CHAPTER 9
Domain Name System, WINS, and DNSSEC
IN THIS CHAPTER
![]() Getting Started with DNS on Windows Server 2016
Getting Started with DNS on Windows Server 2016
![]() Understanding the Evolution of Microsoft DNS
Understanding the Evolution of Microsoft DNS
![]() DNS in an Active Directory Domain Services Environment
DNS in an Active Directory Domain Services Environment
![]() Reviewing the Windows Internet Naming Service
Reviewing the Windows Internet Naming Service
![]() Installing and Configuring WINS
Installing and Configuring WINS
![]() Planning, Migrating, and Maintaining WINS
Planning, Migrating, and Maintaining WINS
Name resolution is a key component in any network operating system (NOS) implementation. The capability of any one resource to locate other resources is the centerpiece of a functional network. Consequently, the name-resolution strategy chosen for a particular NOS must be robust and reliable, and it ideally will conform to industry standards.
Windows Server 2016 utilizes the domain name system (DNS) as its primary method of name resolution, and DNS is a vital component of any Active Directory implementation. Windows Server 2016’s DNS implementation was designed to be compliant with the key Request for Comments (RFCs) that define the nature of how DNS should function. This makes it particularly beneficial for existing network implementations because it allows Windows Server 2016 to interoperate with other types of RFC-compliant DNS implementations.
DNS in Windows Server 2016 remains mostly unchanged. A couple of new features are listed as follows:
![]() You can configure setup a DNS server to responds to certain DNS queries. For example, you can specify DNS responses to be based on client IP address (location), time of the day, and various other parameters.
You can configure setup a DNS server to responds to certain DNS queries. For example, you can specify DNS responses to be based on client IP address (location), time of the day, and various other parameters.
![]() DNS has been hardened against malicious attacks. These include a new feature called Response Rate Limiting (RRL) prevents possibility of malicious systems using your DNS servers to initiate a denial of service attack on a DNS client.
DNS has been hardened against malicious attacks. These include a new feature called Response Rate Limiting (RRL) prevents possibility of malicious systems using your DNS servers to initiate a denial of service attack on a DNS client.
![]() You also now have DNS-based Authentication of Named Entities (DANE), which you will use with TLSA (Transport Layer Security Authentication) records to advise clients what CA they should expect will be delivering the certificate for your domain name. This prevents man-in-the-middle attacks where a hacker hijacks the DNS cache and points the client to a server that will issue a certificate the hacker has control over.
You also now have DNS-based Authentication of Named Entities (DANE), which you will use with TLSA (Transport Layer Security Authentication) records to advise clients what CA they should expect will be delivering the certificate for your domain name. This prevents man-in-the-middle attacks where a hacker hijacks the DNS cache and points the client to a server that will issue a certificate the hacker has control over.
![]() You can now add records that are not specifically supported by the Windows DNS server. These records are specified as “unknown” record functionality.
You can now add records that are not specifically supported by the Windows DNS server. These records are specified as “unknown” record functionality.
![]() IPv6 root hints are finally here, letting you use native IPV6 root hints support to perform Internet name resolution against IPV6 root servers.
IPv6 root hints are finally here, letting you use native IPV6 root hints support to perform Internet name resolution against IPV6 root servers.
![]() There are also a number of new PowerShell commandlets that are available for DNS Server.
There are also a number of new PowerShell commandlets that are available for DNS Server.
IPv6 is rapidly gaining traction in the IT world and is an integral feature of the Windows Server 2016 operating system. Windows Server 2016 supports IPv4 fully in roles such as DNS, Dynamic Host Configuration Protocol (DHCP), and Internet Information Services (IIS). Windows Server 2016 even includes additional features such as the GlobalNames zone (GNZ) to support single-label names with IPv6.
The second type of name resolution, mapping legacy Microsoft NetBIOS names into IP addresses, is provided by Windows Internet Naming Service (WINS). Although it is technically possible (and ideal) to create a Windows Server 2016 environment free of NetBIOS name resolution, the truth is that divorcing a network from WINS dependency is very difficult, so it will likely remain an active part of network services in most organizations, at least for many more years. You can find more information about WINS in the “Reviewing the Windows Internet Naming Service” section later in this chapter.
NOTE
When Windows Server 2008 DNS service was released, it introduced a new feature known as the GNZ. The GNZ provided single-label name resolution for large enterprise networks that do not deploy WINS and for which using DNS name suffixes to provide single-label name resolution was not practical. Windows 2016 supports the GNZ.
Windows Server 2016 includes both enhanced DNS Security Extensions (DNSSEC) and enhanced PowerShell support. Introduced to the platform in Windows 2008, DNSSEC in Windows 2016 includes online signing and automated key management to allow signing of Active Directory integrated zones and easier management. PowerShell offers you feature parity with the traditional DNSCMD.EXE tool, allowing administrators to switch to PowerShell for all DNS administration and automation.
This chapter details the key components of DNS in general and provides an overview of Windows Server 2016’s implementation of DNS. A particular emphasis is placed on the role of DNS in Active Directory Domain Services (AD DS) and the way it fits in standard and nonstandard configurations. Step-by-step instructions outline how to install and configure specific DNS components on Windows Server 2016. In addition, troubleshooting DNS issues and specific Active Directory design scenarios help to give a hands-on approach to your understanding of DNS.
The Need for DNS
Computers and humans conceptualize in drastically different ways. In terms of understanding locations, humans are much better at grasping the concept of names rather than numbers. For example, most people think of cities by their names, not by their ZIP codes. Computers, however, work in binary, and subsequently prefer to work with numbers. For example, computers at the post office translate the city and address names into specific ZIP codes for that region, helping each letter reach its destination.
Name resolution for computer systems works in a similar way. A user-friendly name is translated into a computer-identifiable number. TCP/IP uses a number scheme that uniquely identifies each computer interface on a network by a series of numbers, such as 10.1.2.145, known as an IP address. Because most humans are not interested in memorizing several of these types of numbers, they must be easily resolvable into user-friendly names such as www.microsoft.com.
DNS, in its simplest form, provides for name resolution in a distributed fashion, with each server or set of servers controlling a specified zone and with entries for each resource called resource records (RRs) that indicate the location of a particular object.
A good analogy for DNS can be found in telephone books. Each city or metropolitan area (namespace) publishes a separate phone book (zone) that contains many listings (resource records) that map people’s names to their phone numbers (IP addresses). This simple example illustrates the basic principle behind DNS. When you understand these basics, further drilling down into the specifics, especially with regard to Windows Server 2016’s DNS, is possible.
History of DNS
The Internet, as originally implemented, utilized a simple text file called a HOSTS file that contained a simple list of all servers on the Internet and their corresponding IP addresses. This file was copied manually from the master server to multiple secondary HOSTS servers. As more and more servers were added to the Internet, however, updating this file became unmanageable, and a new system became necessary.
In 1983, in direct response to this problem, the RFCs for the DNS were drawn up, and this form of name resolution was implemented on a large scale across the Internet. Instead of a small number of static HOSTS files, DNS servers formed a hierarchical method of name resolution, in which servers resolved only a certain segment of hosts on the Internet and delegated requests that it did not manage. This allowed the number of records held in DNS to scale enormously, without a subsequently large performance decrease.
Microsoft developed its own implementation of DNS in Windows NT 4.0, which was based on the RFC standards on which DNS was founded. With the introduction of Windows 2000, Microsoft adopted DNS as the principle name-resolution strategy for Microsoft products. Older, legacy name-resolution systems such as WINS are slowly being phased out. Since that time, the DNS implementation used by Microsoft has evolved to include a number of key benefits that distinguish it from standard DNS implementations (for example, UNIX BIND). To understand these improvements, however, you first need a basic understanding of DNS functionality.
Establishing a Framework for DNS
DNS structure is closely tied to the structure of the Internet and often is confused with the Internet itself. The structure of DNS is highly useful, and the fact that it has thrived for so long is a tribute to its functionality. A closer examination of what constitutes DNS and how it is logically structured is important in understanding the bigger picture of how DNS fits into Windows Server 2016.
Explaining the DNS Hierarchy
DNS uses a hierarchical approach to name resolution in which resolution is passed up and down a hierarchy of domain names until a particular computer is located. Each level of the hierarchy is divided by dots (.), which symbolize the division. A fully qualified domain name (FQDN), such as server1.sales.companyabc.com, uniquely identifies a resource’s space in the DNS hierarchy. Figure 9.1 shows how the fictional CompanyABC fits into the DNS hierarchy.
The top of the hierarchy is known as the root, and is represented by a single . (dot). Moving down the DNS hierarchy, the next layer in the model is made up of top-level domain (TLD) names, which are .com, .net, .gov, .fr, and similar domain namespaces that loosely define the particular category that a domain namespace fits into. The Internet Assigned Numbers Authority (IANA) oversees the global root zone management and management of the TLDs. The IANA is operated by the Internet Corporation for Assigned Names and Numbers (ICANN). The official list of all generic TLDs maintained by IANA is given in Table 9.1.
TABLE 9.1 List of Generic Top-Level Domain Names
TLD |
Purpose |
.aero |
Air Travel Industry |
.asia |
Asia-Pacific Region |
.biz |
Businesses |
.cat |
Catalan Language |
.com |
Commercial |
.coop |
Cooperatives |
.edu |
Educational Institutions |
.gov |
U.S. Government |
.info |
Informational |
.int |
International Organizations |
.jobs |
Companies (Job Postings) |
.mil |
U.S. Military |
.mobi |
Mobile Devices |
.museum |
Museums |
.name |
Individuals |
.net |
Network |
.org |
Organization |
.pro |
Professions |
.tel |
Internet Communications |
.travel |
Travel and Tourism Industry |
.xxx |
Adult Entertainment |
For example, educational institutions are commonly given .edu extensions, and commercial businesses are given .com extensions. These extensions form the first set of branches to the DNS tree. The .biz, .com, .info, .name, .net, and .org are all open TLDs, meaning any individual or entity can register the domains. Other TLDs have restrictions based on the intended use.
In addition to the generic TLDs, the IANA maintains country-code TLDs. These country codes are the two-letter codes specified in International Organization for Standardization (ISO) 3166 standard. For example, .co is maintained for Colombia and .fr is maintained for France. Interestingly, all the country-code TLDs listed in ISO 3166 are maintained, but some are unused, such as the Saint Martin (.mf). There are also a handful of exceptions, such as the listing for United Kingdom, which is listed in the ISO 3166 standard as .gb, but .uk is used instead.
The second level in the DNS hierarchy commonly contains the business name of an organization, such as companyabc in Figure 9.1. This level is normally the first area in the DNS hierarchy where an organization has control over the records within the domain and where it can be authoritative.
Subdomains can easily be, and often are, created in the DNS hierarchy for various reasons. For example, sales.microsoft.com is a potential domain that could exist as a sublevel of the microsoft.com domain. The DNS hierarchy works in this way, with multiple levels possible.
The DNS Namespace
The bounded area that is defined by the DNS name is known as the DNS namespace. microsoft.com is a namespace, as is marketing.companyabc.com. Namespaces can be either public or private. Public namespaces are published on the Internet and are defined by a set of standards. All the .com, .net, .org, and similar namespaces are external, or public. An internal namespace is not published to the Internet, but is also not restricted by extension name. In other words, an internal, unpublished namespace can occupy any conceivable namespace, such as companyabc.local or companyabc.internal. Internal namespaces are most often used with Active Directory because they give increased security to a namespace. Because such namespaces are not published, they cannot be directly accessed from the Internet.
Getting Started with DNS on Windows Server 2016
To fully understand the capabilities that Windows Server 2016 offers for DNS, the product should be installed in a lab environment. This helps to conceptualize the various components of DNS that are presented in this chapter.
Installing DNS Using the Add Roles Wizard
Although you can install and configure DNS in various ways, the most straightforward and complete process involves invoking the Add Roles Wizard and the subsequent Configure a DNS Server Wizard. The process detailed in this section illustrates the installation of a standard zone. Multiple variations of the installation are possible, but this particular scenario is illustrated to show the basics of DNS installation.
NOTE
It is recommended that DNS servers be configured with static IPv4 addresses because if the IP address changes, clients might be unable to contact the DNS server.
Installation of DNS on Windows Server 2016 is straightforward, and no reboot is necessary. To install and configure the DNS role on a Windows Server 2016 computer, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the Dashboard section and click the Add Roles and Features link.
3. Click Next on the Before You Begin page.
4. Leave the default selection Role-Based or Feature-Based Installation and click Next.
5. Select the server from the server pool to add the DNS role to and click Next.
6. Select the DNS Server Role check box and click Add Features.
NOTE
When the DNS Role box is checked, the Add Roles and Features Wizard does a readiness check to ensure that the target server is ready for the DNS role. For example, if a static IP address is not set for the target server, a warning will pop up.
7. Click Next to skip the Features selection.
8. Click Next on the Introduction to DNS Server page.
9. Click Install on the Confirmation page to install the DNS role.
10. Click Close to exit the Add Roles and Features Wizard.
The DNS role can also be installed locally on a server core installation using PowerShell with the following command:
Install-WindowsFeature–Name DNS-Server-Full-Role
The DNS role has been installed on the Windows Server 2016 server, but has not been configured. To configure the role, complete the following steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select Action, Configure a DNS Server.
6. On the Welcome page for the Configure a DNS Server Wizard, click Next to continue.
7. Select Create Forward and Reverse Lookup Zones (Recommended for Large Networks), and then click Next.
8. Select Yes, Create a Forward Lookup Zone Now (Recommended), and then click Next.
9. Select the type of zone to be created—in this case, choose Primary Zone—and click Next. If the server is a writable domain controller, the Store the Zone in Active Directory check box is available.
10. If storing the zone in Active Directory, select the replication scope and click Next.
11. Type the FQDN of the zone in the Zone Name box, and then click Next.
12. At this point, if creating a non-AD-integrated zone, you can create a new zone text file or import one from an existing zone file. In this case, choose Create a New File with This File Name, and accept the default. Click Next to continue.
13. The subsequent page allows a zone to either accept or decline dynamic updates. For this example, leave dynamic updates disabled by selecting the Do Not Allow Dynamic Updates option button and clicking Next.
NOTE
Dynamic updates allow DNS clients to register and update their own resource records in the DNS zone. When enabling dynamic updates to be accepted by your DNS server, be sure you know the sources of dynamic updated information. If the sources are not reliable, you can potentially receive corrupt or invalid information from a dynamic update.
14. The next page allows for the creation of a reverse lookup zone. Here, select Yes, Create a Reverse Lookup Zone Now, and then click Next.
15. Select Primary Zone for the reverse lookup zone type, and then click Next.
16. If storing the zone in Active Directory, select the replication scope and click Next.
17. Accept the default IPv4 Reverse Lookup Zone, and then click Next.
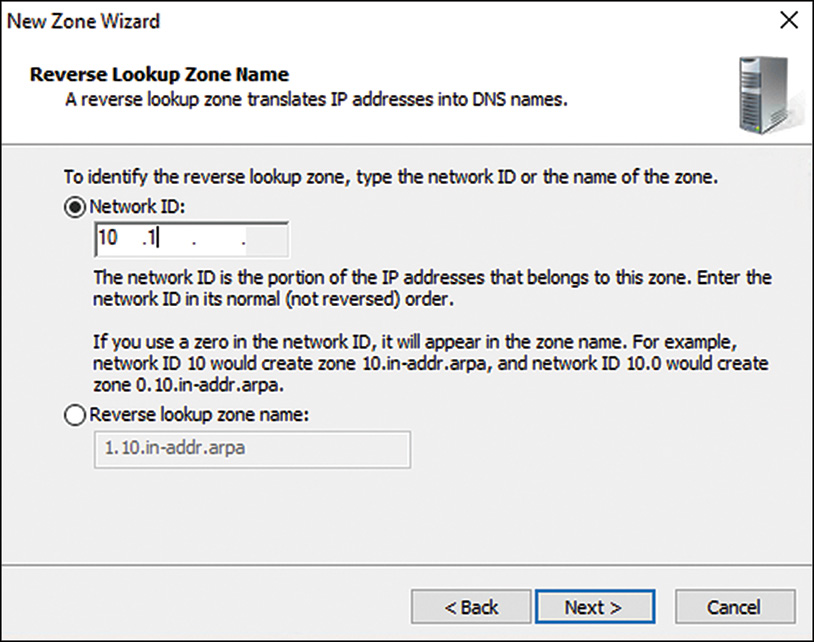
18. Type in the network ID of the reverse lookup zone, and then click Next. (The network ID is usually the first set of octets from an IP address in the zone. If a Class A IP range of 10.1.0.0 with a subnet mask of 255.255.0.0 is in use on a network, you enter the values 10.1, as illustrated in Figure 9.2.)
19. Again, if creating a non-AD-integrated zone, you are offered the option to create a new zone file or to use an existing file. For this example, choose Create a New File with This File Name, and click Next to continue.
20. Again, you are presented the option for dynamic updates. For this example, leave dynamic updates disabled by selecting the Do Not Allow Dynamic Updates option button and clicking Next.
21. The next page deals with the setup of forwarders, which is described in more detail in the “Understanding DNS Zones” section later in this chapter. In this example, choose No, It Should Not Forward Queries, and click Next to continue.
22. The final window displays a summary of the changes that will be made and the zones that will be added to the DNS database. Click Finish to finalize the changes and create the zones.
NOTE
Depending on network connectivity, there might be a pop-up dialog box between the two clicks to finish the DNS changes in step 20. If you are not connected to a local-area network (LAN), an error dialog box is displayed regarding searching for root hints. Although the dialog box notes the root hint error, clicking OK will still configure DNS successfully.
Resource Records
In the DNS hierarchy, objects are identified through the use of resource records (RRs). These records are used for basic lookups of users and resources within the specified domain and are unique for the domain in which they are located. Because DNS is not a flat namespace, however, multiple identical RRs can exist at different levels in a DNS hierarchy. The distributed nature of the DNS hierarchy allows such levels.
Several key resource records exist in most DNS implementations, especially in those associated with Windows Server 2016 AD DS. A general familiarity with these specific types of RRs is required to gain a better understanding of DNS.
Start of Authority (SOA) Records
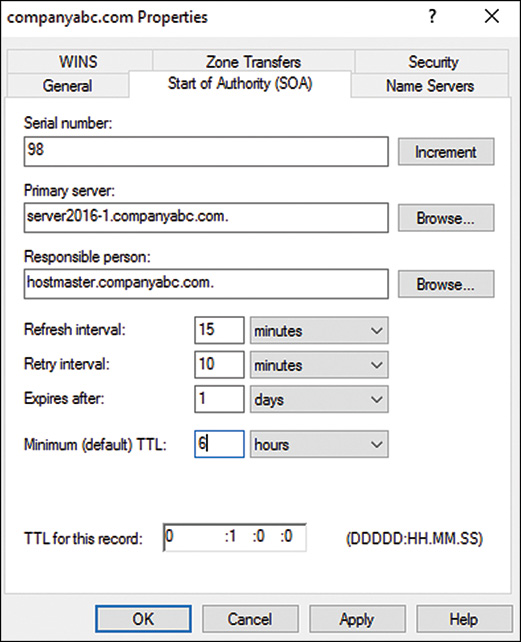
The Start of Authority (SOA) record in a DNS database indicates which server is authoritative for that particular zone. The server referenced by the SOA records is subsequently the server that is assumed to be the authoritative source of information about a particular zone and is in charge of processing zone updates. The SOA record contains information such as the Time-to-Live (TTL) interval, the contact person responsible for DNS, and other critical information, as illustrated in Figure 9.3.
