7
Visual Cryptography and Random Grids
Shyong Jian Shyu
Ming Chuan University, Taiwan
CONTENTS
7.1 Introduction
A random grid was defined by Kafri and Keren in 1987 [7] as a transparency comprising a two-dimensional array of pixels. Each pixel is either fully transparent or simply opaque and the choice between the alternatives is made by a coin-flip procedure. Thus, there is no correlation between the values of different pixels in the array.
We could encrypt binary pictures or shapes into two random grids such that only the areas containing information in the two grids are intercorrelated, while the others are purely random. When the two grids are superimposed together, the correlated areas will be resolved from the random background due to the difference in light transmission so that the secret picture or shape can be seen visually. Just like conventional schemes in visual cryptography, the decoding process is done by the human visual system where no computation is needed; however, no extra pixel expansion is required using random grids.
Observing the interesting features of random grids in image encryption, which were discussed right before Naor and Shamir's visual cryptographic scheme (VCS) [9], Shyu [12, 13] generalized the random grids-based approaches into visual cryptograms of random grids (VCRG) for achieving visual secret sharing recently. The most appealing benifits using random grids lie in that the pixel expansion needed is merely one and no basis matrix is needed. With the same contrast in the reconstructed results, the optimal pixel expnasion in (n, n)-VCS is 2n−1; while that in (n, n)-VCRG is still 1.
We study the random grids-based schemes, analyze the performances, and demonstrate their feasibilities in this chapter. The rest of the chapter is organized as follows. The fundamental characteristics of random grids are discussed in Section 7.2. Section 7.3 discusses how to apply visual cryptograms of random grids in visual cryptography where the formal definition of VCRG is given, and the designs, analyses, and implementations of (2, 2)-VCRGs and (n, n)-VCRGs for binary, gray-level and color images are examined. Section 7.4 exhibits some concluding remarks.
7.2 Random Grids
7.2.1 Random Pixel, Random Grid, and Average Light Transmission
We refer to a binary pixel r as a random pixel if the choice for r to be transparent or opaque in R is totally random; or equivalently, the probability for r to be transparent is equal to that for r to be opaque,
where 0 (1) denotes a transparent (opaque) pixel. Since a transparent pixel lets through the light while an opaque one stops it, the average light transmission of random pixel r is , denoted as
Definition 1 R is a binary random grid if each pixel r in R is a binary random pixel.
Regarding a random grid R, the number of transparent pixels is probabilistically the same as that of opaque ones so that the average light transmission of R is also , denoted as
7.2.2 Superimposition of Random Grids
Let ⊗ denote the generalized ”or” operation, which describes the relation of the superimposition of two random pixels or grids pixel by pixel. It is obvious that r ⊗ r (R ⊗ R) is entirely the same as r (R), that is
for each pixel r in R.
Let R1 and R2 be two independent random grids with the same size. When R1 and R2 are superimposed pixel by pixel, each pixel (either transparent or opaque) in R1 has an equal possibility to be stacked by a transparent pixel or an opaque pixel in R2.We call r1 = R1[i,j] the corresponding pixel of r2 = R2[i′, j′] if and only if i = i′ and j = j′ (the positions of r1 at R1 and r2 at R2 are the same). It is easy to see that the order of the two random grids does not affect the superimposed result, i.e.,
Indeed, ⊗ is a commutative operation.
Table 7.1 Results of the superimposition of two random pixels.
| r1 | r2 | r1 ⊗ r2 |
| 0 | 0 | 0 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 1 | 1 | 1 |
Table 7.1 shows the superimposed results of the corresponding random pixels r1 and r2. There is only one outcome among the four possible combinations of r1 ⊗ r2 showing transparency. Since the four possible combinations occur with an equal probability, the probability for r1 ⊗ r2 to be transparent is . That is, the average light transmission of the superimposition of R1 and R2 (r1 and r2) is .
We summarize the aforementioned properties in Lemma 1.
Lemma 1 If R1 and R2 are two independent random grids with J(R1) = J (R2) = 1/2,
J(R1 ⊗ R2) = J(R2 ⊗ R1) = 1/4;
J(R1 ⊗ R1) = 1/2.
We define to be the inverse random grid of R if and only if
for each r′ in where r is the corresponding pixel of r′ in R and r̄ denotes the inverse of r. It is easy to see that r ⊗ r̄ = 1 and (1 denotes a grid in which all pixels are opaque), that is
For each pixel r′ in , since , we obtain
In general, the relationship of the average light transmissions of R ∈ R is given in Lemma 2.
Lemma 2 If R is a random grid with J(R) = λ, .
Proof From J(R) = λ, we know that for any pixel r ∈ R Prob (r = 0) = λ and Prob(r = 1) = 1 − λ. Let be the corresponding pixel of r. Thus, Prob(r′ = 1)= Prob(r = 1) = 1 − λ and Prob(r′ = 1) = Prob(r = 1) = λ. We have . ■
Consider two independent random grids X and Y. There is another important property called the principle of combination : if we cut a section, say A, from X and replace it with section B (with the same size as A) from Y, the result, denoted as Z = (X A) ∩ B, is another random grid, i.e.,
We shall expose how to use the aforemnetioned characteristics of random grids to accomplish visual secret sharing in the next section.
7.3 Visual Cryptograms of Random Grids
First of all, we give a formal definition to VCRG for binary images in Section 7.3.1. Section 7.3.2 presents three algorithms for producing (2, 2)-VCRGs for binary images. The implementation results of these algorithms are reported in Section 7.3.3. Section 7.3.4 evaluates the performances of these algorithms in terms of light contrast. Then, algorithms for producing (n, n)-VCRGs for binary images are discussed in Section 7.3.5. Further, those for gray-level and color images are examined in Section 7.3.6. Section 7.3.7 reports the experimental results of (n, n)-VCRGs. The correctness of these algorithms would be proved and the corresponding light contrasts would be analyzed accordingly.
7.3.1 Definition of VCRG
Consider a set of n random grids E = {R1, R2,…, Rn}, which are encrypted to share a a secret image B such that R1 ⊗ R2 ⊗… ⊗ Rn reveals B to our eyes while any group of less than n grids obtains no information about B. We call E a set of visual cryptograms of random grids with respect to B.
Let B(0) (B(1)) denote the area of white (black) pixels in B and SE [B(0)] (S[B(1)]) denotes the area of pixels in SE corresponding to B(0) (B(1)) where SE = R1 ⊗ R2 ⊗⋯⊗Rn. Formally, a set of (n, n) visual cryptograms of random grids for a binary image is now defined as follows.
Definition 2 Given a binary image B, n random grids {R1, R2,…, Rn} comprise a set of visual cryptograms, referred to as (n, n)-VCRG of B if the following conditions hold:
Ri is a random grid with J(Ri) = 1/2 for 1 ⩽ i ⩽ n;
J(SD[B(0)]) = J(SD[B(1)]) where which is the superimposed result of some set of d distinct random grids in E, i.e., D ⊂ E, 2 ⩽ d ⩽ n − 1 and 1 ⩽ i1 < i2 < ⋯< id ⩽ n; and
J(SE[B(0)]) > J(SE[B(1)]) where SE = R1 ⊗ R2 ⊗ … ⊗ Rn and E = {R1, R2, … , Rn}.
Both Conditions 1 and 2 are ”security” conditions which ensure that each individual grid and the superimposed result of any group of less than n random grids are merely random grids so that no information of B can be obtained. Condition 3 is the ”contrast” condition, which claims that once the light transmission of SE[B(0)] is larger than that of SE [B(1)], our visual perception is able to distinguish B(0) from B(1) by observing SE due to the difference of their light transmissions in SE.
Note that this definition is different from that in Naor and Shamir’s model. Suppose that C1 and C2 are the two encoded shares produced by some (2, 2)-VCS using basis matrices M0 and M1 with respect to binary image B. Then the security condition in (2, 2)-VCS is w(Mb[1]) = (Mb[2]) for b ∈ {0, 1} where Mb[i] is the ith row of Mb for i ∈ {1, 2}, while the contrast condition becomes w(M1[1]or M1[2]) − (M0[1] or M0[2]) > 0. Let c1 in C1 and c2 in C2 be the corresponding pixels of b in B. Let d = c1 ⊗ c2 where d is in D = C1 ⊗ C2. Let b(0) (b(1)) denote the pixel of b = 0(1) and d[b(0)] (d[b(1)]) denote such d corresponding to b(0) (b(1)). Since each b = 0 (1) is encoded according to M0 (M1 ), the contrast condition in (2, 2)-VCS assures w(d[b(1)])−w(d[b(0)]) > 1 so that d(1) can be identified from d(0) for all d(0)’s and d(1)’s in D. However, VCRG only demands J(S[B(0)]) −J(S[B(1)]) > 0, or equivalently, t(s[b(0)]) − t(s[b(1)]) > 0.
7.3.2 (2, 2)-VCRG Algorithms for Binary Images
Let random_pixel(0, 1) be a function that returns a binary value 0 or 1 to represent a transparent or opaque pixel, respectively, by a coin-flip procedure and denote the complement of R1[i, j]. Each of the following three algorithms successfully encodes a secret binary image B into two random grids R1 and R2 which constitute a set of (2, 2)-VCRG.
Algorithms 1–3. Sharing a binary image by two random grids
Input: A w × h binary image B where B[i, j] ∈ {0, 1} (white or black), 1⩽i⩽w and 1⩽j⩽h
Output: Two shares of random grids R1 and R2 which reveal B when superimposed where Rk[i, j] ∈ {0, 1} (transparent or opaque), 1⩽i⩽w, 1⩽j ⩽h and k ∈ {1, 2}
Encryption(B)
Algorithm 1.
1. Generate R1 as a random grid, J(R1) = 1/2
// for (each pixel R1[i, j], 1⩽i⩽w, and 1⩽j⩽h) do
// R1[i,j] = random_pixel (0, 1)
2. for (each pixel B[i, j], 1⩽i ⩽w and 1⩽j ⩽h) do
2.1 { if (B[i, j]=0) then R2[i,j] = R1[i,j]
else
}
3. output(R1, R2)
Algorithm 2.
1. Generate R1 as a random grid, J(R1) = 1/2
2. for (each pixel B[i, j], 1⩽i⩽w and 1⩽j⩽h) do
2.1 { if (B|i, j|=0) then R2|i, j| = R2|i, j|
else R2[i, j] = random_pixel(0, 1)
}
3. output(R1, R2)
Algorithm 3.
1. Generate R1 as a random grid, J(R1) = 1/2
2. for (each pixel B[i, j], 1⩽i⩽w and 1⩽j⩽h) do
2.1 { if (B[i, j] = 0) then R2[i, j] = random_pixel(0, 1)
else
}
3. output(R1, R2)
The three algorithms are capsulated into a generic procedure named Encryption so that when Encryption(B) is called, each of Algorithms 1, 2, or 3 can be applied onto B. Also note that in this paper, 0 (1) denotes a white (black) pixel in the secret binary image or a transparent (opaque) pixel in the encrypted share interchangeably.
Table 7.2 summarizes the encoding process of pixel b in secret image B into r1 and r2 by Algorithms 1, 2, and 3 respectively, the result of r1 ⊗ r2 and its average light transmission.
Let B(0) (B(1)) denote the area of all of the transparent (opaque) pixels in B, that is, pixel b is in B(0) (B(1)) if and only if b = 0 (b = 1) where B = B(0) ∪ B(1) and B(0) ∩ B(1) = Ø. We denote the area of pixels in random grid R corresponding to B(0) (B(1)) by R[B(0)] (R[B(1)]), that is, pixel r is in R[B(0)] (R[B(1)]) if and only if r’s corresponding pixel b is in B(0) (B(1)). Surely, R = R[B(0)] ∪ R[B(1)] and R[B(0)] ∩ R[B(1)] = Ø.
Based upon the above notations, we have the following theorem.
Theorem 1 Given a binary image B, {R1, R2} produced by Algorithms 1−3, respectively, is a set of (2, 2)-VCRG of B.

Table 7.2 Encoding b into r1 and r2 and results of s = r1 ⊗ r2 by Algorithms 1, 2, and 3.
Proof To prove that R1 and R2 constitute a set of (2, 2)-VCRG, we should validate whether the following two conditions (setting n = 2 in Definition 2) hold:
J(R1) = J(R2) ; and
J(S[B(0)]) > J(S[B(1)]) where S = R1 ⊗ R2.
Let us examine Algorithm 1 first. Let R1 [B(b)] denote the area of pixels in R1 that corresponds to B(b) for b = 0 or 1. Note that R1 = R1[B(0)] ∪ R1[B(1)] where R1[B(0)] ∩ R1[B(1)] = Ø. Since Step 1 in Algorithm 1 composes R1 as a random grid with J(R1) =1/2, we have R1(R1) = R(R1[B(0)]) = J(R1[B(1)]) = 1/2. When B[i, j] = 0, we have R2[i, j] = R1[i, j]. That means J(R2 |B(0)|) = J(R1[B(0)]) = 1/2. Moreover, when B[i, j] = 1, . By Lemma 2, we have . Due to the facts that R2 = R2[B(0)] ∪ R2[B(1)] and J(R2[B(0)]) = J(R2[B(1)]) = 1/2, we have J(R2) = 1/2 by the principle of combination. Therefore both of R1 and R2 are merely random grids and none of them individually leaks any information about B. Jhe security condition of Definition 2 is met.
Consider B(0) (the ares of transparent pixels in B). Since R2[i, j] = R1[i, j] for each B[i, j] = 0 (or B[i, j] ∈ B(0)), thus S[B(0)] = R1[B(0)] ⊗ R2[B(0)] = R1[B(0)]. Jhus J(S[B(0)]) = 1/2. Regarding B(1), for each B[i, j] = 1 (or B[i, j] ∈ B(1)). We have S|B(1)| = R1[B(1)] ⊗ R2[B(1)] = 1 (an area with all opaque pixels), i.e., J(S[B(1)]) = 0. Jhus J(S[B(0)]) > J(S[B(1)]). Jhe light contrast condition of Definition 2 is satisfied. Jherefore, {R1, R2} produced by Algorithm 1 is a set of (2, 2)-VCRG of B and (J(S[B(0)]), J(S[B(1)])) = (1/2, 0).
For Algorithm 2, we have J(R2[B(0)]) = J(R1[B(0)]) = 1/2 and R2[B(1)] is purely a random grid with J(R2[B(1)]) = 1/2. Jhus, R2 is a random grid with J(R2) = 1/2. Since R2[B(0)] = R1[B(0)], J(S[B(0)]) = J(R1|B(0)| ⊗ R2|B(0)| = J((R1|B(0)|) = 1/2; while R1|B(1)| and R2|B(1)| are two independent random grids so that J(S[B(1)]) = J(R1[B(1)] ⊗ < R2[B(1)]) = J(R1[B(1)]) × J(R2[B(1)]) = 1/4 (by Lemma 1(1)). We obtain J(S[B(0)]) > J(S[B(1)]).
For Algorithm 3, J(R2[B(0)]) = 1/2 because R2[B(0)] is a purely random grid and . We have J(R2) = 1/2. Further, due to the fact that R1 [B(0)] and R2[B(0)] are independent, J(S[B(0)]) = J(R1[B(0)] ⊗ J R2[B(0)]) = J(R1[B(0)]) × J(R2[B(0)]) = 1/4; on the other hand, since , S[B(1)] = R1 [B(1)] ⊗ (R2[B(1)] = 1, i.e. J(S[B(1)] = 0. We have J(S[B(0)]) > J(S[B(1)]).
Based upon the above statements, we realize that both security and contrast conditions in Definition 2 hold for all of the three algorithms. We conclude that no information of B can be obtained from random grids R1 or R2 individually, while S reveals B in our visual system for all of the three algorithms. Jheorem 1 is proved.
The following corollary is an immediate consequence from the statements in the proof of Jheorem 1.
Corollary 1 (J(S[B(0)]), J(S[B(1)])) = (1/2, 0), (1/2, 1/4) or (1/4, 0) for Algorithms 1–3, respectively where S = R1 ⊗ R2 and {R1, R2} is a set of (2, 2)-VCRG produced by Algorithms 1–3 with respect to secret image B.
7.3.3 Experiments for (2, 2)-VCRG
Figure 7.1 illustrates the results of the implementation of the above three algorithms. Figure 7.1(a) is secret binary image B, Figures 7.1(b) and (c) present the two random grids produced by Algorithm 1 and Figure 7.1(d) is the superimposed result of these two shares ((b) and (c)). Figures 7.1(e)–g) illustrate the corresponding results by Algorithm 2, while Figures 7.1(h)–(j) are the corresponding results by Algorithm 3. It can be easily seen from Figure 7.1 that the encrypted shares (see Figure 7.1(b), (c), (e), (f), (h), and (i)) are merely random pictures and no information about B can be obtained. Only when the two shares are superimposed (see Figures (d), (g), and (j)), can we see B by our visual system. It is worthy of notifying that there is no extra pixel expansion in Figures 7.1(b)–(j).
Figure 7.2 shows the reconstructed results by using Naor and Shamir’s approach for encrypting B in Figure 7.1(a). The pixel expansion of Figure 7.2(a) is 2, while that of Figure 7.2(b) is 4 ( by applying and . Jhe former does not retain the aspect ratio with respect to B, while the latter does. Both sizes of the results in Figure 7.2 are larger than that of B.
7.3.4 Definition of Light Contrast and Performance Evaluation
To evaluate the relative difference of the light transmissions between the transparent and opaque pixels in reconstructed image S by these random grid-based algorithms, we define the light contrast of S with respect to B as follows.
Definition 3 Jhe light contrast of a set E of VCRG produced by an encryption algorithm for a binary image B is defined as
where S is the superimposed result of all visual cryptograms in E.
Let E1, E2, and E3 denote the three sets of (2, 2)-VCRG produced by Algorithms 1–3, respectively. By Definition 3, the light contrasts of E1, E2, and E3 are c(E1) = 1/2 (= (1/2 − 0)/(1 + 0)), c(E2) = 1/5 (= (1/2 − 1/4)/(1 + 1/4)), and c(E3) = 1/4 (= (−1/4 − 0)/(1 + 0)). Jhat is, Algorithm 1 achieves the highest light contrast among the three. Jhis outcome can also be observed by comparing the reconstructed images in Figures 7.1(d), (g), and (j) in which (d) is more recognizable than (g) and (j). Note that 1 + J(S[B(1)]) is introduced as the denominator of c(E) in favor of a less J(S[B(1)]) (than a larger one) when two schemes have a same numerator (i.e., J(S[B(0)]) − T(S[B(1)])). For instance, both of E2 and E3 have the same result of J(S[B(0)]) − T(S[B(1)])), yet their J(S[B(1)])’s are 1/4 and 0, respectively. Jhus, c(E3) > c(E2) according to Definition 3. As we can see, the reconstructed image by E3 (Figure 7.1(j)) is indeed more recognizable than that by E2 (Figure 7.1(g)) by our visual system. In general, we prefer a set of VCRG with a larger light contrast that helps our visual perception to recognize the result. Thus, Algorithm 1 is more preferable than the other two.

FIGURE 195.7
Implementation results of Algorithms 1, 2, and 3 for encrypting binary image B: (a) B; (b), (c), and (d) two encrypted shares and reconstructed image by Algorithm 1; (e), (f), and (g) two encrypted shares and reconstructed image by Algorithm 2; (h), (i), and (j) two encrypted shares and reconstructed image by Algorithm 3.

FIGURE 196.7
Reconstructed results by Naor and Shamir’s approach for binary image B in Figure 7.1(a): (a) m = 2, (b) m = 4.
We summarize the reconstructed light contrasts by these three algorithms in Jable 7.3.
Table 7.3 Light contrasts by Algorithms 1–3 in producing VCRG-2.
| E | J (S[B(0)]) | J (S[B(1)]) | c(E) |
| Algorithm 1 | 0 | ||
| Algorithm 2 | |||
| Algorithm 3 | 0 |
It is noticed that various definitions of contrast in [9, 14, 1] all depend on pixel expansion so that they are not suitable any more to measure the effectiveness of our schemes. On the contrary, since we consider the light transmissions through different areas of the transparency, the measurement of light contrast is more generalized and can be applied to all kinds of schemes.
We discuss how to generate (n, n)-VCRG in the next subsection.
7.3.5 Algorithms of (n, n)-VCRG for Binary Images
Consider an h × w binary image B and n random grids R1, R1, …, Rn with the same dimension. We call r1, r2, …, rn the corresponding pixels of b ∈ B if all rk’s in Rk’s for 1 ⩽ k ⩽ n have the same coordinates as b (if b = B[i, j], then rk = Rk [i, j] where 1 ⩽ i ⩽ h and 1 ⩽ j ⩽ w).
By extending the idea of Algorithm 2 directly, we may obtain a set of two out of n visual cryptograms of random grids where any pair of two out of the n shares can reveal the secret when superimposed. Given a binary image B, we first find a random grid R1 with J(R1) = 1/2. Jhen, we define Rk for 2 ⩽ k ⩽ n as follows:
for each pixel rk ∈ Rk where r1, r2, …, rn are corresponding pixels of b ∈ B. It is easy to see that all Rk’s are random grids and when b = 0, t(rj ⊗ rj) = t/(r1 ⊗ r1) = t(r1) = 1/2; while b =1, t(ri ⊗ rj) = 1/4 by Lemma 1 for each pair of i and j where 1 ⩽ i ≠ j ⩽ n. Jhat is, J(Ri[B(0)] ⊗ Rj[B(0)]) = 1/2 > 1/4= J(Ri[B(1)] ⊗ Rj [B(1)]). As a result, {R1, R2, …, Rn} produced in this way is a set of two out of n visual cryptograms of random grids. Yet, it is not a set of (n, n)-VCRG, since Condition 2 in Definition 2 fails.
Let us extract some informative features from the idea in Algorithm 1. Let B = {0, 1} be a binary set. We introduce a function f : B × B → B defined as follows to transcribe the basic idea in Algorithm 1:
for x, s, ∈ B where is the inverse value of s. We may say that function f(x, s) preserves the value of s if x = 0, and reverses it otherwise (x = 1). In the subject of sequential circuits, the behavior of f(x, s) is equivalent to that of a T flip-flop where s, x and f(x, s) are the current state, toggle input, and next state, respectively. In the area of logical operations, f(x, s) can be implemented by using the Exclusive-OR operation (⊕), that is, f(x, s) = x ⊕ s.
Let B be a binary image and R1 be a random grid with J(R1) = 1/2. By introducing function f, the essential idea of Algorithm 1 for generating each pixel r2 ∈ R2 corresponding to r1 ∈ R1 and b ∈ B can be formulated as
Note that when b = 0, r2 = r1; while b = 1, . This is exactly the same as the manipulation of Step 2 in Algorithm 1.
This critical observation is emphasized as a corollary as follows.
Corollary 2 If R1 is a random grid with J(R1) = 1/2 and the corresponding pixel r2 ∈ R2 of ri ∈ R1 is obtained by r2 = f(b, r1) for each r1 ∈ R1 with any b ∈ B, then R2 is a random grid with J(R2) = 1/2.
By using function f, our first construction of a set of (n, n)-VCRG (E = {R1, R2, ..., Rn}) with respect to B is now introduced as follows. We first generate n − 1 random grids R1, R2, ..., Rn−1 independently with J(Rk) = 1 / 2 for 1 ⩽ k ⩽ n − 1. Jhat is, for every pixel b ∈ B its n − 1 corresponding pixels r1, r2, …,rn − 1 are totally random where rk ∈ Rk for 1 ⩽ k ⩽ n − 1. Based upon r1, r2, …,rk, we compute ak for 1 ⩽ k ⩽ n − 1 by using the recursive formula:
Then, we find rn according to b and αn−1 by
It is noticed that formula (7.11) is a special case of formula (7.13) by setting n = 2. After all rn’s ∈ Rn corresponding to all b’s ∈ B are computed, we obtain Rn. Then, E = {R1, R2,…, Rn} is reported as a set of (n, n)-VCRG of B. The whole idea is formally illustrated in Algorithm 4.
Algorithm 4. Encrypting a secret image into a set of (n, n)-VCRG
Input: an h × w binary image B and an integer n
Output: E = {R1, R2,…, Rn} constituting (n, n)-VCRG of B
1. for (1 ⩽ k ⩽ n − 1) do
{ generate Rk as a random grid, J(Rk) = 1/2
}
2. for (each pixel B[i, j], 1 ⩽ i ⩽ h and 1 ⩽ j ⩽ w) do
2.1 { a1 = R1[i,j]
2.2 for (2 ⩽ k ⩽ n − 1) do
{ak = f(Rk [i, j], ak−1) //f(x, s) is defined in formula (7.10)
}
2.3 Rn[i,j]= f(B[i,j],an−1)
}
3. output(R1, R2,…, Rn)
Before we prove that E = {R1,R2,…,Rn} generated by Algorithm 4 with respect to B is indeed a set of (n, n)-VCRG of B, we explore more useful features among multiple random grids in the following.
It is easy to see that two independent random grids produce another random grid as they are superimposed even when their light transmission is not 1/2. We formalize this in Lemma 3, which is a generalized version of Lemma 1.
Lemma 3 Given two independent random grids R1 and R2 with J(R1) = λ1 and J(R2) = λ2, R1 ⊗ R2 is a random grid with J(R1 ⊗ R2) = λ1λ2.
Proof For any pixel r1 ∈ R1 and its corresponding pixel r2 ∈ R2, we have Pwb(r1 = 0) = λ1 and Pwb(r2 =0) = λ2. r1 ⊗ r2 is transparent if and only if both of r1 and r2 are transparent, that is, Pwb(r1 ⊗ r2 = 0) = Pwb(r1 = 0) × Pwb(r2 = 0) = λ1λ2. Therefore, J(R1 ⊗ R2) = J(Ri) × J(R2) = λ1λ2.
The theme of Lemma 3 can be extended for more than two random grids.
Lemma 4 If U = {R1, R2, …, Ru} is a set of u ≥ 2 independent random grids with J(Ri) = λ for 1 ≤ i ≤ u, then SU is a random grid with J(SU) = λu where SU = R1 ⊗ R2 ⊗ ⋯ ⊗ Ru.
Proof We prove by mathematical induction. Consider the case of V = {R1, R2}. The statement (i.e., J(SV) = λ2) is true by Lemma 3. Assume that the statement holds for the case of V = {R1, R2,…, Ru−1}, that is, SV is a random grid with J(SV) = λu−1 where SV = R1 ⊗ R2 ⊗ ⋯ ⊗ Ru−1. Then, we further consider U = {R1, R2,…, Ru} = V ∪ {Ru}. SU is simply the superimposed result of SV and Ru, i.e., SU = SV ⊗ Ru. By Lemma 3, we have J(SU) = J(SV ⊗ Ru) = J(SV) × J(Ru) = (λu−1) × λ = λu.
Since the superimposition operation ⊗ is commutative, it is not hard to obtain that the results of different superimposing orders of R1, R2,…, Ru are all the same (i.e., SU). As a matter of fact, the superimposed result of any subset of U is also a random grid as indicated in Lemma 5.
Lemma 5 Let U = {R1, R2, …, Ru} be a set up u ≥ 2 independent random grids and where 1 ≤ i1 < i2 < ⋯ < iv ≤ u and J(Ri) = λ for 1 ≤ i ≤ u. SV is a random grid with J(SV) = λv where .
The proof of Lemma 4 can be easily applied to prove Lemma 5. Consider a set of u independent random grids U = {R1, R2,…, Ru} where J(Rk) = 1/2 for 1 ≤ k ≤ u. We may generate a set of u binary images A = {A1, A2,…, Au} with respect to U in such a way that each pixel ak ∈ Ak is defined by formula (7.12), that is,
where ak ∈ Ak and rk ∈ Rk are corresponding pixels for 1 ≤ k ≤ u. Lemma 6 claims that all of A1, A2,…, Au are random grids with J(Ak) = 1/2 for 1 ≤ k ≤ u.
Lemma 6 For A = {A1, A2,…, Au} generated by formula (7.12) with respect to U = {R1, R2,…, Ru} where J(Rk) = 1/2, Ak is a random grid with J(Ak) = 1/2 for 1 ≤ k ≤ u.
Proof We prove by mathematical induction. For the case of |A| = 1 (i.e., u = 1), since a1 ∈ A1 is equal to r1 ∈ R1 by formula (7.12), A1 is exactly the same as R1. Thus, A1 is a random grid with J(A1) = J(R1) = 1/2. Assume that the statement holds for the case of |A| = u − 1, that is, A1, A2,…, Au−1 are random grids with J(Ak) = 1/2 for 1 ≤ k ≤ u − 1. Due to the reasons that ru(∈ Ru) = 0 or 1, J(Au−1) = 1/2, and for each pixel au ∈ Au, au = f(ru, au−1), we obtain that Au is also a random grid with J(Ak) = 1/2 by Corollary 2.
According to formula (7.12), for each pixel ak ∈ Ak,
That is, the value of ak is determined by its k corresponding pixels r1 , r2 , … , rk for 1 ≤ k ≤ u. From Lemma 6, we know that ak ∈ Ak for 1 ≤ k ≤ u is a random pixel with .
Let be a set of v random grids randomly selected from U, (i.e. v ⊂ U) where 1 ≤ v ≤ u. Let SU(0)(S(0)) denote the area of transparent pixels in SU(SV) where . Now we would like to examine the light transmission of the area of pixels in Au corresponding to SU(0)(S(0)), referred to as Au[SU(0)] (Au[SV(0)]).
Lemma 7
J(Au[SU(0)]) = 1;
J(Au[SV(0)]) = 1/2.
Proof
(1) From Lemma 4, we have J(SU) = 1/2U. Consider pixel s = 0(or s ∈ SU(0)). The only chance for s = 0 is that its corresponding pixels r1, r2,…,ru should all be transparent, i.e., r1 = r2 = ⋯ = ru =0. Under this circumstance, by formula (7.14) s’s corresponding pixel au in Au becomes
That is, if s = 0 (or s ∈ SU(0)). then au = 0. As a result, J(Au[SU(0)]) = 1.
(2) Let where w = u − v (i.e., {j1, j2,…, jw} = {1, 2, … ,u} — {i1, i2, …, iv}). From Lemma 5, we know that both SV and SW are random grids with J(SV) = 1/2v and J(SW) = 1/2u−v. Since the order of random grids does not affect the result of superimposition, without losing generality, let (j1, j2, …, jw) = (1, 2, … , w) and i1, i2,…, iv) = (w + 1, w + 2,…, u). That is, W = {R1, R2,…, Rw} and V = {Rw+1, Rw+2,…, Ru}. (This can easily be done by renaming all of the random grids.) We focus on pixel t = 0 in Sv (or t ∈ Sv(0)) only. Its corresponding pixels rw+1 ∈ Rw+1, rw+2 ∈ Rw+2,…, ru ∈ Ru should all be transparent, i.e., rw+1 = rw+2 = ⋯ = ru =0. Consequently, its corresponding pixel au ∈ Au becomes
From Lemma 6, we have t(au) = 1/2. In summary, if t = 0 in Sv (or t ∈ v(0)), then t(au) = 1/2; therefore, J(Au[Sv(0)]) = 1/2.
Lemmas 5–7 investigate the properties of u random grids in U = {R1, R2, … , Ru} and another u random grids A1, A2, … , Au produced by formula (7.12) with respect to U for u ≥ 2. Now we pay attention to Algorithm 4. Give a secret image B and n participants, Algorithm 4 first produces a set of n − 1 independent random grids, namely R = {R1, R2,…, Rn−1}, based upon which A1, A2,…, An−1 are generated, and then Rn is produced according to An−1 and B. We claim that Rn is a random grid and the superimposed result of any group of less than n shares is also a random grid.
Lemma 8 Give a secret image B and a set of independent random grids R = {R1, R2,…, Rn−1},
Rn generated by formula (7.13) is a random grid with J(Rn) = 1/2; and
SD is a random grid with J(SD) = 1/2d where and .
Proof
By setting u = n − 1 in Lemma 6, we know that An−1 is a random grid with J(An−1) = 1/2 (or t(an−1) = 1/2) for an−1 ∈ An−1• For rn ∈ Rn[B(0)], rn = f(0,an−1) = an−1; while rn ∈ Rn[B(1)], rn = f(1, an−1) = ān−1. It implies that both Rn[B(0)] and Rn[B(1)] are areas of random grids with Rn[B(0)] = 1/2 = Rn[B(1)]. By the principle of combination, Rn is a random grid with J(Rn) = 1/2.
Since the generation of Rn is different for R1, R2,…, Rn−1 (in fact, Rn is generated from B and An−1 which depends upon R1, R2,…, Rn−1 (see formulae (7.12) and (7.13))), there are two cases with regard to the constituents of D : Case 1: Rn ∉ D; and Case 2: Rn ∈ D.
For Case 1, since all random grids in D are independently generated, SD is a random grid according to Lemma 5 with J(SD) = J(SD[B(0)]) = J(SD[B(1)]) = 1/2d.
Regarding Case 2, assume that . Let (i.e., D = L ∪{Rn}) and . From Lemma 5, we realize that SL is a random grid with J(SL) = 1/2d−1. Besides, by setting u = n − 1 and v = d − 1 in Lemma 7(2), we obtain J(An−1[SD(0)]) = 1/2. Consider any pixel an−1 ∈ An−1[SD(0)] and its corresponding pixels st ∈ SD(0) (i.e., where for 1 ≤ k ≤ d − 1), b G B and rn ∈ Rn. If b = 0, rn = f(b, an−1) = f(0, an−1) = an−1; otherwise (b = 1), rn = f(1, an−1) = ān−1. We obtain that t(rn) = 1/2 on condition that st ∈ SD(0). It means that J(Rn[SD(0)]) = 1/2.
