As part of the defense, an in-depth strategy associated with your organization's information security control implementation, you may find that you already have a wealth of tools at your disposal to properly alert to and defend yourself against threats. These are the tools that are already deployed throughout your enterprise and are used to manage your environment from the following perspectives:
- Network
- Server
- Workstation
- Application
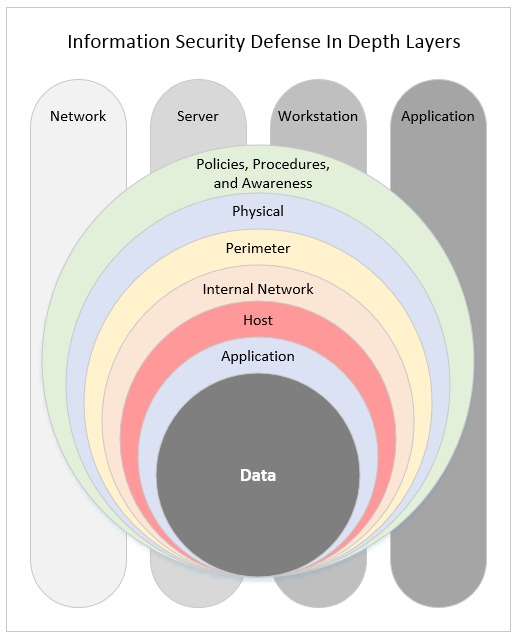
The layers of defense applied to your organization's network, servers, workstations, and applications provide protection from threats as well as reporting and alerting in the event of threatening acts on an information system. Protection and visibility that are part of the defensive layers include:
- Policies, procedures, and awareness layer:
- Policies and procedures provide you with the necessary information to understand what normal looks like from business risk and technical implementation perspectives. While policies and procedures don't provide reporting or alerts, they do provide you with the information needed to ensure that you can have effective alerting.
- Awareness ensures that you have adequately trained your leadership, general, and technical users regarding their duties as it relates to policies and procedures. This helps to further inform how we will implement alerting as our users have been trained and should not be violating policy.
- Physical layer: Guards, guns, and flashlights:
- ID badges
- Motion
- Cameras
- Motion detectors
- Perimeter layer: Protection for the outermost part of your network:
- Web proxies: Act as an intermediary device between an internal network endpoint and an internet-based HTTP resource
- Denial of service prevention: Tools that allow network resources to resist denial of service attacks
- SMTP proxies: Act as an intermediary device between an internal SMTP server and an internet-based SMTP resource
- Firewalls: A network device that controls outgoing and incoming network traffic
- Internal network layer: Protection for internal enterprise's network resources where your users and applications reside:
- IPSec tunnels: Allow secure communications between devices
- Network access control: Ensures that only approved devices are permitted access to the enterprise network
- Network segmentation: Ensures that resources on the network can only access the resources they are entitled to access
- Network intrusion prevention/detection systems: Ensure that suspicious traffic is analyzed and, if necessary, blocked on the network to prevent an intrusion by an attacker
- Host layer: Protections for server and workstation operating system:
- Operating system's security controls: This is the appropriate implementation of security controls throughout the operating system.
- Malware tools: Tools that detect and eliminate malware from the host.
- Host intrusion prevention/detection system: Ensures that suspicious traffic is analyzed and if necessary blocked on the host to prevent an intrusion by an attacker.
Vulnerability management system.
- Application layer: Protection for enterprise web applications:
- Application reverse proxies: Act as an intermediary between an internal web resource and internet or external user
- Security Assertion Markup Language (SAML): Allows internal identity services to be extended to other services inside and outside of the enterprise network
- Single sign on: Allows for a single set of credentials to be utilized throughout the enterprise network
- Web application firewall: Provides protection for web vulnerabilities in enterprise web applications
- Data layer: Protection against data abuse:
- Information rights management: Allows data to be secured inside and outside of the network, typically implementing a call home mechanism to verify file permissions before allowing access
- Database security: Implementation of appropriate security controls from a database perspective
- Mobile device encryption: Ensuring that organizational data is properly encrypted across mobile devices
- Data loss prevention (DLP): Tools that allow organizational data protection polices to be automated and enforced at that network level
