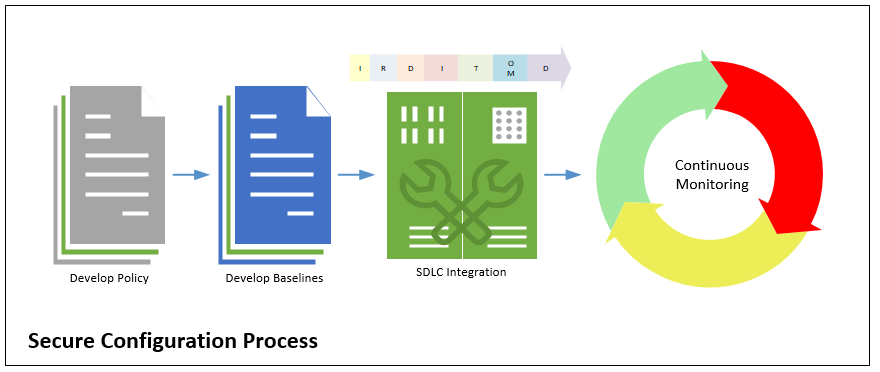
Securely configuring your information systems is a foundation IT hygiene management component that cannot be ignored. Unfortunately, far too often IT organizations overlook secure configuration, leading to an inevitable exposure of the organizational intellectual property.
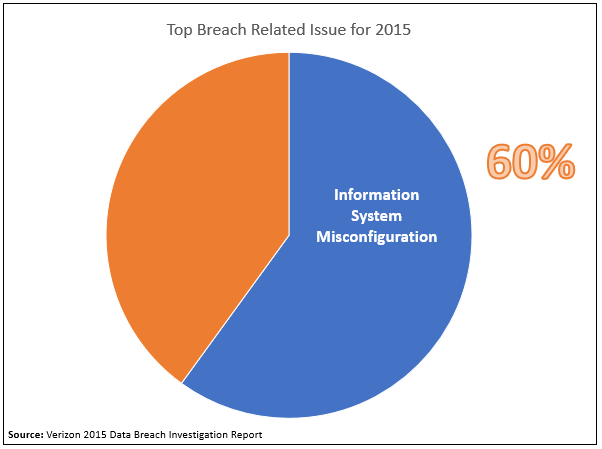
The Verizon 2015 data breach report highlighted that 60% of all breaches could be traced back to information system misconfiguration, which clearly shows that this is a real and very serious problem:
Developing a completely secure configuration strategy means that you should address the following components within your organization: