The following are the elements for a successful information security program:
- Policy: The rules for how your information security program behaves in addition to organizational policy
- Information security services: Technical and operational capabilities provided to the organization as a service:
- Vulnerability management service (vulnerability scanners)
- Malware detection services (antivirus/anti-malware)
- Log monitoring services (SIEM/log aggregation)
- Threat detection services (host and network IDs)
- Security architecture: Working with the business and IT teams to ensure that new IT systems are properly architected to properly protect the information that they contain commensurate with the information's value
- Information security guidance: Working with the business and IT teams helping them to properly understand and implement security requirements:
- Information security awareness and training: Specific training where information system users are trained in the acceptable use of the information system
- Information security advisement: Activities implemented by the information security program to ensure that information security requirements are properly understood and implemented by both business and IT users
- Information security categorization: Assist the business and IT users in the proper categorization of information assets
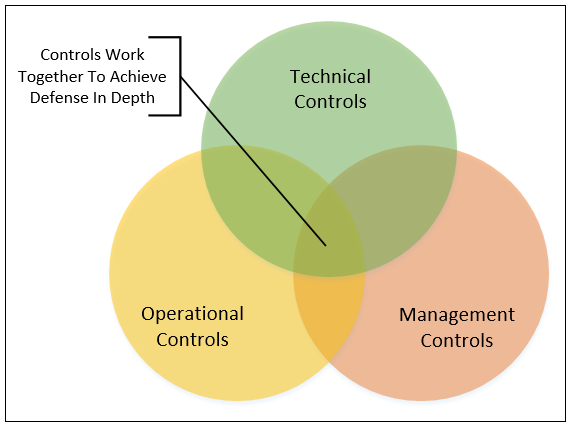
These information security program functions provide the organization's management, operational, and technical information security controls which, when properly implemented, work to secure the organization-sensitive information:
- Technical controls: Security controls implemented on the information system that serve to protect the information system from unauthorized access. These are controls that are installed and reside on the information system by the IT team. Examples of technical controls include:
- Firewalls: Devices that restrict network traffic into and out of a network zone.
- Encryption: Can be used to protect data in motion as well as data at rest by protecting the confidentiality of data:
- For data in motion you may implement a protocol such as IPSec to protect data being transmitted from one server to another.
- For data at rest you could implement a tool such as BitLocker on a Microsoft Windows system. This tool serves to ensure that data on a hard drive is kept confidential if the hard disk is stolen.
- Antivirus software: Provides protection against malware infections. Can be implemented at the server, workstation or network level.
- Operational controls: Security controls that are implemented on an ongoing basis by individuals within the organization. Many of these control types deal with the day-to-day operations of the organizational information systems. Examples of operational controls include:
- Contingency planning: A process where an organization establishes how it will respond to a system outage
- Configuration management: The utilization of organizational-approved baselines to ensure a common configuration across devices
- Change management: A process where organizational stakeholders review proposed changes to document that a change is occurring and to ascertain whether potential misconfigurations may exist in the change
- Management controls: Policies, practices, and procedures at the organizational, information system, and personnel levels. Examples of management controls include:
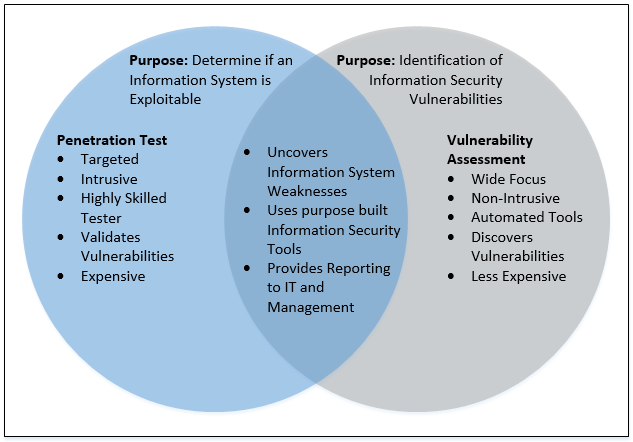
- Vulnerability assessment: An assessment by an information security professional that attempts to uncover weaknesses in an information system. The vulnerability assessment will be reconducted as weaknesses are mitigated to ensure that the weakness no longer exists.
- Penetration tests: Penetration tests take the output of the vulnerability assessment and attempt to exploit the weaknesses that were discovered.
It is very common to see vulnerability assessments improperly categorized as penetration tests by information security professionals. A penetration test is a much deeper dive into the information system than a vulnerability assessment and requires a much more skilled information security professional than a vulnerability assessment requires.
This difference between penetration tests and vulnerability assessments is important for many reasons:
-
-
- Penetration tests cost more than vulnerability assessments
- Penetration tests examine the information system much more closely
- Penetration tests remove false positives from the vulnerability assessment
-
-
- Risk assessments: Quantitative and qualitative risk assessments that serve to inform management regarding the risk to their information and information systems.
The organization's information security program utilizes a layered approach (defense in depth) to ensure adequate protection of sensitive information across the enterprise network: