As you work through the various frameworks, it is important to remember that they are not checklists. These frameworks need to be used to develop your own security program. A key aspect in developing a strong information security program is to understand that you should not be boiling the ocean. By this, I mean that you should not be trying to do so much that you end up doing nothing or worse, causing serious harm to the organization.
As you develop your plan to implement your information security program, you must consider where you are presently from an information security program maturity perspective. As you engage in planning, you need to think about how you can push your program along the maturity life cycle. As an example, you cannot push your organization into a place where you are implementing continuous and effective monitoring of security controls if you are implementing those controls in an ad hoc fashion. You must first focus on developing plans where information security control development is part of the organizational culture and system development life cycle.
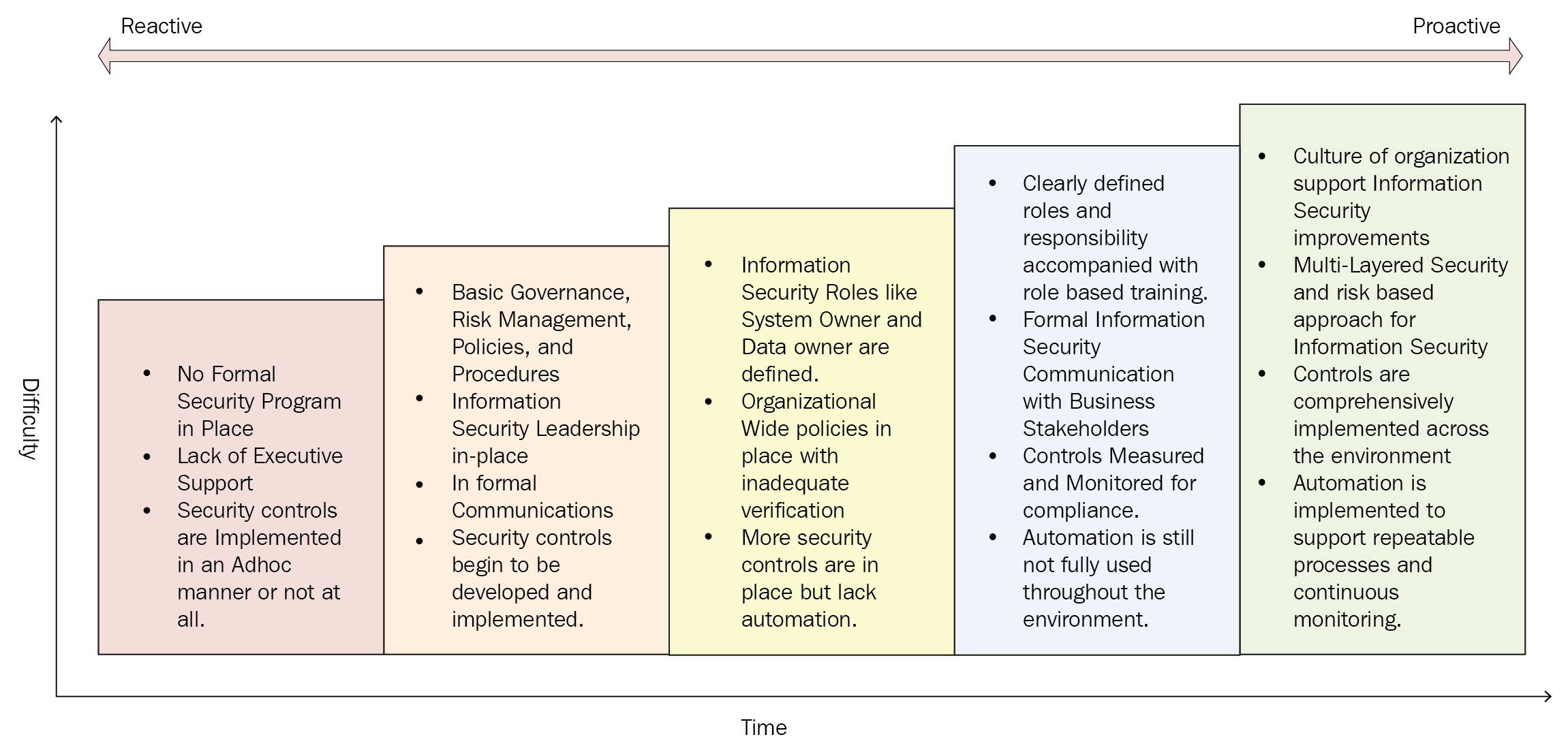
- Initial:
- No formal security program in place
- Unstaffed or understaffed
- Security controls are implemented in an ad hoc manner or not at all
- Developing:
- Basic governance and risk management policies, standards, procedures, and guidelines are in place
- Information security leadership is in place
- Informal communications
- Security controls begin to be developed and implemented
- Defined:
- Information security roles such as system owner and data owner are defined
- Organization-wide polices are in place with inadequate verification
- More security controls are in place but lack automation
- Managed:
- Clearly defined roles and responsibilities accompanied by role-based training
- Formal information security communication with business stakeholders
- Controls measured and monitored for compliance
- Automation is still not fully used throughout the environment
- Optimized:
- Culture of organization supports information security improvements for people, processes, and technology
- Organization implements a risk-based management program for information security
- Controls are comprehensively implemented across the environment
- Automation is implemented to support repeatable processes and continuous monitoring