The easiest way to install Microsoft Windows Server 2003 on a computer while preserving existing domain information, programs, and computer settings is to perform an upgrade installation. This process is easy for member servers and standalone servers, and even easier when upgrading a Windows Server 2003 server to Windows Server 2003 R2. (The process is akin to installing a Windows feature pack.)
Upgrading domain controllers to Windows Server 2003 is more complex, particularly when upgrading a Windows NT 4.0 domain to Windows Server 2003. Before you upgrade a Windows NT 4.0 domain to Windows Server 2003, document the existing network and plan the upgrade process (including whether to perform a domain restructure). Then prepare the domain and computers, and perform the upgrade according to your plan (which states the order in which to upgrade servers and domains, among other things).
To upgrade a Windows 2000 domain controller to Windows Server 2003, or a Windows Server 2003 domain controller to Windows Server 2003 R2, you must update the Active Directory forest and domain schemas before upgrading the operating system itself.
This chapter discusses all these tasks as well as the architectural changes in Windows since Windows NT 4.0, how to upgrade client computers to Windows XP, and how to upgrade the Active Directory functional level to enable advanced functionality after the upgrade is complete.
More Info
To install Windows Server 2003 R2 on a member server or standalone serve, skip ahead to the Chapter 6 section; to upgrade or add a Windows Server 2003 R2 domain controller to an existing Active Directory forest, first refer to the Preparing Domains and Computers section of this chapter.
Windows 2000 and the Windows Server 2003 family introduce numerous architectural improvements as well as some changes to the way Windows domains work. The following sections discuss the changes that are relevant to upgrading: the types of server roles available and the type of domain trusts that are used; new support for devices; Plug and Play (PnP); Power Management; and of course, the addition of the Active Directory service.
In Windows 2000 and the Windows Server 2003 family, the types of server roles are slightly different from those available in Windows NT. Windows NT 4.0 servers can have one of four roles: primary domain controller (PDC), backup domain controller (BDC), member server, and standalone server. Windows 2000 and the Windows Server 2003 servers can have one of three roles: domain controller (DC), member server, and standalone server.
Note
Windows Server 2003 also uses the term "server role" to describe the function a server performs—for example, file server, print server, or SharePoint server.
Windows NT domains are single-master based, with the PDC serving as the master repository for a given domain. The PDC must carry out all changes to the domain. BDCs serve as working backups to the PDC and reduce the load on the PDC by serving client requests themselves. BDCs maintain a current copy of the domain by synchronizing periodically with the PDC; you can upgrade a BDC to the PDC if the PDC server fails or is taken out of service.
Member servers are simply Windows NT servers that belong to a Windows NT domain and are not domain controllers. Member servers usually perform file sharing or print sharing or run some other type of server software, such as Web, Domain Name System (DNS), or Dynamic Host Configuration Protocol (DHCP) server software. You can’t upgrade a Windows NT 4.0 member server to a PDC or BDC without a clean reinstallation of Windows NT, and you can’t demote a PDC or BDC to a member server without reinstalling Windows NT.
Standalone servers are Windows NT servers that do not belong to a Windows NT domain and are instead part of a workgroup. It is important to understand that although a standalone server doesn’t belong to a Windows NT domain, it isn’t limited in its duties as a server. It can still act as a DNS, DHCP, or other type of server, but it can’t act as a central repository for user and group data like a PDC or BDC can. To upgrade a standalone server to a PDC or BDC, you must reinstall Windows NT.
The member server and standalone server roles are unchanged for the Windows 2000 Server and Windows Server 2003 families, but Windows 2000 and Windows Server 2003 replace the PDC and BDC roles with a single domain controller role. Domains in Windows 2000 are finally multiple-master based, with all Windows 2000 or Windows Server 2003 domain controllers acting as peers to one another. Any domain controller can make changes to the domain at will. All domain information is stored in Active Directory, which the File Replication Service (FRS) replicates between all domain controllers. The tradeoff is that Windows 2000 and Windows Server 2003 domain controllers cannot exist on a Windows NT domain until you upgrade the PDC of the domain to Windows 2000 or Windows Server 2003. For more information, see the Planning a Windows NT Domain Upgrade section of this chapter.
You can promote Windows 2000 and Windows Server 2003 member servers and standalone servers to domain controller status, and you can demote domain controllers to member servers or standalone servers without reinstalling the operating system—the only way to demote a BDC under Windows NT. However, as always, it’s preferable not to make more role changes than necessary.
Active Directory is probably the most important new feature in the Windows 2000 Server and Windows Server 2003 family. It is a scalable, easily administered, fault-tolerant directory service that is required by Windows 2000 and Windows Server 2003 domain controllers. Active Directory is also the usual repository for the DNS server database on Windows 2000 and Windows Server 2003 DNS servers.
Chapter 13 and Chapter 14 discuss Active Directory in detail, so this chapter addresses it only briefly to review a few points relevant to upgrading Windows NT domains to Active Directory.
Although Active Directory doesn’t make fundamental changes to the way domains work for end users, it does introduce some important domain structures that affect the way you approach domain design. Active Directory, like the directory service in Windows NT, uses domains as the core unit of logical structure. Domains help organize the network structure to match the organization of the company. Each domain requires at least one domain controller (and preferably more) to store the domain information, and each domain controller can make changes to the domain. See Chapter 3 for more about domain planning.
Active Directory domains use DNS names for domain names instead of the Network Basic Input/Output System (NetBIOS) naming structure of Windows NT domains (although Windows 2000 Server and Windows Server 2003 generate NetBIOS names for backward compatibility). Active Directory domains are hierarchically organized—as required by DNS. Active Directory refers to hierarchically organized groups of domains with a contiguous namespace trees, and groupings of trees with noncontiguous namespaces are known as forests. For example, example.local and all subdomains (support.example.local, finance.example.local, and so forth) belong to a single tree; while a different division of the company (example.com, for example) has its own tree in the forest. Because the companies share their networks and administer them together, they belong to the same forest; the suppliers and partners of the companies would have their own forests. You can establish trust relationships between the forests as necessary to allow them to do business with one another more easily.
Active Directory domains are nearly identical between Windows Server 2003 and Windows 2000 Server; however, upgrading the functional level of a forest and relevant domains to one of the Windows Server 2003 functional levels provides enhanced Active Directory management capabilities, including the ability to rename and move domains within or between forests. For more information, see the Switching Forest and Domain Functional Levels section of this chapter.
Active Directory also introduces the concepts of sites and organizational units (OUs). A site is a group of one or more Internet Protocol (IP) subnets that share local area network (LAN) connectivity. Within a site there can be one or more domains, or a single domain can span multiple sites. See the Planning the Site Topology section later in this chapter for further information.
Organizational units (OUs) are similar to domains in that they are containers for network objects such as user accounts and resources. Unlike domains, however, they do not mark a security boundary, and creating OUs doesn’t require adding domain controllers (because OUs exist within a domain and thus make use of the existing domain controller infrastructure). OUs in Active Directory provide an excellent way to provide organization within a domain without the need for additional security policies and domain controllers. You can easily convert OUs to domains, and domains to OUs, which makes them very flexible. See Chapter 9 for more information about the uses and creation of OUs.
The first domain you create in Active Directory automatically becomes the forest root domain—the top-level domain in the Active Directory hierarchy. If you create additional domain trees (with their own contiguous namespaces), Active Directory creates transitive two-way trusts between the trees and the forest root domain, as if the trees were child domains. Indeed, from a trust and replication perspective, it appears that the subsequent trees are children of the forest root, even though they use completely different namespaces.
Besides its significance as the hub of replication between trees, the forest root domain also contains the Enterprise Admins and Schema Admins groups, which have forest-wide administrative scope.
Because the forest root domain is so important, fault-tolerance and recoverability is critical. If a regional catastrophe wiped out all domain controllers and backups in the forest root domain, the Enterprise Admins and Schema Admins groups would be forever lost, and you would have to re-create the entire forest.
To help reduce the need to alter the forest root domain, you can create a dedicated forest root domain exclusively for forest-level administration and replication, and place the majority of accounts and resources in child domains. Because there are few user accounts and resources in a dedicated forest root domain, Active Directory structures that consist of a dedicated forest root and a single child domain are often said to be using the Single Global Domain Model. Active Directory structures that consist of a dedicated forest root with multiple child domains are referred to as using the Regional Domain Model—a nod to the fact that the child domains are often organized geographically.
Trust relationships are an important component of large networks that consist of multiple domains. Simply stated, a trust relationship is a policy that enables users from one domain to access resources in another domain.
For example, say that a user, Susan, in the domain Administration, wants to access a resource in the domain Manufacturing, and that the Manufacturing domain trusts the Administration domain. When Susan attempts to access the resource, the resource must verify that she has an account that has permission to access it. To authenticate Susan, the resource in the Manufacturing domain contacts its local domain controller (DC, BDC, or PDC), which in turn queries a domain controller in the Administration domain and verifies that Susan has a valid account and that the account belongs to a group permitted to access the resource.
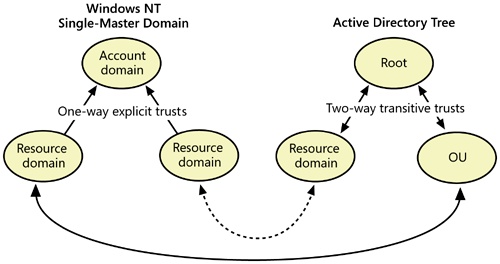
Among and between Windows NT 4.0 and earlier domains, all trusts are nontransitive, meaning that each trust is a one-way relationship between two domains that you must explicitly create. For two domains to trust each other, you must create two separate trust relationships—one for each direction.
A nontransitive trust is also strictly limited. For example, suppose that the domain Finance also trusts the domain Administration (as shown in Figure 6-1). When nontransitive trusts are involved, this statement tells you only that the Finance and Manufacturing domains both allow users from the Administration group access to their domains. It does not tell you anything about the relationship between the Finance and Manufacturing domains, nor does it indicate whether Administration, in turn, allows either Finance or Manufacturing to authenticate users. You must create each trust relationship separately and explicitly.
Active Directory introduces transitive trusts. Transitive trusts are always two-way, and they support pass-through authentication. Creating a trust between the Administration and Manufacturing domains (now probably called administration.example.local and manufacturing.example.local) automatically means that users in each domain can be authenticated and be eligible to access resources in the other domain (though they still need to have proper permissions, of course).
Pass-through authentication comes into play with child domains. With Active Directory domains, users in the child domain can use the parent domain’s trusts by means of the automatic two-way transitive trust that Active Directory creates between the child domain and the parent domain. For example, let’s say you create a widgets.manufacturing.example.local child domain. Users in this domain are automatically eligible to access resources in the manufacturing.example.local domain (the parent domain) as well as the example.local domain (the parent domain of the parent domain—the grandparent domain, if you will).
Transitive trusts become available after you upgrade a domain to Active Directory. Despite some confusion over the matter, they do operate in domains that use the Windows 2000 mixed functional level and work between trees in a forest, but they do not apply to remaining Windows NT domains in your company or to clients connected to Windows NT BDCs. (These domains and clients rely on existing one-way nontransitive trusts.) Explicit one-way trusts are also available between Active Directory–based domains, but you must create them manually.
Windows Server 2003 provides additional capability to set up one-way or two-way transitive trusts between forests, and the ability to rename and move domains within and between forests after you upgrade the forests to the Windows Server 2003 forest functional level.
Table 6-1 shows the possible trust relationships between different types of domains.
Table 6-1. Trust relationships between domains of different types
Windows NT Domain | Active Directory Domain (Same Forest) | Active Directory Domain (Different Forest) | |
|---|---|---|---|
Windows NT Domain | One-way trust[a] | One-way trust[a] | One-way trust[a] |
Active Directory Domain (Windows 2000) | One-way trust[a] | Two-way transitive trust (One-way trust available) | One-way trust[a] |
Active Directory Domain (Windows Server 2003 forest functional level) | One-way trust[a] | Two-way transitive trust (One-way trust available) | Two-way transitive forest trust (One-way trust available) |
[a] You can establish one-way trusts in both directions, simulating a two-way trust. | |||
Hardware support for the Microsoft business operating systems has come a long way. Windows 2000 shed the Windows NT legacy of nonexistent drivers, device configuration nightmares, and poor support for modern technologies by introducing top-of-the-line hardware support for the whole alphabet soup: Plug and Play (PnP), Universal Serial Bus (USB), Institute of Electrical and Electronics Engineers (IEEE) 1394 (Firewire), and Advanced Configuration Power Interface (ACPI) device configuration and power management.
Note
An up-to-date, ACPI-compatible BIOS is required for full use of PnP and power management. The ACPI BIOS should support the Advanced Programmed Interrupt Controller (APIC) standard, which raises the 15 interrupt request (IRQ) limit and enhances IO performance as well. (All multiprocessor systems support APIC, as do all systems certified for use with Windows Server 2003 or Windows XP.) If the system doesn’t boot after upgrading a standard Programmed Interrupt Controller (PIC) BIOS to APIC operation, restore the old BIOS or reinstall the operating system. Windows Server 2003 supports legacy Advanced Power Management (APM) and PnP BIOSs, but their features are limited.
Device drivers in Windows 2000 also changed to enhance system stability and to increase the number of devices supported. Windows 2000 supports the Win32 Driver Model (WDM), enabling most WDM drivers to work interchangeably with Windows 2000, Windows XP, Windows Server 2003, Windows 98, and Windows Me. Device Driver Signing triggers an alert when you install drivers that Microsoft hasn’t tested and digitally signed. (Administrators can create policies blocking the installation of unsigned drivers.) Microsoft also fine-tuned the driver model to reduce system instability and to facilitate PnP and power management. Windows XP added device driver rollback, and support for CD-RW drives and USB 2.0 devices. Windows Server 2003 added support for Fibre Channel, Hot Plug PCI, and storage area networks (SANs), among other technologies.
However, broad device driver availability is only part of the equation for servers. Because device drivers are one of the leading causes of system instability, simply having a driver isn’t enough. It is very important that servers use only device drivers that are Microsoft certified and digitally signed.
Note
The vast majority of Windows 2000 drivers work fine in Windows XP and Windows Server 2003. Although many Windows NT 4.0 drivers work in Windows Server 2003, they do not support power management or Plug and Play and can more easily decrease the stability of the operating system. For this reason, most companies use Group Policy to block the installation of Windows NT 4.0 drivers. Windows 98 and Windows Me WDM drivers often work fine on Windows XP systems, but avoid them on servers for stability reasons—drivers are a leading cause of system crashes. Windows 95, Windows 3.x, and MS-DOS drivers absolutely don’t work in Windows 2000, Windows XP, or Windows Server 2003.
Software support, like hardware support, is another area where Windows has made great advances since Windows NT 4.0, which is largely incapable of running applications written for other versions of Windows, such as Windows 98. Windows Server 2003 and Windows XP run many popular Windows 98 and Windows Me applications out of the box and support many more with Application Compatibility Updates, which are available from Microsoft Update (http://update.microsoft.com/microsoftupdate).
Windows XP and Windows Server 2003 also provide special compatibility modes that simulate key aspects of the Windows 95, Windows 98, Windows NT, or Windows 2000 operating systems, allowing end users to take additional steps to run incompatible programs. Microsoft also provides the Application Compatibility Toolkit (see http://www.microsoft.com/technet/prodtechnol/windows/appcompatibility/default.mspx) that administrators can use to inventory deployed applications, evaluate any compatibility problems, and create custom compatibility fixes for the applications. See Chapter 29 for more information about application compatibility technologies.
Note
Upgrading an existing Windows 98–based or Windows Me–based system presents additional complexities. Vendors often have one version of their software for Windows 98 and Windows Me, and another for Windows NT, Windows 2000, and Windows XP. Furthermore, the same application is installed differently depending on the operating system involved. Consequently, many applications require vendor-provided migration files (upgrade packs) during the operating system upgrade, or they must be uninstalled and then reinstalled after the upgrade completes.
Upgrading a Windows NT 4.0 domain to Active Directory isn’t quite the three-click process that you perform when upgrading a single Windows NT 4.0 workstation to Windows XP. In fact, considerable planning is necessary before you even start Windows Setup on the first computer. You must upgrade some computers, such as the PDC and BDCs, in a specific order, while you can upgrade other computers, such as client computers and Windows NT member servers, at any time.
The following sections are essential for anyone planning a Windows NT 4.0 domain upgrade. They cover documenting an existing network, making a recovery plan, planning the Active Directory forest, and developing an upgrade strategy. Subsequent sections cover preparing for the upgrade, the actual upgrade process, and finally, switching an upgraded domain into native Windows 2000 or Windows Server 2003 mode.
Note
You must upgrade the Active Directory schema before adding Windows Server 2003 domain controllers to an existing Windows 2000 Active Directory forest or before adding Windows Server 2003 R2 domain controllers to a Windows Server 2003 or Windows 2000 Active Directory forest. See the Updating the Active Directory Schema section of this chapter for more information.
If your current domain structure is unsatisfying, it might be tempting to start from scratch, migrating accounts and resources into a fresh Active Directory domain. Resist this impulse if possible.
When migrating to a new domain, you must select a new domain name (a political nightmare in its own right), update all existing links and e-mail addresses, and educate users how to log on and find resources in the new domain. In addition, it’s important to realize that everyone needs to sign off on a decision of this magnitude, and that can be tough. The decision to migrate to a new domain structure is political, not technical.
With that said, it makes sense to look at migrating to a new domain or domain tree if doing so makes it possible to merge two or three separate domains or trees into a single domain or tree. Just remember to carefully weigh the pros and cons and get everyone’s approval before tackling this complex issue. If you choose to migrate to a new domain, refer to the Active Directory for Microsoft Windows Server 2003 Technical Reference for information about the Active Directory Migration Tool (ADMT) and other tools that can help make migration easier.
Note
An in-place domain upgrade is a domain upgrade that you perform while leaving the domain intact. You can also upgrade domains by removing the PDC from the domain, and upgrading it offline. Meanwhile, the BDCs provide services to the existing domain. After testing the upgraded PDC, bring it back into the production domain and upgrade the remaining BDCs.
The first step in planning an in-place domain upgrade is to document the current network structure. To do so, take an inventory of the following network attributes:
The sections that follow describe how to document each of these features.
Important
Windows Server 2003 digitally signs all server message block (SMB) protocol communications by default for greater network security. Because of this, Windows 9x systems must install the DS Client Pack (found on a Windows 2000 Server CD-ROM in the clientswin9x folder) and Windows NT 4.0 systems must be running Service Pack 4 or newer to access Windows Server 2003 domain controllers. Computers running Microsoft Windows for Workgroups or Mac OS X do not at present support SMB signing. If you can’t upgrade or retire these systems, you can disable this setting using Group Policy—the location is Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity OptionsMicrosoft Network Server: Digitally Sign Communications.
The type of domain structure, or model, that the existing Windows NT domains use determines how you implement Active Directory trees and forests. Table 6-2 summarizes the types of domain models that might be in use.
