To have an effective security operation center, it is critical that you implement the necessary personnel roles to properly operate and maintain the environment. In the following list, you will find the personnel roles needed to fully implement a security operations center. Do not get hung up on the names of the roles if they do not match those in your organization. Each organization will have its own naming convention derived from the organization's culture:
- Security operations center analysts:
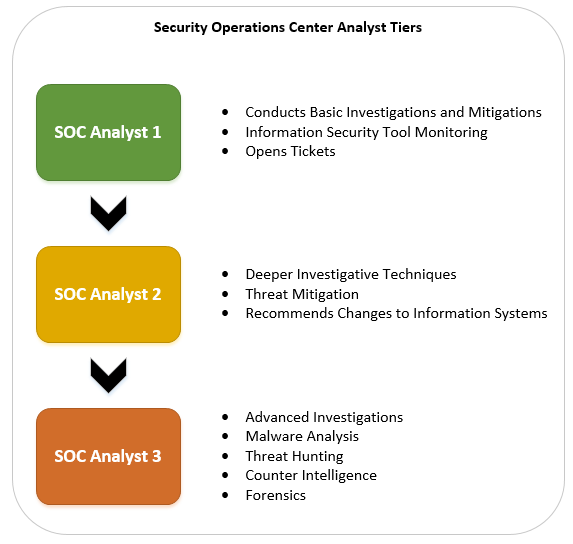
- Tier one: More junior information security analyst with a couple of years' experience in the information security field. Possesses a basic knowledge of networking, systems, and applications:
- Conducts information security tool monitoring
- Conducts basic investigations and mitigations
- Opens tickets
- Tier two: Poses a stronger knowledge of the information security tools used by the SOC as well as a deeper understanding of networking, systems, and applications:
- Deeper investigative techniques
- Threat mitigation
- Recommends changes to information systems
- Tier 3: Is stronger in SOC and IT skills than the tier two analysts and typically has skills in forensics, malware analysis, threat intelligence, and more:
- Advanced investigations
- Malware analysis
- Threat hunting
- Counter intelligence
- Forensics
- Tier one: More junior information security analyst with a couple of years' experience in the information security field. Possesses a basic knowledge of networking, systems, and applications:
-
- Serve as primary team member performing incident response: It includes preparation, detection, analysis, containment, eradication, recovery, and post-incident activities:

-
-
- As required, this role may additionally:
- Implement additional information security tools in support of the security operations center. Most complex implementations would be performed by a security engineer.
- Create new operational procedures related to threat detection, analysis, containment, eradication, and recovery.
- As required, this role may additionally:
-
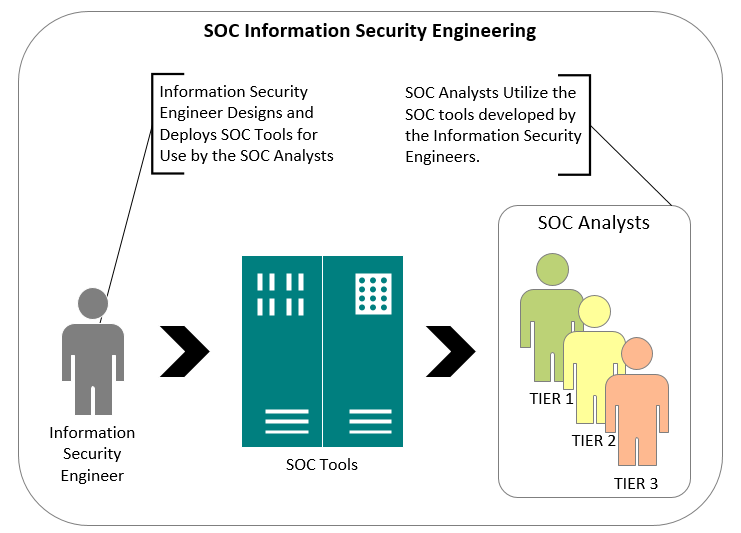
- Information security engineers:
- Responsible for the systems development/engineering life cycle from Chapter 3, Preparing for Information and Data Security, which includes initiation, requirements analysis, design, implementation, testing, operations and Maintenance, and disposition of security operations tools:

-
- Typically, the security engineer will support the security operations center as well as the enterprise organization. As a result, they:
- Develop capabilities for the SOC, such as:
- Security information and event management (SIEM) systems
- Vulnerability management systems
- Develop capabilities for the enterprise such as:
- Firewall and IDS/IPS designs
- Implementation of security requirements within enterprise projects
- Develop capabilities for the SOC, such as:
- Typically, the security engineer will support the security operations center as well as the enterprise organization. As a result, they:
- Security operations center manager:
- The security operations center manager is responsible for the overall management of the SOC and its day-to day-operations. Additionally, the SOC manager is responsible for:
- Creating a new SOC-related policy.
- Creating and approving new SOC-related procedures and processes.
- Managing security operations center analysts. Typically, the SOC analysts work directly for the SOC manager.
- Coordinating with information security engineers. Typically, the information security engineers work within a different part of the information security program. However, there is nothing precluding an SOC from having its own information security engineers.
- The security operations center manager is responsible for the overall management of the SOC and its day-to day-operations. Additionally, the SOC manager is responsible for:
- Chief information security officer (CISO):
- Is responsible for developing the overall organizational information security program, which includes the organization's security operations center
- Approves all new policies, procedures, and processes related to the SOC
- Ensures that the SOC capability aligns with the organization's information security risk management program and compliance programs
- Communicates SOC threat data to organizational management in support of the overall information security program goals
