Incident response procedures are a tactical component of the incident response capability, whereby the incident responder has clearly documented repeatable processes, which allow the incident responder to conduct the activities necessary to do the following:
- Detect and analyze whether a threat exists
- Contain, eradicate, and recover from a threat
When it comes to incident response procedures you will want to implement a checklist approach that allows your incident responders to have clear instructions and guidance, including all the necessary steps to conduct a specific incident response activity. The following sample is a recommended checklist that your organization should implement:
- Emergency contact checklist: One of the biggest issues that many organizations encounter during an incident or emergency is not knowing who to contact. In a crisis, this can cause mistakes to be made as team members run around, scream, and shout. A good checklist will clearly communicate who, what, when, why, and, how communications should be conducted during an incident response activity. A communication checklist should include:
- Information for the entire incident response team:
- Information security team
- IT team (network, systems, apps, and so on)
- Business team
- Information for the entire incident response team:
- Call tree: Key roles for incident response and their order of contact.
- Security analysis checklist: An incident responder should develop checklists for the various technologies and business applications on their network. These checklists are very tactical and are designed as a guide for the incident handler to drill down deeper into the affected system. Focused areas for security analysis checklists include:
- Operating systems: macOS, Windows, Linux
- Network services: DNS, DHCP, Microsoft Active Directory
- Business applications: Salesforce, Oracle, SAP
- Incident handler bag checklist: All incident responders should have a ready-to-go bag that has all the information they need to perform their duties if they were to become displaced, or needed to go to another facility to perform incident response duties. The bag should include:
- Physical emergency contact checklist (if USB drives and laptops fail)
- Physical copies of any other checklists or policies that are deemed mission-critical
- An empty, lined notebook for documenting the incident
- Necessary tools and utilities to perform incident response and forensic functions per your organization's incident response plan
- Blank USB thumb drives
- An incident response laptop—an organization may choose to put a laptop in each incident responder's bag or have one laptop for multiple responders to use
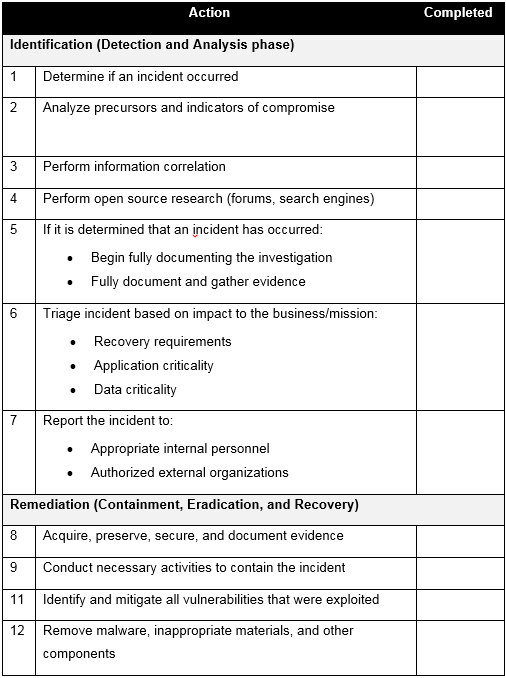
The following example is a simple high-level checklist that characterizes the overall incident response process. In the example, you can see that an emergency contact checklist would be used in step 7. The key takeaway here is that you will not have a single checklist to conduct your incident response activities. You will use multiple checklists to successfully closeout an incident:

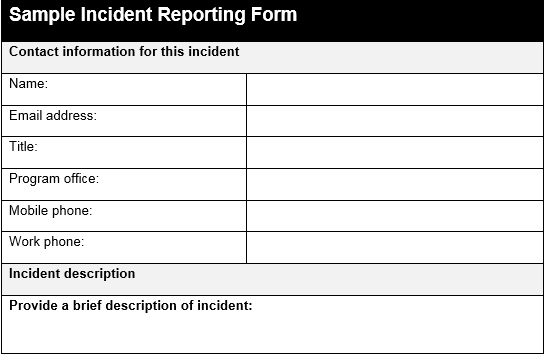
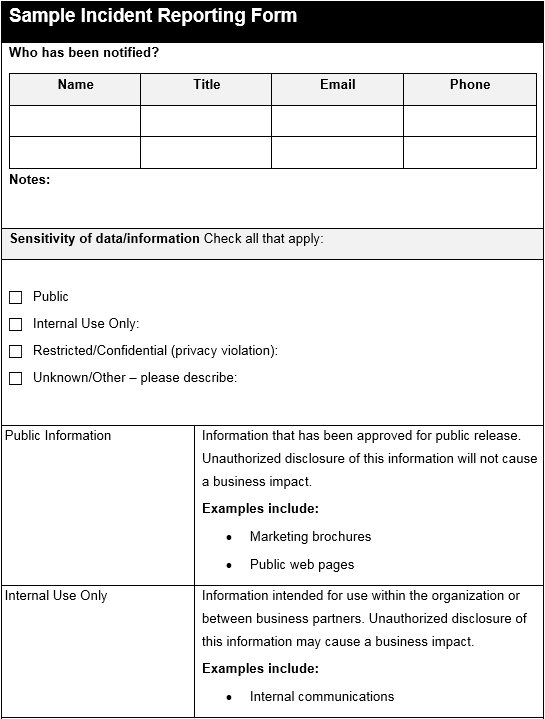
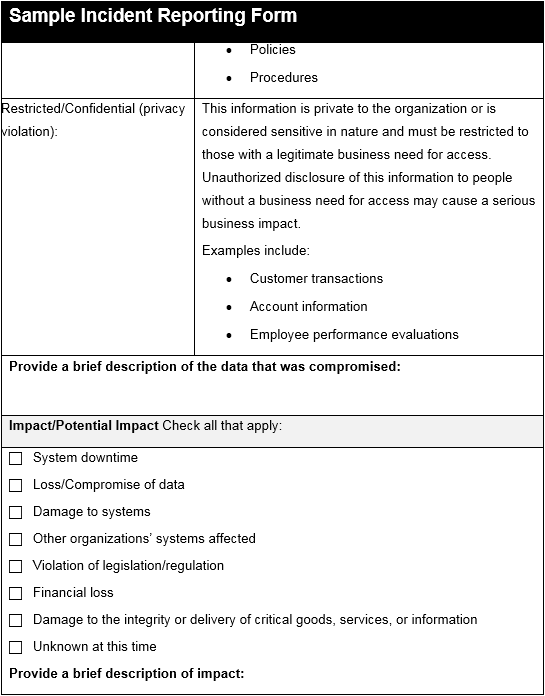
The following is a sample incident response form that would be used to collect information related to an incident: