Clearly document the purpose of the system from a business perspective. In the example of a document management system, you would want to show what business need is being fulfilled. If your organization is utilizing a project management framework then you can use the information that will come out of the project chartering process to obtain this information. Otherwise, you will need to interview the business and IT stakeholders to gather this information.
- Business purpose: Implement a document management system to store manufacturing plans and diagrams in a secure and searchable fashion.
- System description: If your organization knows how they are going to implement the business purpose statement then you will want to document this now. For example, if your organization uses SharePoint and they intend to use SharePoint to satisfy the business purpose, then document the technology and other facts that are available:
- This section describes the system in narrative form using non-technical terms (tech speak):
- The technology used should be clearly defined-in this case, SharePoint. While SharePoint is the product being implemented, this is not considered a technical term.
- Will the capability be hosted internally or outsourced?
- How does the business unit plan on using this capability?
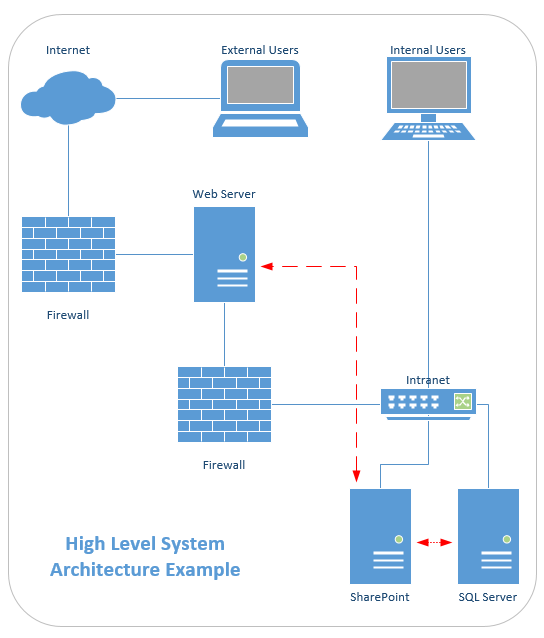
- What is the high-level proposed system architecture? Include an architecture drawing that includes (if applicable):
- Information system's subsystem
- Interfaces to external systems
- System hardware architecture
- System software architecture
- Storage architecture
- Backup/disaster recovery architecture
- Internal communications architecture
- User inputs
- User output
- This section describes the system in narrative form using non-technical terms (tech speak):
The key take away here is to develop a high-level architecture drawing that will help you to better:
- Communicate the various aspects of the information system to all stakeholders
- Verify with the project stakeholders that you accurately understand the system
- Add information security controls to show the interaction between the information system and security controls.
- Identify the functions and, if possible, the system elements that fall within the security boundary for the information system.