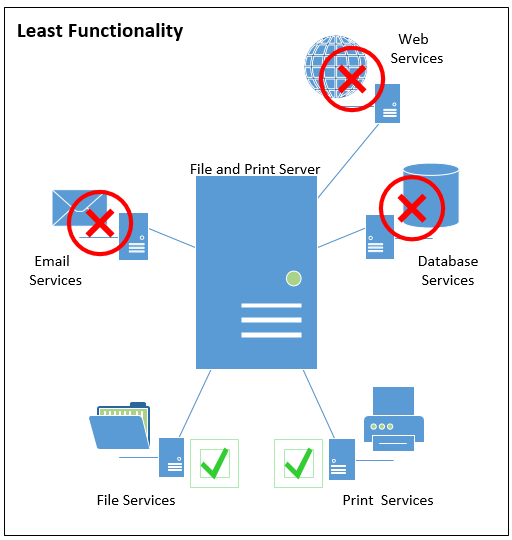
Modern information systems provide a great deal of capability and flexibility to the organization. As you are designing your information system, it is important to understand not just what your information system needs to do to meet business requirements, but also the operating system functionality that is not required to meet those same requirements.
You will want to ensure that you are restricting the functionality of the information system so that it operates as required while not exposing any unneeded services that can be used by an attacker to exploit the system. To achieve this, do the following:
- Ensure that you have installed everything that you need for your information system to function as intended. This includes:
- Operating systems complements
- Support applications
- Operations and information security management agents
- APIs
- Uninstall or restrict any components that are not needed for the information system to operate as expected. This includes:
- Default installed operating system components
- Software or services that may be included as value-added components of the required application software
- Testing tools that may have been installed during implementation to validate system capabilities