To explore the light transmission of SD (= SD ⊗ Rn = (SD (0) ⊗ Rn[SD(0)]) ∪ (SD(1) ⊗ Rn[SD(1)])), we only need to consider the light transmission of SD(0) ⊗ Rn[SD(0)], since no light can pass through the area of SD(1) ⊗ Rn[SD(1)] (note that SD(1) is the area of opaque pixels in SD). Due to the facts that J(SD) = 1/2d−1 = J(SD(0))(by Lemma 5) and J(Rn[SD(0)]) = 1/2 (proved previously). We have J(SD) = J(SD(0) ⊗ Rn[SD(0)]) = J(SD(0)) × J(Rn[SD(0)]) = (1/2d−1) × (1/2) = 1/2d by Lemma 3.
Based upon the above discussions, we prove the correctness of Algorithm 4 in Theorem 2.
Theorem 2 Given a binary image B, ℰ = {R1, R2, …, Rn} produced by Algorithm 4 with respect to B is a set of(n, n)-VCRG of B.
Proof We prove that ℰ = {R1, R2,…, Rn} meets the three conditions in Definition 2 respectively in the following.
From Step 1 of the algorithm, we realize that R = {R1, R2,…, Rn−1} are truly random grids with J(Ri) = 1/2 for 1 ≤ i ≤ n − 1. From Lemma 8(1), Rn is also a random grid with J(Rn) = 1/2. Thus, all of R1, R2,…, Rn are random grids with a light transmission of 1/2. Condition 1 of Definition 2 holds.
Regarding any subset of ℰ with d(< n) random grids, namely , 1 ≤ i1 < i2 < ⋯ < id ≤ n, we have that SD is a random grid with J(SD) = 1/2d from Lemma 8(2). Condition 2 holds.
Let R = {R1, R2,…, Rn−1}, SR = R1 ⊗ R2 ⊗ ⋯ ⊗ Rn-i and sr ∈ SR, rn ∈ Rn, b ∈ B as well as ri ∈ Ri for 1 ≤ i ≤ n − 1 be corresponding pixels. By Lemma 4, we know J(SR) = J(SR[B(1)]) = J(SR[B(0)]) = 1/2n−1. We focus on pixel sr ∈ SR that is transparent. The only case for sr = 0 is r1 = r2 = ⋯ = rn−1 = 0. In this case, their corresponding pixel an−1 ∈ An−1 is also 0 (or J(An−1[SR(0)]) = 1, see also Lemma 7(1) by setting u = n − 1 and U = R). Thus, when b = 0, rn = f(p, an−1) = f(0,0) = 0, while b =1, rn = f(p, an−1) = f(1, 0) = 1. We obtain that r1 ⊗ r2 ⊗ ⋯ ⊗ rn−1 ⊗ rn = sr ⊗ rn = sr ⊗ 0 = sr for b = 0; while r1 ⊗ r2 ⊗•⋯ ⊗ rn−1 ⊗ rn = sr ⊗ rn = sr ⊗ 1 = 1 for b =1. That is, J(Sℰ[B(0)]) = J(SR[B(0)]) = 1/2n−1 > J(SE[B(1)]) = 0. Condition 3 holds.
Since all of the three conditions in Definition 2 hold, we conclude that E = {R1, R2,…, Rn} generated by Algorithm 4 is a set of (n, n)-VCRG of B.
Corollary 3 is an immediate result from Theorem 2.
Corollary 3 (J(Sℰ[B(0)]), J(Sℰ[B(1)])) = (1/2n−1, 0) where ℰ = {R1, R2, …, Rn} is produced by Algorithm 4 with respect to B and Sℰ = R1 ⊗ R2 ⊗ ⋯ Rn.
We give a simple example for n = 3 to explain the relationship among corresponding pixels b ∈ B, r1 ∈ R1, r2 ∈ R2, r3 ∈ R3, a1 ∈ A1, and a2 ∈ A2 in Algorithm 4.
Example 1. Consider n = 3 and a secret image B. Algorithm 4 first generates R1 and R2 independently; then produces A1 and A2 by formula (7.12); at last finds R3 depending on B and A2 according to formula (7.13). Let ℰ = {R1, R2, R3}. Table 7.4 summarizes all of the possible combinations of corresponding pixels b ∈ B, r1 ∈ R1 , and r2 ∈ R2; and their corresponding results of a1(= r1) ∈ A1, a2(= f(r2, a1)) ∈ A2, and r3(= f(b, a2)) ∈ R3; as well as the superimposed results of r1 ⊗ r2, r1 ⊗ r3, r2 ⊗ r3, and r1 ⊗ r2 ⊗ r3. Table 7.5 lists the light transmissions of the corresponding results in Table 7.4.
It is seen from Tables 7.4 and 7.5 that all of R1, R2, R3, A1, A2 are random grids with a light transmission of 1/2. Besides, J(SD[B(0)]) = J(SD[B(1)]) = 1/4 and J(SD[B(0)]) = 1/4 > 0 = J(SD[B(1]) where D(⊂ ℰ) = {R1, R2}, {R1, R3} or {R2, R3}. It means that each group of two random grids obtains no information about B(0) or B(1) when superimposed (thus, no information about the colors of pixels in B can be found), while B(0) and B(1) can be identified from Sℰ due to the difference of their light transmissions, that is, we see B out of Sℰ because of J(Sℰ[B(0)]) > J(Sℰ[B(1)]).
Table 7.4 All possible combinations of b, r1, and r2, the corresponding results of a1(= r1), a2 = f(r2, a1), r3 = f(b, a2), and r1 ⊗ r2, r1 ⊗ r3, r2 ⊗ r3 as well as r1 ⊗ r2 ⊗ r3 by Algorithm 4 for (3, 3)-VCRG.

Algorithm 4 can be viewed as the generalization from the idea in Algorithm 1. Such knowledge can be easily adapted to generalize the ideas in Algorithms 2 and 3. Algorithms 5 and 6 are the results accordingly.
Table 7.5 Light transmissions of the corresponding pixels in Table 7.3.
| b | t(r1) | t(a1) | t(r2) | t(a2) | t(r3) |
| 0 | 1/2 | 1/2 | 1/2 | 1/2 | 1/2 |
| 1 | 1/2 | 1/2 | 1/2 | 1/2 | 1/2 |
| t(r1 ⊗ r2) | t(r1 ⊗ r3) | t(r2 ⊗ r3) | (r1 ⊗ r2 ⊗ r3) |
| 1/4 | 1/4 | 1/4 | 1/4 |
| 1/4 | 1/4 | 1/4 | 0 |
Algorithm 5–6. Encrypting a secret image into n random grid as a set of (n, n)-VCRG (based upon Algorithms 2 and 3, respectively)
Input: an h × w binary image B and an integer n
Output: a set of n random grids ℰ = {R1, R2, …, Rn} constituting (n, n)-VCRG of B
Algorithm 5.
1. for (1 ≤ k ≤ n − 1) do
{generate Rk as a random grid, J(Rk) = 1/2
}
2. for (each pixel B[i, j], 1 ≤ i ≤ h and 1 ≤ j ≤ w) do
2.1 {a1 = R1[i, j]
2.2 for (2 ≤ k ≤ n − 1) do
{ak = f(Rk[i, j], ak−1)
}
2.3 if (B[i, j] = 0) then Rn[i, j] = f(B[i, j], an−1)
( = f(0, an−1) = an−1)
else Rn[i, j] =random_pixel()
}
3. output(R1, R2, …, Rn)
Algorithm 6.
1. for (1 ≤ k ≤ n − 1) do
{generate Rk as a random grid, J(Rk) = 1/2
}
2. for (each pixel B[i, j], 1 ≤ i ≤ h and 1 ≤ j ≤ w) do
2.1 {a1 = R1[i, j]
2.2 for (2 ≤ k ≤ n − 1) do
{ ak = f(Rk[i, j],ak−1)
}
2.3 if (B[i, j] = 0) then Rn[i, j] =random_pixel()
else
}
3. output(R1, R2, …, Rn)
Theorem 3 declares the validity of Algorithm 5 and 6 in producing (n, n)-VCRG.
Theorem 3 Given a secret binary image B, ℰ = {R1, R2, …, Rn} produced by Algorithms 5 or 6 with respect to B is a set of (n,n)-VCRG of B.
The statements in the proof of Theorem 2 can be easily applied to prove Theorem 3. We omit the details here.
In Algorithm 5, if b = 0, rn = f(b, an−1) = f(0, an−1) = an−1, otherwise (b = 1) rn =random_pixel( ). Consequently, we obtain J(Sℰ[B(0)]) = 1/2n−1 by Corollary 3 and J(Sℰ[B(0)]) = 1/2n because all pixels in Rk[B(1)] are random pixels for 1 ≤ k ≤ n. Regarding Algorithm 6, if b = 0, rn =random_pixel(); otherwise (b = 1), rn = f(p, an−1) = f(1, an−1) = ān−1. Thus, we have J(Sℰ [B(0)]) = 1/2n since J(Sk[B(0)]) =J(Rk) = 1/2 for 1 ≤ k ≤ n, and J(Sℰ [B(1)]) = 0 since the only condition for r1 ⊗ r2 ⊗ … ⊗rn to let through the light (i.e., r1 = r2 = … = rn−1 = rn = 0) would never occur (once r1 = r2 = … = rn−1 = 0, we have an−1 = 0; but b = 1 causes rn = ān−1 = 1). We obtain the following corollary.
Corollary 4 (J(Sℰ[B(0)]), J(Sℰ[B(1)])) = (1/2n−1, 1/2n) or (1/2n, 0) where ℰ = {R1, R2, … , Rn} is produced by Algorithms 5 or 6, respectively, with respect to B and Sℰ = R1 ⊗ R2 ⊗ … ⊗ Rn.
The light contrasts of Algorithms 4–6 in point of Definition 3 are summarized in Table 7.6. It is seen from Table 7.6 that among the three approaches, the light contrast obtained by Algorithm 4 is the best.
Table 7.6 Light contrasts by Algorithms 4-6 for ( n, n)-VCRG.
| ℰ | J(S[B(0)]) | J(S [B(1)]) | c(ℰ) |
| Algorithm 4 | 1/2n−1 | 0 | 1/2n−1 |
| Algorithm 5 | 1/2n−1 | 1/2n | 1/(2n + 1) |
| Algorithm 6 | 1/2n | 0 | 1/2n |
7.3.6 Algorithms of (n, n)-VCRG for Gray-Level and Color Images
In Shyu [12], the encryption algorithms of (2, 2)-VCRG for gray-level and color images were generalized from those for a binary image. We apply the same reasoning and skills adopted by Shyu in [12] to extend the binary (n, n)-VCRG algorithms to cope with gray-level and color images.
According to Ref. [12], we simply transform a gray-level image G into its binary version H by some halftone technology and encrypt the binary equivalent by using the aforementioned algorithms directly. Let Encryption_VCRG(B, n) denote the procedure of applying Algorithms 4, 5, or 6 to obtain (n, n)-VCRG with respect to binary image B. Algorithm 7 describes the idea formally.
Algorithm 7. Encrypting a gray-level image into a set of (n, n)-VCRG
Input: an h × w gray-level image G and an integer n
Output: a set of n random grids ℰ = {R1, R2, …, Rn} constituting a VCRG-n of G
1. H = ℋ(G) // ℋ(G) is a halftone function with respect to G
2. (R1, R2,…, Rn) =Encryption_VCRG(H, n)
// Encrypt H by Algorithms 4, 5, or 6 directly
3. output(R1, R2, …, Rn)
Regarding the (n, n)-VCRG for a color image, we follow the experience from Ref. [12] where the binary (2, 2)-VCRG encryption algorithms were extended to their color versions by utilizing skills including color decomposition, halftoning, and color composition. Specifically, we decompose a color image P into the c, m and y components (which are the primitive colors in the sub-tractive model), namely PC, Pm, and Py; halftone each of them to be Pc, Pm, and Py such that each pixel px ∈ Px is either x or 0 where x ∈ {c, m, y} and encrypt the three halftone images into , and by using any of Algorithms 4, 5, or 6 where the corresponding sets of binary colors are {c, 0}, {m, 0}, and {y, 0}, respectively (instead of {1,0}). Let Ri denote the image composed by and , i.e., for 1 ≤ i ≤ n. Then, ℰ = {R1, R2,…, Rn} can be reported as a set of color (n, n)-VCRG of P. It means that only when all Ri’s are superimposed can we see P , while any group of less than n shares obtains nothing but a color random grid.
Let Encrypt_cVCRG(Px, x, n) denote the procedure of encrypting Px into n shares in terms of binary color set {x, 0} where x ∈ {c, m, y}. It is easy to implement Encrypt_cVCRG(Px by using Algorithms 4, 5, or 6 as long as we take 0 and x as the inverse to each other and modify random_pixel() to return 0 or x randomly. Algorithm 8 summarizes the whole idea of producing color (n, n)-VCRG for a color image.
Algorithm 8. Encrypting a color image into a set of (n, n)-VCRG
Input: an h × w color image P and an integer n
Output: a set of n color random grids ℰ = {R1, R2,..., Rn} constituting a (n, n)-VCRG of P
1. Decompose P into (Pc, Pm, Py)
2. for (x ∈ {c, m, y}) do Px = ℋ(Px)
// ℋ(Px) is an x-colored halftone function so that for each px ∈ Px, px = x or 0
3. for (x ∈ {c, m, y}) do
4. for (1 ≤ i ≤ n) do
// color composition of , and
5. output(R1, R2, …, Rn)
Based upon the statements in the proofs of Theorems 2 and 3 as well as those for color (2, 2)-VCRG in Ref. [12], we have the following consequence.
Theorem 4 Given a color image P, ℰ = {R1, R2, …, Rn} produced by Algorithm 8 with respect to P is a set of color (n, n)-VCRG of P.
7.3.7 Experiments for (n, n)-VCRG
We designed four experiments by computer simulations to verify the feasibility and applicability of the VCRG algorithms. Experiment 1 was designed to test Algorithms 4, 5, and 6 to obtain sets of VCRG-3 for a binary image. Experiments 2 and 3 focused on producing sets of VCRG-3 for gray-level and color images, respectively. The sets of VCRG-4 were tested in Experiment 4. All computer programs in these experiments were coded in Borland C++ Builder and run in a PC with Windows.
Experiment 1: Encrypting a binary image to obtain VCRG-3.
In this experiment, we adopted Algorithms 4, 5, and 6 to produce three sets of VCRG-3, respectively, for binary image B as in Figure 7.3. Figure 7.4 illustrates the implementation results of Algorithm 4 where (a), (b), and (c) are the three random grids produced, namely , and , respectively; (d), (e) and (f) are the superimposed results of , and , respectively; and (g) is the result of .

FIGURE 7.3
Binary image B in Experiment 1.
We see from Figure 7.4 that (a)–(f), including and the superimposed results of all groups of two out of the three shares, are merely random grids from which no secret can be obtained, whereas (g) , the superimpositiion of the three random grids, reveals B to our visual system. As a result, produced by Algorithm 4 is indeed a set of VCRG-3 of B. It is lucid that Figure 7.4 provides some visualized evidence to Theorem 2.
Figures 7.5 and 7.6 show the corresponding results of Algorithms 5 and 6 for VCRG-3 with respect to B where and are the two sets of random grids produced by Algorithms 5 and 6, respectively. It is seen from Figure 7.5 and 7.6, and are surely two sets of VCRG-3 of B. The correctness of Theorem 3 is visually shown here.
In summary, based upon Figures 7.4-6, and are random grids with (see Figures 7.4(a)–(c), 7.5(a)–(c), and 7.6(a)–(c)) and (see Figures 7.4(d)–(f), 7.5(d)–(f), and 7.6(d)–(f)) for 1 ≤ i ≠ j ≤ 3 and a ∈ {4, 5, 6}. By comparing the reconstructed images, i.e., and (see Figures 7.3(g), 7.4(g), and 7.5(g), respectively), we realize that (by Algorithm 4) attains the highest light contrast, while (by Algorithm 5) the lowest. In fact, these results are foretold by Table 7.6: c(ℰ4) = 1/4, c(ℰ5) = 1/9, c(ℰ6) = 1/8 for n = 3 where for a ∈ {4, 5, 6}.
Experiment 2: Encrypting a gray-level image to obtain VCRG-3.
Figure 7.7 illustrates the experimental results of applying Algorithm 7 to produce a set of VCRG-3 for a gray-level image. Figure 7.7(a) is the gray-level image G to be encrypted; (b) shows the halftone version H of G by using the error diffusion technology; (c), (d), and (e) present the outcomes of Algorithm 7 where Encryption_VCRG(H, 3) was implemented by Algorithm 4, namely and , respectively; (f), (g), and (h) give the superimposed results of and , respectively; and (i) depicts that of . As seen from Figure 7.7, and the superimposed results from any two out of them are nothing but random pictures, where reveals H, and consequently G. We realize that is a set of VCRG-3 with respect to G.

FIGURE 209.7
Implementation results of Algorithm 4 for VCRG-3 with respect to B: (a) , (b) , (c) ; (d) , (e) , (f) ; (g) .

FIGURE 210.7
Implementation results of Algorithm 5 for VCRG-3 with respect to B: (a) , (b) , (c) ; (d) , (e) , (f) ; (g) .
