Here is where we come to the true purpose of establishing a security operations center—containment, eradication, and recovery from external and internal threats to your organization. Being able to respond to a threat rapidly will spell the difference between an easily contained versus a highly damaging incident.
Your remediation strategy is also very much tied to your business's mission, and the steps that you take to remediate a threat can be very different from one organization to another.
Regardless of your organization's business strategy, your SOC team must ensure that they effectively:
- Contain the threat: Ensuring that the attacker is unable to or finds it very difficult to cause damage on other information systems
- Eradicate the threat: The complete removal of the threat from your information system
- Recover from the threat: Restore the information system back to its fully operational capability
Strategies used as part of this phase include:
- Updating and/or patching to close vulnerabilities in your network, servers, workstations, and applications
- Updating system access to remove an attacker's privileges
- Changing network access to disrupt attacker communications
- Reimage or reset devices to ensure the removal of attacker software
- Ensure that SOC monitoring capabilities are properly tuned to ensure efficient detection based on lessons learned
- Ensure that additional security controls are applied to the information systems as needed to prevent future attacks
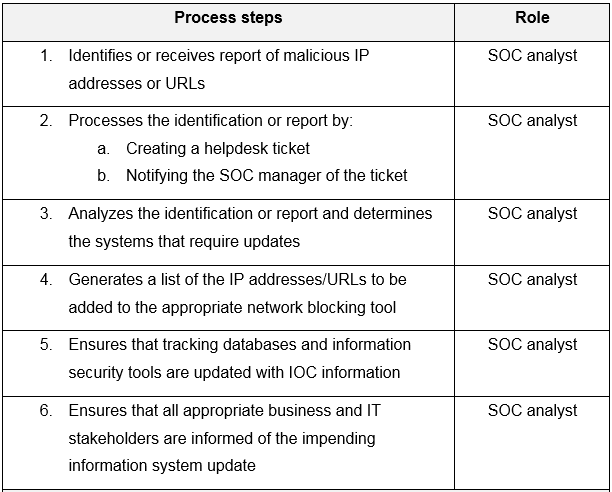
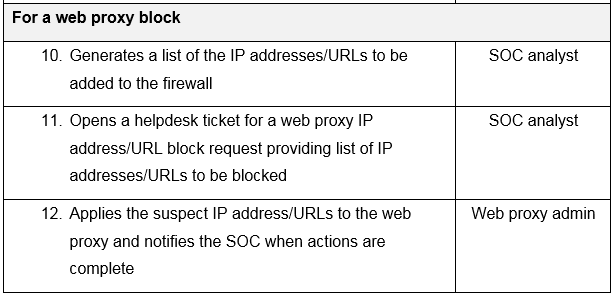
The following is a sample security operations center standard operating procedure (SOP), which provides the steps an organization could use to block network access to a threat as part of normal operations or in response to an incident: