the term ![]() is the first order Taylor approximation (up to an additive constant term) of
is the first order Taylor approximation (up to an additive constant term) of ![]() , the nonconcave part of the objective function. With this interpretation, the M-IWF algorithm can be seen as letting each user sequentially solve a partially linearized version of the WSRM problem. Since the first order Taylor approximation is a locally tight approximation of the weighted sum-rate objective function, the weighted sum-rates computed by the sequential M-IWF algorithm improve monotonically. Moreover, since the users update their power allocations locally, the M-IWF algorithm can be implemented in a distributed manner as long as the interference prices are exchanged among the users at each iteration. We shall refer to the sequential modification of the M-IWF as the multichannel distributed pricing (MDP) algorithm.
, the nonconcave part of the objective function. With this interpretation, the M-IWF algorithm can be seen as letting each user sequentially solve a partially linearized version of the WSRM problem. Since the first order Taylor approximation is a locally tight approximation of the weighted sum-rate objective function, the weighted sum-rates computed by the sequential M-IWF algorithm improve monotonically. Moreover, since the users update their power allocations locally, the M-IWF algorithm can be implemented in a distributed manner as long as the interference prices are exchanged among the users at each iteration. We shall refer to the sequential modification of the M-IWF as the multichannel distributed pricing (MDP) algorithm.
The interference pricing idea has been extended to the MISO IC in [62,63], and to the MIMO IC with single stream per user in [64]. Ref. [65] considered interference pricing for the general MIMO IC without the single data stream per user restriction. Similar to the parallel IC situation, the convergence of the interference pricing algorithm for the MIMO IC has only been analyzed for the sequential user update case. It will be interesting to see how the pricing technique (and its convergence proof) can be extended to the MIMO IC/IBC/IMAC models with an arbitrary number of streams per user, while allowing simultaneous user updates. A step in this direction was taken by Venturino et al. [66] which extended the interference pricing technique to the MISO IBC model. Their algorithm (named Iterative Coordinated BeamForming (ICBF)) calculates proper pricing coefficients that enable each BS to update their respective beamformers. Convergence was always observed in the simulation, but no formal proof was given. A recent survey of various pricing techniques used in wireless networks can be found in [67]. We also refer the readers to the web pages of BerryandHonig for other related works on this topic.
Algorithms based on successive convex approximation
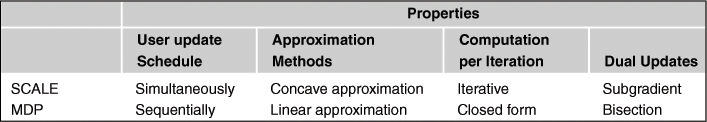
The MDP algorithm belongs to a class of algorithms called successive convex approximation (SCA). The idea is to construct and maximize a series of (concave) lower bounds of the original WSRM problem, so that a high quality solution can be obtained asymptotically. See Figure 8.7 for a graphical illustration of how this class of algorithms work. In [68], an algorithm called Successive Convex Approximation for Low complExity (SCALE) is proposed to improve the spectral efficiency of the DSL network. This algorithm transforms the noncocave sum rate maximization problem into a series of convex problems by utilizing the following lower bound
![]() (8.60)
(8.60)
![]() (8.61)
(8.61)
where the inequality (8.60) is tight at ![]() . This lower bound allows the WSRM problem to be approximated by
. This lower bound allows the WSRM problem to be approximated by
 (8.62)
(8.62)

After a log transformation ![]() , this relaxed problem turns out to be concave in
, this relaxed problem turns out to be concave in ![]() . The SCALE algorithm alternates between the following two steps:
. The SCALE algorithm alternates between the following two steps:
Step 1 can be solved either in a centralized fashion using Geometric Programming (GP) technique, or by solving the dual problem of (8.62) in a distributed way. This algorithm is guaranteed to reach a stationary point of the original sum rate maximization problem. We briefly compare the major differences of the MDP and SCALE algorithms in Table 8.3.

Figure 8.7 Graphical illustration of the family of algorithms using successive convex approximation. In this example, ![]() is the initial point. At
is the initial point. At ![]() , a (strictly) concave function
, a (strictly) concave function ![]() is used to approximate the original non-convex function
is used to approximate the original non-convex function ![]() . The optimal solution of
. The optimal solution of ![]() , is found by standard optimization technique. Then the (strictly) concave function
, is found by standard optimization technique. Then the (strictly) concave function ![]() is constructed at the point
is constructed at the point ![]() .
. ![]() is then optimized to obtain the point
is then optimized to obtain the point ![]() . Continue this process, a stationary solution of the original function
. Continue this process, a stationary solution of the original function ![]() can be found.
can be found.
In [69], a different lower bound is proposed for the WSRM problem. Specifically, the authors decompose the objective function as the difference of two concave functions of ![]() (referred to as the “dc” function)
(referred to as the “dc” function)
 (8.63)
(8.63)
Similar to the steps of SCA introduced earlier, in each iteration of the algorithm, the second sum is replaced with its linear lower bound, and the resulting concave maximization problem is solved. Compared to the MDP algorithm which linearizes ![]() , this algorithm linearizes all the interference terms in each iteration. As such, it linearizes more terms than the MDP algorithm per iteration.
, this algorithm linearizes all the interference terms in each iteration. As such, it linearizes more terms than the MDP algorithm per iteration.
A related algorithm has been proposed in the recent work [33] where the authors considered the general utility maximization problem in MISO IC (i.e., problem formulation (8.39)). Besides providing complexity results, the authors proposed an algorithm that is able to converge to local optimal solutions for problem (8.39) with any smooth (twice continuously differentiable) utility functions. The basic idea is to let the users cyclically update their beamformers using projected gradient ascent algorithm. In particular, at iteration t, user k takes a gradient projection step to compute the direction ![]() by solving the following problem
by solving the following problem
![]() (8.64)
(8.64)
![]()
In contrast to the MDP and SCALE, the subproblem (8.64) linearizes the entire objective function of (8.39) at the current point ![]() , and has an additional quadratic regularization term
, and has an additional quadratic regularization term ![]() . This subproblem is a convex quadratic minimization problem over a ball. As such, it is easier to solve than the corresponding subproblems of MDP and SCALE which are based on partial linearization of the original WSRM objective function. We list below the main steps of this cyclic coordinate ascent (CCA) algorithm:
. This subproblem is a convex quadratic minimization problem over a ball. As such, it is easier to solve than the corresponding subproblems of MDP and SCALE which are based on partial linearization of the original WSRM objective function. We list below the main steps of this cyclic coordinate ascent (CCA) algorithm:
The CCA algorithm only works in MISO IC case, and it is not clear how to extend it to the MIMO IC.
Algorithms based on weighted MMSE minimization
A different weighted sum-rate maximization approach was proposed in [70] for the MIMO broadcast downlink channel, where the WSRM problem is transformed to an equivalent weighted sum MSE minimization (WMMSE) problem with some specially chosen weight matrices. Since the optimal weight matrices are generally unknown, the authors of [70] proposed an iterative algorithm that adaptively chooses the weight matrices and updates the linear transmit/receive beamformers at each iteration. A nonconvex cost function was constructed in [70] and shown to monotonically decrease as the algorithm progresses. But the convergence of the iterates to a stationary point (or the global minimum) of the cost function is not known. Later, a similar algorithm was proposed in [71] for the interference channel where each user only transmits one data stream.
It turns out that this WMMSE based resource allocation approach can be extended significantly to handle the MIMO-IC and MIMO-IBC/IMAC models as well as general utility functions. In particular, the authors of [72,73] established a general equivalence result between the global (and local) minimizers of the weighted sum-utility maximization problem (e.g., (8.40) and (8.52)) and a suitably defined weighed MMSE minimization problem. The latter can be effectively optimized by utilizing the block coordinate descent technique, resulting in independent, closed form iterative update across the transmitters and receivers. The resulting algorithm is named the WMMSE algorithm.
To gain some insight, let us consider the special case of a scalar IC system where the equivalence of the WSRM problem (8.52) and a weighted sum MSE minimization can be seen more directly. Let ![]() denote the complex gains used by the transmitter j and receiver k respectively. Consider the following weighted sum-MSE minimization problem
denote the complex gains used by the transmitter j and receiver k respectively. Consider the following weighted sum-MSE minimization problem
 (8.65)
(8.65)
where ![]() is a positive weight variable, and
is a positive weight variable, and ![]() is the mean square estimation error
is the mean square estimation error
![]()
To see the equivalence, we can check the first order optimality condition to find the optimal ![]() and
and ![]()
 (8.66)
(8.66)
Plugging these optimal values in (8.65) gives the following equivalent optimization problem

which, upon a change of variable ![]() , is equivalent to
, is equivalent to

This establishes the equivalence of the WMMSE problem (8.65) and the WSRM problem (8.52). More importantly, the equivalence goes one step further: there is a one-to-one correspondence between the local minimums of the two problems (see [72,73]).
The equivalence relation implies that maximizing the weighted sum-rate can be accomplished via iterative weighted MSE minimization. The latter problem is in the space of ![]() and is easier to handle since optimizing each variable while holding the others fixed is convex and easy (e.g., closed form). This property has been exploited in [72,73] to design the WMMSE algorithm. In contrast, the original sum-rate maximization problem (8.52) is in the space of p and is nonconvex, which makes the iterative optimization process difficult.
and is easier to handle since optimizing each variable while holding the others fixed is convex and easy (e.g., closed form). This property has been exploited in [72,73] to design the WMMSE algorithm. In contrast, the original sum-rate maximization problem (8.52) is in the space of p and is nonconvex, which makes the iterative optimization process difficult.
The general form of the WMMSE algorithm can handle any utility functions satisfying the following conditions
 (8.67)
(8.67)
![]() (8.68)
(8.68)
![]() (8.69)
(8.69)
In addition, it also handles a wide range of channel models, e.g., MIMO and parallel IC/IBC/IMAC. It is well known that ![]() , where
, where ![]() is the mean square error (MSE) matrix for user k. Define a set of new functions:
is the mean square error (MSE) matrix for user k. Define a set of new functions: ![]() . Similar to the scalar IC case, the equivalence of the following two optimization problems can be established
. Similar to the scalar IC case, the equivalence of the following two optimization problems can be established
 (8.70)
(8.70)
 (8.71)
(8.71)
![]()
where ![]() is the inverse map of
is the inverse map of ![]() . The WMMSE algorithm finds a stationary point of the alternative problem (8.71). In particular, it alternately updates the three sets of variables
. The WMMSE algorithm finds a stationary point of the alternative problem (8.71). In particular, it alternately updates the three sets of variables ![]() , or
, or ![]() for problem (8.71), each time keeping two sets of variables fixed. The WMMSE algorithm for a MIMO IC is listed in the following table:
for problem (8.71), each time keeping two sets of variables fixed. The WMMSE algorithm for a MIMO IC is listed in the following table:
We note that in Step 6, ![]() is the Lagrangian multiplier for the constraint
is the Lagrangian multiplier for the constraint ![]() . This multiplier can be found easily by bi-section method. Also, notice that all updates are in closed form (except for
. This multiplier can be found easily by bi-section method. Also, notice that all updates are in closed form (except for ![]() ) and can be performed simultaneously across users.
) and can be performed simultaneously across users.
To compare the performance and the efficiency of various resource allocation methods, we consider a simple simulation experiment involving a parallel-IC and a MIMO-IC. We first specialize the WMMSE algorithm to the parallel-IC scenario and compare it with SCALE and MDP algorithms described earlier. To specialize the WMMSE algorithm for a parallel IC, let us restrict the transmit/receive matrices for each user to be diagonal. That is, the beamforming directions are fixed to be unit vectors and we only optimize power loading factors on the parallel channels. Let ![]() denote the user k’s transmit filter vector, with
denote the user k’s transmit filter vector, with ![]() corresponding to the complex scaling coefficient to be used for the data stream on channel n. Similarly, the receive filter vector and the weight vector are denoted by
corresponding to the complex scaling coefficient to be used for the data stream on channel n. Similarly, the receive filter vector and the weight vector are denoted by ![]() respectively. Then the WMMSE algorithm for the parallel IC channel can be described as:
respectively. Then the WMMSE algorithm for the parallel IC channel can be described as:
In the simulation, we set the weights ![]() all equal to 1, and set the maximum power
all equal to 1, and set the maximum power ![]() for all the users. We set the stopping criteria as
for all the users. We set the stopping criteria as ![]() for all algorithms. The channel coefficients are generated from the complex Gaussian distribution
for all algorithms. The channel coefficients are generated from the complex Gaussian distribution ![]() . For MIMO IC, all the transmitters and receivers are assumed to have the same number of antennas.
. For MIMO IC, all the transmitters and receivers are assumed to have the same number of antennas.
We first investigate the performance of SCALE, MDP and the parallel version of the WMMSE algorithm for a parallel IC. Figure 8.8 illustrates the sum rate performance of different algorithms when ![]() and
and ![]() . We see that these algorithms all have similar performance across all the SNR values. Figure 8.9 shows the averaged CPU time comparison of these three algorithms under the same termination criteria and the same accuracy for the search of Lagrangian variables. We observe that the WMMSE requires much less computational time compared to the other two algorithms when the number of users becomes large. Note that the first step in the SCALE algorithm is implemented using the subgradient and the fixed point iterations suggested in [68, Section IV-A]. The stepsizes for the subgradient method as well as the number of the fixed point iterations need to be tuned appropriately to ensure fast convergence.
. We see that these algorithms all have similar performance across all the SNR values. Figure 8.9 shows the averaged CPU time comparison of these three algorithms under the same termination criteria and the same accuracy for the search of Lagrangian variables. We observe that the WMMSE requires much less computational time compared to the other two algorithms when the number of users becomes large. Note that the first step in the SCALE algorithm is implemented using the subgradient and the fixed point iterations suggested in [68, Section IV-A]. The stepsizes for the subgradient method as well as the number of the fixed point iterations need to be tuned appropriately to ensure fast convergence.

Figure 8.8 Comparison of the averaged sum rate performance versus SNR of different algorithms in parallel IC. ![]() . Each curve in the figure is averaged over 100 random channel realizations.
. Each curve in the figure is averaged over 100 random channel realizations.

Figure 8.9 Comparison of the averaged CPU time versus the number of users of different algorithms in parallel IC. ![]() . Each curve in the figure is averaged over 100 random channel realizations.
. Each curve in the figure is averaged over 100 random channel realizations.
Next we examine the performance of the WMMSE and the MIMO distributed pricing (MIMO-DP) algorithm developed in [65] in the context of a MIMO-IC. Figure 8.10 illustrates the sum rate performance of the two algorithms when ![]() and
and ![]() . Figure 8.11 shows the averaged CPU time comparison of the two algorithms. We again observe that the WMMSE requires much less computational time compared with the MIMO-DP algorithm when the number of users becomes large.
. Figure 8.11 shows the averaged CPU time comparison of the two algorithms. We again observe that the WMMSE requires much less computational time compared with the MIMO-DP algorithm when the number of users becomes large.

Figure 8.10 Comparison of the averaged sum rate performance versus SNR of different algorithms in MIMO IC. ![]() . Each curve in the figure is averaged over 100 random channel realizations.
. Each curve in the figure is averaged over 100 random channel realizations.

Figure 8.11 Comparison of the averaged CPU time versus the number of users of different algorithms in MIMO IC. ![]() . Each curve in the figure is averaged over 100 random channel realizations.
. Each curve in the figure is averaged over 100 random channel realizations.
Different from many algorithms discussed earlier (e.g., CCA, MDP), the WMMSE algorithm allows all transmitters/receivers to update their beamformers simultaneously. This feature leads to simple implementation and fast convergence. It will be interesting to see how this algorithm can be further extended to include other utility functions such as the min-rate utility, and to other formulations like QoS constrained power minimization. Also, further research is needed to uncover the full algorithmic potential of WMMSE algorithm for a wide range of applications including joint base station assignment, power control, and beamforming.
Algorithms for cross layer resource allocation
We briefly mention a few cross-layer resource allocation algorithms which require solving a weighted sum-utility problem at each step. These algorithms jointly optimize physical layer as well as the media access (MAC) layer resources to improve the overall system performance.
Recently, Yu et al. [74] considered the joint MAC layer scheduling and physical layer beamforming and power control in a multicell OFDMA-MIMO network. The algorithm assigns the users to the BSs according to their individual priority and channel status. The beamformers are updated using a MSE duality results developed in [75,76] for multicell network. The transmit powers of the BSs are updated by using the Newton’s method. In [77–79], the authors considered the WSRM problem in a multicell downlink OFDMA wireless network. They proposed to let the BSs alternate between the following two tasks to achieve high system throughput: (1) optimally schedule the users on each channel; (2) jointly optimize their downlink transmit power using a physical layer resource allocation algorithm such as M-IWF or SCALE. Razaviyayn et al. [80] proposed to adaptively group users into non-interfering groups, and optimize the transceiver structure and the group membership jointly. Such grouping strategy results in fair resource allocation, as cell-edge users with weak channels are protected from the strong users. A generalized version of the WMMSE algorithm has been developed to perform such joint optimization. In all these works the resulting resource allocation schemes achieved a weighted sum-utility that is significantly higher than what is possible with only performing physical layer beamforming/power allocation.
Joint admission control and downlink beamforming is another example of cross layer resource allocation. For a single cell MISO network, this problem has been considered in [81,82]. A related problem is the joint BS selection and power control/beamforming problem. This problem has been addressed in the traditional CDMA based network (see, e.g., [83–85]), in OFDMA networks (e.g., [86–88]) and in a more general MIMO-HetNet in which all BSs operate on the same frequency bands [89,90]. An interesting research direction to pursue is to effectively incorporate these higher layer protocols to boost the system performance for a MIMO and parallel IBC/IMAC network.
2.08.3.3.4 Algorithms for QoS constrained power minimization
For the scalar IC model, the QoS constrained min-power problem as formulated in (8.42) has been considered in [83,85,91]. They derived conditions for the existence of a feasible power allocation given a set of SINR targets. Define a ![]() matrix
matrix ![]() as follows
as follows
 (8.72)
(8.72)
If ![]() , an optimal power allocation
, an optimal power allocation ![]() can be found as follows
can be found as follows
![]() (8.73)
(8.73)
where ![]() . The convexity of the feasible SINR region for this problem has been established in [92,93].
. The convexity of the feasible SINR region for this problem has been established in [92,93].
Alternatively, Yates [94] has provided a framework that allows the users to compute the optimal solution of problem (8.42)distributedly by the following fixed point iteration
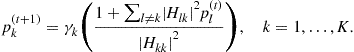 (8.74)
(8.74)
This algorithm is shown to have linear rate of convergence, that is,
![]() (8.75)
(8.75)
where ![]() is the optimal solution of the min-power problem, and
is the optimal solution of the min-power problem, and ![]() is some positive constant. Recently Boche and Schubert [95] has proposed a different algorithm based on a Newton-type update that exhibits even faster (super-linear) rate of convergence. This algorithm can be applied to more general scenarios when the receivers are equipped with multiple antennas.
is some positive constant. Recently Boche and Schubert [95] has proposed a different algorithm based on a Newton-type update that exhibits even faster (super-linear) rate of convergence. This algorithm can be applied to more general scenarios when the receivers are equipped with multiple antennas.
When the set of SINR targets cannot be supported by the system (that is, the problem (8.42) is infeasible), the call admission control mechanism should be invoked. A couple of recent works [96,97] have considered the problem of joint admission and power control arises in the QoS constrained power minimization problem. See [98] for a survey on the general topic of call admission control.
For a MISO IC, Bengtsson Ottersten [50,99] considered the min-power transmit beamforming problem under QoS constraints (problem (8.43)). Define ![]() and
and ![]() , this problem can be equivalently formulated as
, this problem can be equivalently formulated as
 (8.76)
(8.76)

Relaxing the rank constraint, this problem is a convex semidefinite program and can be solved efficiently. Interestingly, the authors showed that a rank-one solutions must exist for the relaxed problem, revealing a certain hidden convexity in this problem. The following procedure can be used to construct a rank-1 solution from an optimal solution ![]() of the relaxed problem:
of the relaxed problem:
The approach works for the IBC model as well. It can also be extended to include other resource allocation options, such as admission control and base station assignment; see [84,100,101] for details.
2.08.3.3.5 Algorithms for hybrid formulations
For a scalar IC, Chiang et al. [102] proposed to use a technique called geometric programming (GP) to find an approximate solution to the WSRM problem with QoS constraint. They showed that after approximating the rate function ![]() by
by ![]() , the WSRM problem becomes a GP and can be solved efficiently. Moreover, with this approximation, the resource allocation problem falls into the family of problems considered in [32,41], which can be transformed into equivalent convex optimization problems. For this family of problems, fast and distributed algorithms based on certain Newton-type iteration have been proposed in [103].
, the WSRM problem becomes a GP and can be solved efficiently. Moreover, with this approximation, the resource allocation problem falls into the family of problems considered in [32,41], which can be transformed into equivalent convex optimization problems. For this family of problems, fast and distributed algorithms based on certain Newton-type iteration have been proposed in [103].
However, this approximation is not so useful in practice because (1) it is accurate only in high SINR region; (2) it always leads to a solution for which all links are active. The latter feature is undesirable because having all links active can be highly suboptimal when interference is strong. In fact, the main difficulty with WSRM is precisely how to identify which links should be shut off, an important option that is excluded by the GP approximation approach.
Recognizing such problems, the same authors further proposed in [102] a successive convex approximation (GP-SCA) method that aims at finding a stationary solution to the original WSRM problem. In particular, let ![]() ,
, ![]() and
and ![]() , for
, for ![]() . Utilizing the arithmetic-geometric mean inequality, the users’ rate functions can be lower-approximate as
. Utilizing the arithmetic-geometric mean inequality, the users’ rate functions can be lower-approximate as
![]() (8.78)
(8.78)
 (8.79)
(8.79)
![]() (8.80)
(8.80)
This lower bound is again concave (upon performing a log-transformation), and it is tight when ![]() . The QoS constrained WSRM problem with the approximated objective (8.79) can be again solved by a GP. A similar alternating procedure as the one we have introduced for the SCALE algorithm can be used to compute a stationary solution to the WSRM problem with QoS constraint.
. The QoS constrained WSRM problem with the approximated objective (8.79) can be again solved by a GP. A similar alternating procedure as the one we have introduced for the SCALE algorithm can be used to compute a stationary solution to the WSRM problem with QoS constraint.
Algorithms based on global optimization
There are a number of attempts to find globally optimal solution for the WSRM problem. However, these algorithms are all based on implicit enumeration (not surprising in light of the complexity results in Section 2.08.3.2). As a result, they can only solve small scale problems and are unlikely to be suitable for implementation in practical applications. However, this does not mean that global optimization algorithms for WSRM are useless. For one thing, they can be a valuable tool to benchmark various low-complexity suboptimal approaches for resource allocation (e.g., those described earlier in this section).
For a scalar IC, Qian et al. [104] proposed to use an existing algorithm [105,106] for nonconvex fractional programming to find the global optimal solution for the hybrid problem (8.45). Specifically, introducing a set of auxiliary variable ![]() , the scalar WSRM problem with SINR constraint can be formulated into the following equivalent form
, the scalar WSRM problem with SINR constraint can be formulated into the following equivalent form
 (8.81)
(8.81)

This reformulated problem has a concave objective (upon a log transformation), and a nonconvex feasible set ![]() . The global optimization algorithm of [105,106] solves the reformulated problem via some convex optimization problems over a sequence shrinking convex sets
. The global optimization algorithm of [105,106] solves the reformulated problem via some convex optimization problems over a sequence shrinking convex sets ![]() . The worst case complexity of this algorithm is exponential.
. The worst case complexity of this algorithm is exponential.
Several other global optimization methods have been proposed to solve the utility maximization problems for more general IC models. For example, [107–110] considered the parallel IC model, and [111] treated the two user-MISO IC model. In particular, the algorithm proposed in [110] utilized the dc structure (8.63) of the weighted sum rate function, and applied a branch-and-bound (BB) algorithm to find global optimal solution to the WSRM problem. Due to their exponentially increasing complexity, these algorithms are only suitable for benchmarking resource allocation algorithm for networks with relatively small number of links. For example, the work of [104,107] compared their global algorithms for a small parallel IC with ![]() , and a scalar IC with K up to 10.
, and a scalar IC with K up to 10.
An important open problem is how to develop efficient algorithms (suitable for large networks) that can find (provably) tight upper bounds for the system performance.
2.08.3.3.6 Algorithms for robust resource allocation
All of the aforementioned resource management schemes require perfect channel state information (CSI) at the transmitter side. However, in practice the CSI obtained at the transmitter is susceptible to various sources of uncertainties such as quantization error, channel estimation error or channel aging. These uncertainties may significantly degrade the performance of resource allocation schemes that are designed using perfect CSI. As a result, robust designs are needed for practical resource management.
Several recent contributions considered robust linear transmitter design in a MISO channel with a single transmitter and multiple receivers. Let ![]() and
and ![]() denote the true channel and the estimated channel between the transmitter and the k-th receiver, respectively. Let
denote the true channel and the estimated channel between the transmitter and the k-th receiver, respectively. Let ![]() denote the uncertainty set of channel
denote the uncertainty set of channel ![]() , which is the set of possible values that
, which is the set of possible values that ![]() may take after obtaining the estimated channel
may take after obtaining the estimated channel ![]() . Consider the following specific form of uncertainty set
. Consider the following specific form of uncertainty set
![]() (8.82)
(8.82)
where ![]() is the vector of estimation error and
is the vector of estimation error and ![]() is the uncertainty bound. One of the most popular formulation of the robust design is the following QoS constrained min power problem
is the uncertainty bound. One of the most popular formulation of the robust design is the following QoS constrained min power problem
 (8.83)
(8.83)

This formulation aims at minimizing the total transmission power while ensuring that the SINR constraints are satisfied under all possible channel uncertainties. Define

In [112] problem (8.83) has been reformulated into the following semi-infinite SOCP
![]() (8.84)
(8.84)
 (8.85)
(8.85)
This reformulation is a convex restriction to the original problem (8.83) in that the the complex magnitude ![]() in the constraint is replaced by the lower bound equal to its real part
in the constraint is replaced by the lower bound equal to its real part ![]() . However, due to the presence of
. However, due to the presence of ![]() on both sides of the SOC constraint (8.85), this reformulated problem is still difficult to solve. A conservative design is then developed by assuming independent uncertainties for
on both sides of the SOC constraint (8.85), this reformulated problem is still difficult to solve. A conservative design is then developed by assuming independent uncertainties for ![]() on the left and right hand sides of each constraint in (8.85). With such an assumption, problem (8.85) can be transformed to the following SDP problem and solved efficiently using standard interior point method.
on the left and right hand sides of each constraint in (8.85). With such an assumption, problem (8.85) can be transformed to the following SDP problem and solved efficiently using standard interior point method.
![]() (8.86)
(8.86)

Instead of solving (8.84) by the SDP relaxation (8.86), Vucic and Boche [113] proposed to solve (8.84) by: (1) directly applying the ellipsoid method from convex optimization and (2) approximating (8.84) by a robust MSE constrained min power problem. Let ![]() denote the scalar receive filter used at receiver k. Let
denote the scalar receive filter used at receiver k. Let ![]() denote the unit vector with its k-th element being 1. Define the MSE of the k-th user as
denote the unit vector with its k-th element being 1. Define the MSE of the k-th user as
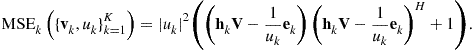 (8.87)
(8.87)
The robust MSE constrained min power problem is given as
 (8.88)
(8.88)
![]() (8.89)
(8.89)
This problem is convex and can be equivalently formulated as an SDP problem and efficiently solved by interior point methods. It is shown in [113] that both the ellipsoid method approach and the robust MSE constrained reformulation approach achieve better performance than the SDP relaxation (8.86) in terms of various system level performance measures.
As noted earlier, the original min power SINR constrained problem (8.83) is not equivalent to the formulation (8.84), as the latter replaces the nonlinear term ![]() by a linear lower bound
by a linear lower bound ![]() . Implicit in this reformulation is the additional requirement that
. Implicit in this reformulation is the additional requirement that ![]() is positive for all the channels
is positive for all the channels ![]() . Recently, the authors of [114] showed that the direct SDP relaxation of the original problem (8.83) is actually tight as long as the size of the uncertainty set is sufficiently small. This implies that robust resource allocation for MISO channels can be solved to global optimality in polynomial time, provided the channel uncertainty is small. More precisely, define
. Recently, the authors of [114] showed that the direct SDP relaxation of the original problem (8.83) is actually tight as long as the size of the uncertainty set is sufficiently small. This implies that robust resource allocation for MISO channels can be solved to global optimality in polynomial time, provided the channel uncertainty is small. More precisely, define ![]() , and
, and ![]() , the problem (8.83) can be equivalently reformulated as
, the problem (8.83) can be equivalently reformulated as
 (8.90)
(8.90)
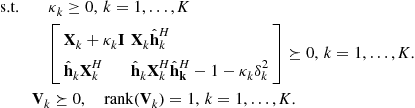
When the rank constraints are dropped, this problem becomes the following SDP and can be efficiently solved
 (8.91)
(8.91)
Let ![]() . Let
. Let ![]() denote the above SDP problem when the bounds on the uncertainty set is
denote the above SDP problem when the bounds on the uncertainty set is ![]() . Let
. Let ![]() denote the optimal value of the the problem
denote the optimal value of the the problem ![]() . Suppose that for some choice of uncertainty bounds
. Suppose that for some choice of uncertainty bounds ![]() , the problem
, the problem ![]() is strictly feasible. Define the set
is strictly feasible. Define the set
 (8.92)
(8.92)
Then, according to Song et al. [114], for any vector of uncertainty bounds ![]() , the problem
, the problem ![]() is feasible. Moreover, its optimal solution
is feasible. Moreover, its optimal solution ![]() satisfies
satisfies ![]() , and it must be the optimal solution of the original problem (8.83).
, and it must be the optimal solution of the original problem (8.83).
Alternative system level objectives and constraints can be considered to result in different formulations of the robust resource allocation problem. For example, Ref. [115] considered robust design for both the averaged sum MSE minimization problem and the worst case sum MSE minimization problem. Ref. [116] considered the worst case weighted sum rate maximization problem and min-rate maximization problem. The authors of [117] considered the robust beamformer design in a cognitive radio network in which there are additional requirements that the transmitter’s interference to the primary users should be kept under a prescribed level. However, most of the above cited works focus on robust design in a single cell network with a single transmitter. The extensions to the general MIMO IC/IBC/IMAC will be interesting.
To close this section, we summarize the properties of most of the algorithms discussed in this section in Table 8.4. These algorithms usually admit certain forms of decentralized implementation, in which the computational loads are distributed to different entities in the network. We emphasize that the per-iteration computational complexity and the amount of message exchanges are important characteristics for practical implementation of these distributed algorithms. Efficient computation ensures real time implementation, while fewer number of message exchanges per iteration implies less signaling overhead. In Table 8.4, these characteristics are listed for each of the algorithms. We note that the computational complexity and the required message exchanges are calculated on a per iteration basis, where in one iteration each user ![]() completes one update. Also note that in Table 8.4, the variable T in ICBF, SCALE-Dual, and M-IWF represents the number of inner iterations needed; the variable
completes one update. Also note that in Table 8.4, the variable T in ICBF, SCALE-Dual, and M-IWF represents the number of inner iterations needed; the variable ![]() in Bisection-SOCP and SCALE-GP represents the required precision for their respective inner solutions; the variable t in MAPEL represents the iteration index; the variable B in BB and ISB represents the maximum number of transmitted bits allowed for each subchannel; the variable C in the BB algorithm represents its computation overhead.
in Bisection-SOCP and SCALE-GP represents the required precision for their respective inner solutions; the variable t in MAPEL represents the iteration index; the variable B in BB and ISB represents the maximum number of transmitted bits allowed for each subchannel; the variable C in the BB algorithm represents its computation overhead.
2.08.4 Distributed resource allocation in interference channel
Most of the algorithms introduced in the previous section are either centralized or require certain level of user coordination. Such coordination may be costly in infrastructure based networks, and is often infeasible for fully distributed networks. In this section we discuss fully distributed resource allocation algorithms that require no user coordination.
2.08.4.1 Game theoretical formulations
In scenarios where users cannot exchange information explicitly, it is no longer possible to allocate resources using the maximizer of a system wide utility function. Instead, we need to rely on alternative solution concepts for distributed resource allocation. One such concept that is particularly useful in our context is the renowned notion of Nash equilibrium (NE) for a noncooperative game; see [118,119], and the Yale Open Course online. In a noncooperative game, there are a number of players, each seeking to maximize its own utility function by choosing a strategy from an individual strategy set. However, the utility of one player depends on not only the strategy of its own, but also those of others in the system. As a result, when players have conflicting utility functions, there is usually no joint player strategy that will simultaneously maximize the utilities of all players. For such a noncooperative game, a NE solution is defined as a tuple of joint player strategies in which no single player can benefit by changing its own strategy unilaterally.
Mathematically, a K-person noncooperative game in the strategic form is a three tuple ![]() , in which
, in which ![]() is the set of players of the game;
is the set of players of the game; ![]() is the joint strategic space of all the players, with
is the joint strategic space of all the players, with ![]() being player k’s individual strategy space;
being player k’s individual strategy space; ![]() , where
, where ![]() is user k’s utility function. In the above definition we have used
is user k’s utility function. In the above definition we have used ![]() to denote player k’s strategy,
to denote player k’s strategy, ![]() to denote the strategies of all remaining users. It is clear that player k’s strategy depends on its own strategy
to denote the strategies of all remaining users. It is clear that player k’s strategy depends on its own strategy ![]() as well as those of others
as well as those of others ![]() . A NE of the game
. A NE of the game ![]() is defined as the set of joint strategies of all the players
is defined as the set of joint strategies of all the players ![]() such that the following inequality is satisfied simultaneously for all players
such that the following inequality is satisfied simultaneously for all players ![]()
![]() (8.93)
(8.93)
Clearly at a NE, the system is stable as none of the players has any intention to switch to a different strategy. We define a best response function for each player in the game, as its best strategy when all other players have their strategies fixed
![]() (8.94)
(8.94)
Using this definition, a NE of the game ![]() can be alternatively defined as
can be alternatively defined as
![]() (8.95)
(8.95)
Figure 8.12 is an illustration of the NE point of a game with 2-player and affine best response functions. This figure also shows how a sequence of best response may enable the players to approach the NE.

Figure 8.12 Illustration of the Nash Equilibrium (NE) of a 2-user scalar game. This figure also shows the process of a sequence of best responses that reach the NE. The function ![]() represents user k’s best response function. Suppose both users initially choose 0. User 2 acts first and chooses point A which is its best response, User 1 acts next and chooses its best response point B. User 2 acts again and chooses point C. Continuing iteratively in this fashion, the NE will be reached in the limit.
represents user k’s best response function. Suppose both users initially choose 0. User 2 acts first and chooses point A which is its best response, User 1 acts next and chooses its best response point B. User 2 acts again and chooses point C. Continuing iteratively in this fashion, the NE will be reached in the limit.
Let us illustrate the notion of NE in our 2-user scalar IC model (8.14). Suppose these two users are the players of a game, and their strategy spaces are ![]() . Assume that the users’ utility functions are their maximum transmission rates defined in (8.18). Thus, for this example, user 1’s best response function admits a particular simple expression
. Assume that the users’ utility functions are their maximum transmission rates defined in (8.18). Thus, for this example, user 1’s best response function admits a particular simple expression
 (8.96)
(8.96)
This says that regardless of user 2’s transmission strategy, user 1 will transmit with full power. The same can be said about user 2. Consequently, the only NE of this game is the transmit power tuple ![]() . Obviously, assuming that each user is indeed selfish and they intend to maximize their own utility, the NE point
. Obviously, assuming that each user is indeed selfish and they intend to maximize their own utility, the NE point ![]() can be implemented without any explicit coordination between the users. Now let us assess the efficiency of such power allocation scheme in terms of system sum rate. In Figures 8.13 and 8.14, we plot the rate region boundary and the NE points for different interference levels. We see that when interference is low, the NE corresponds exactly to the maximum sum rate point. However, when interference is strong, the NE scheme is inferior to the time sharing scheme in which the users transmit with full power in an orthogonal and interference free fashion (e.g., TDMA or FDMA). Nonetheless, it should be pointed out that the NE point can be reached without user coordination, while the time sharing scheme requires the users to synchronize their transmissions.
can be implemented without any explicit coordination between the users. Now let us assess the efficiency of such power allocation scheme in terms of system sum rate. In Figures 8.13 and 8.14, we plot the rate region boundary and the NE points for different interference levels. We see that when interference is low, the NE corresponds exactly to the maximum sum rate point. However, when interference is strong, the NE scheme is inferior to the time sharing scheme in which the users transmit with full power in an orthogonal and interference free fashion (e.g., TDMA or FDMA). Nonetheless, it should be pointed out that the NE point can be reached without user coordination, while the time sharing scheme requires the users to synchronize their transmissions.

Figure 8.13 An illustration of the efficiency of the NE for 2-user IC when the interference is weak. ![]() ,
, ![]() ,
, ![]() . At point A and C, a single user transmits using full power; at the NE point, both users transmit using full power.
. At point A and C, a single user transmits using full power; at the NE point, both users transmit using full power.

Figure 8.14 An illustration of the inefficiency of the NE for 2-user IC when the interference is strong. ![]() ,
, ![]() ,
, ![]() . At point A and C, a single user transmits using full power; at the NE point, both users transmit using full power.
. At point A and C, a single user transmits using full power; at the NE point, both users transmit using full power.
We refer the readers tothe September 2009 issue of IEEE Signal Processing Magazine for the applications of game theory to wireless communication and signal processing.
2.08.4.2 Distributed resource allocation for interference channels
Early works on distributed physical layer resource allocation in wireless networks largely deal with the scalar IC models. Sarayda et al. [120,121] and Goodman and Mandayam [122] are among the first to cast the general scalar power control problem in a game theoretic framework. They proposed to quantify the tradeoff between the users’ QoS requirements and energy consumption by a utility function in the form:
![]() (8.97)
(8.97)
where ![]() is user k’s fixed transmission rate, and
is user k’s fixed transmission rate, and ![]() is a function of user k’s SINR that characterizes its bit error rate (BER). They showed that any NE point is inefficient in the Pareto sense, i.e., it is possible to increase the utility of some of the terminals without hurting any other terminal. To improve the efficiency of the power control game, they proposed to charge the users with a price that is proportional to their transmit powers. Specifically, each users’ utility function now becomes
is a function of user k’s SINR that characterizes its bit error rate (BER). They showed that any NE point is inefficient in the Pareto sense, i.e., it is possible to increase the utility of some of the terminals without hurting any other terminal. To improve the efficiency of the power control game, they proposed to charge the users with a price that is proportional to their transmit powers. Specifically, each users’ utility function now becomes ![]() , where
, where ![]() is a positive scalar that can be appropriately chosen by the system operator. They showed that this modified game always admits a NE, and proposed an algorithm that allows the users to reach one of the NEs by adapting their transmit powers in the best response fashion. Meshkati et al. [123,124] extended the above works to the multi-carrier data network. They defined the utility function for each user as
is a positive scalar that can be appropriately chosen by the system operator. They showed that this modified game always admits a NE, and proposed an algorithm that allows the users to reach one of the NEs by adapting their transmit powers in the best response fashion. Meshkati et al. [123,124] extended the above works to the multi-carrier data network. They defined the utility function for each user as
![]() (8.98)
(8.98)
where the function ![]() represents the BER of user k, and it incorporates the underlying structure of different linear receivers. However, such multi-carrier power control game is more complicated than the scalar power control game introduced early, and in certain network configurations it is possible that no NE exists (see [123]).
represents the BER of user k, and it incorporates the underlying structure of different linear receivers. However, such multi-carrier power control game is more complicated than the scalar power control game introduced early, and in certain network configurations it is possible that no NE exists (see [123]).
An alternative approach in distributed power control is to directly optimize the individual users’ transmission rates. Consider a K-user N-channel parallel IC model. Assume that each user ![]() is interested in maximizing its transmission rate, and again assume that its total transmission power budget is
is interested in maximizing its transmission rate, and again assume that its total transmission power budget is ![]() . Then the users’ utility functions as well as their feasible spaces can be expressed as
. Then the users’ utility functions as well as their feasible spaces can be expressed as
 (8.99)
(8.99)
 (8.100)
(8.100)
Fixing ![]() , user k’s best response solution
, user k’s best response solution ![]() is the classical water-filling (WF) solution
is the classical water-filling (WF) solution
 (8.101)
(8.101)
where ![]() is the dual variable ensuring the sum power constraint, and the operator
is the dual variable ensuring the sum power constraint, and the operator ![]() . Figure 8.15 illustrates the WF solution for user k. We note that in order to compute the WF solution, user k needs to know the terms
. Figure 8.15 illustrates the WF solution for user k. We note that in order to compute the WF solution, user k needs to know the terms ![]() , which is simply the set of noise-plus-interference (NPI) levels on all its channels. They can be measured locally at its receiver. We refer to this game as a WF game.
, which is simply the set of noise-plus-interference (NPI) levels on all its channels. They can be measured locally at its receiver. We refer to this game as a WF game.
Yu et al. [60] is the first to formulate the distributed power control problem as a WF game. The authors proposed an iterative water-filling algorithm (IWFA) in which the following two steps are performed iteratively:
Variations of the IWFA algorithm allow the users to update using different schedules. The following three update schemes have been proposed: (a) simultaneous update, in which all the users update their power in each iteration, see [60,125]; (b) sequential update, in which a single user updates in each iteration, see [125,126]; (c) asynchronous update, in which a random fraction of users update in each iteration, and they are allowed to use outdated information in their computation, see [127]. Regardless of the specific update schedule used, the IWFA algorithm is a distributed algorithm because only local NPI measurements are needed for the users to perform their independent power update.
The properties of the WF game as well as the convergence conditions of the IWFA have been extensively studied. The original work has only provided sufficient conditions for the convergence of the IWFA in a 2-user network. Subsequent works such as [125,126,128–130] generalized this result to networks with arbitrary number of users. Luo and Pang [126] characterized the NE of the water-filling game as the solution to the following affine variational inequality (AVI)
![]() (8.102)
(8.102)
where ![]() is a block partitioned matrix with its
is a block partitioned matrix with its ![]() th block defined as
th block defined as ![]() . Using the AVI characterization (8.102), they also showed that the sequential version of the IWFA corresponds to the classical projection algorithm whose convergence to the unique NE of the water-filling game is guaranteed if the following contraction condition is satisfied
. Using the AVI characterization (8.102), they also showed that the sequential version of the IWFA corresponds to the classical projection algorithm whose convergence to the unique NE of the water-filling game is guaranteed if the following contraction condition is satisfied
![]() (8.103)
(8.103)
where ![]() and
and ![]() is the strictly lower and strictly upper triangular part of a
is the strictly lower and strictly upper triangular part of a ![]() matrix
matrix ![]() given by
given by
 (8.104)
(8.104)
Also using the AVI characterization (8.102), the authors of [129,125] further proved that the condition
![]() (8.105)
(8.105)
is sufficient for the convergence of the IWFA as well as the uniqueness of the NE. We refer the readers to [131] for a detailed comparison of various conditions for the convergence of the IWFA. It is worth noticing that all the sufficient conditions for the convergence of IWFA require that the interference among the users are weak. For example, a sufficient condition for (8.105) is
![]() (8.106)
(8.106)
where ![]() is a set of constant scalars. Intuitively, this condition says that at the receiver of each user
is a set of constant scalars. Intuitively, this condition says that at the receiver of each user ![]() , the power of the useful signal should be larger than the power of total interference. When the interference is strong, IWFA diverges. Leshem and Zehavi [132] provided an example in which all forms of IWFA diverge, regardless of their update schedules. We remark that extending the IWFA so that it converges in less stringent conditions that do not require the interference to be weak is still an open problem. Without any algorithmic modifications, the standard IWFA is only known to converge [126] when the crosstalk coefficients are symmetric
, the power of the useful signal should be larger than the power of total interference. When the interference is strong, IWFA diverges. Leshem and Zehavi [132] provided an example in which all forms of IWFA diverge, regardless of their update schedules. We remark that extending the IWFA so that it converges in less stringent conditions that do not require the interference to be weak is still an open problem. Without any algorithmic modifications, the standard IWFA is only known to converge [126] when the crosstalk coefficients are symmetric
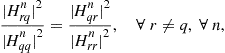
regardless the interference levels.
The IWFA has been recently generalized to MIMO IC model. In the MIMO WF game, the strategy of each user ![]() is its transmission covariance matrix
is its transmission covariance matrix ![]() . The rate utility function and strategy set for user k can be expressed as
. The rate utility function and strategy set for user k can be expressed as
 (8.107)
(8.107)
![]() (8.108)
(8.108)
In this case, each user k’s best response ![]() is again a water-filling solution, see [133]. Arslan et al. [134] suggested that in each iteration, the users’ covariance can be updated as
is again a water-filling solution, see [133]. Arslan et al. [134] suggested that in each iteration, the users’ covariance can be updated as
![]() (8.109)
(8.109)
where ![]() is a set of constants that satisfy
is a set of constants that satisfy ![]() and
and ![]() . They claimed that their algorithm converges when the interference is weak, but no specific conditions are given. This work has been generalized by Scutari et al. [131,135], in which rigorous conditions for the convergence of the MIMO IWFA have been derived. In particular, consider a MIMO network in which
. They claimed that their algorithm converges when the interference is weak, but no specific conditions are given. This work has been generalized by Scutari et al. [131,135], in which rigorous conditions for the convergence of the MIMO IWFA have been derived. In particular, consider a MIMO network in which ![]() and the direct link channel matrices
and the direct link channel matrices ![]() are all nonsingular. Define a
are all nonsingular. Define a ![]() matrix
matrix ![]() as
as
 (8.110)
(8.110)
Then the condition ![]() is sufficient for the convergence of the sequential/simultaneous/asynchronous MIMO IWFA. This condition is again a weak interference condition, and future work is needed to extend the MIMO IWFA to work in networks without this restriction. We refer the readers to web pages of Yu, Palomar, andPangfor other works related to the WF games and IWFA.
is sufficient for the convergence of the sequential/simultaneous/asynchronous MIMO IWFA. This condition is again a weak interference condition, and future work is needed to extend the MIMO IWFA to work in networks without this restriction. We refer the readers to web pages of Yu, Palomar, andPangfor other works related to the WF games and IWFA.
The above parallel and MIMO WF games have been extended in several directions. A series of recent works considered the robustness issue in a WF games. For instance, Gohary et al. [136] considered the WF game in the presence of a jammer. Let us denote user 0 as the jammer and denote its transmission power as ![]() . The rate utility function of a normal user k (
. The rate utility function of a normal user k (![]() ) becomes
) becomes
 (8.111)
(8.111)
Suppose the jammer’s objective is to minimize the utility of the whole system. This can be reflected by its utility function and the strategy set
 (8.112)
(8.112)
 (8.113)
(8.113)
Gohary et al. [136] proposed a generalized IWFA (GIWFA) algorithm in which the normal users and the jammer all selfishly maximize their respective utility functions. Notice that the selfish maximization problems are all convex. The convergence condition for the GIWFA is
![]() (8.114)
(8.114)
where the matrix ![]() is defined in (8.104), and
is defined in (8.104), and ![]() and
and ![]() are constants related to the system parameters. Clearly this condition is more restrictive than those of the original IWFA, for example the condition (8.103). This is partly because the presence of the jammer introduces uncertainty to the NPI that each normal user experiences.
are constants related to the system parameters. Clearly this condition is more restrictive than those of the original IWFA, for example the condition (8.103). This is partly because the presence of the jammer introduces uncertainty to the NPI that each normal user experiences.
Uncertainty of the NPI is also caused by events such as sudden changes in the number of users in the system or errors of interference measurement at the receivers. Setoodeh and Haykin [137] seek a formulation that takes into consideration the worst case NPI errors. Let ![]() denote the power of NPI that user k should have experienced on channel n if no measurement errors occur. Let
denote the power of NPI that user k should have experienced on channel n if no measurement errors occur. Let ![]() be the measured NPI value, with
be the measured NPI value, with ![]() representing the NPI uncertainty. Let
representing the NPI uncertainty. Let ![]() and suppose it is bounded, i.e.,
and suppose it is bounded, i.e., ![]() for some
for some ![]() . In this robust WF game, the objectives of the users are to maximize their worst case transmission rate. In other words, user ks utility function can be expressed as
. In this robust WF game, the objectives of the users are to maximize their worst case transmission rate. In other words, user ks utility function can be expressed as
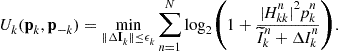 (8.115)
(8.115)
This formulation trades performance in favor of robustness, thus the equilibrium solution obtained is generally less efficient than that of the original IWFA. In [138], an averaged version of IWFA was proposed which converges when the error of the NPI ![]() satisfies certain conditions. In [139], the authors provided a probabilistically robust IWFA to deal with the quantization errors of the NPI at the receiver of each user. In this algorithm, users allocate their powers to maximize their total rate for a large fraction of the error realization.
satisfies certain conditions. In [139], the authors provided a probabilistically robust IWFA to deal with the quantization errors of the NPI at the receiver of each user. In this algorithm, users allocate their powers to maximize their total rate for a large fraction of the error realization.
Another thread of works such as [58,140–143] generalized the original WF game and the IWFA to interfering cognitive radio networks (CRN). In a CRN, the secondary users (SUs) are allowed to use the spectrum that is assigned to the primary users (PUs) as long as the SUs do not create excessive interference to the primary network. Suppose the secondary network is a K-user N-channel parallel IC. Let ![]() denote the set of PUs in the network. Let
denote the set of PUs in the network. Let ![]() denote the channel gain from SU k to PU q on channel n. The following aggregated interference constraints are imposed on the secondary network (these constraints are also referred to as the interference temperature-constraints, see [144,145])
denote the channel gain from SU k to PU q on channel n. The following aggregated interference constraints are imposed on the secondary network (these constraints are also referred to as the interference temperature-constraints, see [144,145])
 (8.116)
(8.116)
where ![]() represents the maximum aggregated interference allowed at the receiver of PU q on channel n. The original WF algorithm needs to be properly modified to strictly enforce these interference constraints in the equilibrium. Xie et al. [143] formulated the power allocation problem in this CRN as a competitive market model. In this model, each channel has a fictitious price per unit power, and the users must purchase the transmission power on each channel to maximize their data rates. Scutari et al. [135,146] systematically studied the WF game with interference constraints. For each primary user q, they introduced a set of interference prices
represents the maximum aggregated interference allowed at the receiver of PU q on channel n. The original WF algorithm needs to be properly modified to strictly enforce these interference constraints in the equilibrium. Xie et al. [143] formulated the power allocation problem in this CRN as a competitive market model. In this model, each channel has a fictitious price per unit power, and the users must purchase the transmission power on each channel to maximize their data rates. Scutari et al. [135,146] systematically studied the WF game with interference constraints. For each primary user q, they introduced a set of interference prices ![]() . Each SU is charged for their contribution of total interference at PUs’ receiver. Specifically, a SU k’s utility function and feasible set is defined as
. Each SU is charged for their contribution of total interference at PUs’ receiver. Specifically, a SU k’s utility function and feasible set is defined as
 (8.117)
(8.117)
 (8.118)
(8.118)
where ![]() is user k’s transmission rate. The NE of this interference-constrained WF game is the tuple
is user k’s transmission rate. The NE of this interference-constrained WF game is the tuple ![]() that satisfies the following conditions
that satisfies the following conditions

Scutari et al. [135,146] derived the conditions for the existence and uniqueness of the NE for this game. Introduce a ![]() matrix
matrix ![]()
 (8.119)
(8.119)
where ![]() . Then the condition
. Then the condition ![]() guarantees the uniqueness of the NE. A set of distributed algorithms that alternately update the users’ power allocation and the interference prices were proposed to reach the NE of this game. The MIMO generalization has been considered in [147], whereby both the SUs and PUs are equipped with multiple antennas. Another extension [142] considered the possibility that the SU-PU channels may be uncertain, and formulated a robust WF game that ensures the SU-PU interference constraints are met even in the worst case channel conditions.
guarantees the uniqueness of the NE. A set of distributed algorithms that alternately update the users’ power allocation and the interference prices were proposed to reach the NE of this game. The MIMO generalization has been considered in [147], whereby both the SUs and PUs are equipped with multiple antennas. Another extension [142] considered the possibility that the SU-PU channels may be uncertain, and formulated a robust WF game that ensures the SU-PU interference constraints are met even in the worst case channel conditions.
All the above mentioned WF games can be categorized as rate adaptive (RA) games, in which the users selfishly maximize their own data rates. One drawback of the RA formulation is that individual users have no QoS guarantees. Alternatively, a fixed margin (FM) formulation allows each user to minimize its transmission power while maintaining its QoS constraint. The FM formulation is more difficult to analyze due to the coupling of the users’ strategy spaces resulted from the QoS constraint. For the parallel IC model, the utility function and the strategy set for user k in a FM formulation can be expressed as
 (8.120)
(8.120)
![]() (8.121)
(8.121)
where ![]() is the rate target for user k. The solution to the individual users’ utility maximization problems, assuming the feasibility of the rate targets, is again a water-filling solution
is the rate target for user k. The solution to the individual users’ utility maximization problems, assuming the feasibility of the rate targets, is again a water-filling solution
 (8.122)
(8.122)
where ![]() is the water-level that is associated with user k’s rate constraint.
is the water-level that is associated with user k’s rate constraint.
A NE of this FM game (which is usually referred to as the generalized NE due to the coupling of the users’ strategy spaces) is defined as a power vector ![]() that satisfies
that satisfies
![]() (8.123)
(8.123)
Similar to the min-power QoS constrained formulation discussed in the previous section, the first thing we need to characterize for this FM game is the feasibility of a given set of rate targets. The following condition is among many of those that have been derived in [148] which guarantee the existence of a bounded power allocation achieving the given set of rate targets
 (8.124)
(8.124)
This condition is again a weak interference condition. The following condition is sufficient for the uniqueness of the (generalized) NE of the FM game
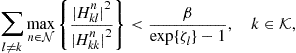 (8.125)
(8.125)
where ![]() is related to the set of given rate targets. This condition is also sufficient for the convergence of a FM-IWFA in which the users sequentially or simultaneously update their power using the WF solution. Algorithmic extension of this work to the CRN with interference constraints of the form (8.116) has been considered recently in [149]. It remains to see how the FM games and their theoretical properties (e.g., uniqueness of the NE, convergence of the FM-IWFA) can be extended to MIMO CRNs with interference constraints.
is related to the set of given rate targets. This condition is also sufficient for the convergence of a FM-IWFA in which the users sequentially or simultaneously update their power using the WF solution. Algorithmic extension of this work to the CRN with interference constraints of the form (8.116) has been considered recently in [149]. It remains to see how the FM games and their theoretical properties (e.g., uniqueness of the NE, convergence of the FM-IWFA) can be extended to MIMO CRNs with interference constraints.
We remark that the NE points of the various RA based WF games introduced in this section is generally inefficient, in the sense that the sum rate of the users is often smaller compared with that of the socially optimal solutions.1 In Figure 8.16, we illustrate such inefficiency of the NE in a parallel IC with ![]() and randomly generated channel coefficients. We plot the NE point of the WF game as well as the rate region boundary achieved by the SCALE algorithm. In order to improve the efficiency of the NE, user coordination must be incorporated into the original WF game. The pricing algorithms such as MDP, M-IWF or WMMSE introduced in the previous section are examples of such extensions. In those algorithms, system efficiency is improved due to explicit message exchange and cooperation among the users. Careful analysis is needed to identify the tradeoffs between the improvement of the system sum rate and the signaling overhead. Evidently, when the total number of users in the system is large, a complete cooperation of all users is too costly. An interesting problem is to decide how to partition the users into collaborative groups in a way that strike an optimal tradeoff between system performance and coordination overhead.
and randomly generated channel coefficients. We plot the NE point of the WF game as well as the rate region boundary achieved by the SCALE algorithm. In order to improve the efficiency of the NE, user coordination must be incorporated into the original WF game. The pricing algorithms such as MDP, M-IWF or WMMSE introduced in the previous section are examples of such extensions. In those algorithms, system efficiency is improved due to explicit message exchange and cooperation among the users. Careful analysis is needed to identify the tradeoffs between the improvement of the system sum rate and the signaling overhead. Evidently, when the total number of users in the system is large, a complete cooperation of all users is too costly. An interesting problem is to decide how to partition the users into collaborative groups in a way that strike an optimal tradeoff between system performance and coordination overhead.
2.08.5 Resource allocation via interference alignment
Theoretically, the optimal resource allocation for a MIMO interference channel is related to the characterization of the capacity region of an interference channel, i.e., determining the set of rate tuples that can be achieved by the users simultaneously. In spite of intensive research on this subject over the past three decades, the capacity region of interference channels is still unknown (even for small number of users). The lack of progress to characterize the capacity region of the MIMO interference channel has motivated researchers to derive various approximations of the capacity region. For example, the maximum total degrees of freedom (DoF) corresponds to the first order approximation of sum-rate capacity in the high SNR regime. Specifically, in a K-user interference channel, we define the degrees of freedom region as the following [21]:
 (8.126)
(8.126)
where ![]() is the capacity region and
is the capacity region and ![]() is the rate of user k. The total DoF in the system can be defined as the following:
is the rate of user k. The total DoF in the system can be defined as the following:
![]() (8.127)
(8.127)
Roughly speaking, the total DoF is the number of independent data streams that can be communicated in the channel without interference.
For various channel models, the DoF region or the total DoF have been characterized recently. In particular, for a point-to-point MIMO channel with M antennas at the transmitter and N antennas at the receiver, the total DoF is ![]() . Different approaches such as SVD precoder or V-BLAST can be used to achieve this DoF bound. For a 2-user MIMO fading interference channel with user k equipped with
. Different approaches such as SVD precoder or V-BLAST can be used to achieve this DoF bound. For a 2-user MIMO fading interference channel with user k equipped with ![]() transmit antennas and
transmit antennas and ![]() receive antennas (
receive antennas (![]() ), Jafar and Fakhereddin [151] proves that the maximum total DoF is
), Jafar and Fakhereddin [151] proves that the maximum total DoF is
![]() (8.128)
(8.128)
Therefore, for the case of ![]() , the total DoF in the system is the same as the single user case. In other words, we do not gain more DoF by increasing the number of users from one to two. Interestingly, if generic channel extensions (drawn from a continuous probability distribution) are allowed either across time or frequency, Cadambe and Jafar [21] showed that the total DoF is
, the total DoF in the system is the same as the single user case. In other words, we do not gain more DoF by increasing the number of users from one to two. Interestingly, if generic channel extensions (drawn from a continuous probability distribution) are allowed either across time or frequency, Cadambe and Jafar [21] showed that the total DoF is ![]() for a K-user MIMO interference channel, where M is the number of transmit/receive antennas per user. This surprising result implies that each user can effectively utilize half of the total system resources in an interference-free manner by aligning the interference at all receivers.2 Moreover, this total DoF can be achieved by using a carefully designed linear beamforming strategy.
for a K-user MIMO interference channel, where M is the number of transmit/receive antennas per user. This surprising result implies that each user can effectively utilize half of the total system resources in an interference-free manner by aligning the interference at all receivers.2 Moreover, this total DoF can be achieved by using a carefully designed linear beamforming strategy.
Mathematically, a linear beamforming strategy for a K-user MIMO IC can be described by the transmit beamforming matrices ![]() and the receive beamforming matrices
and the receive beamforming matrices ![]() . The receiver k estimates the transmitted data vector
. The receiver k estimates the transmitted data vector ![]() as follows
as follows
![]() (8.129)
(8.129)
where the power of the data vector ![]() is normalized such that
is normalized such that ![]() , and
, and ![]() is the estimate of
is the estimate of ![]() at the k-th receiver. The matrices
at the k-th receiver. The matrices ![]() and
and ![]() are the beamforming matrices at the k-th transmitter and receiver respectively, where
are the beamforming matrices at the k-th transmitter and receiver respectively, where ![]() (
(![]() ) is the number of antennas at transmitter k (respectively receiver k). Without channel extension, the linear interference alignment conditions can be described by the following zero-forcing conditions [156,157]
) is the number of antennas at transmitter k (respectively receiver k). Without channel extension, the linear interference alignment conditions can be described by the following zero-forcing conditions [156,157]
![]() (8.130)
(8.130)
![]() (8.131)
(8.131)
The first equation guarantees that all the interfering signals at receiver k lie in the subspace orthogonal to ![]() , while the second one assures that the signal subspace
, while the second one assures that the signal subspace ![]() has dimension
has dimension ![]() and is linearly independent of the interference subspace. Clearly, as the number of users K increases, the number of constraints on the beamformers
and is linearly independent of the interference subspace. Clearly, as the number of users K increases, the number of constraints on the beamformers ![]() increases quadratically in K, while the number of design variables in
increases quadratically in K, while the number of design variables in ![]() only increases linearly. This suggests the above interference alignment can not have a solution unless K or
only increases linearly. This suggests the above interference alignment can not have a solution unless K or ![]() is small.
is small.
If the interference alignment conditions (8.130) and (8.131) hold for some linear beamforming matrices ![]() , then transmitter k can use
, then transmitter k can use ![]() to send
to send ![]() independent data streams to receiver k (per channel use) without any interference. Thus,
independent data streams to receiver k (per channel use) without any interference. Thus, ![]() represents the DoF achieved by the k-th transmitter/receiver pair in the information theoretic sense of (8.126). In other words, the vector
represents the DoF achieved by the k-th transmitter/receiver pair in the information theoretic sense of (8.126). In other words, the vector ![]() in (8.130) and (8.131) represents the tuple of DoF achieved by linear interference alignment. Intuitively, the larger the values of
in (8.130) and (8.131) represents the tuple of DoF achieved by linear interference alignment. Intuitively, the larger the values of ![]() , the more difficult it is to satisfy the interference alignment conditions (8.130) and (8.131).
, the more difficult it is to satisfy the interference alignment conditions (8.130) and (8.131).
In principle, we can allocate resources by maximizing the total achievable DoF. In particular, for a specific channel realization ![]() , we need to find the beamforming matrices
, we need to find the beamforming matrices ![]() to maximize the total DoF while satisfying (8.130) and (8.131).
to maximize the total DoF while satisfying (8.130) and (8.131).

