We will now take a look at some of the techniques and tools used by the attacker to launch their attacks and campaigns:
- Password cracking: The hacker utilizes specialized software to recover passwords that have been transmitted over the network, from recovered password databases stored at rest, and application software that implements their own methods of authentication. A common method for implementing password cracking is to implement automated guessing through the use of password dictionaries.
The following is a list of the password cracking tools that we can use:- Brutus: http://sectools.org/tool/brutus/
- RainbowCrack: http://sectools.org/tool/rainbowcrack/
- Wfuzz: http://sectools.org/tool/wfuzz/
- Cain and Abel: http://sectools.org/tool/cain/
- John the Ripper: http://sectools.org/tool/john/
- THC Hydra: http://sectools.org/tool/hydra/
- Medusa: http://sectools.org/tool/medusa/
- ophcrack: http://sectools.org/tool/ophcrack/
- L0phtCrack: http://sectools.org/tool/l0phtcrack/
- Aircrack-ng: https://www.aircrack-ng.org/downloads.html
- Vulnerability assessment scanner tools: These tools utilize databases of known vulnerabilities with specialized software that scan the network to see if there are any matches with the database. The tool then creates a vulnerability listing that ties the vulnerability to an IP address so that it can be reviewed. In the case of an administrator, this list can be used to fix an information system. In the case of an attacker, this list is the front door.
The following is a list of the vulnerability assessment scanner tools that we can use:- OpenVAS: http://www.openvas.org/
- Burp Suite: https://portswigger.net/burp/communitydownload
- Arachni: http://www.arachni-scanner.com/
- w3af: http://w3af.org/
- Vega: https://subgraph.com/vega/
- Nmap: https://nmap.org/
- Microsoft Baseline Security Analyze: https://www.microsoft.com/en-us/download/details.aspx?id=7558
- Qualys FreeScan: https://www.qualys.com/forms/freescan/
- Nessus: https://www.tenable.com/products/nessus-home
- Rapid7 (InsightVM and Metasploit): https://www.rapid7.com/
- Manual vulnerability assessment: The truly skilled hacker is able to test information systems based on their own knowledge for vulnerabilities that scanners cannot detect. This is where manual testing comes into play.
Manual testing also clearly marks the division between vulnerability assessment and penetration testing as part of the information security program. In order to have an effective program, you must ensure that your periodic testing includes manual/penetration testing. Without this type of testing, you will be missing the information system's vulnerabilities that your adversaries won't miss.
- Keystroke logging: With keystroke logging, the attacker installs either software or a physical device on the computer with the intention of capturing all keystrokes entered on the computer:
- Software-based keyloggers: Following are the hypervisor-based keyloggers:
- Hypervisor-based keyloggers: It operates at the hypervisor level of a virtualized infrastructure and sits at a place below the operating system. In this case, known detection tools at the operating system level will be able to detect the keylogger.
- Kernel-based keyloggers: It operates in the kernel mode of the operating system as a rootkit and is typically not detectable by antivirus tools as they do not have access to the layer of the operating system.
- Hardware-based keyloggers: Following are the hardware-based keyloggers:
- Keyboard hardware: These types of keyloggers are connected between a computer and a keyboard. They contain internal memory and intercept keystrokes sent from the keyboard to the computer. This type of keylogger requires physical access to the computer.
- Wireless keyboard sniffers: Specialized hardware and software that can intercept keystrokes sent between a wireless keyboard and the computer it is attached to. This type of keylogger requires that the attacker is in close proximity to the computer being attacked.
- Software-based keyloggers: Following are the hypervisor-based keyloggers:
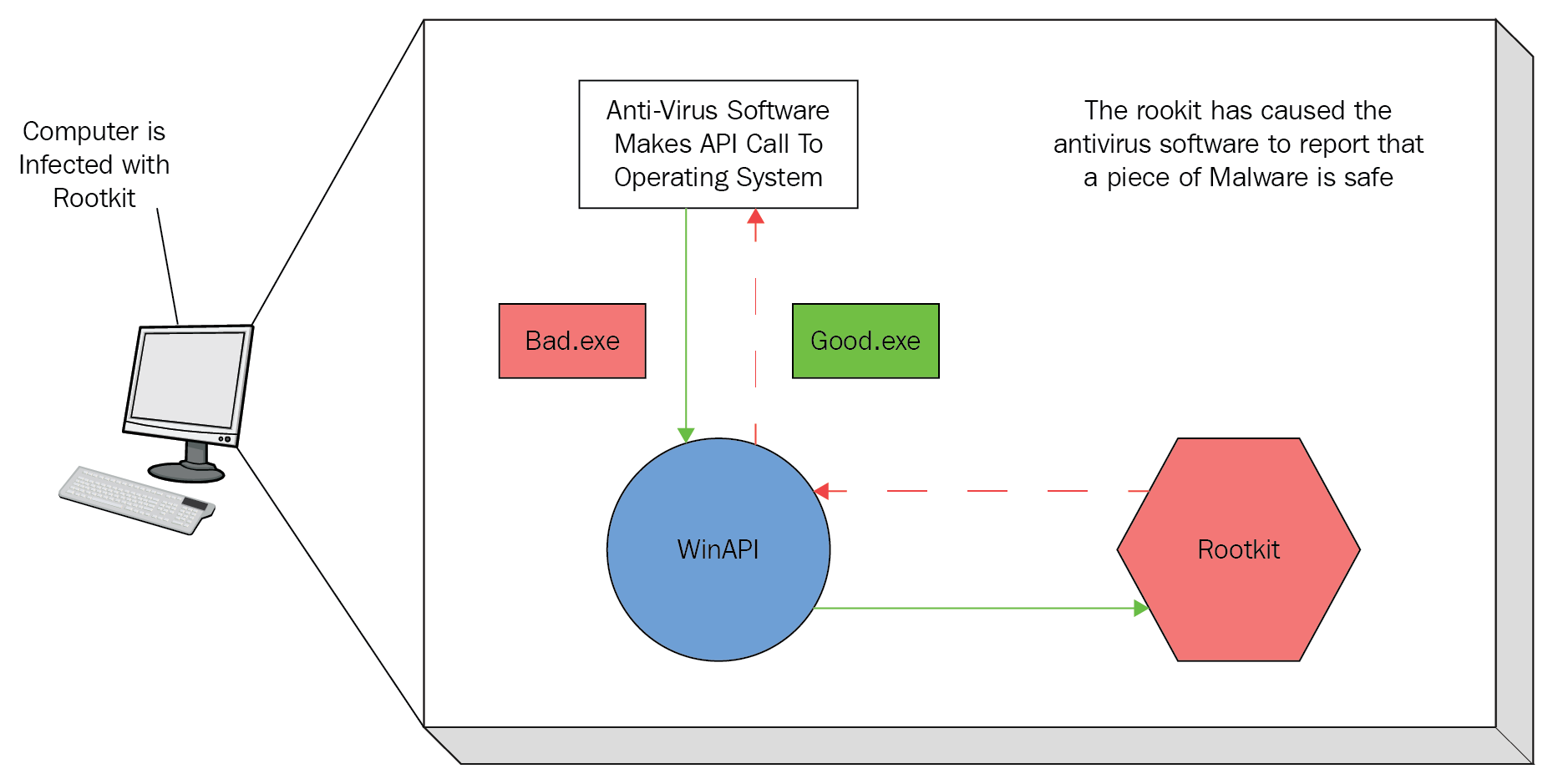
- Rootkit: A rootkit is a piece of software that is installed by a hacker that is very difficult to detect and is used to take control of an operating system. A rootkit replaces key operating system software causing the operating system to appear normal when in fact it contains malware. Because rootkits run at such low levels in the operating system, they have the ability to make themselves look legitimate by responding to higher levels in the operating system with information that is expected as part of normal operations:
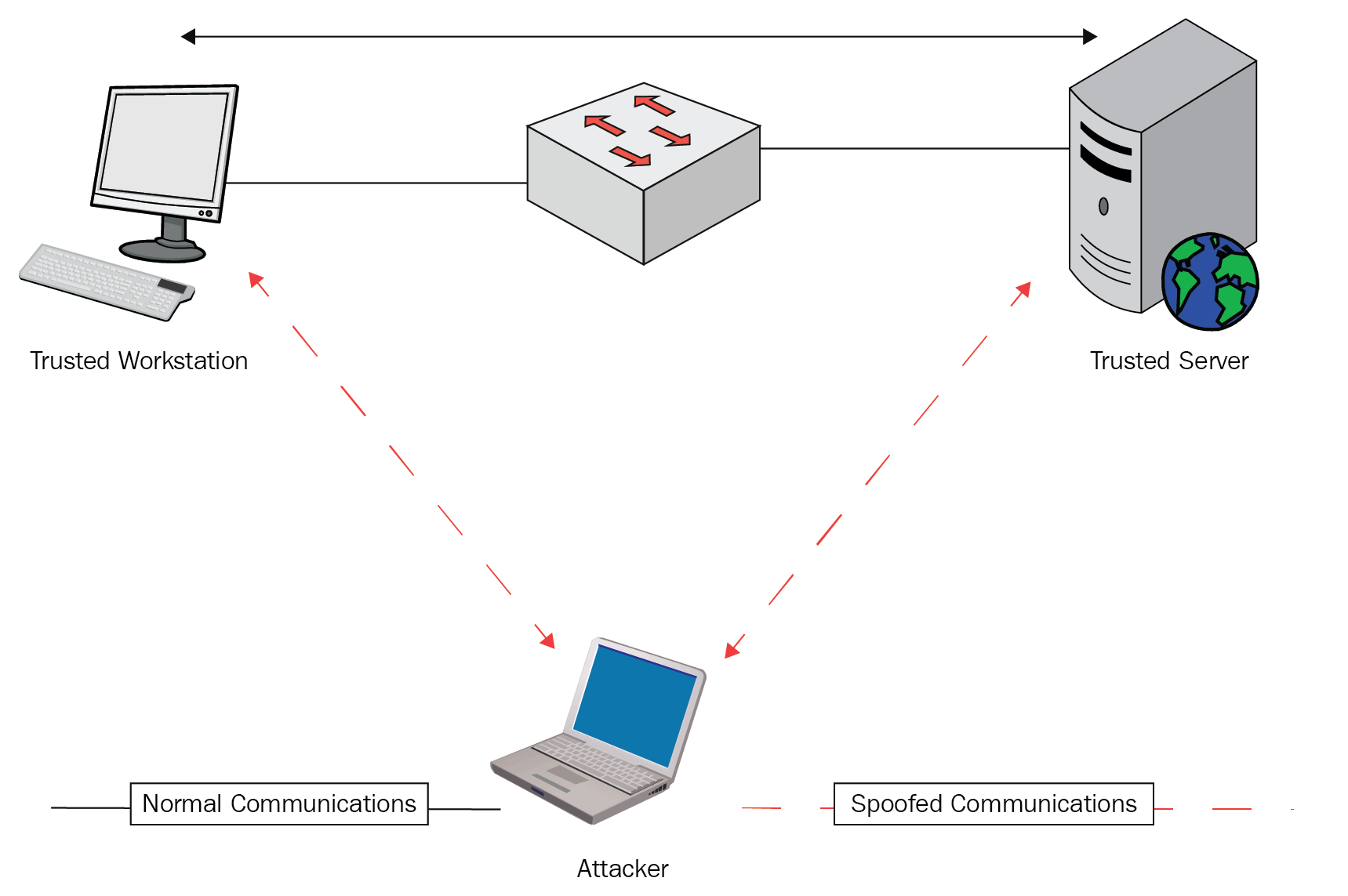
- Spoofing: As part of a spoofing attack, a hacker will install software or build a system with the intention of mimicking another system. In some cases, the hacker may spoof themselves with the intention of appearing like a trusted client system in order to gain access to a backend server environment. In other cases, the hacker will spoof themselves as the underlying information system infrastructure in order to harvest information from unsuspecting users. Hackers can use this technique to harvest sensitive company information and passwords to backend information systems:
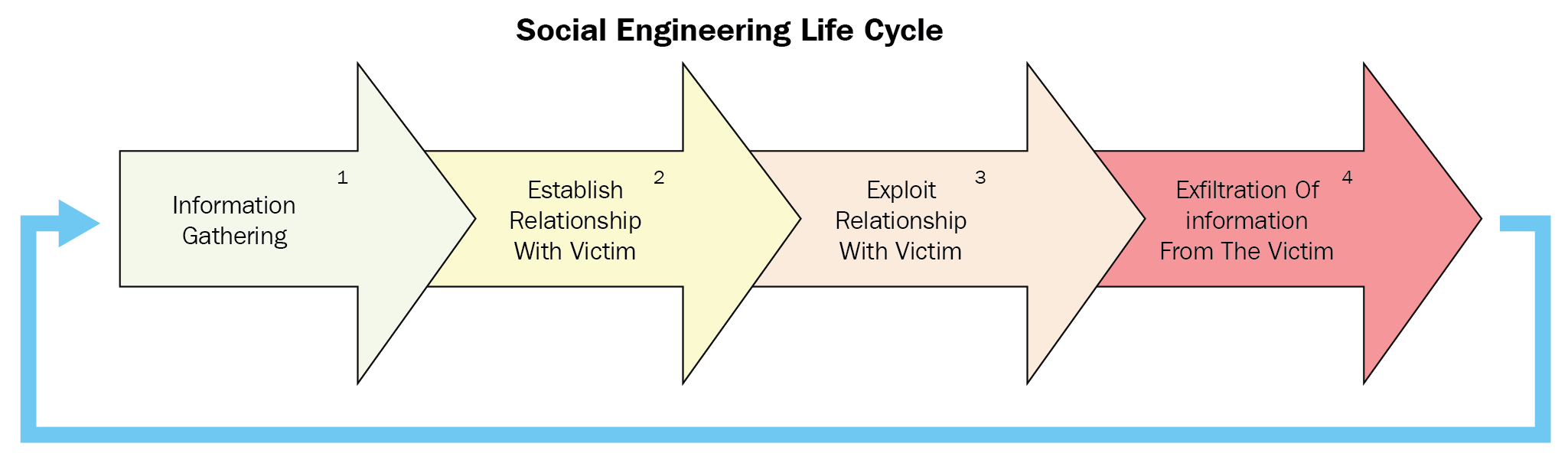
- Social engineering: This hacking technique is very hands-on and can often not include any special tools other than the hacker. Social engineering has to do with manipulating an individual's natural bias to want to trust another person:
- Pretexting: With pretexting, the hacker creates a scenario that they use against their victim to lure them into divulging information that will allow the attacker to gain further access to the organization's information system. As part of the scenario, an attacker will establish a position of authority so that the user believes that the request is valid, and that the attacker has a right to know their confidential information.
An example of pretexting is when a hacker contacts a user of a company posing as a member of the organization's information technology team. They can make a request for the user to provide them with their username and password so that they can troubleshoot an issue with an information system. In many cases, a user will hand over their credentials because they believe that the individual requesting the username and password are well-intentioned and want to do a service for the user. In reality, the hacker has just harvested the user credentials and will use them to further their intrusion into the information system.
- Phishing: Using these techniques, hackers can take the concept of pretexting and apply some technology to expand the number of individuals they are reaching at a single moment. In the pretexting example, the attacker was reaching out to a single user at a time. With the phishing example, the attacker can reach millions of users in a single campaign.
An example of phishing is receiving an email saying that your bank information is no longer valid and that you need to log in to your bank's website to fix the issue. In the case of a well-executed phishing campaign:- The email will contain a link for you to click that will take you to the attacker's website rather than the actual bank's website.
- The attacker's website will look and function like the bank's website.
- The URL in the browser will look similar to the URL of the bank's website.
- The attacker's website will accept the user credentials and pass the user to the real website. The user will not realize that anything has happened.
The following screenshot is an example of a phishing campaign. Notice that the email appears to come from Netflix and that it generically addresses the user. The link will take the user to the attacker's website if clicked. This image is taken from an actual phishing message:

- Spear phishing: While very similar to phishing, spear phishing adds a dimension of analysis on the part of the attacker against the victim. With spear phishing, the attacker performs reconnaissance against their victim in order to gain important personal details that the victim will recognize as information that only a colleague would have. Therefore, the main difference between phishing and spear phishing is that the attacker sends a customized email to lure a single user, versus the millions of emails that are sent out in a phishing campaign. The success of spear phishing attacks is higher than phishing attacks because of the customization that goes into the spear phishing email.
- Water holing: This attack takes advantage of websites that contain vulnerabilities and that a user trusts. In this attack, the adversary will do reconnaissance to determine websites that a user or group of users often use within an organization. The attacker will then work to compromise the trusted website. Once the website is compromised, the website can be used as a platform to install malware on the unsuspecting users' machines. The attacker can simply wait for the users to go to the website or they can craft a spear phishing email to lure them to the site.
- Baiting: In baiting, the attacker will use a physical medium such as DVDs and USB drives to trick the users into placing the drives into their computers. In practice, it doesn't really take a whole lot of tricking as users will often insert removable media they have no reason to trust in their computers. As with phishing, the best defense against baiting is training the users ahead of time:
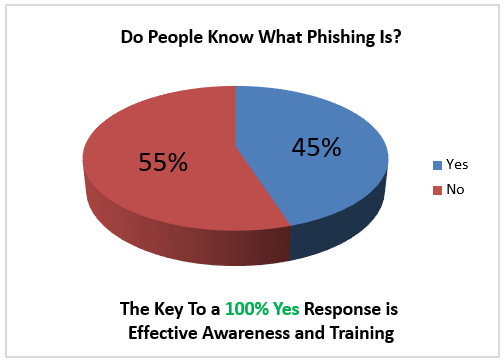
- Awareness training to combat phishing: The most effective countermeasure you can put in place to combat phishing is to raise the awareness of your user population to the threat of phishing and spear phishing. It is easy for the information security professional to become complacent and believe that everyone knows about phishing and that there is no reason to waste time with a training program. However, this couldn't be further from the truth. As information security professionals, we must remember that other parts of the organization exist to perform their specialized work and they do not exist to ponder interesting facts about information security. Other members of the organization sitting in their various departments (HR, finance, manufacturing, and so on) will be surprised to find out that others outside of the organization may want to contact them for the purpose of using them to commit fraud against the organization.