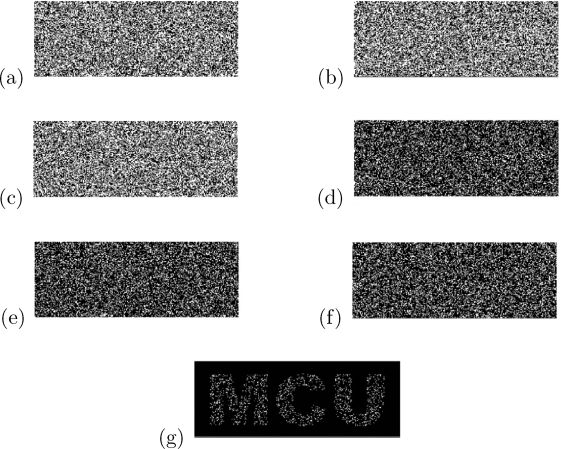
FIGURE 211.7
Implementation results of Algorithm 6 for VCRG-3 with respect to B: (a) , (b) , (c) ; (d) , (e) , (f) ; (g) .
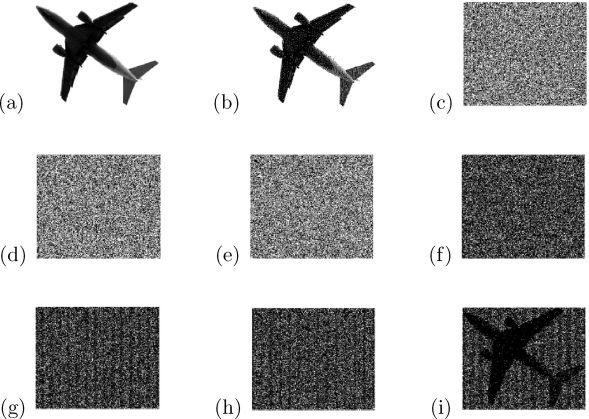
FIGURE 7.7
Results of Algorithm 7 where Encryption_VCRG (H, 3) was implemented by Algorithm 4 with respect to gray-level image G in Experiment 2: (a) G; (b) halftone version H of G; (c) , (d) , (e) ; (f) , (g) , (h) ; (i) .
Let and denote the outcomes of Algorithm 7 when Encryption_VCRG(H, 3) was implemented by Algorithms 5 and 6, respectively, with respect to G. Figures 7.8(a) and (b) are the superimposed results of and , respectively. It is noted that the three encrypted shares and the superimposed result of any group of two out of the three shares are indeed random grids that are omitted here.
The feasibility and applicability for Algorithm 7 to encrypt a gray-level image into VCRG-3 are demonstrated in a visual sense from Figures 7.7 and 7.8. Obviously, implementing Encryption_VCRG (H, 3) based upon Algorithm 4 makes Algorithm 7 achieve the highest contrast (while that based upon Algorithm 5 is the worst).
Experiment 3: Encrypting a color image to obtain color VCRG-3.
We tested Algorithm 8 with respect to a color image for obtaining color VCRG-3 in this experiment. Figure 7.9(a) is the color image P to be encrypted; (b), (c), and (d) are Pc, Pm, and Py, which are the c, m, and y components of P, respectively; (e), (f), and (g) are Pc, Pm, and Py which are the c-, m-, and y-colored halftone images (by error diffusion) of Pc, Pm and Py, respectively.
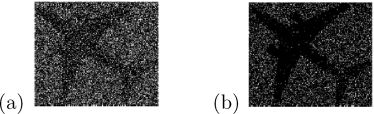
FIGURE 7.8
Reconstructed results of VCRG-3 with respect to G : (a) (b)
By Step 3 of Algorithm 8, Px would be encrypted into by Eycrypt_cVCRG(Px, x, 3) for x ∈ {c, m, y}. When Eycrypt_cVCRG(Pm, m, 3) was based upon Algorithm 4, Figure 7.10 evidences the effectiveness of for being a set of m-colored VCRG-3 with respect to Pm in which (a)–(f) are the results of , and , respectively; and (g) is that of . Regarding Pc and Py, the corresponding results are similar to Figure 7.10 so that we simply omit them.
The encrypted monochromatic-colored shares and were further composed to obtain color random grid for 1 ≤ i ≤ 3 in Step 4 of Algorithm 8. We show the corresponding results in Figure 7.11 where (a)–(c) are color random grids R1, R2, R3; (d)–(f) give results of R1 ⊗ R2, R1 ⊗ R3, R2 ⊗ R3, respectively; and (g) shows that of R1 ⊗ R2 ⊗ R3. When we implemented Eycrypt_cVCRG(Px, x, 3) is based upon Algorithm 4, 5, or 6. The correctness of Theorem 4 holds in a visual sense from the results of Figures 7.8-10.
Experiment 4: Obtaining VCRG-4.
From the above analytic and experimental results, we know that Algorithm 4 achieves the higher light contrast as compared to Algorithms 5 and 6 for binary and gray-level images, so does Algorithm 8 based upon Algorithm 4 as compared to those based upon Algorithms 5 and 6 for a color image. We only tested Algorithm 4 for binary VCRG-4 and Algorithm 8 based upon Algorithm 4 for color VCRG-4 here. Figure 7.12 summarizes the results of binary VCRG-4 where (a) is the binary image B encrypted; (b)–(e) are R1, R2, R3, R4 produced by Algorithm 4; (f) presents the result of R1 ⊗ R2; (g) shows that of R1 ⊗ R2 ⊗ R3; and (h) gives that of R1 ⊗ R2 ⊗ R3 ⊗ R4. Even though the superimposed results from other groups of less than four shares are not shown here, they are really random grids as expected. It is seen from Figure 7.12 that only when all four shares are superimposed can we see B, while no group of less than four shares tells anything about B. {R1, R2, R3, R4} is indeed a set of VCRG-4.

FIGURE 214.7
(See color insert.) Results of Steps 1 and 2 of Algorithm 8 for VCRG-3 with respect to color image P in Experiment 3: (a) P; (b) Pc, (c) Pm, (d) Py; (e) Pc, (f) Pm, (g) Py.

FIGURE 215.7
(See color insert.) Results of Step 3 of Algorithm 8 with respect to Pm where Eycrypt_cVCRG(Pm, m, 3) was based upon Algorithm 4: (a) , (b) , (c) ; (d) , (e) (f) (g) .
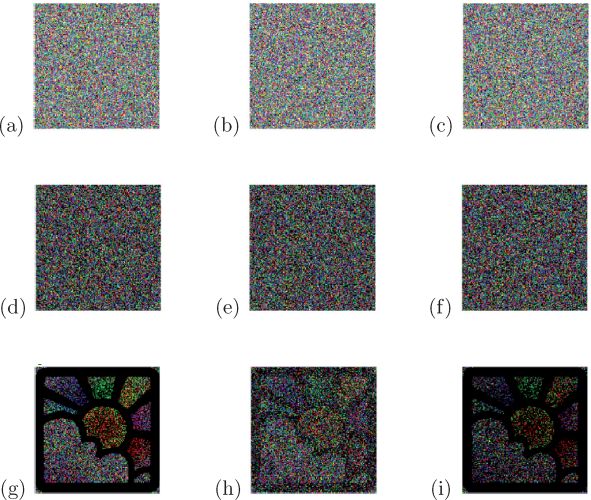
FIGURE 216.7
(See color insert.) Results of Algorithm 8 for VCRG-3 with respect to P: (a) R1, (b) R2, (c) R3; (d) R1 ⊗ R2, (e) R1 ⊗ R3, (f) R2 ⊗ R3; (g) R1 ⊗ R2 ⊗ R3 (based upon Algorithm 4); (h) (based upon Algorithm 5); (i) (based upon Algorithm 6).
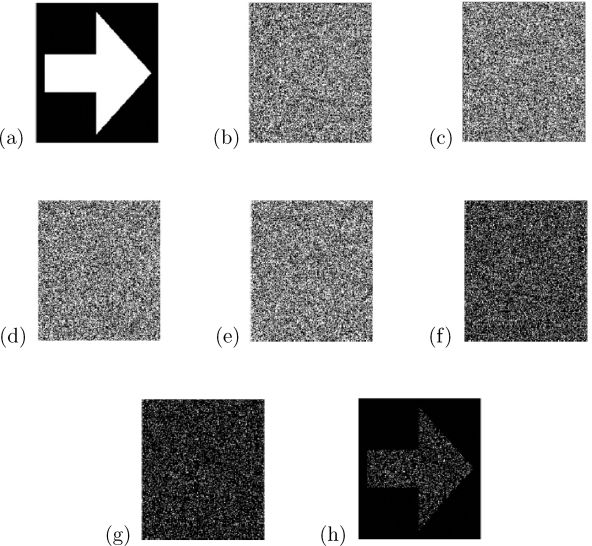
FIGURE 7.12
Results of Algorithms 4 for VCRG-4 with respect to binary image B: (a) B; (b) R1, (c) R2, (d) R3, (e) R4; (f) R1 ⊗ R2; (g) R1 ⊗ R2 ⊗ R3; (h) R1 ⊗ R2; (g) R1 ⊗ R2 ⊗ R3 ⊗ R4.
