- Develop the test plan: Now that you have testable requirements for the information system and you are in the design phase, it is time to develop the test plan, test procedures, and mechanisms you will use to report the results of the information security test that you perform. Your test plan should answer the following questions:
- What is the scope of the test?
- Who will be conducting the test?
- What is required to conduct the test (tools, personnel, and so on)?
- How should the outputs of the testing be handled (company proprietary, confidential, and so on)?
- If a system outage or a security event occurs, who should be contacted?
Your test procedures should be carefully planned to include all the necessary steps to conduct the test, including the information needed to ascertain whether a test has passed or failed. In the following example, the tester is validating a web application for a cross-site scripting vulnerability. The tester enters the cross-site scripting exploit code <script>alert(123)</script> into an input field on the web application and submits the request to the web server. If the web browser returns an alert box that says 123, the test has failed and the input field in the web application is vulnerable to cross-site scripting. Otherwise, the test has passed and the input field is not vulnerable. The tester would continue to test all input fields using this test to ensure each input field is not vulnerable to cross-site scripting:
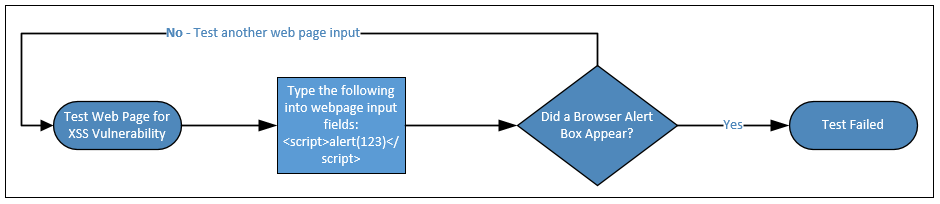
Finally, develop a reporting mechanism where you clearly provide the results of the security test for the project team. The report should include the identified vulnerabilities and recommended mitigation necessary to close the discovered vulnerabilities. The results of the testing should include both passed and failed tests, with artifacts supporting the tester's assertion. The report should be provided to the appropriate individual(s) in your organization, following the data handling guidance that was previously identified in the test plan.
- Testing throughout the design process: The information security professional will be engaged with the information system design team throughout the development process. While there is a clear part of the SDLC that is reserved for the acceptance testing of the information system, the information security professional will perform the required testing services throughout the design process to ensure that security services are working as expected and do not hinder the expected functioning of the information system.
It is very important that the information security professional be well-engaged in this part of the SDLC, as this is where the design elements are being tested and proof of concepts implemented in support of the future production information system. Being part of this process serves to ensure that security is part of the information system and that it has been designed in; not being part of this process runs the risk of security services not being adequately implemented, which will result in inadequate protections for the production information system.