Unfortunately, according to Razaviyayn et al. [156], this problem is NP-hard. So we are led to find suboptimal solution for this problem. However, no efficient algorithms have been developed to approximately solve this problem at this point.
Instead of maximizing the total DoF, we can focus on a seemingly simpler problem: for a given channel realization ![]() and a fixed DoF tuple
and a fixed DoF tuple ![]() , check if there exist linear beamformers
, check if there exist linear beamformers ![]() satisfying the alignment conditions (8.130) and (8.131). Notice that the conditions (8.130) and (8.131) are quadratic polynomial equations, which are difficult to solve in general. However, if we fix either
satisfying the alignment conditions (8.130) and (8.131). Notice that the conditions (8.130) and (8.131) are quadratic polynomial equations, which are difficult to solve in general. However, if we fix either ![]() or
or ![]() , the quadratic equations become linear and can be solved via the linear least squares. This suggests the following alternating directions method for solving (8.130) and (8.131) (for a fixed
, the quadratic equations become linear and can be solved via the linear least squares. This suggests the following alternating directions method for solving (8.130) and (8.131) (for a fixed ![]() ):
):
Notice that the optimal solution ![]() for (8.132) is given by the eigen-vectors of
for (8.132) is given by the eigen-vectors of ![]() corresponding to the
corresponding to the ![]() -smallest eigen-values. The above algorithm is proposed first in [158] and later in [159], albeit from a different perspective. Obviously, this algorithm cannot converge if the DoF vector
-smallest eigen-values. The above algorithm is proposed first in [158] and later in [159], albeit from a different perspective. Obviously, this algorithm cannot converge if the DoF vector ![]() is not achievable. However, even if
is not achievable. However, even if ![]() is achievable, there has been no formal analysis that shows this alternating direction algorithm indeed will converge.
is achievable, there has been no formal analysis that shows this alternating direction algorithm indeed will converge.
The lack of formal convergence proof may not be surprising. In fact, according to [156], even checking the feasibility of (8.130) and (8.131) is NP-hard when each transmitter/receiver is equipped with at least three antennas. Hence, for a given channel realization, assigning DoFs to the users in a manner that ensures feasibility is not easy. However, when the number of antennas at each transmitter/receiver is at most two, the problem of checking feasibility is polynomial time solvable ([156]).
Now let us turn our attention to the generic solvability of the interference alignment problem (8.130) and (8.131). In other words, we focus on the existence of a beamforming solution to the quadratic polynomial equations (8.130) and (8.131) when the channel matrices are randomly generated. To this end, it is natural to count the number of scalar equations and the number of scalar variables in the conditions (8.130) and (8.131). It is tempting to conjecture that there is an interference alignment solution if and only if the number of constraints is no larger than the number of variables (see [157]). Recently, Razaviyayn et al. [160] and Bresler et al. [161] have settled this conjecture completely in one direction, and partially in the other direction. They derive a general condition, described below, that must be satisfied by any DoF tuple ![]() achievable through linear interference alignment.
achievable through linear interference alignment.
Let us denote the polynomial equations in (8.131) by the index set
![]()
The following result ([160,161]) provides an upper bound on the total achievable DoF when no channel extension is allowed. Consider a K-user flat fading MIMO interference channel where the channel matrices ![]() are generic (e.g., drawn from a continuous probability distribution). Assume no channel extension is allowed. Then any tuple of degrees of freedom
are generic (e.g., drawn from a continuous probability distribution). Assume no channel extension is allowed. Then any tuple of degrees of freedom ![]() that is achievable through linear interference alignment (8.130) and (8.131) must satisfy the following inequalities
that is achievable through linear interference alignment (8.130) and (8.131) must satisfy the following inequalities
![]() (8.133)
(8.133)
![]() (8.134)
(8.134)
![]() (8.135)
(8.135)
Roughly, the left hand side of (8.135) is equal to the number of independent scalar variables in (8.130) and (8.131) and the right hand side of (8.135) corresponds to the number of constraints in (8.130). Thus, the necessity of condition (8.135) for the existence of a feasible alignment scheme can be understood by counting the dimensions. However, a formal proof of this condition requires the use of field extension theory ([160]). We remark that condition (8.135) can be used to bound the total DoF achievable in a MIMO interference channel. In particular, the following upper bounds follow directly from condition (8.135).
a. In the case of ![]() for all k, interference alignment is impossible unless
for all k, interference alignment is impossible unless

b. In the case of ![]() , interference alignment requires
, interference alignment requires

which further implies

The principal assumption enabling the surprising result of [21] is that the channel extensions are exponentially long in ![]() and are generic (e.g., drawn from a continuous probability distribution). If no channel extensions are allowed, part (b) above shows that the total achievable DoF in a MIMO interference channel is bounded by a constant
and are generic (e.g., drawn from a continuous probability distribution). If no channel extensions are allowed, part (b) above shows that the total achievable DoF in a MIMO interference channel is bounded by a constant ![]() , regardless of how many users are present in the system. While this bound is an improvement over the single user case which has a maximum DoF of
, regardless of how many users are present in the system. While this bound is an improvement over the single user case which has a maximum DoF of ![]() , it is significantly weaker than the maximum achievable total DoF of
, it is significantly weaker than the maximum achievable total DoF of ![]() for a diagonal frequency selective (or time varying) interference channel with independent channel extensions. The latter grows linearly with the number of users in the system [21].
for a diagonal frequency selective (or time varying) interference channel with independent channel extensions. The latter grows linearly with the number of users in the system [21].
If channel extensions are restricted to have a polynomial length or are not generic, the total DoF for a MIMO interference channel is still largely unknown even for the Single-Input-Single-Output (SISO) interference channel. This is an interesting open problem. For the 3-user special case, Ref. [162] provided a characterization of the total achievable DoF as a function of the diversity.
Conversely, if all users have the same DoF d and the number of antennas ![]() are divisible by d for each k, then condition (8.135) for each subsystem of (8.130) and (8.131) is also sufficient for the feasibility of interference alignment for generic choice of channel coefficients (e.g., drawn from a continuous probability distribution). If in addition,
are divisible by d for each k, then condition (8.135) for each subsystem of (8.130) and (8.131) is also sufficient for the feasibility of interference alignment for generic choice of channel coefficients (e.g., drawn from a continuous probability distribution). If in addition, ![]() and
and ![]() for all k and
for all k and ![]() are divisible by d, then these results imply that interference alignment is achievable if and only if
are divisible by d, then these results imply that interference alignment is achievable if and only if ![]() . Moreover, Bresler et al. [161] considered the symmetric case with
. Moreover, Bresler et al. [161] considered the symmetric case with ![]() for all k, and proved that the feasibility of interference alignment in this case is equivalent to
for all k, and proved that the feasibility of interference alignment in this case is equivalent to ![]() , regardless of the divisibility of M by d. When K is odd and
, regardless of the divisibility of M by d. When K is odd and ![]() , then d divides M, so this result and Theorem 2 are in agreement. However, the case when K is even is not covered by Theorem 2.
, then d divides M, so this result and Theorem 2 are in agreement. However, the case when K is even is not covered by Theorem 2.
To summarize, the initial work [21] is exciting and suggests that it may be possible to allocate resources in a MIMO IC based on DoF. However, the complexity and design of the interference alignment schemes have presented several challenges to the practicality of this approach for resource allocation.
![]() For a given channel realization, to determine whether a given set of DoF tuple is achievable is NP-hard (i.e., exponential effort is likely to be required for large number of users).
For a given channel realization, to determine whether a given set of DoF tuple is achievable is NP-hard (i.e., exponential effort is likely to be required for large number of users).
![]() Without channel extensions, the average DoF per user is shown to be at most
Without channel extensions, the average DoF per user is shown to be at most ![]() , which is significantly smaller than
, which is significantly smaller than ![]() when there are a large number of independent channel extensions (see [21]). Here M is the number of antennas at each transmitter and receive. Notice that the average per user DoF of
when there are a large number of independent channel extensions (see [21]). Here M is the number of antennas at each transmitter and receive. Notice that the average per user DoF of ![]() approximately doubles that of the orthogonal approaches (e.g. TDMA or FDMA).
approximately doubles that of the orthogonal approaches (e.g. TDMA or FDMA).
![]() It requires too many channel extensions to reap the DoF benefit promised by Cadambe and Jafar [21].
It requires too many channel extensions to reap the DoF benefit promised by Cadambe and Jafar [21].
![]() It requires full CSI, which can be difficult for large networks.
It requires full CSI, which can be difficult for large networks.
![]() It often requires selecting a set of feasible DoFs for the users a priori, which is difficult.
It often requires selecting a set of feasible DoFs for the users a priori, which is difficult.
At this point, interference alignment appears most useful for a small system (e.g., 3–4 links) where a closed form interference alignment solution exists [21], and when using no or a small number of channel extensions. For a large network, direct maximization of the weighted sum-rate (or weighted sum utility maximization) seems to offer more potential for resource allocation and interference mitigation. For one thing, it requires the same amount of CSI, and yet can offer more sum-rate performance across all SNR regime than that of interference alignment. Moreover, it does not require selecting a DoF for each user in advance. As for future work, we suggest further investigation of the benefits of interference alignment for a small system with a few channel extensions.
Relevant Theory: Signal Processing Theory and Array Signal Processing
See Vol. 1, Chapter 3 Discrete-Time Signal and Systems
See Vol. 1, Chapter 12 Adaptive Filters
See Vol. 3, Chapter 19 Array Processing in the Face of Nonidealities
References
1. Cave M, Doyle C, Webb W. Essentials of Modern Spectrum Management. Cambridge University Press 2007.
2. Goldsmith A. Wireless Communications. New York: Combridge University Press; 2005.
3. FCC, Report of the spectrum efficiency working group, 2002. <http://www.fcc.gov/sptf/reports.html>.
4. Sahai A, Mishra M, Tandra R, Woyach K. Cognitive radios for spectrum sharing. IEEE Signal Process Mag. 2009;140–146.
5. 3GPP, Evolved Universal Terrestrial Radio Access (EUTRA) and Evolved Universal Terrestrial Radio Access Network (EUTRAN); overall description, (2011) 3GPP TS 36.300, V8.9.0.
6. Chandrasekhar V, Andrews J. Femtocell networks: a survey. IEEE Commun Mag. 2008;59–67.
7. Damnjanovic A, Montojo J, Wei Y, et al. A survey on 3GPP heterogeneous networks. IEEE Wireless Commun. 2011;18:10–21.
8. Foschini G, Karakayali K, Valenzuela R. Coordinating multiple antenna cellular networks to achieve enormous spectral efficiency. IEE Proc Commun. 2006;153:548–555.
9. Gesbert D, Hanly S, Huang H, Shamai S, Simeone O, Yu W. Multi-cell MIMO cooperative networks: a new look at interference. IEEE J Sel Areas Commun. 2010;28:1380–1408.
10. Gesbert D, Kiani S, Gjendemsj A, ien G. Adaptation, coordination, and distributed resource allocation in interference-limited wireless networks. Proc IEEE. 2007;95:2393–2409.
11. Khan F. LTE for 4G Mobile Broadband: Air Interface Technologies and Performance. Cambridge University Press 2009.
12. Martín-Sacristán D, Monserrat JF, Cabrejas-Peñuelas J, Calabuig D, Garrigas S, Cardona N. On the way towards fourth-generation mobile: 3GPP LTE and LTE-advanced. EURASIP J Wireless Commun Networks. 2009;4(1–4):10.
13. Sawahashi M, Kishiyama Y, Morimoto A, Nishikawa D, Tanno M. Coordinated multipoint transmission/reception techniques for LTE-advanced. IEEE Wireless Commun. 2010;17:26–34.
14. Cover TM, Thomas JA. Elements of Information Theory. second ed. Wiley 2005.
15. Han T, Kobayashi K. A new achievable rate region for the interference channel. IEEE Trans Inform Theory. 1981;27:49–60.
16. Etkin R, Tse D, Wang H. Gaussian interference channel capacity to within one bit. IEEE Trans Inform Theory 2008.
17. Carleial AB. A case where interference does not reduce capacity. IEEE Trans Inform Theory. 1975;21:569–570.
18. Sato H. The capacity of the Gaussian interference channel under strong interference. IEEE Trans Inform Theory. 1981;27:49–60.
19. Chung ST, Cioffi JM. The capacity region of frequency selective Gaussian interference channel under strong interference. IEEE Trans Commun. 2007;55:1812–1821.
20. Shang X, Chen B, Kramer G, Poor H. Capacity regions and sum-rate capacities of vector Gaussian interference channels. IEEE Trans Inform Theory. 2010;56:5030–5044.
21. Cadambe V, Jafar S. Interference alignment and degrees of freedom of the k-user interference channel. IEEE Trans Inform Theory. 2008;54:3425–3441.
22. Shang X, Chen B, Kramer G, Poor H. Noisy-interference sum-rate capacity of parallel Gaussian interference channels. IEEE Trans Inform Theory. 2011;57:210–226.
23. Shang X, Kramer G, Chen B. A new outer bound and the noisy-interference sum-rate capacity for Gaussian interference channels. IEEE Trans Inform Theory. 2009;55:689–699.
24. Hui JYN, Humblet PA. The capacity region of the totally asynchronous multiple-access channel. IEEE Trans Inform Theory. 1985;31:207–216.
25. Charafeddine M, Paulraj A. Maximum sum rates via analysis of 2-user interference channel achievable rates region. In: 43rd Annual Conference on Information Sciences and Systems. 2009;170–174.
26. Charafeddine M, Sezgin A, Paulraj A. Rate region frontiers for n-user interference channel with interference as noise. In: Proceddings of Annual Allerton Conference on Communications, Control and, Computing. 2007.
27. Hayashi S, Luo Z-Q. Spectrum management for interference-limited multiuser communication systems. IEEE Trans Inform Theory. 2009;55:1153–1175.
28. Jorswieck EA, Larsson EG. The MISO interference channel from a game-theoretic perspective: a combination of selfishness and altruism achieves pareto optimality. In: IEEE ICASSP. 2008;5364–5367.
29. Larsson E, Jorswieck E. Competition versus cooperation on the MISO interference channel. IEEE J Sel Areas Commun. 2008;26:1059–1069.
30. Jorswieck EA, Larsson EG, Danev D. Complete characterization of the pareto boundary for the MISO interference channel. IEEE Trans Signal Process. 2008;56:5292–5296.
31. Mo J, Walrand J. Fair end-to-end window-based congestion control. IEEE/ACM Trans Network. 2000;8:556–567.
32. Boche H, Naik S, Alpcan T. Characterization of convex and concave resource allocation problems in interference coupled wireless systems. IEEE Trans Signal Process. 2011;59:2382–2394.
33. Liu Y-F, Dai Y-H, Luo Z-Q. Coordinated beamforming for MISO interference channel: complexity analysis and efficient algorithms. IEEE Trans Signal Process. 2011;59:1142–1157.
34. Luo Z-Q, Zhang S. Dynamic spectrum management: complexity and duality. IEEE J Sel Top Signal Process. 2008;2:57–73.
35. Razaviyayn M, Hong M, Luo Z-Q. Linear transceiver design for a MIMO interfering broadcast channel achieving max-min fairness. In: 2011 Asilomar Conference on Signals, Systems, and Computers. 2011.
36. Ho ZKM, Gesbert D. Balancing egoism and altruism on interference channel: the MIMO case. In: 2010 IEEE International Conference on Communications (ICC). 2010;1–5.
37. Sadek M, Tarighat A, Sayed A. A leakage-based precoding scheme for downlink multi-user mimo channels. IEEE Trans Wireless Commun. 2007;6:1711–1721.
38. Shi S, Schubert M, Boche H. Downlink mmse transceiver optimization for multiuser MIMO systems: duality and sum-mse minimization. IEEE Trans Signal Process. 2007;55:5436–5446.
39. Ulukus S, Yates R. Iterative construction of optimum signature sequence sets in synchronous cdma systems. IEEE Trans Inform Theory. 2001;47:1989–1998.
40. Boche H, Schubert M. A calculus for log-convex interference functions. IEEE Trans Inform Theory. 2008;54:5469–5490.
41. Boche H, Schubert M. A unifying approach to interference modeling for wireless networks. IEEE Trans Signal Process. 2010;58:3282–3297.
42. Stanczak S, Wiczanowski M, Boche H. Distributed utility-based power control: objectives and algorithms. IEEE Trans Signal Process. 2007;55:5058–5068.
43. Garey MR, Johnson DS. Computers and Intractability: A guide to the Theory of NP-Completeness. San Francisco, USA: W.H. Freeman and Company; 1979.
44. Liu Y-F, Dai Y-H, Luo Z-Q. Max-min fairness linear transceiver design for a multi-user MIMO interference channel. In: Proceedings of the International Conference on Communicaitons 2011. 2011.
45. M. Razaviyayn, M. Hong, Z.-Q. Luo, Linear transceiver design for a MIMO interfering broadcast channel achieving max-min fairness, accepted by Signal Processing, special issue on sensor array processing, 2013.
46. Foschini G, Miljanic Z. A simple distributed autonomous power control algorithm and its convergence. IEEE Trans Veh Technol. 1993;42:641–646.
47. Zander J. Distributed cochannel interference control in cellular radio systems. IEEE Trans Veh Technol. 1992;41:305–311.
48. Zander J. Performance of optimal transmitter power control in cellular system. IEEE Trans Veh Technol. 1992;41:57–63.
49. Hanly SV, Tse D. Power control and capacity of spread spectrum wireless networks. Automatica. 1999;35:1987–2012.
50. Bengtsson M, Ottersten B. Optimal and Suboptimal Transmit Beamforming, Handbook of Antennas in Wireless Communications. CRC Press 2001.
51. Wiesel A, Eldar YC, Shamai(Shitz) S. Linear precoding via conic optimization for fixed MIMO receivers. IEEE Trans Signal Process. 2006;54:161–176.
52. Luo Z-Q, Yu W. An introduction to convex optimization for communications and signal processing. IEEE J Sel Areas Commun. 2006;24:1426–1438.
53. Luo Z-Q, Zhang S. Duality gap estimation and polynomial time approximation for optimal spectrum management. IEEE Trans Signal Process. 2009;57:2675–2689.
54. Yu W, Lui R. Dual methods for nonconvex spectrum optimization of multicarrier systems. IEEE Trans Commun. 2006;54:1310–1322.
55. Boyd S, Vandenberghe L. Convex Optimization. Cambridge University Press 2004.
56. Huang JW, Berry RA, Honig ML. Distributed interference compensation for wireless networks. IEEE J Sel Area Commun. 2006;24.
57. Wang F, Krunz M, Cui SG. Price-based spectrum management in cognitive radio networks. IEEE J Sel Top Signal Process. 2008;2.
58. Wu Y, Tsang DHK. Distributed multicahnnel power allocation algorithm for spectrum sharing coginitive radio networks. In: WCNC Proceedings, Las Vagas, USA. 2008.
59. Yu W. Multiuser water-filling in the presence of crosstalk. In: Information Theory and Applications, Workshop 07. 2007.
60. Yu W, Ginis G, Cioffi JM. Distributed multiuser power control for digital subscriber lines. IEEE J Sel Areas Commun. 2002;20:1105–1115.
61. Shi C, Berry RA, Honig ML. Monotonic convergence of distributed interference pricing in wireless networks. In: 2009;1619–1623. Proceedings of the 2009 IEEE international conference on Symposium on Information Theory. vol. 3.
62. Schmidt DA, Grundinger A, Utschick W, Honig ML. Distributed precoder optimization for interfering MISO channels. In: International ITG Workshop on Smart Antennas. 2008;285–290.
63. Shi C, Berry RA, Honig ML. Distributed interference pricing with MISO channels. In: 46th Annual Allerton Conference on Communication, Control, and Computing. 2008;539–546.
64. Shi C, Schmidt DA, Berry RA, Honig ML, Utschick W. Distributed interference pricing for the MIMO interference channel. IEEE Int Conf Commun. 2009;1–5.
65. Kim S-J, Giannakis G. Optimal resource allocation for MIMO Ad Hoc cognitive radio networks. In: 46th Annual Allerton Conference on Communication, Control, and, Computing. 2008;39–45.
66. Venturino L, Prasad N, Wang X. Coordinated linear beamforming in downlink multicell wireless networks. IEEE Trans Wireless Commun. 2010;9:1451–1461.
67. Schmidt D, Shi C, Berry R, Honig M, Utschick W. Distributed resource allocation schemes. IEEE Signal Process Mag. 2009;26:53–63.
68. Papandriopoulos J, Evans JS. SCALE: a low-complexity distributed protocol for spectrum balancing in multiuser DSL networks. IEEE Trans Inform Theory. 2009;55.
69. Tsiaflakis P, Diehl M, Moonen M. Distributed spectrum management algorithms for multiuser DSL networks. IEEE Trans Signal Process. 2008;56:4825–4843.
70. Christensen SS, Agarwal R, Carvalho ED, Cioffi JM. Weighted sum-rate maximization using weighted MMSE for MIMO-BC beamforming design. IEEE Trans Wireless Commun. 2008;7:4792–4799.
71. Schmidt D, Shi C, Berry RA, Honig ML, Utschick W. Minimum mean squared error interference alignment. In: Proceedings of Asilomar Conference, Pacific Grove, CA. 2009.
72. Shi Q, Razaviyayn M, Luo Z-Q, He C. An iteratively weighted MMSE approach to distributed sum-utility maximization for a MIMO interfering broadcast channel. In: 2011 IEEE International Conference on Acoustics, Speech and, Signal Processing (ICASSP). 2011;3060–3063.
73. Shi Q, Razaviyayn M, Luo Z-Q, He C. An iteratively weighted MMSE approach to distributed sum-utility maximization for a MIMO interfering broadcast channel. IEEE Trans Signal Process. 2011;59:4331–4340.
74. Yu W, Kwon T, Shin C. Multicell coordination via joint scheduling beamforming and power spectrum adaptation. In: Proceedings of IEEE International Conference on Computer Communication (INFOCOM). 2011.
75. Dahrouj H, Yu W. Coordinated beamforming for multicell multi-antenna wireless systems. IEEE Trans Wireless Commun. 2010;9:1748–1759.
76. Song B, Cruz R, Rao B. Network duality for multiuser MIMO beamforming networks and applications. IEEE Trans Commun. 2007;55:618–630.
77. Kim J, Cho D. A joint power and subchannel allocation scheme maximizing system capacity in dense femtocell downlink systems. In: IEEE 20th International Symposium on Personal, Indoor and Mobile Radio, Communications. 2009;1381–1385.
78. Venturino L, Prasad N, Wang X. An improved iterative water-filling algorithm for multi-cell interference mitigation in downlink OFDMA networks. In: ACSSC. 2007;1718–1722.
79. Venturino L, Prasad N, Wang X. Coordinated scheduling and power allocation in downlink multicell OFDMA networks. IEEE Trans Veh Technol. 2009;58:2835–2848.
80. M. Razaviyayn, H. Baligh, A. Callard, Z.-Q. Luo, Joint user grouping and transceiver design in a mimo interfering broadcast channel, submitted to IEEE Transactions on Signal Processing for publication.
81. Matskani E, Sidiropoulos N, Luo Z-Q, Tassiulas L. Convex approximation techniques for joint multiuser downlink beamforming and admission control. IEEE Trans Wireless Commun. 2008;7:2682–2693.
82. Matskani E, Sidiropoulos N, Luo Z-Q, Tassiulas L. Efficient batch and adaptive approximation algorithms for joint multicast beamforming and admission control. IEEE Trans Signal Process. 2009;57:4882–4894.
83. Hanly SV. An algorithm for combined cell-site selection and power control to maximize cellular spread spectrum capacity. IEEE J Sel Areas Commun. 1995;13:1332–1340.
84. Rashid-Farrokhi F, Tassiulas L, Liu K. Joint optimal power control and beamforming in wireless networks using antenna arrays. IEEE Trans Commun. 1998;46:1313–1324.
85. Yates RD, Huang CY. Integrated power control and base station assignment. IEEE Trans Veh Technol. 1995;44:1427–1432.
86. Gao L, Wang X, Sun G, Xu Y. A game approach for cell selection and resource allocation in heterogeneous wireless networks. In: The Proceeding of the SECON. 2011.
87. Hong M, Garcia A, Barrera J. Joint distributed AP selection and power allocation in cognitive radio networks. In: The Proceedings of the IEEE INFOCOM. 2011.
88. Perlaza SM, Belmega EV, Lasaulce S, Debbah M. On the base station selection and base station sharing in self-configuring networks. In: Proceedings of the Fourth International ICST Conference on Performance Evaluation Methodologies and Tools. 2009;71:1–71:10.
89. Hong M, Luo Z-Q. Joint linear precoder optimization and base station selection for an uplink MIMO network: a game theoretic approach. In: Proceedings of the IEEE ICASSP. 2012.
90. Sanjabi M, Razaviyayn M, Luo Z-Q. Optimal joint base station assignment and downlink beamforming for heterogeneous networks. In: 2012 IEEE ICASSP. 2012.
91. S.V. Hanly, Information capacity of radio networks, Ph.D. Dissertation, Cambridge University, 1993.
92. Boche H, Stanczak S. Convexity of some feasible qos regions and asymptotic behavior of the minimum total power in cdma systems. IEEE Trans Commun. 2004;52:2190–2197.
93. Stanczak S, Boche H. On the convexity of feasible qos regions. IEEE Trans Inform Theory. 2007;53:779–783.
94. Yates RD. A framework for uplink power control in cellular radio systems. IEEE J Sel Areas Commun. 1995;13:1341–1347.
95. Boche H, Schubert M. A superlinearly and globally convergent algorithm for power control and resource allocation with general interference functions. IEEE/ACM Trans Network. 2008;16:383–395.
96. Liu Y-F, Dai Y-H, Luo Z-Q. Joint power and admission control via linear programming deflation. In: Proceedings of the ICASSP. 2012.
97. Mitliagkas I, Sidiropoulos N, Swami A. Joint power and admission control for ad-hoc and cognitive underlay networks: convex approximation and distributed implementation. IEEE Trans Wireless Commun. 2011;10:4110–4121.
98. Ahmed M. Call admission control in wireless networks: a comprehensive survey. IEEE Commun Survey Tut. 2005;7:49–68.
99. Bengtsson M, Ottersten B. Optimal downlink beamforming using semidefinite optimization. In: Proceedings of the 37th Annual Allerton Conference. 1999.
100. Bengtsson M. Jointly optimal downlink beamforming and base station assignment. In: 2001;2961–2964. 2001 IEEE International Conference on Acoustics, Speech, and Signal Processing (ICASSP ’01). vol. 5.
101. Stridh R, Bengtsson M, Ottersten B. System evaluation of optimal downlink beamforming with congestion control in wireless communication. IEEE Trans Wireless Commun. 2006;5:743–751.
102. Chiang M, Tan CW, Palomar DP, O’Neill D, Julian D. Power control by geometric programming. IEEE Trans Wireless Commun. 2007;6:2640–2651.
103. Wiczanowski M, Stanczak S, Boche H. Providing quadratic convergence of decentralized power control in wireless networks–the method of min-max functions. IEEE Trans Signal Process. 2008;56:4053–4068.
104. Qian L, Zhang Y, Huang J. MAPEL: Achieving global optimality for a non-convex wireless power control problem. IEEE Trans Wireless Commun. 2009;8:1553–1563.
105. Frenck JBG, Schaible S. Fractional Programming. In: Handbook of Generalized Convexity and Generalized Monoticity. Springer 2006;335–386.
106. Phuong NTH, Tuy H. A unified monotonic approach to generalized linear fractional programming. J Global Optim. 2003;26.
107. Qian L, Zhang Y. Monotonic optimization for non-concave power control in multiuser multicarrier network systems. In: Proceedings of IEEE International Conference on Computer, Communication (INFOCOM). 2009;172–181.
108. Tan CW, Chiang M, Srikant R. Fast algorithms and performance bounds for sum rate maximization in wireless networks. In: Proceedings of the IEEE International Conference on Computer Communication (INFOCOM). 2009;1350–1358.
109. Tan CW, Friedland S, Low SH. Spectrum management in multiuser cognitive wireless networks: optimality and algorithm. IEEE J Sel Areas Commun. 2011;29:421–430.
110. Xu Y, Le-Ngoc T, Panigrahi S. Global concave minimization for optimal spectrum balancing in multi-user DSL networks. IEEE Trans Signal Process. 2008;56:2875–2885.
111. Jorswieck EA, Larsson EG. Monotonic optimization framework for the two-user MISO interference channel. IEEE Trans Commun. 2010;58:2159–2168.
112. Shenouda MB, Davidson T. Convex conic formulations of robust downlink precoder designs with quality of service constraints. IEEE J Sel Top Signal Process. 2007;1:714–724.
113. Vucic N, Boche H. Robust QoS-Constrained optimization of downlink multiuser MISO systems. IEEE Trans Signal Process. 2009;57:714–725.
114. Song E, Shi Q, Sanjabi M, Sun R, Luo Z-Q. Robust SINR-constrained MISO downlink beamforming: When is semidefinite programming relaxation tight? In: The Proceedings of IEEE International Conference on Acoustics, Speech, and, Signal Processing (ICASSP). 2011;3096–3099.
115. Shenouda MB, Davidson T. On the design of linear transceivers for multiuser systems with channel uncertainty. IEEE J Sel Areas Commun. 2008;26:1015–1024.
116. Tajer A, Prasad N, Wang X. Robust linear precoder design for multi-cell downlink transmission. IEEE Trans Signal Process. 2011;59:235–251.
117. Zheng G, Wong K-K, Ng T-S. Robust linear MIMO in the donwlink: a worst-case optimization with ellipsoidal uncertainty regions. EURASIP J Adv Signal Process. 2008;2008:1–15.
118. Basar T, Olsder G. Dynamic Noncooperative Game Theory. SIAM 1999.
119. Osborne MJ, Rubinstein A. A Course in Game Theory. MIT Press 1994.
120. Sarayda CU, Mandayam NB, Goodman DJ. Pricing and power control in a multicell wireless data network. IEEE J Sel Areas Commun. 2001;19:1883–1892.
121. Sarayda CU, Mandayam NB, Goodman DJ. Efficient power control via pricing in wireless data network. IEEE Trans Commun. 2002;50:291–303.
122. Goodman D, Mandayam N. Power control for wireless data. IEEE Personal Commun. 2000;7:48–54.
123. Meshkati F, Chiang M, Poor HV, Schwartz SC. A game-theoretic approach to energy-efficient power control in multicarrier CDMA systems. IEEE J Sel Areas Commun. 2006;24:1115–1129.
124. Meshkati F, Poor H, Schwartz S. Energy-efficient resource allocation in wireless networks. IEEE Signal Process Mag. 2007;24:58–68.
125. Scutari G, Palomar DP, Barbarossa S. Optimal linear precoding strategies for wideband noncooperative systems based on game theory—Part II: Algorithms. IEEE Trans Signal Process. 2008;56.
126. Luo Z-Q, Pang J-S. Analysis of iterative waterfilling algorithm for multiuser power contorl in digital subscriber lines. EURASIP J Appl Signal Process. 2006;2006:1–10.
127. Scutari G, Palomar DP, Barbarossa S. Asynchronous iterative water-filling for Gaussian frequency-selective interference channels. IEEE Trans Inform Theory. 2008;54.
128. Cendrillon R, Huang J, Chiang M, Moonen M. Autonomous spectrum balancing for digital subscriber lines. IEEE Trans Signal Process. 2007;55:4241–4257.
129. Scutari G, Palomar DP, Barbarossa S. Optimal linear precoding strategies for wideband noncooperative systems based on game theory—Part I: Nash equilibria. IEEE Trans Signal Process. 2008;56.
130. Shum KW, Leung KK, Sung CW. Convergence of iterative waterfilling algorithm for Gaussian interference channels. IEEE J Sel Areas Commun. 2007;25:1091–1100.
131. Scutari G, Palomar DP, Barbarossa S. Competitive design of multiuser MIMO systems based on game theory: a unified view. IEEE J Sel Areas Commun. 2008;26.
132. Leshem A, Zehavi E. Game theory and the frequency selective interference channel. IEEE Signal Process Mag. 2009;26.
133. Telatar E. Capacity of multi-antenna Gaussian channels. Eur Trans Telecommun. 1999;585–596.
134. Arslan G, Demirkol M, Song Y. Equilibrium efficiency improvement in MIMO interference systems: Adecentralized stream control approach. IEEE Trans Wireless Commun. 2007;6:2984–2993.
135. Scutari G, Palomar DP, Pang J-S, Facchinei F. Flexible design of cognitive radio wireless systems: from game theory to variational inequality theory. IEEE Signal Process Mag. 2009;26.
136. Gohary RH, Huang Y, Luo Z-Q, Pang J-S. Generallized iterative water-filling algorithm for distributed power control in the presence of a jammer. IEEE Trans Signal Process. 2009;57:2660–2674.
137. Setoodeh P, Haykin S. Robust transmit power control for cognitive radio. Proc IEEE 2009;915–939.
138. Hong M, Garcia A. Averaged iterative water-filling algorithm: robustness and convergence. IEEE Trans Signal Process. 2011;59:2448–2454.
139. Gohary RH, Willink TJ. Robust IWFA for open-spectrum communications. IEEE Trans Signal Process. 2009;57:4964–4970.
140. Hong M, Garcia A. Equilibrium pricing of interference in cognitive radio networks. IEEE Trans Signal Process. 2011;59:6058–6072.
141. Pang J-S, Scutari G, Palomar D, Facchinei F. Design of cognitive radio systems under temperature-interference constraints: a variational inequality approach. IEEE Trans Signal Process. 2010;58:3251–3271.
142. Wang J, Scutari G, Palomar D. Robust MIMO cognitive radio via game theory. IEEE Trans Signal Process. 2011;59:1183–1201.
143. Xie Y, Armbruster B, Ye Y. Dynamic spectrum management with the competitive market model. IEEE Trans Signal Process. 2010;58:2442–2446.
144. FCC, In the matter of establishment of an interfernce temperature metric to quantify and management interference and to expand available unlicensed operation in certain fixed, mobile and satellite frequency band, 2003, ET Docket No. 03–237.
145. Zhang R, Liang Y-C, Cui S. Dynamic resource allocation in cognitive radio network. IEEE Signal Process Mag. 2010;102–114.
146. Scutari G, Palomar DP, Facchinei F, Pang J-S. Convex optimization, game theory, and variational inequality theory. IEEE Signal Process Mag. 2010;27:35–49.
147. Scutari G, Palomar D. MIMO cognitive radio: a game theoretical approach. IEEE Trans Signal Process. 2010;58:761–780.
148. Pang J-S, Scutari G, Facchinei F, Wang C. Distributed power allocation with rate constraints in Gaussian parallel interference channels. IEEE Trans Inform Thoery. 2008;54:3471–3489.
149. Wu Y, Tsang DHK. Distributed power allocation algorithm for spectrum sharing cognitive radio networks with QOS guarantee. In: Proceedings of IEEE International Conference on Computer Communication (INFOCOM). 2009.
150. Yu W, Rhee W, Boyd S, Cioffi JM. Iterative water-filling for Gaussian vector multiple-access channels. IEEE Trans Inform Theory. 2004;50:145–152.
151. Jafar SA, Fakhereddin M. Degrees of freedom for the MIMO interference channel. IEEE Trans Inform Theory 2007.
152. Birk Y, Kol T. Informed-source coding-on-demand (ISCOD) over broadcast channels. In: Proceedings of the IEEE International Conference on Computer Communications, San Francisco, CA. 1998;1257–1264.
153. S. Jafar, Degrees of freedom on the MIMO x channel-optimiality of the MMK scheme, 2006. Available from: <Arxiv:cs.IT/0607099v2, 2006>.
154. Maddah-Ali M, Motahari A, Khandani A. Communication over MIMO x channels: Interference alignment, decomposition, and performance analysis. IEEE Trans Inform Theory 2008.
155. Jafar S, Shamai S. Degrees of freedom region for the MIMO X channel. IEEE Trans Inform Theory 2008;151–170.
156. Razaviyayn M, Boroujeni M, Luo Z-Q. Linear transceiver design for interference alignment: complexity and computation. IEEE Trans Inform Theory. 2012;58:2896–2910.
157. Yetis CM, Gou T, Jafar SA, Kayran AH. On feasibility of interference alignment in MIMO interference networks. IEEE Trans Signal Process. 2010.
158. Gomadam K, Cadambe VR, Jafar SA. Approaching the capacity of wireless networks through distributed interference alignment. In: Proceedings of the 2008 IEEE GLOBECOM. 2008.
159. Peters S, Heath R. Interference alignment via alternating minimization. In: 2009 IEEE International Conference on Acoustics, Speech, and Signal Processing, 2001, Proceedings (ICASSP ’09). 2009;2445–2448.
160. M. Razaviyayn, G. Lyubeznik, Z.-Q. Luo, On the degrees of freedom achievable through interference alignment in a MIMO interference channel, IEEE Trans. Signal Process (in press).
161. G. Bresler, D. Cartwright, D. Tse, Settling the feasibility of interference alignment for the MIMO interference channel: the symmetric case, 2011. Available from: <Arxiv:1104.0888v1>.
162. Bresler G, Tse D. Degrees-of-freedom for the 3-user gaussian interference channel as a function of channel diversity. In: Proceedings of the Allerton Conference on Communication, Control, and Computing, Allerton, IL. 2009.
1However, note that in a MAC channel, which is a special case of the IC, the NEs are indeed efficient. See [150]. In this case, the sequential version of the IWFA converge to a joint strategy that maximizes the system sum rate.
2The idea of interference alignment was introduced in [152–154] and the terminology “interference alignment” was first used in [155].