- What information assets are within your organization?
- What is the value of those assets to your organization?
- What will it take to properly secure those assets commensurate with their value?
An organization's information systems are jam-packed with data that is required for the organization to accomplish its mission. It is important when you begin the process of performing data categorization that you understand that not all data is made equal, and therefore, not all data has the same value to the organization. As a result, you will not be applying the same security controls to protect all data throughout the organization as this would result in wasting resources.
If you reserve your most difficult-to-implement and most costly security controls for data that has the highest value to the organization you will be establishing an efficient and cost-conscious information protection program. This is a key component to a successful information security program as it establishes the following:
- Trust in the information security program: Your information security program should be able to distinguish between sensitive and non-sensitive information. Additionally, it should be able to provide tailored guidance regarding how to protect the different types of information. Not doing this will cause the organization to do unnecessary work for some subset of your corporate data, causing frustration with project and finance teams.
- Fiscal responsibility: A key part of a successful information security program is senior leadership support. One way to ensure that you lose your leadership's support is to waste their resources. By selecting only the needed security controls for a particular type of organizational data, you are showing your leadership that you are committed to saving the organization money and that you value the resources that you have been given.
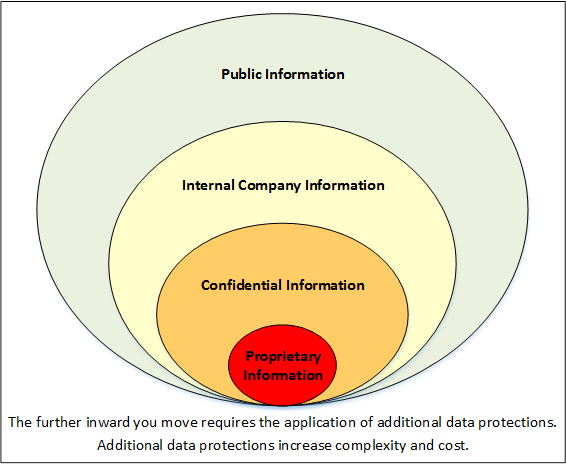
As an information security professional conducting data classification you must ensure that you properly identify organizational data, properly apply the most prudent security controls, and ensure that the organization's resources are being maximized and used efficiently.