Since n = 4 in this experiment, we have J(Ri) = 1/2 (see Figures 7.12(b)– (e)), J(Ri ⊗ Rj) = 1/4 (see (f)), and J(Ri ⊗ Rj ⊗ Rk) = 1/8 (see (g)) for 1 ≤ i ≠ j ≠ k ≤ 4. Further, from Table 7.6 we know that the light contrast of Algorithm 4 is c(ℰ4) = 1/8 for n = 4. Figure 7.13 gives some experimental results of Algorithm 8 for color VCRG-4 where Eycrypt_cVCRG(Px, x, 4) was based upon Algorithm 4 with respect to P (see Figure 7.9(a)). Figures 7.13(a)–(d) are the color random grids R1, R2, R3, R4 produced; (e) presents the result of R1 ⊗ R2; (f) shows that of R1 ⊗ R2 ⊗ R3; and (g) gives that of R1 ⊗ R2 ⊗ R3 ⊗ R4. As seen from Figure 7.13, we realize that {R1 ⊗ R2 ⊗ R3 ⊗ R4} is a set of color VCRG-4 of P.
The results of the above four experiments are visualized evidences to the correctness of Theorems 2-4. The proposed schemes (Algorithms 4-8) in producing VCRG-n for a secret image are feasible and applicable. Among the approaches, Algorithm 4 (Algorithm 8 based upon Algorithm 4) is the most effective scheme in terms of light contrast for binary or gray-level (color) images.
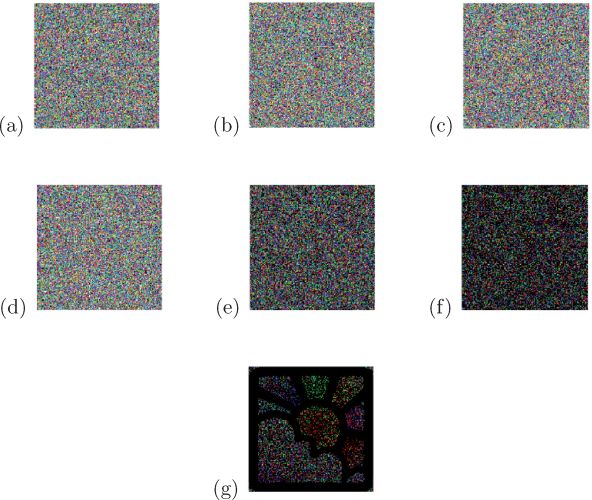
FIGURE 218.7
(See color insert.) Results of Algorithms 8 where Encrypt-cVCRG(Px, x, 4) was based upon Algorithm 4 for VCRG-4 with respect to P (Figure 7.9(a)): (a) R1, (b) R2, (c) R3, (d) R4; (e) R1 ⊗ R2; (f) R1 ⊗ R2 ⊗ R3; (g) R1 ⊗ R2 ⊗ R3 ⊗ R4.
It is noticed that when we adopt the light contrast to measure the reconstructed result for a conventional n out of n visual secret sharing scheme [9], the best result is 1/2n−1. That means that Algorithm 4 achieves the same best light contrast. Moreover, it is so appealing that these schemes neither induce any extra pixel expansion nor require encoding basis matrix. Those approaches in conventional visual cryptography suffer from the disadvantage of the inevitable pixel expansion, which increases exponentially as n increases (and additionally increases as c or [log2c] for the color cases where c is the number of colors in the secret image), in the basis matrices. Table 7.7 summarizes the pixel expansions needed by some efficient n out of n visual cryptographic schemes in the literature and our (n, n)-VCRG schemes. Owing to the reason that the size of the encrypted shares and reconstructed image would not be expanded, our schemes based upon random grids are more attractive than those in conventional visual cryptography for both theoretical concerns and practical applications.
7.4 Concluding Remarks
In this chapter, we propose novel schemes for visual secret sharing using random grids. At first, we give a new definition for the visual cryptograms of n(≥ 2) random grids with respect to a binary image. Based upon the definition, we design effective algorithms, prove their correctness formally, analyze the light contrast in the reconstructed image, and demonstrate their feasibility by computer simulations. By exploiting the skills of halftone and color decomposition in Ref. [12], the enhanced algorithms are also developed and verified to deal with gray-level and color images.
The proposed schemes incorporate human visual intelligence with information security in such a way that no computation but only human vision is needed in the decryption process. They provide cost effective, handy, and portable solutions to image encryption or sharing even for inexperienced users, especially for circumstances where no computer can be accessed. Since a secret image can be encrypted/shared among n(≥ 2) participants (instead of only two), our approaches extend and generalize the studies in Refs. [12, 7] such that the applicability of image encryption or sharing can be broadened to a greater extent.
The n shares of random grids generated by our VCRG-n algorithms work well just like those shares by the conventional n out of n visual secret sharing schemes based upon the definition of Naor and Shamir [9]. However, the pixel expansion in our schemes is 1 for both of the binary and color images, while that in Ref. [9] is 2n−1 for the binary case and that in Ref. [11] is [log2c] × 2n−1 for the color image containing c colors. Therefore, the size of the encoded shares by our schemes would be much smaller (the same as the secret image). Further, the sophisticated encoding basis matrices in Refs. [9, 5, 4, 8, 14, 2, 1, 3, 10, 6, 11] are no more needed in our schemes. Regarding the visual perception in the reconstructed images, our Algorithm 4 achieves the same light contrast as good as the best n out of n visual secret sharing scheme devised in Ref. [9]. These clarify the superiority of our schemes.
Our encryption algorithms can be easily hardwired by incorporating a 0/1 random number generator with T flip-flops or Exclusive-OR gates. It would be an interesting challenge to design a special VCRG hardware for image encryption. In fact, many research topics in conventional visual cryptography could be reexamined in view of random grids.
Bibliography
[1] C.N. Yang and C.S. Laih. New colored visual secret sharing schemes. Des. Codes Cryptogr., 20:325–335, 2000.
[2] C. Blundo, A. De Santis, and D.R. Stinson. On the contrast in visual cryptography schemes. J. Cryptogr, 12:261–289, 1999.
[3] C. Blundo, A. De Santis, and D.R. Stinson. Improved schemes for visual cryptography. Des. Codes Cryptogr., 24:255–278, 2001.
[4] S. Droste. New results on visual cryptography. in: N. Koblitz (Ed.), Advances in Cryptology: CRYPTO96, Lecture Notes in Computer Science, 1109:401–415, 1996.
[5] G. Ateniese, C. Blundo, A. De Santis, and D. R. Stinson. Constructions and bounds for visual cryptography. in: F.M. der Heide, B. Monien (Eds.), Automata, Languages and Programming: ICALP’96, Lecture Notes in Computer Science, 1099, Springer, Berlin: 416–428, 1996.
[6] Y.C. Hou. Visual cryptography for color images. Pattern Recognition, 36:1619–1629, 2003.
[7] O. Kafri and E. Keren. Encryption of pictures and shapes by random grids. Opt. Lett, 12:377–379, 1987.
[8] M. Naor and B. Pinkas. Visual authentication and identification. in: B.S. KaliskiJr. (Ed.), Advances in Cryptology: CRYPTO97, Lecture Notes in Computer Science, 1294:322–336, 1997.
[9] M. Naor and A. Shamir. Visual cryptography. in: A. De Santis (Ed.), Advances in Cryptology: Eurpocrypt’94, Lecture Notes in Computer Science, 950:1–12, 1995.
[10] P.A. Eisen and D.R. Stinson. Threshold visual cryptography schemes with specified whiteness levels of reconstructed pixels. Des. Codes Cryptogr., 25:15–61, 2002.
[11] S.J. Shyu. Efficient visual secret sharing scheme for color images. Pattern Recognition, 39:866–880, 2006.
[12] S.J. Shyu. Image encryption by random grids. Pattern Recognition, 40:1014–1031, 2007.
[13] S.J. Shyu. Image encryption by multiple random grids. Pattern Recognition, 42:1582–1596, 2009.
[14] E.R. Verheul and H.C.A. Van Tilborg. Constructions and properties of k out of n visual secret sharing schemes. Designs Codes Cryptography, 11:179–196, 1997.
