Ideas Behind Three-tier Computing
With the rise of less costly, faster, and more reliable networking software and hardware, most large enterprises organize their infrastructure on some variant of a three-tiered computing approach, outlined as follows.
First Tier
In its simplest form, computing networks today in any large enterprise environment store their data in a back-end system. This back end, or first tier, is actually where all of the data used in the organization is collected and retrieved for mining, editing, and storage. Typically, this data is organized in a large back-end database, such as the software products from Oracle,[10] Sybase, and Informix.
[10] Oracle is a registered U.S. trademark of Oracle Corporation, Redwood City, California.
Second Tier
This tier is where most of the applications on the system exist, which is why it is also called the application tier. Applications on this level don't mean the desktop-centric user programs, such as Microsoft[11] Word or Excel. Instead, these are the more complex enterprise resource planning (ERP), customer resource management (CRM), and supply chain applications, accounting software, and company billing applications.
[11] Microsoft is a U.S. registered trademark of Microsoft Corporation.
The main point is that these applications all need to interact with the data that is stored on the back end. A company uses the databases on the back end to provide the information used to interact with the applications. The application pulls the data from the back end as demanded and processes it, then puts it right back into the database as the information is modified.
Third Tier
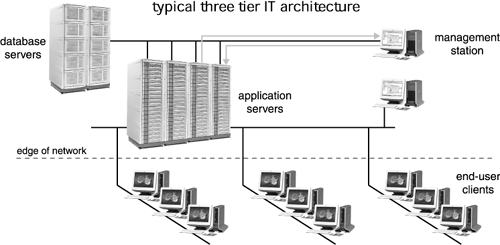
This tier is also called the edge of the network. Though this edge is somewhat sinister sounding, it really refers to where the company's internal network touches the network of the outer world, the vast “cloud” that is the Internet. Here is where the enterprise either branches off to users who may be widely dispersed geographically or to other companies. The edge of the network is where the firewall and the systems that handle data encryption/decryption as well as Web serving exist. A clear representation of this tiered system is seen in Figure 4-1.
Figure 4-1. A Three-Tiered Network System