Table 6-2. Domain models available in Windows NT
Domain Model | Description |
|---|---|
Single-domain | A single Windows NT domain |
Single-master | One account domain and multiple resource domains |
Multiple-master | Multiple account domains with two-way trusts between them and multiple resource domains that trust all master domains |
Complete trust | Every domain is a resource domain and an account domain, with each domain trusting every other domain |
Document existing trust relationships, and determine whether all trusts are still necessary. Windows preserves existing trust relationships during an upgrade to maintain compatibility with Windows NT 4.0 BDCs. However, Windows doesn’t import trusts with Windows NT 4.0 domains into Active Directory. Re-create these trusts in Active Directory before upgrading or taking the last BDC in the domain offline.
If you upgrade any domains into separate forests and want to maintain trust relationships between the forests, delete the existing trusts (which use NetBIOS domain names) after upgrading the PDC and re-create them using fully qualified DNS domain names. See Chapter 14 for information about working with trusts in Active Directory
Record the current number of account domains and resource domains. Also think about whether you want to restructure your domains, either before or after you upgrade the network to Active Directory.
If the company has already deployed DNS, carefully document the namespaces currently in use. You cannot easily rename domains after you create them, and they must be unique on the network.
A crucial and sometimes forgotten step in documenting a network is to make an inventory of the servers. Record the server names, hardware capabilities, locations, operating system version, and service pack levels of the following types of servers, and evaluate any compatibility issues or problems with the servers before you begin the upgrade process:
Domain Controllers. You must upgrade the Windows NT 4.0 PDC before upgrading any other domain controllers in the domain or adding any Windows 2000 or Windows Server 2003 domain controllers if you want to maintain the existing domain. You can upgrade the BDCs after that.
Windows Server 2003 and Windows 2000 replace the LAN Manager Replication Service feature of Windows NT with the file replication service (FRS), which Windows installs automatically on all domain controllers. If you must maintain compatibility with the LAN Manager Replication Service, see Microsoft Knowledge Base Article 248358 or refer to the Microsoft Windows Server 2003 Resource Kit.
Note
The preferred way to upgrade a domain is to purchase a new server to use as the PDC to upgrade. (Install Windows as a BDC, and then promote it to PDC.) This ensures that the computer is modern, compatible, and fast enough to adequately run Windows Server 2003. It also minimizes the amount of junk residing on the hard drive and in the registry, providing the "closest-to-clean installation" experience possible.
File and Print Servers. You can easily upgrade file and print servers to Windows Server 2003 or migrate the server settings and data to a server running Windows Server 2003. Migrating to a new server can yield performance gains from newer hardware and can also help consolidate servers. Use the Microsoft File Server Migration Toolkit (available for download at http://www.microsoft.com/windowsserver2003/upgrading/nt4/tooldocs/msfsc.mspx) or Print Migrator to streamline the migration process. (See Chapter 8 for information about migrating print servers.)
DNS, DHCP, and Windows Internet Name Service (WINS) Servers. Upgrade Windows NT 4.0 DNS, DHCP, and WINS servers to Windows Server 2003 or Windows 2000 Server to maximize functionality and to minimize problems.
Windows NT RRAS Servers. Windows NT 4.0 Routing and Remote Access Service (RRAS) servers need access to a real BDC for user information. They work erratically while on a mixed-mode Active Directory domain, and cease to work entirely after you upgrade the last BDC. For this reason, upgrade any Windows NT 4.0 RRAS servers before you start the domain upgrade process (if practical), or immediately after stabilizing the newly upgraded domain with two or more domain controllers.
Note
When setting up an Active Directory domain, the Active Directory Setup Wizard gives you the option of weakening the security settings for Active Directory to support pre–Windows 2000 clients. (They’re talking about Windows NT 4.0 RRAS servers here.) Don’t do it—instead upgrade or replace these servers with Windows 2000 or Windows Server 2003 RRAS servers.
Windows NT 3.51 Servers. If there are still Windows NT 3.51 servers or clients on your network, upgrade them or get rid of them. If you absolutely can’t part with your Windows NT 3.51 (or earlier) computers, leave an existing domain running under Windows NT 4.0 (or create one if necessary) and establish the appropriate trust relationship between this domain and your Active Directory structure. Just keep them off Active Directory domains.
Security Alert
Windows NT 3.51 computers joined to an Active Directory domain can deny access to user or group logon events, or they can incorrectly grant access to users or groups to which you have denied access. These difficulties and security breaches occur because of the way in which Windows NT 3.51 generates access tokens when a user logs on to the server.
NetWare Servers. Determine whether you want to synchronize Active Directory with Novell Directory Services (NDS). Check the release notes included on the Windows Server 2003 CD-ROM for any compatibility issues with NetWare. (Chapter 27 discusses interoperability.)
Samba Servers. Samba servers might require access to a real Windows NT 4.0 domain controller (instead of a Windows Server 2003 running the PDC emulator). Record the location and capabilities of any Samba servers on the network, and make a special note of whether they require access to Windows NT domain controllers. (If they do, postpone switching the network to a native mode until this issue is cleared up.) Many Samba servers also do not support SMB signing.
Other Application Servers. Evaluate all application servers carefully for known issues with Windows 2000, Windows Server 2003, and Active Directory.
Important
Windows NT 4.0 Enterprise Edition clusters cannot perform a rolling upgrade directly to Windows Server 2003. (A rolling upgrade allows the cluster to stay online while you upgrade each node one at a time.) To deal with this, either take the cluster offline and upgrade each node, or perform a rolling upgrade to Windows 2000, and then Windows Server 2003.
There are several steps to take when planning the Active Directory forest for your organization, including designing the Active Directory structure, choosing DNS names, and planning the site topology. This section briefly covers these steps. See Chapter 3 for additional information about planning the namespace and the domain structure. Refer to the Windows Server 2003 Resource Kit for more in-depth planning help.
When designing the Active Directory structure for an existing Windows NT–based network, take into consideration the current Windows NT domain model: single domain, single-master domain, multiple-master domain, or complete trust. (See Table 6-2 for a summary.) This section guides you through designing an Active Directory domain structure appropriate for your existing network model.
Note
When designing your Active Directory structure, start simple. If it’s possible to end up with a single domain, begin with that plan. Explore designs that are more complex than necessary, but go with the simplest design that fits—it’ll be easier to understand, administer, and troubleshoot (especially when you start using Group Policy).
The Windows NT single-domain model consists of a single domain, with all accounts and resources stored together.
The single-domain model is easy to upgrade: the single domain under Windows NT becomes the forest root domain in Active Directory. You can then use OUs to organize the accounts and resources and to delegate some of the administrative burden.
Large domains and networks that might be reorganized at some point should consider creating a dedicated forest root domain (as described in the Real World sidebar Using Dedicated Forest Root), and then upgrading the Windows NT domain as a child domain of the forest root. This requires additional resources and adds some complexity, but not as much as adding a normal domain would.
The Windows NT single-master–domain model consists of one master domain that contains all user accounts, and one or more resource domains that trust the master domain and contain only computer accounts and other resources.
If you have a single-master–domain model, create a dedicated forest root domain (discussed in the Real World sidebar Using Dedicated Forest Root), and make the former master domain the first child domain. Then add the resource domains as second-level child domains.
If the company has a centralized network structure, after upgrading the domains to Active Directory and switching the master domain to Windows 2000 or Windows Server 2003 native mode, consider restructuring the domains into a single child domain. You can use OUs either to mimic the resource domains or to organize them more logically with the accounts and resources grouped and organized according to the company’s structure.
Merging the resource domains back into a single child domain under the dedicated forest root offers a number of advantages. Because there are fewer domains to manage, the administrative burden is less. You can use OUs to create a detailed network structure without dealing with trusts. In addition, you can delegate administrative authority to the OUs, giving you the flexibility to handle the administrative tasks the way you want. You can also perform Active Directory queries faster and more efficiently in a single domain. Finally, because OUs don’t require domain controllers, there is the potential to free up some underused computing resources for other tasks. Figure 6-2 shows a single-master Windows NT domain converted to an Active Directory tree using a dedicated forest root domain, with a resource domain converted to an OU after switching the account domain to Windows 2000 or Windows Server 2003 native mode.
A company with a more decentralized organization, or one with different business units, might want to keep multiple domains but convert its resource domains into full-fledged domains, with both resources and user accounts. (With Active Directory, there is no reason to keep distinct resource domains.) This arrangement allows users to be in the same domain as the resources they use, reducing traffic and making it easier for users to find and access the resources they need. However, you must wait until you upgrade all relevant domains and switch the target domain to Windows 2000 or Windows Server 2003 native mode before you can move the accounts. This is because an object that is moved between domains loses its ability to access resources to which it formerly had access, unless the native mode SIDHistory feature can provide the resources with the object’s old security identifier (SID).
The multiple-master–domain model in Windows NT consists of a network with two or more master domains that contain all the user accounts, and multiple resource domains that trust each master domain and contain all the computer accounts and other resources. Large networks use this model to circumvent the Windows NT limit of 40,000 objects per domain.
Because of the flexibility and simplicity the Active Directory single-domain or single global domain models offer, many companies with a multiple-master–domain model choose to consolidate their domains into a single Active Directory domain (with or without a dedicated forest root domain) and use OUs to hierarchically structure their network. If you choose to consolidate the domains, create the forest root domain first (if applicable) and then perform the domain upgrades just as if you were going to preserve the existing domain structure. After you upgrade the domains and switch the target domain to a native-mode functional level, you can move all accounts into the single domain without the need to reassign permissions on the objects.
To create a single-domain tree (with a contiguous namespace) during the domain upgrade, create a dedicated forest root domain and stabilize it with a couple of domain controllers. (See the Real World sidebar Using Dedicated Forest Root, in the previous section.) Then upgrade the master domains one by one, adding them to the Active Directory tree as children of the forest root, which also serves as the tree root domain in this example. Figure 6-3 shows a multiple-master Windows NT domain converted to an Active Directory tree, with two resource domains converted to OUs after switching the account domains to native mode. After you upgrade the account domains, upgrade the resource domains and add them to the tree as children of the account domains (grandchildren of the forest root). Once the upgrade is complete, switch the account domains to a Windows 2000 or Windows Server 2003 native mode, and consider consolidating the resource domains into the account domains, using OUs when applicable.
If you want to keep each master domain in an authoritative role, create a multiple-tree forest. First, create a dedicated forest root domain to serve as the root for the forest. Dedicate this domain exclusively to forest administration; do not create your users or resources in this domain. Then seed each master domain as the root for a new tree in the forest. (This is called the tree root domain.) In this case, it doesn’t matter which master domain you upgrade first, but you must upgrade the master domain for each tree before upgrading the resource domains.
The Windows NT complete-trust model involves multiple domains that all trust each other.
Highly decentralized companies or companies that implemented domains in a piecemeal fashion and gradually connected them often use the Windows NT complete-trust model. The model provides a lot of autonomy and flexibility for each master domain, but it also results in a large administrative burden.
When upgrading an enterprise that uses the complete trust model to Active Directory, many companies try to consolidate their domains into a single tree or even a single domain. If you want to maintain the autonomy of the current domain structure of the complete-trust model, set up each current master domain as a new tree root domain. When you create the Active Directory structure like this, you automatically reduce the amount of administration necessary, as all trusts between domains in an Active Directory tree or forest are automatically transitive. (If this is undesirable, create multiple forests.)
When you upgrade the network, first create the forest root domain, preferably by creating a dedicated forest root. (You could also upgrade an existing domain and seed it as the forest root, although Microsoft discourages this.) When you have the forest root domain up and running with a couple of domain controllers, you can upgrade the account domains and add them as children of the forest root or as roots in new trees. If necessary, after upgrading domains, you can replace any transitive trusts with Windows NT–style one-way trusts to limit access within a forest.
Note
A one-way trust can also be set up to permit a legacy Windows 3.51 or Windows NT 4.0 domain or a child domain of another forest (such as one belonging to a business partner) to access a specific domain in the tree or forest. When you set up an explicit one-way trust in Active Directory, it works identically to trusts in Windows NT—that is, the trust is not transitive. If you grant a domain access to a single domain in the tree or forest, the trusted domain cannot access any other domain in the tree, even though the tree is linked with transitive trusts.
After conceiving an Active Directory structure, it’s time to name the baby. If you haven’t read Chapter 3 yet, you might want to refer to it for namespace planning information. After you settle on a naming convention and decide whether to use separate internal and external domain names, it’s time to choose the DNS names for the forest root domain and any additional trees. To do so, use the following steps as a guide—just remember that domain names are highly political in nature, so if you’re fond of your job, don’t create the domain structure and namespace without first getting the approval of the authorities in your organization.
Identify what domain names are currently in use with your company. If you use separate domain names for the corporate network and the company’s Internet presence, choose the one in use for the corporate network. This name should be a registered, Internet-valid DNS name so that it’s guaranteed to be unique.
Choose a domain name suffix to use for the forest root domain, and by extension, the entire forest. Windows uses .local by default, but if you plan to include any Mac OS X clients in the forest, choose a different suffix such as .office or .lan. (Note that .local conflicts with the Rendezvous feature of Mac OS X, though there are some workarounds.)
Choose what domain name prefix or full domain name to use for the forest root domain name. This is a crucial decision because the forest root can’t be deleted or easily changed, and if you’re creating a single tree forest, the forest root name (corp.example.local) also serves as the root name for the tree. (Child domains append their names to the front of the root domain name—for example, marketing.corp.example.local.)
This prefix should conform to the following specifications:
Not currently in use on the network (if you’re going to use a dedicated forest root domain).
Isn’t used on the Internet. It’s fine to use your company’s Internet domain name (for example, example.local). Just remember to add a prefix to it so that local clients don’t get confused trying to access your company Web site (for example, use corp.example.local).
Isn’t likely to ever become outdated. (Broad geographical names work well unless you live in Turkey or Russia.)
Is 15 characters or fewer, and consists only of Internet standard characters (A-Z, a-z, 0-9, and "-"). This allows legacy clients to use the prefix as the NetBIOS domain name.
Is easy to remember and makes sense.
If you’re creating multiple trees, decide what DNS names to use as the root for each tree. Once again, get explicit buy-in from all decision-makers on the project on each of these names because they’re difficult to change and users see them every day.
Arrange to have the forest root DNS prefix ownership, along with the domain names of any additional trees, delegated to the forest administrator, which is likely you. When the actual Active Directory domains are set up or upgraded, you can delegate the ownership of any additional DNS domains to the administrator responsible for DNS in that domain. (See Chapter 14 and Chapter 16 for help with this.)
Sites, an important new feature of Active Directory, define the boundaries of LAN connectivity, making WAN links more efficient. When you set up sites that mark the sections of the network that have high-speed symmetrical connectivity (10 Mbps is a good number to use), Active Directory tunes the way it uses the WAN links. It reduces the frequency of replication between sites and directs clients’ service requests, such as client logon events or directory searches, to domain controllers that are available locally.
Sites are independent of domains. Whereas domains typically mirror a company’s logical organizational structure, sites mirror the physical network structure of a company. A single site might consist of one or more domains, trees, or even forests; or a single domain might span multiple sites. A site can consist of a single IP subnet (which is often the case because subnets frequently mark physical network boundaries) or multiple IP subnets, but all subnets must share reliable, high-speed connectivity to be a part of a single site.
Note
It is becoming increasingly common for a company’s WAN link to be as fast as an internal LAN. However, the WAN link charge might be based on usage, or a company might use the link heavily for real-time, bandwidth-intensive tasks such as video, reducing the available bandwidth. In such cases, you might still want to set up a site structure for the Active Directory forest to avoid burdening the WAN link with excessive replication and service requests.
When planning to upgrade a Windows NT domain to Active Directory, it is important to plan the site topology so that you can set up the site structure promptly after upgrading. Ask yourself the following questions and record your answers:
Two types of connections are available for intersite replication: point-to-point synchronous low-speed remote procedure call (RPC) and Simple Mail Transfer Protocol (SMTP). Any domains that span multiple sites must have at least a point-to-point synchronous low-speed RPC connection between the sites within the domain. This connection is required because you can’t use SMTP for intersite replication between domain controllers in the same domain; you can use SMTP links only for schema, configuration, and global catalog (GC) information replication. Therefore, if you have multisite domains, double-check the link between the sites to make sure you have adequate connectivity for this setup.
You would be wise to have a global catalog server on each site to allow a local domain controller to service requests for any resource in the forest without having to use the WAN link. However, the global catalog server shouldn’t be the same server as the infrastructure master unless there are no other domain controllers in the domain, because this configuration breaks the infrastructure master’s ability to update other domain controllers in the domain. (See Chapter 15 for information about the infrastructure master role.)
Place at least one DNS server in each site, and have a minimum of two domain controllers per site for redundancy. (This isn’t as important for remote sites with a small number of clients.)
Note
Place at least one Windows Server 2003 domain controller in each site. Doing so allows Windows Server 2003 to take over the topology generator role, improving intersite replication efficiency and scalability, even when the rest of the domain controllers are running Windows 2000. Switching to Windows Server 2003 functional level results in additional efficiency and scalability improvements, including automatically selecting bridgehead servers and allowing the maximum number of sites per domain to increase to 3000. (The limit is 300 otherwise.)
Upgrading a Windows NT 4.0 domain involves a fair amount of risk. If the PDC fails the upgrade and there aren’t any BDCs available, the entire domain fails. To protect your network from this unhappy possibility (and others), you need a recovery plan.
The following sections provide specific recommendations for safeguarding a network from disasters.
Be sure all domains you plan to upgrade have at least one BDC in addition to the PDC. This prevents the domain from being orphaned (or lost entirely) if the PDC fails the upgrade. Having a working and recently synchronized BDC allows the network to function (almost) normally while you upgrade the PDC. (Some programs or services such as WINS don’t like it when the PDC is gone.)
Back up each system before upgrading it. This is perhaps overly cautious on some desktop systems that do not store any data locally, but it’s important on servers, especially domain controllers. Also, make sure you test the backups by restoring randomly selected data from the backup, or even performing a full restoration into a Microsoft Virtual Server environment. (See Chapter 29 for information about Microsoft Virtual Server.)
Synchronize the PDC with all its replication partners before upgrading it. If the PDC fails the domain upgrade, you can promote a BDC to the PDC and the domain won’t lose any changes.
Freshly synchronized BDCs and new tape backups of the PDC protect you from most disasters. However, it’s good insurance to take a freshly synchronized BDC offline before upgrading the PDC. This provides you with a quickly available, working backup of the domain as it existed before you started the upgrade process. If the upgraded PDC replicates bad domain information to the BDCs or the domain becomes damaged in some other way, having an offline backup allows you to go back to a healthy copy of the domain.
To prepare a BDC to act as an offline domain backup, synchronize the BDC with the PDC domain, back up the BDC, and then disconnect the network cable to the BDC. If a major disaster occurs after upgrading the PDC and it is necessary to restore the domain to its pre–Active Directory state, use the following steps:
Demote any Windows 2000 or later domain controllers on the network back to member server status.
Reconnect the offline BDC to the network.
Promote the formerly offline BDC to a PDC.
Synchronize the new PDC with the other BDCs on the network. This returns the domain to the state it was in immediately before you took the BDC offline.
Important
All changes to the domain performed after taking the backup BDC offline are lost if you bring the BDC back online and promote it to a PDC. Because of this, keep a record of any changes you make (such as creating or deleting accounts, and changing group memberships or trust relationships). By doing so, in the event of a disaster you can manually re-create the lost changes.
After documenting the existing network infrastructure, making a recovery plan, and designing the Active Directory trees and sites, you’re ready to put it all together and create an actual upgrade plan. This section presents some general guidelines that apply to all domain upgrades, as well as some tips for specific domain models.
As mentioned earlier in this chapter, Windows NT 4.0 RAS servers don’t play well with Active Directory networks. Because of this, upgrade or replace any Windows NT 4.0 RAS servers with Windows Server 2003 or Windows 2000 member servers running Routing and Remote Access (RRAS) before upgrading the PDC and starting the domain upgrade. If this isn’t feasible, put all Windows NT 4.0 RAS servers near the top of the list of servers to upgrade after you upgrade the PDC and a few BDCs.
Start the domain upgrade by carefully examining the current PDC. Although Active Directory uses peer-based, multiple-master domain controllers, the first domain controller retains extra services that in some cases you cannot easily move to other domain controllers. These services include the global catalog server, the Operations Master, and the PDC emulator. (The PDC emulator provides services for Windows NT, Windows 95, Windows 98, and Windows Me clients, and also performs some tasks in a pure Windows 2000, Windows XP, and Windows Server 2003 environment.)
Because of these additional roles the upgrade PDC must perform, the first PDC should be especially fast, powerful, and reliable. The best way to ensure that the PDC is fast enough is to buy a powerful new server and install Windows NT 4.0 Server on it as a BDC with Service Pack 6a and the latest hot fixes. Promote the server to your PDC, let it sit for a little while, and then take it offline and perform the upgrade to Windows Server 2003. This ensures that your first domain controller is on the most powerful and up-to-date hardware you have available, and it provides the closest-to-clean install experience possible from an upgrade.
If you want to create a dedicated forest root domain, you need to do this before you upgrade the PDC. After you have the new domain up and running with a couple of domain controllers, you can upgrade the PDC and join it to this new tree as a child domain.
If you have any Windows NT 4.0 RAS servers or computers running Windows NT 3.51 or earlier, upgrade or retire these systems as discussed earlier in this chapter.
Disable the LAN Manager Replication Service on all Windows NT 4.0 servers because it’s incompatible with Active Directory networks. The file replication service (FRS) feature of Windows 2000 and Windows Server 2003 domain controllers replaces it. (Note that the new DFS Replication service of Windows Server 2003 R2 does not replace FRS for domain controller replication.)
More Info
If you want to synchronize FRS with LAN Manager Replication Service, see the "Synchronize File Replication Services" topic in the Windows Server 2003 Deployment Guide at http://www.microsoft.com/technet/prodtechnol/windowsserver2003/library/DepKit/6e81e1f0-7d13-480b-be24-5887f8bfa3cc.mspx. This topic discusses a workaround using tools from the Windows Server 2003 Deployment Kit companion CD.
The first server you upgrade must be the Windows NT PDC in the account domain you want to use as the root of the new Active Directory tree. This is true whether the tree you’re creating is the first in the forest or the twentieth in the third forest—upgrade the PDC first if you want to upgrade the Windows NT domain instead of creating a new domain.
Note
If you’re going straight from Windows NT to Windows Server 2003–based domain controllers without passing "Go" (Windows 2000), consider using the Windows Server 2003 Interim functional level. This mode offers a number of advantages over Windows 2000 mixed mode, and it still allows Windows NT BDCs (but no Windows 2000 domain controllers) to operate in the domain. For more information, see the Switching Forest and Domain Functional Levels section later in this chapter.
It’s important to get another Windows Server 2003 or Windows 2000 domain controller online quickly after you upgrade the PDC. If the sole Windows Server 2003 domain controller goes down, you’ll have to promote a BDC to PDC and start over again (though most changes will survive, except any changes incapable of being stored on a Windows NT BDC).
Another reason that it’s important to quickly add additional domain controllers is because computers running Windows 2000, Windows XP, or Windows Server 2003 authenticate preferentially with Windows Server 2003 and Windows 2000 domain controllers. If there are too few Windows Server 2003 or Windows 2000 domain controllers available, clients might not be able to authenticate during busy times. (Most clients can log on using cached credentials, but you should nonetheless add domain controllers quickly.) If you can’t add additional Windows Server 2003 or Windows 2000 domain controllers in a prompt manner, configure the Windows Server 2003 domain controllers to appear to all clients as Windows NT 4.0 domain controllers. To do so, refer to the Windows Server 2003 Resource Kit or Knowledge Base Article 298713.
Because the master copy of the domain information is stored in Active Directory after you upgrade the PDC, you don’t need to upgrade BDCs. Instead, you can replace them with new Windows Server 2003 or Windows 2000 domain controllers, or perform clean installations on BDCs and then install Active Directory when finished.
If you do choose to upgrade BDCs, do so one at a time, and pause before upgrading or retiring the last BDC. Verify that you’ve dealt with all incompatible clients and servers, re-create in Active Directory any trusts in that are established with Windows NT 4.0 domains, and to be extra safe, take the last BDC offline for a week or more before upgrading or retiring it. If nothing erupts in flames, go ahead with your plan.
Important
Make sure that the first domain controller is visible on the network when upgrading a BDC. When you upgrade a BDC, it replicates only with the PDC emulator. If the former PDC isn’t available, the BDC takes over the PDC emulator and other roles, creating serious problems when the first domain controller comes back online.
Upgrade member servers and workstations whenever you want—either before or after you upgrade the domain. Windows 2000, Windows XP, and Windows Server 2003 clients and member servers work perfectly well with Windows NT domains; however, the benefits of Active Directory aren’t available to clients and member servers until you upgrade the domain.
Schedule the domain upgrade at a time that has the lowest impact on the user population. It’s best to avoid upgrades during major projects and during the busiest times of year if possible. Even perfect upgrades produce some impact on the users, especially if you perform any domain restructuring or consolidation.
It’s important to ascertain whether Active Directory is functioning properly after a domain upgrade, before it’s too late to back out and restore the Windows NT 4.0 domain. Use these criteria as a starting point:
Users can log on successfully.
Users can access e-mail.
Users and groups can access resources for which they have permissions, including resources in other domains (when applicable).
Active Directory is functioning properly. (Use Dcdiag.exe.)
Replication works properly. (Use Repadmin.exe and Nltest.exe to verify this.)
The first step in the actual upgrade process for servers running Windows NT 4.0 or Windows 2000 Server is to prepare the domains and computers for the upgrade. This important step streamlines the upgrade process and makes it go as smoothly as possible.
You can upgrade to Windows Server 2003, Standard Edition, from the following operating systems:
Windows 2000 Server
Windows NT 4.0 Server with Service Pack 5 or later
Windows NT 4.0 Terminal Services with Service Pack 5 or later
To upgrade to Windows Server 2003, Enterprise Edition, you must be running one of the following operating systems:
Windows 2000 Advanced Server
Windows NT 4.0 Enterprise Edition
You can install Windows Server 2003 R2 on a server running Windows Server 2003 with Service Pack 1 without performing an operating system upgrade.
Perform the following actions to prepare a Windows NT–based domain for upgrading to Active Directory:
Verify that all PDCs and BDCs that you plan to upgrade are running Windows NT Server 4, or Windows NT Server 4 Enterprise Edition with Service Pack 6a.
Clean up the directories and user accounts to eliminate old baggage. When you upgrade the domain, Windows moves all user accounts into Active Directory. Although Active Directory is extremely scalable, disused accounts do take up hard disk space and make identifying valid accounts more difficult. There’s no point in storing and replicating disused accounts indefinitely, so delete them before you upgrade.
Clean out unused directories, and uninstall outdated software.
Disable trusts that you don’t want to preserve.
Synchronize the PDC with all the BDCs, and then implement the recovery plan described earlier in the Making a Recovery Plan section, including taking one of the BDCs offline and disconnecting it from the network.
To prepare the computers for the upgrade, perform these tasks for each computer involved:
Check the system requirements for the version of Windows to which you’re upgrading to make sure the computer meets them. See Chapter 5 for more information.
Check the Windows Server Catalog on the Microsoft Web site (http://www.microsoft.com/windows/catalog/server/). If possible, replace components that the Windows Catalog doesn’t list as 100-percent compatible.
Insert the Windows Server 2003 or Windows XP CD-ROM (if you’re upgrading a client), and check the system for compatibility problems.
If you’re upgrading from Windows NT 4.0, install Windows NT 4.0 Service Pack 6a.
If you’re upgrading a Windows 2000 server running Microsoft Internet Security and Acceleration (ISA) Server 2000, make sure ISA Server 2000 Service Pack 1 or later is installed.
If you’re upgrading a Windows 2000 domain controller that has the Server for NIS component of Services For UNIX 2.0 installed, see Microsoft Knowledge Base Article 293783 at http://support.microsoft.com for information about a supported hotfix.
Read the Read1st.txt and Relnotes.doc files on the Windows 2000 CD-ROM to check for application or hardware issues.
Check the Event Viewer. Fix any problems before you upgrade.
Uninstall any virus protection programs you have installed, unless you know that they work under Windows Server 2003 without modification.
Perform and verify a full system backup, including the system state, and create or update the emergency repair disk.
Record the hardware configuration of the system for reference in case of a hardware conflict or problem. Include installed devices, interrupt requests (IRQs), jumper settings, and the hard disk configuration.
Disable any Windows NT 4.0 software-based disk mirrors, volume sets, stripe sets, or stripe sets with parity:
If you’re using a software-based mirror set, break the mirror.
If you’re using any volume sets, stripe sets, or stripe sets with parity, back up the data and then delete the set (deleting all data). After you install Windows Server 2003, restore the data to the appropriate basic disk or dynamic disk. (See Chapter 18.)
Uncompress all hard disks (unless they make use of NTFS compression).
Disconnect the serial cable to any serial port uninterruptible power supply (UPS) devices. (You can leave USB UPS devices plugged in.)
Locate all drivers and get the Windows CD-ROM, or connect to the network share with the Windows installation files.
You must update the Active Directory schema before performing the following actions:
Adding a Windows Server 2003 or Windows Server 2003 R2 domain controller to an existing Windows 2000 forest or domain
Adding a Windows Server 2003 R2 domain controller to an existing Windows Server 2003 forest or domain
This section discusses how to test Active Directory before updating the schema, as well as how to update the forest schema, verify the update, and update the domain schema for each domain in which you want to install Windows Server 2003 or Windows Server 2003 R2 domain controllers.
Important
If you use any third-party Active Directory applications or have made any custom changes to the Active Directory schema, verify that they are compatible with the Windows Server 2003 or Windows Server 2003 R2 schema revision levels before updating the forest schema. This is rarely a problem, but it is nearly impossible to undo a schema update once it has propagated, so it’s best to err on the side of caution.
Perform the following actions before updating the Active Directory schema, adding any Windows Server 2003 domain controllers to an existing Windows 2000 Active Directory domain, or upgrading any Windows 2000 domain controllers in the domain to Windows Server 2003:
Verify that all domain controllers in the domain have Netlogon and Sysvol shares by using Dcdiag.exe from the Windows Support Tools. To do so, open a command prompt window, switch to the folder storing Dcdiag.exe, and then type dcdiag /e /test:frssysvol. All domain controllers should pass the tests.
If you see the error message "There are errors after the SYSVOL has been shared", try restarting the File Replication Service on the affected domain controller, check the File Replication Service log in Event Viewer for any additional errors, and then rerun Dcdiag.exe.
View the operations master roles in the forest by using the dcdiag /test:FSMO-CHECK command, and transfer any operation master roles that reside on nonexistent or unhealthy domain controllers to healthy domain controllers. See Chapter 15 for information on transferring operation master roles.
Verify replication using the Windows Server 2003 version of Repadmin.exe on a Windows XP or Windows Server 2003 member server in the forest. To do so, open a command prompt window, switch to the folder storing Repadmin.exe, and then type repadmin /replsum /bysrc /bydest /sort:delta.
All domain controllers should show 0 in the Fails column, and the largest deltas should be less than or roughly equal to the replication frequency on the site links used by the domain controllers for replication. The default replication frequency between sites is 180 minutes; you can change this setting by using the Active Directory Sites And Services MMC snap-in. See Chapter 15 for more information.
Use the Group Policy Verification Tool (Gpotool.exe) to verify proper Group Policy functioning on domain controllers. You can download Gpotool.exe from the Windows 2000 Server Resource Kit at http://www.microsoft.com/windows2000/techinfo/reskit/tools/existing/gpotool-o.asp.
You must update the Active Directory schema before you can add a Windows Server 2003 or Windows Server 2003 R2 domain controller to a Windows 2000 Active Directory forest, or add a Windows Server 2003 R2 domain controller to a Windows Server 2003 Active Directory forest. This also applies to domain controllers upgraded to Windows Server 2003 or Windows Server 2003 R2.
To prepare a forest for Windows Server 2003 or Windows Server 2003 R2 domain controllers, use the following procedure to update the schema in your test lab. This is an important step because you cannot undo a forest schema update. After testing the schema updates, use the procedure in your production network.
Update all Windows 2000 domain controllers and servers running Exchange Server 2000 or later to Windows 2000 Service Pack 4 or later.
Domains with more than 10 domain controllers consume additional network bandwidth during replication unless all domain controllers are running Windows 2000 with Service Pack 3 or later. See Microsoft Knowledge Base Article 331161 at http://support.microsoft.com for more information about this and other issues with Windows 2000 domain controllers running service pack revisions earlier than Service Pack 4.
Important
If you have implemented the Exchange Server 2000 schema changes in the forest prior to updating the forest schema to Windows Server 2003 or Windows Server 2003 R2 levels, you must perform a special schema update to prevent Adprep from mangling attributes. See Microsoft Knowledge Base Article 325379 at http://support.microsoft.com for information about how to prep the schema and for help with fixing mangled attributes. You can safely update the schema for Exchange Server 2000 after updating the forest schema to Windows Server 2003 or Windows Server 2003 R2 level.
Identify the servers with the schema master and infrastructure master roles, and install the appropriate version of the Windows Support Tools on the schema master.
Note
If you’re updating a Window 2000 Active Directory forest to support Windows Server 2003 domain controllers, update the schema to the Windows Server 2003 R2 revision, even if you don’t plan to immediately use Windows Server 2003 R2 domain controllers. This eliminates the hassle of updating the schema a second time when you decide to deploy Windows Server 2003 R2 domain controllers.
On the server designated the schema master, use the Run As feature (discussed in Chapter 12) to open a command prompt window on the schema master using an account that belongs to the Enterprise Admins and Schema Admins groups (or has delegated authority). Or log on to the server using an account that belongs to the Enterprise Admins and Schema Admins groups (or has delegated authority), and open a command prompt window.
Switch to the folder in which you installed the Windows Support Tools, and run the repadmin /showreps command to verify that the last inbound replication succeeded. If the last replication failed, troubleshoot replication before proceeding.
Temporarily disable outbound Active Directory replication by typing repadmin /options +DISABLE_OUTBOUND_REPL.
Switch to the folder in which Adprep.exe is located.
To update the forest schema to Windows Server 2003 R2 level, use the Adprep.exe file located in the CmpnentsR2Adprep folder of the Windows Server 2003 R2 Disc 2 CD-ROM.
Best Practices
Use either the Windows Server 2003 R2 version of Adprep.exe (to upgrade the forest schema to Windows Server 2003 R2 level) or the Windows Server 2003 Service Pack 1 version of Adprep.exe (to upgrade the forest schema to Windows Server 2003 level). These versions of Adprep.exe offer increased error checking and reporting, and provide more control over updating the domain schema. The Windows Server 2003 Service Pack 1 version of Adprep.exe is located in the i386 or amd64 folder of the Windows Server 2003 with Service Pack 1 CD, and is available for download from Microsoft Product Support Services via Microsoft Knowledge Base Article 324392 at http://support.microsoft.com.
Type adprep /forestprep, and watch for any error messages.
If the schema upgrade completed successfully and without errors (see the next section for information about how you can verify that the update proceeded properly), switch to the folder in which you installed the Windows Support Tools, and type repadmin /options -DISABLE_OUTBOUND_REPL to enable outbound replication of the schema master to the network. Then update the schema in each domain in which you want to install Windows Server 2003 or Windows Server 2003 R2 domain controllers.
Otherwise, follow the instructions provided by the error messages, if possible, or restore from backup and research the problem before trying again.
To verify that the schema update operation succeeded for the forest, perform the following steps:
Check the system log in Event Viewer for any errors. (You can safely ignore errors with event ID 1153.)
Install the Windows Support Tools and then use the Dcdiag.exe command from the Windows Support Tools to verify Active Directory functionality. (Ignore any replication errors—the server is disconnected from the network.)
To do so, click Start, choose All Programs, Windows Support Tools, Command Prompt and then type Dcidiag in the command prompt window.
Open ADSI Edit from the Windows Support Tools.
To do so, click Start, choose All Programs, Windows Support Tools, Command Prompt and then type Adsiedit.msc in the command prompt window.
In the ADSI Edit window under the Configuration node, navigate to CN=Configuration,DC=forest_root_domain, where forest_root_domain is the DNS name of the forest root domain, and then navigate to CN=ForestUpdates.
Right-click the CN=Windows2003Update object (shown in Figure 6-4), choose Properties from the shortcut menu, and then view the value for the Revision attribute (or property in Windows 2000). The value should read 9 after updating the forest schema for Windows Server 2003 or Windows Server 2003 R2. (See Table 6-3 for a listing of schema revision numbers.)
Under the Schema node of ADSI Edit, right-click the CN=Schema,CN=Configuration,DC=forest_root_domain object, where forest_root_domain is the DNS name of the forest root domain, and then choose Properties from the shortcut menu.
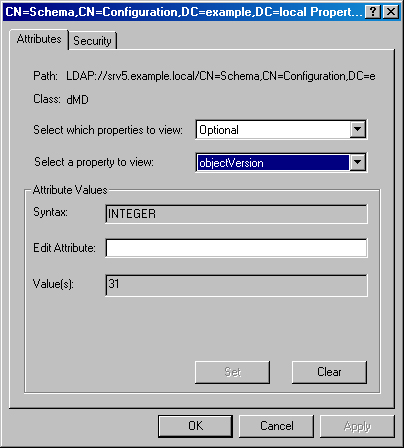
View the value for the objectVersion attribute (or property in Windows 2000), as shown in Figure 6-5. The value should read 31 after updating the forest schema for Windows Server 2003 R2. (See Table 6-3 for a listing of schema version numbers.)
To prepare a domain for Windows Server 2003 or Windows Server 2003 R2 domain controllers, you must update the domain schema to the Windows Server 2003 or Windows Server 2003 R2 levels. Use the following procedure on each domain before adding Windows Server 2003 or Windows Server 2003 R2 domain controllers to the domain:
If you recently updated the forest schema and different computers perform the infrastructure master role and schema master role, wait for Active Directory to replicate the changes to the infrastructure master. Wait 15 minutes if the infrastructure master is in the same site; half a day or a day if it’s in another site.
If your domain controllers are running Windows 2000 Server with Service Pack 2 or earlier, the adprep /forestprep command delays replication. (See Microsoft Knowledge Base Article 331161 at http://support.microsoft.com for more information.)
Open a command prompt window on the infrastructure master using an account that belongs to the Domain Admins or Enterprise Admins group (or has delegated authority).
Temporarily disable outbound Active Directory replication by typing repadmin /options +DISABLE_OUTBOUND_REPL.
Switch to the folder in which Adprep.exe is located.
To update the forest schema to Windows Server 2003 R2 level, use the Adprep.exe file located in the CmpnentsR2Adprep folder of the Windows Server 2003 R2 Disc 2 CD-ROM.
Best Practices
Use either the Windows Server 2003 R2 version of Adprep.exe (to upgrade the schema to Windows Server 2003 R2 level) or the Windows Server 2003 Service Pack 1 version of Adprep.exe (to upgrade the schema to Windows Server 2003 level). These versions of Adprep.exe offer increased error checking and reporting, and they provide more control over updating the domain schema. The Windows Server 2003 Service Pack 1 version of Adprep.exe is located in the i386 or amd64 folder of the Windows Server 2003 with Service Pack 1 CD, and is available for download at http://support.microsoft.com via Microsoft Knowledge Base Article 324392.
Type adprep /domainprep, and watch for any error messages.
Confirm that Adprep upgraded the schema properly by doing the following:
Use Dcdiag from the Windows Support Tools.
Check the system log in Event Viewer for any errors.
Check the Adprep.exe log files in the systemrootSystem32DebugAdprepLogs folder.
If the domain preparation completed without errors, switch to the folder in which you installed the Windows Support Tools, and type repadmin /options -DISABLE_OUTBOUND_REPL to enable outbound replication of the schema master to the network. Otherwise, follow the instructions provided by the error messages, if possible, or restore from backup and research the problem before trying again. Do not proceed until you can confirm that the domain was prepared properly.
Find a time when the network is quiet enough to synchronize all Group Policy Objects (GPOs) between all domain controllers on the domain, and then type adprep /domainprep /gpprep and watch for any error messages.
This step ensures that Resultant Set of Policy (RSoP) works properly with site-based GPOs.
Wait for the changes to replicate to other domain controllers before upgrading any domain controllers to Windows Server 2003 or Windows Server 2003 R2. Allow at least 15 minutes. If there are domain controllers in remote sites, allow half a day or a day.
Although this book concentrates on Windows Server 2003 issues, in all likelihood you’ll spend more time performing client upgrades than server upgrades.
Upgrading to Windows XP is easy, but the results vary depending on the starting operating system. Systems running Windows 2000 almost universally upgrade perfectly. Windows NT 4.0 systems usually upgrade flawlessly, although they might end up with some legacy device drivers.
Computers running Windows 98 or Windows Me are the most difficult to upgrade to Windows XP. Because of these difficulties, perform clean installations instead of upgrades whenever possible. If you need to migrate user settings and data, use the User State Migration Toolkit (USMT), available from the Microsoft Web site at http://www.microsoft.com/technet/desktopdeployment/userstate/userstateusmt.mspx. Before deciding whether to upgrade or to perform new installations, test the upgrade or migration on some clients that are representative of the client population. (Chapter 5 covers performing clean installations of Windows.)
Note
You can automate the upgrading of Windows 2000 clients using the Software Installation feature of Group Policy. To do so, see Chapter 28. You can also automate upgrades using command-line switches. (See Chapter 5 for more information.)
To upgrade a client computer to Windows XP, use the following procedure:
While running Windows 2000, Windows NT 4.0, Windows Me, or Windows 98, close all open programs and disable all virus-protection programs.
Insert the Windows XP CD-ROM, and in the Welcome To Microsoft Windows XP window, click the Install Windows XP link.
Select the Upgrade option, click Next, and then follow the instructions onscreen to upgrade Windows. This upgrades the computer to Windows XP while keeping the settings and programs intact.
If Setup finds hardware or software that isn’t compatible with Windows XP, it lists it on the Report System Compatibility page.
If prompted, select Yes to upgrade your drive to NTFS, unless you want to dual-boot with Windows 98 or Windows Me, or anticipate that you might uninstall Windows XP.
After you plan the domain upgrade and prepare the computer (as discussed earlier in this chapter), you’re ready to begin the upgrade. Use this section to install Windows Server 2003 R2 on a server running Windows Server 2003, or to upgrade a server running Windows NT 4.0, Windows 2000, or Windows Server 2003 to Windows Server 2003 or Windows Server 2003 R2.
Note
Instead of upgrading an existing Windows 2000 domain controller to be the first Windows Server 2003 domain controller in the domain, add a Windows Server 2003 member server and then install Active Directory on it after it’s been up and running for a week or so. This allows your network to continue operating without being affected by the upgrade process.
To install Windows Server 2003 R2 on a server running Windows Server 2003, use the following steps:
If you haven’t yet installed Windows Server 2003 Service Pack 1, install the service pack from Windows Update or another source and then restart the server.
Close all open programs, disable all virus protection programs, and then insert Windows Server 2003 R2 Disc 2.
In the Welcome To Windows Server 2003 R2 window, click the Continue Windows Server 2003 R2 Setup link, and then follow the instructions onscreen in the Windows Server 2003 R2 Setup Wizard.
Note
You must update the Active Directory schema to the Windows Server 2003 R2 revision before you can install Windows Server 2003 R2 on any domain controllers in the forest. See the Updating the Active Directory Schema section of this chapter for more information.
To upgrade a server to Windows Server 2003, use the following steps:
If you’re upgrading a PDC, synchronize with the domain’s BDCs one last time.
When upgrading a Windows NT 4.0 multiple domain network, make sure that you follow your upgrade plan to upgrade the Windows NT 4.0 domains in the proper order.
Close all open programs, and disable all virus-protection programs. Then insert the Windows Server 2003 CD-ROM.
In the Welcome To Windows Server 2003 window, click the Install Windows Server 2003 link.
Select the Upgrade option (shown in Figure 6-6), click Next, and then follow the instructions onscreen to upgrade Windows. This upgrades the computer to Windows Server 2003 while keeping the settings and programs intact.
If Setup finds hardware or software that isn’t compatible with Windows Server 2003, it lists it on the Report System Compatibility page.
If prompted, select Yes to upgrade your drive to NTFS.
Windows Setup copies files to the hard drive and then restarts the computer for the text-based part of Setup. (You might need to remove the CD-ROM temporarily to boot into Setup properly.)
If you are upgrading a PDC or BDC, the Active Directory Installation Wizard starts after Setup completes. If you’re installing Windows Server 2003 R2, finish the Windows Server 2003 R2 Setup process before using the Active Directory Installation Wizard. See Chapter 14 for information about how to use this wizard to install Active Directory and a DNS server if you want to deploy both services on the domain controller (a good idea). Refer to the next section for help in choosing a forest functional level.
Note
Windows doesn’t import existing trusts between Windows NT 4.0 domains into Active Directory when upgrading a Windows NT 4.0 PDC, though the trusts continue to function as long as a BDC is available. Because of this, you must recreate all trusts with Windows NT 4.0 domains in Active Directory before upgrading or taking the last BDC in the upgraded domain offline.
Active Directory has a number of functional levels that dictate what features are available and what versions of Windows can serve as domain controllers. In a forest that includes any Windows Server 2003 domain controllers, there are three forest functional levels, and four domain functional levels. This is an increase from the single forest functional level and two domain functional levels available in Windows 2000.
The following sections help you sort out this increased complexity and figure out what functional levels are appropriate for your network.
Note
Windows Server 2003 R2 does not add any functional levels to Active Directory, though it does require a schema update, as discussed in the Updating the Active Directory Schema section of this chapter.
There are three forest functional levels available in a network with Windows Server 2003 domain controllers: Windows 2000, Windows Server 2003 Interim, and Windows Server 2003.
Windows 2000. The baseline forest functional level that supports Windows Server 2003 and Windows 2000 domain controllers, as well as Windows NT 4.0 BDCs. The Windows 2000 forest functional level permits domains to use any functional level—Windows 2000 mixed or higher—and is the default forest functional level.
Windows Server 2003 interim. A special functional level that is available when upgrading from Windows NT 4.0. The Windows Server 2003 interim functional level supports only Windows Server 2003 domain controllers and Windows NT 4.0 BDCs. It allows group membership changes (instead of the entire group membership list) to be replicated, and it improves the generation of intersite replication topologies. When you choose the Windows Server 2003 interim forest functional level, you must use the Windows Server 2003 interim domain functional level or higher for all domains in the forest.
Windows Server 2003. The native functional level of a forest where all domain controllers run Windows Server 2003. The Windows Server 2003 forest functional level provides the features of the interim functional level, along with other new features such as the ability to rename domains and create two-way, transitive trusts between forests. When you choose the Windows Server 2003 forest functional level, you must use the Windows Server 2003 domain functional level for all domains in the forest.
Start with the Windows 2000 forest functional level if you have any Windows 2000 domain controllers in your forest or if you anticipate that you might. Switching forest or domain functional levels is a one-way process (there’s no going back), and old servers have a surprising knack for sticking around and making themselves useful. For example, you can put an aging Windows 2000 domain controller to good use as a second or third domain controller at a remote site.
Important
Upgrade all Exchange 2000 Active Directory Connection (ADC) servers to Microsoft Exchange Server 2003 before using the Windows Server 2003 interim forest functional level or upgrading to Windows Server 2003 forest functional level. See Microsoft Knowledge Base Article 825916 at http://support.microsoft.com for more information.
If you’re upgrading directly from Windows NT 4.0 and you know that you’ll never want to add a Windows 2000 domain controller to the forest (in any domain), choose the Windows Server 2003 interim functional level when performing the upgrade. (This option appears in the Active Directory Installation Wizard.) If you forgo this option when upgrading the PDC, you can make the switch later, although you’ll have to use a script to do so. (See the Windows Server 2003 Resource Kit for more information.) If your Windows NT 4.0 domains make use of groups with more than 5000 members, you must choose the Windows Server 2003 interim functional level or divide the groups into two or more groups of 5000 members or less (except for the Domain Users group, which is exempt from this limitation).
Note
You can raise the domain functional levels of all domains in the forest to Windows Server 2003 native level without touching each domain, as long as all domains are already at the Windows 2000 native functional level (or Windows Server 2003 native). Simply raise the forest functional level to Windows Server 2003 native level, and all domains follow suit.
When you raise the forest functional level to Windows Server 2003 functional level, you automatically raise the domain functional level for all domains in the forest to the Windows Server 2003 functional level. If there are any Windows 2000 domain controllers, Windows generates a report listing the offending servers and blocks the increase until you upgrade or remove the domain controllers. If there are any domains using Windows 2000 mixed or Windows Server 2003 interim functional levels, Windows blocks the increase until you raise the functional level of the domains to Windows 2000 or Windows Server 2003.
Table 6-4 summarizes the differences between the different forest functional levels. (For a more complete list, see the Windows Server 2003 Help and Support Center.)
Table 6-4. Some differences among forest functional levels
Feature | Windows 2000 | Windows Server 2003 Interim | Windows Server 2003 |
|---|---|---|---|
Supported domain controllers | Windows Server 2003, Windows 2000, Windows NT 4.0 BDCs | Windows NT 4.0 BDCs, Windows Server 2003 | Windows Server 2003 |
Efficient Group Member Replication | No | Yes | Yes |
Improved Replication Topology Generation | Limited; requires Windows Server 2003 domain controller | Full | Full |
Linked value replication | No | Yes | Yes |
Global catalog replication improvements | When both domain controllers are Windows Server 2003 | Yes | Yes |
Maximum number of group members | 5000 (except Domain Users group, which can be higher) | 5000+ | 5000+ |
Domain rename | No | No | Yes |
Transitive forest trusts | No | No | Yes |
Defunct schema objects | No | No | Yes |
Application Group | No | No | Yes |
An Active Directory domain can run in one of four functional levels: Windows 2000 mixed, Windows Server 2003 interim, Windows 2000 native, and Windows Server 2003.
Windows 2000 mixed. The default mode of all newly created domains, as well as upgraded Windows NT domains. While a domain is in mixed mode, Windows NT 4.0 BDCs, Windows 2000 domain controllers, and Windows Server 2003 domain controllers can all coexist on the network.
Windows Server 2003 interim. A new functional level designed for networks that are upgrading a Windows NT domain directly to Windows Server 2003. When using Windows Server 2003 interim functional level, you cannot use Windows 2000 domain controllers in the domain, though you can use Windows 2000 clients and member servers. The Windows Server 2003 interim functional level doesn’t offer any new features on a domain level (though the Windows Server 2003 Interim forest functional level does). Adprep automatically raises all domains in the forest to this level when you raise the forest functional level to the Windows Server 2003 interim functional level.
Windows 2000 native. A functional level for Windows 2000 and newer domain controllers that permits domains to scale past the Windows NT 40,000 account limit, enables the SIDHistory feature (which makes domain restructuring much less painful), and provides the additional Universal and Domain Local groups. When using Windows Server 2000 native functional level, you can only use Windows 2000 and Windows Server 2003 domain controllers.
Windows Server 2003. A functional level for Windows Server 2003 domain controllers only that provides all the features of Windows 2000 functional level, as well as domain controller renaming and a higher maximum number of sites per domain, among other things.
Start with the Windows 2000 mixed domain functional level if you have any Windows 2000 domain controllers in your forest or if you anticipate that you might. Otherwise, choose the Windows Server 2003 Interim functional level. Most companies find themselves remaining in Windows 2000 mixed or Windows Server 2003 interim functional level for some time to ensure compatibility with existing Windows NT 4.0 BDCs or other servers that need access to a "real" Windows NT 4.0 BDC. However, there are advantages to using the Windows 2000 and Windows Server 2003 native functional levels, as described in Table 6-5, especially when restructuring or consolidating domains.
Table 6-5. The differences among domain functional levels
Feature | Windows NT 4.0 | Windows 2000 Mixed | Windows 2000 Native | Windows Server 2003 Interim | Windows Server 2003 |
|---|---|---|---|---|---|
Supported domain controllers | Windows NT 4.0, Windows NT 3.51 BDCs | Windows Server 2003, Windows 2000, Windows NT 4.0 BDCs | Windows Server 2003, Windows 2000 | Windows NT 4.0, Windows Server 2003 | Windows Server 2003 |
Objects per domain | Fewer than 40,000 (20,000 user accounts) recommended | Fewer than 40,000 (20,000 user accounts) recommended | Millions | Millions | Millions |
Multimaster replication | No | Yes | Yes | Yes | Yes |
Group types | Global, Local | Global, Local | Universal, Domain Global, Domain Local, Local | Global, Local | Universal, Domain Global, Domain Local, Local |
Domain controller rename | No | No | No | No | Yes |
Nested groups | No | Distribution groups and local groups that can store global groups only | Yes | Distribution groups and local groups that can store global groups only | Yes |
Convert groups | No | No | Yes | No | Yes |
Cross-domain administration | Limited | Limited | Full | Limited | Full |
Group membership replication | Only membership changes | Entire group membership list | Entire group membership list | Only membership changes | Only membership changes |
Maximum sites per domain | N/A | 300 | 300 | 300 | 3000 |
SIDHistory | No | No | Yes | No | Yes |
Password filters | Installed manually on each PDC and BDC | Installed manually on each domain controller | Installed automatically on all domain controllers | Installed manually on each domain controller | Installed automatically on all domain controllers |
Queries using Desktop Change/Configuration Management | No | Only on Windows 2000 domain controllers | Yes | Only on Windows Server 2003 domain controllers | Yes |
Authentication protocols | NTLM | NTLM, Kerberos | Kerberos | NTLM, Kerberos | Kerberos |
lastLogonTimestamp user/computer attributes | No | No | No | No | Yes |
inetOrgPerson user password | N/A | No | No | No | Yes |
Redirect the Users and Computers containers | No | No | No | No | Yes |
Microsoft recommends a rapid switch to Windows 2000 functional level; however, consider taking a more cautious approach when upgrading from a Windows NT 4.0 network. Running in Windows 2000 mixed or Windows Server 2003 interim functional level allows nervous network administrators a chance to start using Active Directory in a limited manner without losing their Windows NT 4.0 safety net. Wait until it’s clear there is no need for Windows NT 4.0 BDCs before making the domain functional level upgrade because, after you upgrade the domain mode, there is no going back. There is less incentive for most networks to move to the Windows Server 2003 functional level, although large networks should evaluate it more closely, as the increased scalability and replication efficiency can be invaluable.
Before switching functional levels, take the last Windows NT 4.0 BDC or Windows 2000 domain controller offline and test whether there are any remaining legacy applications or servers that break as a result. This step is important because you cannot undo a functional level switch. Once you are sure that you don’t need any legacy domain controllers on the network, and will never again need any, log on to a domain controller using an administrator account and follow these steps to raise the forest or domain functional level:
Click Start, choose Administrative Tools, and then select Active Directory Domains And Trusts.
To raise the forest functional level, right-click Active Directory Domains And Trusts and then choose Raise Forest Functional Level. To raise the domain functional level, right-click the domain for which you want to change the functional level and choose the Raise Domain Functional Level option.
You can also upgrade forests from a command line. (See the Help menu for the procedure.)
Select the functional level, as shown in Figure 6-7, and then click Raise.
When Windows asks you to verify the switch, click OK. Click OK in the next dialog box also.
Important
You can upgrade the functionality of a forest only after all domains within the forest use the Windows 2000 or Windows Server 2003 functional levels. After you upgrade a forest, you can add only domains operating in the same mode or higher. To add a domain with a lower functionality level, you have to create a whole new forest.
Upgrading a computer’s operating system to Windows Server 2003 or Windows XP is relatively easy, but upgrading domains to Active Directory is considerably more complex. You must perform a lot of planning before you can upgrade a Windows NT domain, and some preparation is necessary for Windows 2000 domains as well. This planning includes steps such as documenting the network, devising a recovery plan, creating a suitable Active Directory structure, and then putting it all together into a plan of attack. Despite all the work involved, upgrading domains is usually the least painful way of moving to Active Directory.
The next chapter moves on to the initial configuration steps to take after you complete the Windows Server 2003 installation process.