Security controls implemented on the information system that serves to protect the information system from unauthorized access are controls that are installed and reside on the information system by the IT team.
This part of BCDR is the actual technical implementations that are implemented before a disaster occurs that ensure a smooth transition during an emergency.
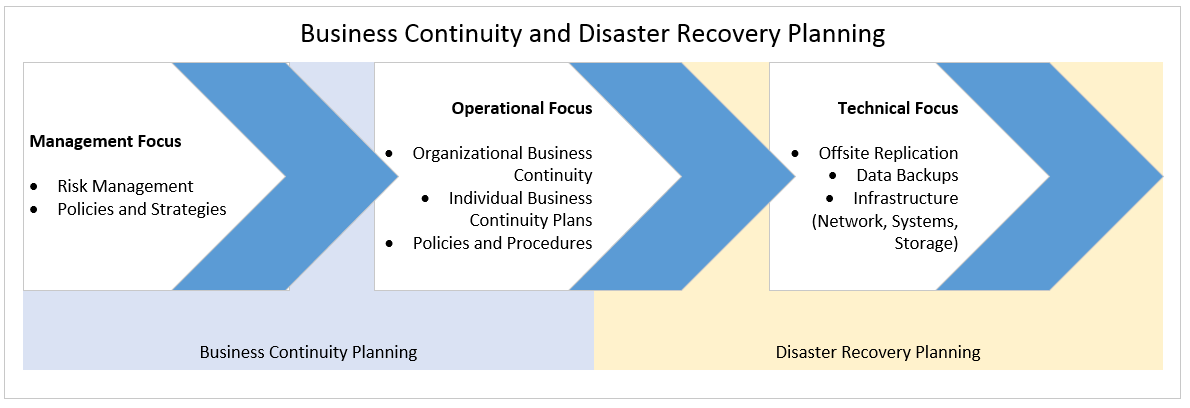
Depending on the organization's risk appetite and requirements developed during the business continuity discussions, the organization may choose to have a fully functioning mirror of the current operating environment, a reduced capability providing the minimum services necessary to get through a disaster, or a hybrid somewhere in between. To achieve these goals, the information technology group will implement services including:
- Offsite replication: Offsite replication ensures that key information services exist in real time at multiple data centers or cloud instances. If one instance of a site is disrupted, another instance can be used in its place to continue business operations.
- Data backups: Data backups are implemented to ensure that a system can be effectively restored. The number of backups will vary based on the organization's policies.
- Infrastructure: Infrastructure (network, systems, and storage) is all the architecture that goes into the effective planning, design, and implementation of an effective disaster recovery plan.
The following figure highlights the fact that the business continuity and disaster recovery processes are truly complementary processes that flow into each other, ultimately leading to a well-developed process to ensure that the business has the people, processes, and technology necessary to recover from a disaster and maintain business continuity: