8
Visual Cryptography and Contrast Bounds
Andreas Klein
Ghent University, Belgium
8.3 Approximate Inclusion Exclusion
8.5 Optimal 3-out-of-n Schemes
8.6 Asymptotic Optimal k-out-of-n Schemes
8.7 Contrast Trade-Offs for Extended Visual Cryptography Schemes
8.1 Introduction
To describe a visual cryptography scheme we encode the encryption of a pixel by Boolean matrices. The rows represent the slides and the columns represent the different subpixels.
For example, the encoding illustrated in Figure 8.1 is described by
M=(010100110110).
To describe the random decision, which must be made when encoding a pixel, we use multisets that contain all possible choices with the right frequency.
This leads to the formal definition of a visual cryptography scheme.
Definition 1 Let Γ be any access structure for n persons. A visual cryptography scheme is a pair of multisets Mb and Mw of Boolean n × m matrices. Which satisfy:

FIGURE 224.8
Example of encoding a visual cryptography scheme.
|Mb| = |Mw| = r
For each ∈ ∉ Γ the restriction of all matrices in Mb to the rows indexed by i ∈ ∈ gives the same multiset of |G| × n matrices as the restriction of all matrices in Mw to the rows indexed by i ∈ G. (This formalizes the requirement that an unqualified set of persons gain no information about the secret.)
G ∈ Γ is a minimal qualified set if every proper subset G′ ⊂ G is not an element of Γ.
For each minimal qualified set of persons G the restriction of a matrix in Mb to the rows indexed by i ∈ G give a |G| × m matrix with at least h(G) nonzero columns and the restriction of a matrix in Mw to the rows indexed by i ∈ G give a |G| × m matrix with at least l(G) nonzero columns. The inequality h(G) > l(G) must be satisfied. (This formalizes the idea that we see a black pixel as a darker gray than a white pixel.)
Note: The condition (a) can be relaxed a bit, we choose |Mb| = |Mw| for simplicity. Some authors require that condition (c) holds for all qualified sets G ∈ Γ not only for the minimal qualified sets.
The performance of visual cryptography scheme is described by 3 parameters.
The randomness r, that measures the amount of entropy needed to encode an image.
The number of subpixels m need to encode an pixel (pixel expansion).
The contrast α = min{(h(G) − l(G))/m|G ∈ Γ} that measures the quality of the reconstructed image.
In applications the contrast is the most important factor. (Anything below 1/10 can be hardly used if you really stack transparencies.) Thus, finding contrast optimal schemes is an important task.
The goal of this chapter is to prove upper bounds on the possible contrast and to construct schemes near that bounds.
8.2 Preliminaries
For the moment we will ignore the pixel expansion and the randomness. Then contrast optimal visual cryptography schemes can be simplified.
Lemma 1 Let Γ be any access structure then there exists a contrast optimal visual cryptography scheme (MW, Mb) for Γ with the property that MW is the multiset of all column permutations of a matrix Mw and Mb is the multiset of all column permutations of a matrix MB.
Proof
Let (M′W, M′B) be a contrast optimal visual cryptography scheme for Γ with pixel expansion m and randomness r.
Let MW = (M′W(1), …, M′W(r)) be the n × (mr) matrix which consist of all matrices M′W(i) ∈ M′W(i = 1, …,r) written in sequence, one after the other. Similarly let MB be the n × (mr) matrix that consists of the matrices in M′B written after each other.
Let G ∉ Γ, by Definition 1 (b) the restriction of MW and MB to the rows i ∈ Γ must give return two matrices that different only for a permutation of their columns, i.e., the scheme (MW, MB) satisfies the security requirement (Definition 1 (b)).
Now let G ∈ Γ by Definition 1 (c) the restriction of every matrix in MB to the rows i ∈ Γ contains at least am more nonzero columns than the restriction of a matrix in MW to the same rows. Thus, the restriction of MB to the rows i ∈ Γ contains at least amr more nonzero columns than the restriction of MW to the rows i ∈ Γ. That proves that the scheme (MW, MB) reconstructs the secret image.□
The advantage of the scheme constructed by Lemma 1 is that the visual cryptography scheme is now described by just two Boolean matrices M′W and M′B instead of two multisets of Boolean matrices. Moreover the order of the columns in M′W and M′B does not matter. For each S ⊆ {1, … ,n} let x(W)S
The security requirements of the visual cryptography scheme translates to the linear equations
∑S⊆{1,…n}S∩G≠0x(W)s=∑S⊆{1,…n}S∩G≠0x(B)s(8.1)
for all G ∉ Γ and the requirement that a qualified subset can see the image translates to
∑S⊆{1,…n}S∩G≠0x(W)s=∑S⊆{1,…n}S∩G≠0x(B)s(8.2)
for all minimal qualified subsets G.
The equations (8.1) and (8.2) lead to the linear program. Replace (8.1) by
∑S⊆{1,…n}S∩T≠0x(W)s+α≤∑S⊆{1,…n}S∩T≠0x(B)s
and require
∑S⊆{1,…n}x(B)s=∑S⊆{1,…n}x(W)s=1
and maximize α. For small values of n it is no problem to feed that program into a computer and get the optimal visual cryptography scheme. (I prepared such a program for my book [11]. You can download it from my homepage http://cage.ugent.be/~klein/vis-crypt/buch/).
For the k-out-of-n access structure it is possible to simplify the linear program and solve it directly.
Lemma 2 Let Γ be the k-out-of-n access structure. Then in addition to Lemma 1 we can require that any row permutation of Mw is also a column permutation of MW and, similarly, every row permutation of MB is also a column permutation of MB.
Proof
Let MW and MB be the two Boolean matrices that describe the visual cryptography scheme constructed in Lemma 1.
For every row permutation a the matrices MσW
Let MσW
Lemma 2 allows us to simplify the linear program for a contrast optimal k-out-of-n visual cryptography scheme. With the notations from above we get x(B)S=x(B)S′
The linear program simplifies to:
n∑i=0(ni)x(W)i=n∑i=0(ni)x(B)i=1(8.3)
This equation express that the variables denotes the fractions of black subpixels and that all fractions add up to 1.
n−j∑i=0(n−ji)x(W)i=n−j∑i=0(n−ji)x(B)i(8.4)
for j = 0, …, k − 1. This equation expresses that the stack of j transparencies always has the same number of white subpixels and replaces (8.1).
Maximize
α=n−k∑i=0(n−ki)x(W)i−n−k∑i=0(n−ki)x(B)i(8.5)
In this form the linear program is simple enough to solve it directly. We will track this problem in Sections 8.5 and 8.6.
The linear program has been independently deduced by several researchers. (Variable transformations like ˆx(W)i=x(W)n−i or ˆx(W)i=(ni)x(W)i
8.3 Approximate Inclusion Exclusion
The well-known inclusion-exclusion-formula states.
|A1∪A2∪…∪An|=∑i|Ai|−∑|Ai∩Aj|+ ∑i<j<k|Ai∩Aj∩Ak|−…−(−1)n|A1∩…∩An|.
Obviously, every term on the right-hand side is needed to determine the size of the union. At this point we can ask whether it is possible to give an approximate inclusion-exclusion formula. More formally we ask:
Given integers m, n with m ≤ n and sets A1, …, An and B1, …, Bn where not all Bi are empty and where
|∩i∈SAi|=|∩i∈SBi|
for every subset S ⊆ {1, …,n} such that |S| < m, what is the smallest (or largest) possible value for the fraction
|A1∪…∪An||B1∪…∪Bn|?
The problem of approximate inclusion-exclusion is closely related to contrast bounds in visual cryptography schemes. For n-out-of-n and (n−1)-out-of-n scheme the solution of the approximate inclusion-exclusion problem translates directly to a contrast optimal visual cryptography scheme (see Theorem 4 for the details of the translation). Other applications of the approximate inclusion-exclusion are constant depth circuits and Boolean functions [15].
It is convenient to replace the size of the sets in the approximated inclusion exclusion problem by arbitrary measures to get a continuous problem. This leads to the following problem. Let (Ω, A, μ) be a measurable space and let A1, …, An and B1, …, Bn be measurable sets with
μ(∩i∈SAi)=μ(∩i∈SBi)
for every subset S ⊆ {1, …, n} such that |S| < m, what is the smallest (or largest) possible value for the fraction
μ(A1∪…∪An)μ(B1∪…∪Bn)?
Similarly to Lemma 1 we can restrict the approximate inclusion-exclusion problem to symmetric collections. With
xi=(nj)[μ(∩j∈SAj∩∩j∉S¯Aj)−μ(∩j∈SBj∩∩j∉S¯Bj)]
for |S| = i the approximate inclusion-exclusion problem leads to the linear program
Maximize:n∑i=1xi(8.6)
subject to:
n∑i=j(ij)xi=0for1≤j<m(8.7)
−1≤∑i∈Sxi≤1for all S⊆{1,…,n}.(8.8)
(See [15] Lemma 3 for a proof).
Dualizing the linear program leads to the following problem of approximation theory (see [15] Lemma 5 and Section 8.6 where we use that technique to determine the asymptotic behavior of k-out-of-n schemes).
Determine
infqmaxx=1,…,n1−q(x)(8.9)
where the infimum ranges over all polynomials q of less than m that have zero constant terms and satisfies q(x) ≤ 1 for all x ∈ {1, …, n}.
The special case m = n leads to Krawtchuck polynomials (see [15] Theorem 3). But for this special case a elementary combinatorial proof exists (see [12]).
Theorem 3 Let A1, …, An and B1, …, Bn be two collections of sets satisfying
|∩i∈SAi|=|∩i∈SBi|
for all proper subsets S of {1, …, n}. Then
|∪ni=1Bi|−|∪ni=1Ai||∪ni=1Bi|≤12n−1.
The bound is sharp.
Proof
We prove by induction on n that the conditions
|∩i∈SAi|=|∩i∈SBi|
for all S ⊊ {1, …, n} and the condition
|n∪i=1Ai|+k=|n∪i=1Bi|
with k > 0 imply that
|n∪i=1Bi|≥k2n−1.
For n = 1 this is trivial. Now suppose that the theorem holds for n and let the sets A1, …, An+1 and B1, …, Bn+1 satisfy
|∩i∈SAi|=|∩i∈SBi|
for all S ⊊ {1, …, n +1} and
|n+1∪i=1Ai|+k=|n+1∪i=1Bi|.
The collections A′i = AiAn+1 and B′i = BiBn+1 satisfy |∪ni=1A′i|+k=|∪ni=1B′i| and for every proper subset S ⊊ {1, …, n} we have
|∩i∈SA′i|=|∩i∈SAi|−|∩i∈SAi∩An+1| =|∩i∈SBi|−|∩i∈SBi∩Bn+1|=|∩i∈SB′i|.
Thus the collections A′i, B′i satisfy the induction hypothesis, i.e., we have |∪ni=1B′i|≥k2n−1.
On the other hand, we have the collections A″i = Ai ∩ An+1 and A″i = Bi ∩ Bn+1. Since
|n∪i=1Ai|=|n∪i=1Bi|⇔|n∪i=1A′i|+|n∪i=1A′′i|=t|n∪i=1B′i|+|n∪i=1B′′i|
and |∪ni=1A′i|+k=|∪ni=1B′i| we find that the collections A″i and B″i satisfy the induction hypothesis with |∪ni=1B″i|+k=|∪ni=1A″i|. Thus, |Bn+1|=|An+1|≥|∪ni=1A″i|≥k2n−1. This proves
|n+1∪i=1Bi|=|n∪i=1B′i|+|Bn+1|≥k2n−1+k2n−1=k2n
as desired.
To see that the bound is sharp consider the sets
Ai={S⊂{1,…,n}||S|even,i∈S}
and
Ai={S⊂{1,…,n}||S|odd,i∈S}.
Since for each nonempty set the number of subsets of even cardinality is trie same as the number subsets of odd cardinality (0=(1−1)n=∑nj=0(−1)j(nj)) we get
|∩i∈SAi|=|∩i∈SBi|=2n−|S|−1
for each proper subset S of {1, …, n}. Hence, the sets Ai and Bi satisfies the requirement conditions of the approximate inclusion-exclusion problem and
|∪ni=1Bi|−|∪ni=1Ai||∪ni=1Bi|=2n−1−(2n−1−1)2n−1=12n−1,
i.e., the bound given by the Theorem is sharp.□
Theorem 3 translates directly to an contrast optimal n-out-of-n visual cryptography scheme.
Theorem 4 (see [16]) The optimal contrast of a n-out-of-n visual cryptography scheme is α = 21−n and the minimal pixel-expansion is m = 2n−1.
Proof
By Lemma 1 a n-out-of-n visual cryptography scheme can be described by two Boolean matrices MW and MB.
Interpret the row vectors of MW and MB as incidence vectors of the sets Ai and Bi.
The security requirement ((b) in Definition 1) says |∪i∈S Ai| = |∪i∈S Bi| for all proper subsets S of {1, …, n}. By the inclusion-exclusion formula this is equivalent to |∪i⊂S Ai| = |∪i⊂S Bi| for all proper subsets S of {1, …, n}. By Theorem 3 we have
α=|∪ni=1Bi|−|∪ni=1Ai||∪ni=1Bi|≤21−n.
Vice versa the incidence vectors of sets solving the approximated inclusion-exclusion problem define a contrast optimal n-out-of-n visual cryptography scheme. Note that 1/α is also a lower bound for the pixel expansion m and the example shows that this bound is sharp. ☐
Using the proof technique of Theorem 3 one could also solve the approximate inclusion-exclusion problem for the case that only the size intersections of up to n − 2 sets are known.
Result 5 (see [12] Theorem 3.6) Let A1, …, An and B1, …, Bn be two collections of sets satisfying
|∩i∈SAi|=|∩i∈SBi|
for all proper subsets S of {1, …, n} with |S| ≤ n − 2. Then
|∪ni=1Ai||∪ni=1Bi|≥1−(n−1⌊n−12⌋)−1.
The bound is sharp.
For the proof see [12]. At this point we show only the construction that proves the sharpness.
We give for every subset S ⊆ {1, …, n} the size
|∩i∈SAi∪i∉SAi|and|∩i∈SBi∪i∉SBi|.
The construction is best understood if we look at the example n = 9 first.
In general we will have a zigzag line of numbers starting on the left side in the B-row with the value ⌊n−12⌋, going down to 1, then has one gap and restart with 1. The general rule is as follows:
|∩i∈SAi∪i∉SAi|={|S|−⌈n2⌉if |S|>n/2,and|S|is odd⌈n2⌉−|S|if |S|<n/2,and|S|is even0in all other cases(8.10)
|∩i∈SBi∪i∉SBi|={|S|−⌈n2⌉if |S|>n/2,and|S|is even⌈n2⌉−|S|if |S|<n/2,and|S|is odd0in all other cases(8.11)
Some elementary combinatorial calculations ([12] Theorem 3.8) show that this example satisfies Result 5 with equality.
Similar to Theorem 4 we can use Result 5 to prove that the contrast α of the optimal (n−1)-out-of-n visual cryptography scheme satisfies α≤2n(n−1⌊n−12⌋). The example given above can be used to construct a scheme that satisfies the bound with equality (see [12] Theorem 3.10).
8.4 Designs and Codes
2-out-of-n visual cryptography schemes are a very special case. In a symmetric, contrast optimal scheme we encode a white pixel by giving all participants the same share. For a black pixel we want to minimize the overlap of black subpixels on the transparencies. This is a typical coding theory problem.
The link to coding theory becomes clear by comparing the following two theorems and their proofs.
Theorem 6 (Plotkin bound) A binary code of length n with minimal distance d>12n has at most 2⌊d2d−n⌋ codewords.
Proof
Let m be the number of codewords. Let A = ∑c≠c′ d(c, c′) where the sum ranges over all pairs of codewords. Since the code has minimal distance d the sum is bounded below by (m2)d.
Let mi be the number of codewords that have 1 in the ith column. The contribution of those columns to the total distance A is mi(m − mi) ≤ ⌊m/2⌋ ⌈m/2⌉.
Hence, ⌊m/2⌋⌈m/2⌉≥A≥12m(m−1)d. For d>12n this gives the bound stated by the Theorem. □
Theorem 7 ([3] Theorem 4.2) The contrast a of an 2-out-of-n visual cryptography scheme is bounded by
α≤⌈n/2⌉⌊n/2⌋n(n−1)={n4n−4for n evenn+14nfor n odd
Proof
Let m be the number of subpixels and α be the contrast. When stacking transparencies the fraction of black subpixels cannot become smaller. Thus, the number of black subpixels on each transparencies must be increased at least by am, i.e. for every transparency t1 and every transparency t2 there must be at least am subpixels that are write on t1 and black on t2. All pairs of transparencies give, therefore, at least n( n − 1) αm black-white subpixel combinations.
Now look at the number of black-white combinations that come from a single subpixel. If the subpixel is white on i transparencies and black on n − i transparencies it contributes i(n − i) black-white combinations. The term i(n − 1) is bounded by ⌊n/2⌋ ⌈n/2⌉.
This lead to the inequality
n(n−1)αm≤⌊n/2⌋⌈n/2⌉m.
Solving the inequality gives the theorem.
The bound of Theorem 7 is sharp and the contrast optimal 2-out-of-n schemes are related to designs. Let’s recall the definition of a 2 — (v, k, λ) design. (I recommend [1] as a reference for design theory.)
Definition 2 A 2 − (v,k, λ) design is a an incidence structure (V, B, I) with
|V| = v points
Every block B ∈ B is incident with k points.
Every pair of points p, q ∈ V is joined by exactly λ blocks.
Theorem 8 (see [3] Theorem 4.4) Let n be even. A 2-out-of-n visual cryptography scheme with optimal contrast α=n+14n and pixel expansion m exists if and only if there exists a 2−(n,n2,m(n−2)4n−4) design.
Proof
If we have equality in Theorem 7 we must have equality in every step.
Thus, for each two transparencies there are exactly am subpixels that are white on the first and black on the second transparency. Furthermore, each subpixel is black on exactly n/2 transparencies.
Let MB be the Boolean matrix that describes the encoding of a black pixel. Interpret MB as an incidence matrix of incidence structure (V, B, I) (Columns of MB corresponds to block and rows of MB to points.)
As we have seen above every block consists of n2 points.
Since for every two transparencies the number of subpixels that is white on the first and black on the second is constant. Each transparency must have the same number of black subpixels. Since each subpixel is black on exactly half of the transparencies the number of black subpixels per transparency must be m2.
Thus, two transparencies have exactly m2=αm=m(n−1)4n−4 common black subpixels In the interpretation as incidence structure: Each two points are joined by m(n−1)4n−4 blocks.
In other words MB is the incidence matrix of a 2−(n,n2,m(n−2)4n−4) design. Conversely the incidence matrix of a 2−(n,n2,m(n−2)4n−4) design satisfies all requirements of a 2-out-of-n visual cryptography scheme. □
Similarly, we can deal with the case of n odd. The Proof of Theorem 7 shows that every column in MB must contain either ⌊n/2⌋ or ⌈n/2⌉ zero entries. So we do not get a design (every block is of the same size), but a structure called pairwise balanced design (PDB) where the size of block may vary between some values. We skip the details and just state the final result.
Result 9 (see [3] Theorem 4.5) Let n he odd. A 2-out-of-n visual cryptography scheme with optimal contrast α=n4n−4 and pixel expansion m exists if and only if there exists a 2−(n,{n−12,n+12},w−m(n+1)4n) PBD such that every point lies in exactly w blocks, where w is an integer in the range
(n−1)m2n≤w≤(n+1)m2n.
A well-known result from coding theory states that Hadamard codes archive equality in the Plotkin bound. So we are not surprised that Hadamard matrices can also be used to construct optimal 2-out-of-n visual cryptography schemes.
Recall the Definition of Hadamard matrices.
Definition 3 A Hadamard matrix is a n × n matrix H with entries ±1 and HHt = nI.
It is well known that except for n = 1, 2 the order of a Hadamard matrix must be divisible by 4. The famous Hadamard conjecture states that for every n a (4n) × (4n) Hadamard matrix exists. See [8] for an overview of constructions of Hadamard matrices.
The connection to visual cryptography is established by the next theorem.
Theorem 10 (see [3] Theorem 4.7) The pixel expansion of a contrast optimal 2-out-of-(4n − 1) visual cryptography scheme is at least m ≥ 4n − 1. A scheme with m = 4n − 1 is equivalent to the existence of a 2 − (4n − 1, 2n − 1, n − 1) design (called a Hadamard design). This is equivalent to the existence of a Hadamard matrix of order 4n.
Proof
Let Mb be the matrix describing the encoding of a black pixel. As in the proof of Theorem 8 we find that each transparency must have the same number w of black subpixels and each two transparencies must share the same number λ < w of black subpixels. Interpret MB as an integer matrix, then
MBMtB=(w−λ)I+λJ.
This matrix has a full rank (det(w − λ)I + λJ = (w − λ)n−1 (nλ − λ + w)) and hence,
4n−1=rankMBMtB≤rankMB≤m.
(This is the Fisher’s inequality.)
Now assume m = 4n − 3 then w must be either 2n − 1 or 2n. In the first case every column of MW must contain 2n − 1 entries 1 and MW is the incidence matrix of a 2 − (4n − 1, 2n − 1, n − 1) design. In the second case every column of MW must contain 2n entries 1 and MW is the incidence matrix of a 2 − (4n − 1, 2n, n) design. But then the complement of MW is the incidence matrix of a 2 − (4n − 1, 2n − 1, n − 1) design. This shows that a contrast optimal 2-out-of-(4n − 1) visual cryptography scheme with pixel expansion m = 4n − 3 implies the existence of a 2 − (4n − 1, 2n − 1, n − 1) design. But conversely you get a 2-out-of-(4n − 1) visual cryptography scheme from a 2 − (4n − 1, 2n − 1, n − 1) design by defining Mb to be the incidence matrix of the design and encode it with a pixel by choosing on all transparencies the same subpixels.
Now we prove that the existence of 2 − (4n − 1, 2n − 1, n − 1) design is equivalent to the existence of a Hadamard matrix of order 4n.
Multiplying a row or a column of a Hadamard matrix with −1 again gives a Hadamard matrix. So without loss of generality we may assume that the first row and the first column of a Hadamard matrix has only 1 as entries. Let H be a Hadamard matrix of order 4n in that normal from. All rows except the first row of H must contain 2n entries −1 and for two rows different rows must differ in exactly 2n columns. Hence, after deleting the first row and first column H forms the incidence matrix of a 2 − (4n − 1, 2n − 1, n − 1) design (with −1 instead of 0 to mark that a point is not incident with a block). Conversely the incidence matrix of a 2 − (4n − 1, 2n − 1, n − 1) becomes a Hadamard matrix, if one replaces all 0 by −1 and adds an extra column and an extra row that contains only 1.
Other 2-out-of-n visual cryptography schemes are also connected to Hadamard matrices.
Result 11 (see [3] Theorem 4.9) The minimal pixel expansion m of contrast optimal 2-out-of-n visual cryptography schemes satisfies:
m≥{2n−nif n evennif n ≡3mod 42nif n ≡1mod 4
If the Hadamard conjecture is true the bounds are sharp.
We remark that there are 2-out-of-n visual cryptography schemes with smaller pixel-expansion that are not contrast optimal. In [3] (Theorem 4.12) 2-out-of-n visual cryptography schemes with pixel expansion m≈√n and contrast α≈14 are constructed. For n=(m⌊m/2⌋) there exists a 2-out-of-n visual cryptography scheme with pixel expansion m and contrast 1/m (just color on each transparency is a different set of ⌊m/2⌋ subpixels). This is the minimal possible pixel expansion.
8.5 Optimal 3-out-of-n Schemes
We construct a scheme that has the normal form of Lemma 2. Remember that we denoted by x(W)i the number of subpixels when encoding a white pixel that are black of the slides 1, …, i and white on the other slides. Similarly x(B)i describes the encoding rule for a black pixel. As we have seen in the introduction, a k-out-of-n scheme must satisfy
αm=n−k∑i=0(n−ki)x(W)i−n−k∑i=0(n−ki)x(B)i(8.12)
and
n−j∑i=0(n−ji)x(W)i−n−j∑i=0(n−ji)x(B)i(8.13)
for j = 0, …, k − 1.
Let S(3, g, n) be the visual cryptography scheme that is described by the values x(W)0=x(B)n=(n−1g)−(n−1g−1),x(W)n−g=x(B)g=1 and all other variables are 0.
Theorem 12 ([2] Theorem 4.6) S(3, g, n) is a 3-out-of-n visual cryptography scheme with pixel expansion m =2(n−1g) and contrast
α=g(n−2g)2(n−1)(n−2).
Proof
For j = 0 we have in (8.13):
(n0)[(n−1g)−(n−1g−1)]+(nn−g)⋅1=(ng)⋅1+(nn)[(n−1g)−(n−1g−1)]=m
For j = 1 we get
(n−10)[(n−1g)−(n−1g−1)]+(n−1n−g)⋅1=(n−1g)⋅1
which is also true, since (n−1n−g)=(n−1g−1). For j = 2 we get
(n−20)[(n−1g)−(n−1g−1)]+(n−2n−g)⋅1=(n−2g)⋅1
which is true since (n−1g)−(n−1g−1)=(n−2g) and (n−2g)+(n−2n−g)=(n−2g)+(n−2q−1)=(n−2g).
Thus, S(3, g, n) satisfies the security requirements of an 3-out-of-n visual cryptography scheme.
The contrast of S(3, g, n) is
αm=(n−30)[(n−1g)−(n−1g−1)]+(n−3n−g)⋅1−(n−3g)⋅1=(n−2g)+(n−2g−1)−(n−1g−1)+(n−3g−3)−(n−33)=(n−3g−1)−(n−2g−3)+(n−3g−3)=(n−3g−1)−(n−3g−2)
So the image is indeed recovered.
The scheme S(3, g, n) archives optimal contrast if we choose g=⌊n+14⌋. This is the best possible contrast for a 3-out-of-n scheme. To prove this result we introduce the canonical form of a k-out-of-n scheme.
Remember that a k-out-of-n scheme is described by the following linear program.
Maximize:
α=n−k∑i=0(n−ki)x(W)i−n−k∑i=0(n−ki)x(B)i(8.14)
Subject to
n∑i=0(ni)x(W)i−n∑i=0(ni)x(B)i=1(8.15)
and
n−j∑i=0(n−ji)x(W)i=n−j∑i=0(n−ji)x(B)i(8.16)
for j = 0, …, k − 1.
Lemma 13 There is an optimal solution of the linear program defined by (8.14), (8.15), and (8.16) that satisfies:
If k is even, then x(W)i=x(W)n−i and x(B)i=x(B)n−i for i = 0, …, n.
If k is odd, then x(W)i=x(B)n−i for i = 0, …, n.
x(W)ix(B)i=0 for all i ∈ {0, …, n}.
We will say the solution of the linear program is in a canonical form.
Proof
We first show that replacing each transparency of a k-out-of-n visual cryptography scheme by its complement again gives a solution of a k-out-of-n visual cryptography scheme. In the language of linear programming:
Let x(W)i,x(B)i be a solution of the linear program (8.14)–(8.16). We claim that
ˆx(W)i={x(W)n−iif k is evenx(B)n−iif k is odd
and
ˆx(B)i={x(B)n−iif k is evenx(W)n−iif k is odd
is also a solution of the linear program.
Since (ni)=(nn−i) the variables ˆx(W)im ˆx(B)i satisfy (8.16).
We claim that equation 8.16 implies
n−j∑i=0(n−ji−h)x(W)i=n−j∑i=0(n−ji−h)x(B)i
for all h ≤ j. For j = 0 this is trivial and for j ≥ 1, h ≥ 1 it follows from (n−ji−h)=(n−j+1i−h+1)−(n−ji−h+1) by induction
n−j∑i=0(n−j+1i−h+1)x(W)i=n−j∑i=0(n−j+1i−h+1)x(B)i
and
n−j∑i=0(n−ji−h+1)x(W)i=n−j∑i=0(n−ji−h+1)x(B)i
To simplify the notation let us assume in the following that k is even.
When k is odd, it is necessary to exchange x(W)i by x(B)i and vice versa.
n−j∑i=0(n−ji)ˆx(W)i=n−j∑i=0(n−ji)x(W)n−i=n∑i=j(n−jn−i)x(W)i=n∑i=j(n−jn−i)x(W)i=n∑i=j(n−jn−i)x(B)i=n−j∑i=j(n−jn−i)x(B)i
i.e., the variables ˆx(W)im ˆx(B)i satisfy (8.16).
By the same argument we get
n−k∑i=0(n−ki−h)x(B)i+(−1)hα=n−k∑i=0(n−ki−h)x(W)i(8.17)
for h ≤ k.
For h = k this shows that ˆx(W)im ˆx(B)i is an optimal solution of the linear program.
Let x(W)i,x(B)i,x(W)i and ˆx(B)i be two solutions of the linear program, then ˜x(W)i=12(x(W)i+x(W)i),˜x(B)i=12(x(B)i+ˆx(B)i) is also a solution of the linear program.
After this transformations we have a solution that satisfies (a) and (b).
Assume that we have a scheme that does not satisfy (c), i.e., the matrices MW and MB have columns in common. Since the corresponding subpixels occur independent of the encoded color they can be omitted. Deleting all columns that occur in MW and MB we get a scheme with smaller pixel expansion and higher contrast. That proves that every optimal k-out-of-n scheme must satisfy (c). □
Now we are ready to determine the optimal contrast of a 3-out-of-n visual cryptography scheme.
Theorem 14 ([2] Theorem 4.7) The contrast a of a 3-out-of-n visual cryptography scheme satisfies
α≤(n−2⌊n+14⌋)⌊n+14⌋2(n−1)(n−2)
Proof
Assume that the scheme is in canonical form (see Lemma 13) and let MW and MB be the n × m Boolean matrices that describe the encoding.
Since the scheme is in canonical form, m is even and exactly m′=m2 subpixels on each slide are black. In terms of the linear program this means
n−1∑j=0x(W)j(n−1j)=n−1∑j=0x(B)j(n−1j)=12.(8.18)
By equation 8.17 (with h =1) the contrast α is
α=n−k∑i=0(n−3i−1)x(B)i−n−k∑i=0(n−3i−1)x(W)i
Since the scheme is in canonical form we have x(W)i=x(B)n−i and hence,
α=n−k∑i=0((n−3i−1)x(B)i−(n−3i−1)x(B)n−i)=n∑i=0x(B)i((n−3i−1)−(n−3n−i−1))=n∑i=0x(B)i((n−3i−1)−(n−3i−2))
Now use equation (8.18) to multiply with 1 and we get
α=∑ni=0x(B)i((n−3i−1)−(n−3i−2))2∑ni=0x(B)i(n−1j)
The inequality ∑xf(x)∑xg(x)≤maxxf(x)g(x) holds for any functions f and g. Hence,
α≤max0≤i≤n(n−3i−1)−(n−3i−2)2(n−1j)
The maximum is reached for i=⌊n+14⌋, which proves the theorem. □
In a recent article M. Bose and R. Mukerjee [5] show how to use group divisible designs and balanced incomplete block designs to construct 3-out-of-n visual cryptography schemes with optimal contrast and small pixel expansion.
8.6 Asymptotic Optimal k-out-of-n Schemes
In the previous sections we solved the problem of contrast optimal visual cryptography schemes exactly. The result for general k-out-of-n is a little bit weaker; we have only a tight bound for the optimal contrast.
We start with the linear program
Maximize:
α=n−k∑i=0(n−ki)x(W)i−n−k∑i=0(n−ki)x(B)i
Subject to:
n∑i=0(ni)x(W)i−n∑i=0(ni)x(B)i
and
n−j∑i=0(n−ji)x(W)i=n−j∑i=0(n−ji)x(B)i
for j = 0, …, k − 1. The sign conditions are x(W)i≥0, x(B)i≥0.
For the following it is convenient to use the variable transform ˆx(W)i=(ni) x(W)i and ˆx(B)i=(ni)x(B)i. The linear program takes the form
Maximize α=c′(ˆx(W)−ˆx(B)) subject to
n∑i=0ˆx(W)i=n∑i=0ˆx(B)i=1
and
A(ˆx(W)−ˆx(B))=0
where A is the k × (n +1) matrix with entries A = (aj,i)
aj,i=(n−ji)(ni)−1=qj(i)
Note that the j-th row of A is the evaluation of a polynomial qj of degree j at the positions i = 0, …, n. Similarly the vector c is the evaluation of k-th degree polynomial p(i)=(n−ki)(ni)−1 at the places i = 0, …, n.
Now dualize the linear program. For each constraint we get a variable in the dual program and since all constraints of the primal program are equalities the variables in the dual program have no sign restriction. Each variable of the primal program gives a constraint in the dual program and since all variables have a sign condition we get inequalities as constraints in the dual program. The dual program is
Minimize s +t subject to
A′u+(s,…,s)≥c(8.19)
A′u+(t,…,t)≥c⇔A′−(t,…,t)≤c(8.20)
Equations (8.19) and (8.20) just state that
s≥maxi=0,…,n(ci−A′iu)t≥maxi=0,…,n(A′iu−ci).
In the optimal solution these inequalities must be equalities, i.e.,
s=maxi=0,…,n(ci−A′iu)(8.21)
t=maxi=0,…,n(A′iu−ci).(8.22)
Now we translate these equations into the language of polynomials. Remember that cj = p(i) for a k-th degree polynomial and that the j-th row of A is the evaluation of a j-th degree polynomial qj. The polynomials qj (j = 0,…, k − 1) form a basis of the vector space Pk−1 of all polynomials of a degree up to k − 1.
So we may write the dual problem as:
Determine
α=minq∈Pk−1(mini=0,…,n(p(i)−q(i))+maxi=0,…,n(q(i)−p(i))).(8.23)
By adding the right constant to q, we can choose maxi=0,…,n(p(i) − q(i)) = maxi=0,…,n(q(i) − p(i)), which simplifies (8.23) to
α=minq∈Pk−1maxi=0,…,n|p(i)−q(i)|.(8.24)
The low terms of p lie in Pk−1, so the problem is just to approximate the term of degree k. Since
p(i)=(n−ki)(ni)−1 =(n−i)!(n−i−k)!(n−k)n! =(n−i)(n−1−i)⋯(n−(k−1)−i)n(n−1)⋯(n−(k−1)) =(1−in)(1−in−1)⋯(1−in−(k−1))
the highest degree term of p(i) is ( − 1)k/nkik where nk = n(n−1) ⋯ (n−k+1).
This simplifies (8.24) to
α=minq∈Pk−1maxi=0,…,n|xknk¯−q(i)|.(8.25)
Equation 8.25 is almost identical to the following classical problem in approximation theory:
minq∈Pk−1maxx∈[−1,1]|xk−q(x)|(8.26)
The only difference is that the approximation points in our problem are discrete.
A well-known result from approximation theory states:
Result 15 (see for example Theorem 5.7 of [18]) Of all monic polynomials of degree k the best approximation to 0 in [−1, 1] with the ‖ ‖∞-norm is 21−kTk, where Tk(x) = cos(k arccos x) denotes the Chebychev polynomial of the first kind.
Hence, the solution of (8.26) is
q(x)=xk−21−kTk(x).
The minimum in (8.26) is 2k−1. Transforming it back to (8.25) we get an upper bound for a (only an upper bound since we switch from continuous evaluation points to discrete points.)
Thus, we have the contrast αn,k of a k-out-of-n visual cryptography scheme is bounded by:
αn,k≤41−knknk¯
Asymptotically continuous evaluation points and discrete evaluation points are the same, thus we have also
limn→∞αn,k≤limn→∞41−knknk¯=41−k.
Obtaining a lower bound for αn,k need a bit extra work. We just cite without proof.
Result 16 (see [14]) The contrast αn,k of a contrast optimal k-out-of-n visual secret sharing scheme satisfies
4k−1≤αn,k≤4k−1nknk¯.
8.7 Contrast Trade-Offs for Extended Visual Cryptography Schemes
In this section we look at a visual cryptography scheme with extended capacity. In [16] Naor and Shamir show that it is possible to create two transparencies such that each transparency shows an image and the stack of the two transparencies reveals another image. The three images must not satisfy any relation.
In general, we have n slides and a subset S of P({1,…,n}){∅}. For an S-extended visual cryptography scheme we require that for every S∈S the stack of the transparencies i ∈ S reveals an image IS. Furthermore, we require that there is no other way to get information about the image IS.
As in the case of the simple visual cryptography schemes we formalize these ideas by describing the encoding algorithm by a multiset of Boolean matrices. This leads to Definition 4.
Definition 4 Let S⊆P({1,…,n}){∅}.
An S-extended visual cryptography scheme is described by multisets MT of n × m Boolean matrices for T⊆S. (For given T each Boolean matrix in MT describes the colors of the subpixels on each transparency, where the corresponding pixel in image It is black if and only if T∈T. For encoding, each matrix in MT is chosen with the same probability.)
The multisets MT must satisfy the following conditions:
1. Let B∈MT. For {i1,…,iq}∈S the Hamming weight of the OR of the rows i1,…, iq of B is h{i1, …, iq} if {i1,…,iq}∈T and l{i1, …, iq} otherwise, i.e.,
wHam((bi1,1,…,bi1,m)OR … OR(biq,1…,biq,m)) ={h{i1,…,iq}if{i1,…,iq}∈ℐl{i1,…,iq}if{i1,…,iq}∉ℐ
(This means stacking the transparencies i1,…,iq together we recover the image I{i1, …, iq}.)
2. For {i1,…,iq} ⊆ {1,…,n} and T, T′⊆S with T∩P({i1,…,iq})=T′∩P({i1,…,iq}) we obtain the same multisets if we restrict the matrices in MT and MT′, respectively, to the rowsi1,…,iq.
(This condition guarantees the security of the different images.)
If S=P({1,…,n}){∅} we simply call this an extended visual cryptography scheme.
S-extended schemes exists as the following theorem shows.
Theorem 17 (see [9]) An S-extended schemes with pixel expansion
m=∑S∈G2|S|−1
and contrast α = 1/m exists
Proof
The S-extended scheme is built from several k-out-of-k schemes. For each S∈S we reserve 2|s| −1 subpixels. On slides with number i ∉ S these subpixels are colored black. For the slides i ∈ S these 2|S| −1 subpixels are used to construct an |S|-out-of-|S| visual cryptography scheme to encode the image IS (see Theorem 4 for the construction).
To illustrate the construction let S={{1,2},{1,3}} then m = 4. The first two pixels are used to encode the image I{1,2} and the next two subpixels are for the image I{1,2}.
A typical matrix of Mø is
M∅=(101110101110)
and a typical matrix of M{{1,2}} is
M∅=(101101101110).
In the upper right corner you see the 2-out-of-2 scheme for the image I{1,2}.
We claim that this construction yields an S-extended scheme.
Let T ⊆ {1,…, n}, what happens if we stack the transparencies i ∈ T?
In the 2|T|−1 subpixels associated with the image IT we have |T|-out-of-|T| scheme and hence either all 2|T|−1 subpixels in the stack are black or only 2|T| −1 −1 subpixels are black depending on the color in the image IT.
For S ≠ T and T ⊈ S we find an i ∈ T with i ∉ S. On transparency i all 2|S| −1 subpixels associated with IS are black. Hence, in the stack of the transparencies i ∈ T these 2 |S| −1 subpixels are always black and do not contribute to the encoded color.
For S ≠ T and T ⊆ S we have a |S|-out-of-|S| scheme for the image IS. By the security requirement stacking only the transparencies i ∈ T the number of black subpixels must be independent of the color of image IS. (There will be exactly 2|S| −1 − 2|S| −|T| −1 black subpixels associated with the image IS.)
As we can see, only the 2|T| −1 subpixels associated with the image IT contribute to the image that we see when stacking the transparencies i ∈ T. Hence, the stack of the transparencies i ∈ T reveals image IT.
Since the scheme is built from several standard k-out-of-k schemes, it inherits the security from the standard visual cryptography scheme. □
Similar to Lemma 1 we can restrict ourselves to the case that MT is the multiset that consists of all column permutations of a matrix MT.
For S ⊆ {1,…, n} we denote by xTs the number of columns of MT that have a 1 in the rows i ∈ S and a zero in the rows i ∉ S. The number of black subpixels in the image IS is either hS (when a black pixel is encoded) or lS when a white pixel is encoded. Analog to the linear program for ordinary visual cryptography we get
Mxℐ=rℐ(8.27)
where rT=(rTS)∅≠S⊆{1,…,n} with xTS=hS if S∈T and rTS=lS if S∉T.
The (2n − 1) × (2n − 1) matrix M = (mS,T)ø≠S,T ⊆{1,…,n} is defined by mS,T= 1 if S ∩ T ≠ ø and mS,T= 1 otherwise.
It possible to solve the program explicitly and the starting point is the observation that M has an simple inverse.
Lemma 18 The matrix M = (mS,T)ø≠S,T ⊆{1,…,n} with mS,T = 1 if S ∩ T ≠ ø and mS,T = 0 otherwise is invertible and M−1 has only the entries ±1 and 0 .
Proof
We prove this by induction on the number n of transparencies.
Sort the variables xT by the following order: First, we enumerate all subsets that do not contain n. The next subset is the set {n}. Then, the other subsets containing n follow.
Writing M1 = (1), we obtain the following recursion formula that follows directly from the definition:
Mn+1=(Mn0n,1Mn01,n111,nMn1n,11n,n).
Here the index denotes the number of transparencies. 0i,j or 1i,j, respectively, denoting a (2i − 1) × (2j − 1) matrix with all entries 0 or 1, respectively.
With M−11=(1) we obtain the following recursion formula for M−1n:
M−1n+1=(0n,n−M−1n1n,1M−1n−11,nM−1n011,nM−1nM−1nM−1n1n,1−M−1n).
Thus, M is invertible, i.e., Equation (8.27) has a unique solution.
We notice that the components of M−1n1n,1 are only −1, 0, and 1 and that 11,nM−1n1n,1=1. Then the formula can be proved by induction.
Thus, M−1n contains only the entries −1, 0, and 1 and therefore the solution of equation (8.27) is integral. □
By Lemma 18 the solution xT of equation (8.27) is an integer vector if the right-hand side rT is an integer vector.
We can explicitly solve equation (8.27) by multiplying with M−1 and get:
xℐS=∑{1,…n}S⊆T⊆{1,…n}(−1)|T|+|S|+n+1rℐT(8.28)
To verify equation (8.28) we can plug in the values of xTS in equation (8.27). The calculation is elementary and uses only the identity
n∑i=0(−1)i(ni)={1for n=00for n>0.
In a solution of an extended visual cryptography scheme every xTS must be nonnegative. This leads to
∑S⊆T⊆{1,…n}(−1)|S|+|T|rℐT≤0(8.29)
for all possible subsets T of P({1,…,n}){∅}.
In left-hand side of inequality (8.29) we have the sum over rT for |S| + |T| even and over −rT for |S| + |T| odd. This becomes maximal if all rT with |S| + |T| even are as large as possible (i.e., equal hT) and all rt with |S| + |T| odd are as small as possible (i.e., equal lT).
Thus, an extended visual cryptography scheme exists if and only if
∑S⊆T⊆{1,…n}|S|≡|T| mod2hT≤∑S⊆T⊆{1,…,n}|S|≠|T| mod2lT(8.30)
holds for each S ⊊ {1,…, n}.
The linear program given by equation (8.30) is very simple and can be solved directly.
Theorem 19 ([13] Theorem 3.4) An extended visual cryptography scheme with n transparencies needs at least 12(3n−1) subpixels. Hence, the construction of Theorem 17 is optimal with respect to the pixel expansion, i.e.,
M(p({1,…,n}){∅})=12(3n−1).
Proof
For each ø ≠ T ⊆ {1,…, n}, let δT = hT − lT. Our goal is to prove that equation (8.30) implies
m≥h{1,…n}≥∑∅≠T⊆{1,…,n}δT2|T|−1.(8.31)
As the first step in this proof we show that, for given values δT (for ø ≠ T ⊆ {1,…,n}), the number h{1,…,n} is minimal if for all S ⊊ {1,…,n} inequality (8.30) is satisfied with equality.
To this end, suppose
∑hT<∑lTS⊆T⊆{1,…,n}S⊆T⊆{1,…,n}|S|≡|T| mod 2|S|≡|T| mod 2
for some S ⊊ {1,…,n}. But the contrast levels
ˉhT={hTfor T⊆ShT−1othrrwise
and
ˉlT={lTfor T⊆SlT−1othrrwise
satisfy (8.30), since
|{T|S⊆T⊆{1,…,n};|T|≡|S| mod 2}| |{T|S⊆T⊆{1,…,n};|T|≡|S| mod 2}|.
This proves that if inequality (8.30) is not satisfied with equality we can find smaller values for the parameters lT and hT, which also satisfy (8.30). Thus, in an optimal scheme (i.e., a scheme with the smallest possible values for lT and hT) inequality (8.30) is satisfied with equality for each T ⊊ {1,…, n}.
Next we claim that
ht=∑∅≠T′⊆{1,…,n}δT′2|T′|−1−∑T⊆T′⊆{1,…,n}δT′2|T′|−1−|T|(8.32)
for ø ≠ S ⊆ {1,…, n} satisfy (8.30) with equality.
To prove this we have to show that
∑S⊆T⊆{1,…,n}|S|≡|T| mod 2[∑∅≠T′⊆{1,…,n}δT′2|T′|−1_∑T⊆T′⊆{1,…,n}δT′2|T′|−1−1|T|]= ∑S⊆T⊆{1,…,n}|S|≡|T| mod 2([∑∅≠T′⊆{1,…,n}δT′2|T′|−1_∑T⊆T′⊆{1,…,n}δT′2|T′|−1−1|T|]−δT)
or equivalently
∑∅≠T′⊆{1,…,n}δT′[∑S⊆T⊆{1,…,n}|S|≡|T| mod 22|T′|−1_∑S⊆T⊆T'|S|≡|T| mod 22|T′|−1−|T|]=∑∅≠T′⊆{1,…,n}δT′[∑S⊆T⊆{1,…,n}|S|≡|T| mod 22|T′|−1_∑S⊆T⊆T'|S|≡|T| mod 22|T′|−1−|T|]+δT′(−1)|T'|+|S|_12.
(Note that the last summand is equal to −δT, for |T’| ≢ |S| mod 2 and equal to 0 otherwise.)
Comparing coefficients for each (δT, we obtain
2n−|S|−1⋅2|T′|−1−∑S⊆T⊆T′|S|≡|T|mod22|T′|−1−|T|= 2n−|S|−1⋅2|T′|−1(∑S⊆T⊆T′|S|≠|T|mod22|T′|−1−|T|)+(−1)|T′|+|S|−12,(8.33)
but this is true since
(−1)|T′|−|S|=(1−2)|T′|−|S| =|T′|−|S|∑i=0(|T′|−|S|i)(−2)i =|T′|−|S|∑i=0i even(|T′|−|S|i)2i−|T′|−|S|∑i=0i odd(|T′|−|S|i)2i =∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−|S|_∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−|S| ,since(|T′|−|S|i)=∑S⊆T⊆T′|T′|−|S|=i1.
Thus,
∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−|T|=(∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−|T|)+(−1)|T′|−|S|
and therefore,
(∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−|T|)+1=(∑S⊆t3T⊆T′|T′|≡|T| mod 22|T′|−|T|)+(−1)|T′|+|S|.
(Note that (−1)|T′| − |S| = (−1)|T′|+|S|.) Division by 2 gives
(∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−1−|T|)=(∑S⊆T⊆T′|T′|≡|T| mod 22|T′|−1−|T|)+(−1)|T′|+|S|−12
as required for equation (8.33).
Suppose that ˉhT(for ∅≠T⊆{1,…,n}) satisfy (8.30) with equality, too.
If inequality (8.30) is satisfied with equality for all subsets S, we can solve these equations recursively and get
hS=h{1,…,n}+FS(δT|T⊆{1,…,n}),
for some function FS Since inequality (8.30) is satisfied with equality for the contrast values hT and h′T this yields
ˉhS=hS+ˉh{1,…,n}−h{1,…,n}.
But for S = ø inequality (8.30) yields ˉh{1,…,n}=h{1,…,n} and therefore ˉhT=hT for all ∅≠T⊆{1,…,n}.
This proves that (8.32) is the only solution of (8.30) that satisfies all inequalities with equality.
Thus, we find
m≥h{1,…,n}≥∑∅≠T′⊆{1,…,n}δT′2|T′|−1≥∑∅≠T′⊆{1,…,n}2|T′|−1=12(3n−1)
what proves the theorem. □
Without proof we mention the following result about the contrast of the different images.
Result 20 ([13] Theorem 3.6) For ø ≠ T ⊆ {1,…,n} let αT=hT−lTm be the contrast of the image It. The contrast levels of the images satisfy
∑∅≠T⊆{1,…,n}2|T|−1αT≤1.(8.34)
Further, let α′T ≥ 0 (for ø ≠ T ⊆ {1,…,n}) satisfy (8.34). Then for every ɛ > 0 there exists a generalized visual cryptography scheme with contrast levels αT (for ø ≠ T ⊆ {1,…,n}) where |αT − α′T| < ɛ for all nonempty subsets T of {1,…,n}.
The situation becomes more complicated if we no longer require that all combinations of transparencies reveal an image. The only case that is completely solved is Result 21.
Result 21 ([13] Theorem 4.4) Let S=O({1,…,n}){∅,{1,…,n}} then the minimal pixel expansion m is given by
m={12(3n−1)−2n−1−1 for n euen12(3n−1)−2n−1 for n odd.
8.8 Enhancing the Contrast by Nonstandard Models
All results in this chapter worked with the original model of visual cryptography as defined in [16]. In several papers extended models were discussed. Without going into details we mention:
In [19] the authors run an edge-detecting algorithm on the original image and use a higher number of subpixels on the edges for improved contrast.
Several authors studied colored visual cryptography (see [6, 17, 20, 7] and Chapter 7 of [11]). One can use additive and subtractive color mixing in combination to obtain good results. A possible variation of the classical 2-out-of-2 scheme replace the white and black subpixels by any two opposing colors.
It was also suggested to use polarization filters of different orientations to encrypt an image.
A interesting variation is the segment based visual cryptography [4]. For a 7-segment display an image may be encoded as:
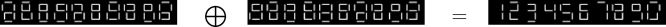
In [10] the authors note that the contrast definition α=h−lm of Naor and Shamir do not always fit the human intuition. They suggest variations like h−lh+l and show how to optimize visual cryptography schemes with respect to the new goal.
8.9 Conclusion
We constructed contrast optimal visual cryptography schemes for various access structures. The constructions exhibit links to different fields like linear programming, approximation theory, the theory of error correcting codes, design theory, and elementary combinatorics.
Bibliography
[1] T. Beth, D. Jungnickel, and H. Lenz. Design Theory. Cambridge University Press, 1985.
[2] C. Blundo, P. D’Arco, A. De Santis, and D. R. Stinson. Contrast optimal threshold visual cryptography schemes. SIAM J. Discrete Math., 16(2):224–261 (electronic), 2003.
[3] C. Blundo, A. De Santis, and D. R. Stinson. On the contrast in visual cryptography schemes. J. Cryptology, 12((4):261–289, 1999.
[4] B. Borchert. Segment-based visual cryptography. Technical report, 17 Wilhelm-Schickard-Institut für Informatik, Univeristät Tübingen, 2007. http://w210.ub.uni-tuebingen.de/volltexte/2007/3048/.
[5] M. Bose and R. Mukerjee. Optimal (n, k) visual cryptography schemes for general k. Des. Codes Cryptogr., 55:19–35, 2010.
[6] S. Cimato, R. De Prisco, and A. De Santis. Optimal colored threshold visual cryptography schemes. Des. Codes Cryptogr., 35((3):311–335, 2005.
[7] S. Cimato, R. De Prisco, and A. De Santis. Colored visual cryptography without color darkening. Theoret. Comput. Sci., 374(1-3):261–276, 2007.
[8] R. Craigen. Hadamard matrices and designs. In C. J. Colbourn and J. H. Dinitz, editors, The CRC Handbook of Combinatorial Designs, pages 370–380. CRC Press, Boco Raton, New York, London, Tokyo, 1996.
[9] S. Droste. New results in visual cryptography. In Advances in cryptology – CRYPTO ’96, volume 1109 of Lect. Notes Comput. Sci., pages 401–415. Springer, Berlin, 1996.
[10] P. A. Eisen and D. R. Stinson. Threshold visual cryptography schemes with specified whiteness levels of reconstructed pixels. Des. Codes Cryptogr., 25((1):15–61, 2002.
[11] A. Klein. Visuelle Kryptographie. Springer-Verlag, Berlin, 2007.
[12] A. Klein and K. Metsch. On approximate inclusion-exclusion. Innov. Incidence Geom., 67:249–270, 2007/2008.
[13] A. Klein and M. Wessler. Extended visual cryptography schemes. Information and Computation, 205((5):716–732, 2007.
[14] M. Krause and H. U. Simon. Determining the optimal contrast for secret sharing schemes in visual cryptography. Combin. Probab. Comput., 12((3):285–299, 2003. Combinatorics, probability and computing (Oberwolfach, 2001).
[15] N. Linial and N. Nisan. Approximate inclusion-exclusion. Combinatorica, 10((4):349–365, 1990.
[16] M. Naor and A. Shamir. Visual cryptography. In Alfredo De Santis, editor, Advances in cryptology - EUROCRYPT '’94, volume 950 of Lect. Notes Comput. Sci., pages 1–12. Springer-Verlag, 1995.
[17] E. R. Verheul and H. C. A. van Tilborg. Constructions and properties of k out of n visual secret sharing schemes. Des. Codes Cryptogr., 11((2):179–196, 1997.
[18] G. A. Watson. Approximation Theory and Numerical Methods. John Wiley & Sons, 1980.
[19] C.N. Yang and T.S. Chen. Visual secret sharing scheme: Improving the contrast of a recovered image via different pixel expansions. In A. Campilho and M. Kamel, editors, ICIAR 2006, volume 4141 of LNCS, pages 468–479, Berlin Heidelberg, 2006. Springer-Verlag.
[20] C.N. Yang and C.S. Laih. New colored visual secret sharing schemes. Des. Codes Cryptogr., 20((3):325–336, 2000.