An SOA record is automatically created when DNS is installed for AD DS in Windows Server 2016 and is populated with the default TTL, primary server, and other pertinent information for the zone. After installation, however, these values can be modified to fit the specific needs of an organization.
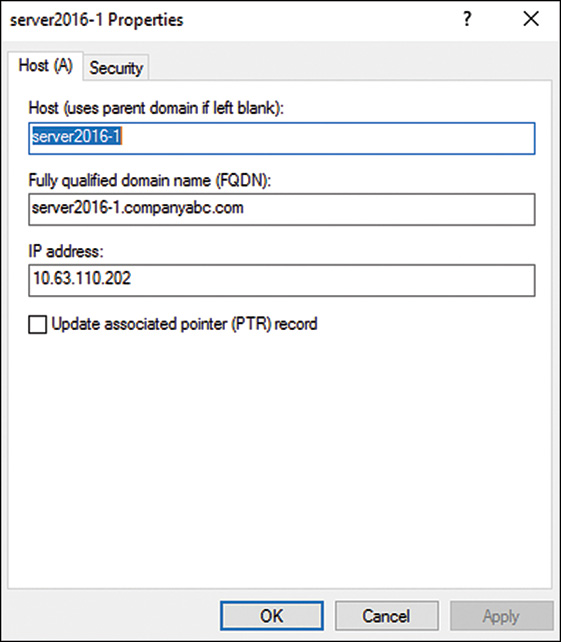
Host (A) Records
The most common type of RR in DNS is the host record, also known as an A record. This type of RR simply contains the name of the host and its corresponding IP address, as illustrated in Figure 9.4.
The vast majority of RRs in DNS are A records because they are used to identify the IP addresses of most resources within a domain.
NOTE
Most resource records also contain advanced information about the record, which includes the TTL and, optionally, the record time stamp. To view or update this information, select Advanced from the View menu of the DNS Management console.
Name Server (NS) Records
Name Server (NS) records identify which computers in a DNS database are the name servers, essentially the DNS servers for a particular zone. Although there can be only one SOA record for a zone, there can be multiple NS records for the zone, which indicate to clients which machines are available to run DNS queries against for that zone.
NOTE
Name Server records, or NS records, do not actually contain the IP information of a particular resource. In fact, in most cases, only A records contain this information. NS records and other similar records simply point to a server’s A record. For example, an NS record will simply point to dc1.companyabc.com, which will then direct the query to the dc1 A record in the companyabc.com zone.
Service (SRV) Records
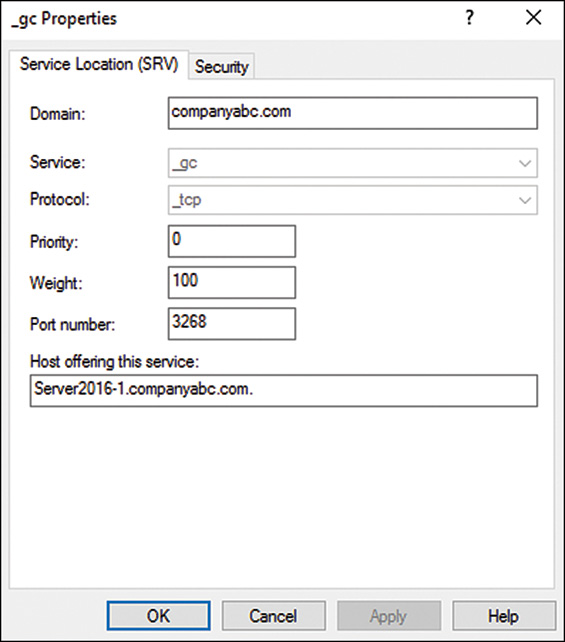
Service (SRV) records are RRs that indicate which resources perform a particular service. Domain controllers in AD DS are referenced by SRV records that define specific services, such as the Global Catalog (GC), Lightweight Directory Access Protocol (LDAP), and Kerberos. SRV records are a relatively new addition to DNS, and did not exist in the original implementation of the standard. Each SRV record contains information about a particular functionality that a resource provides. For example, an LDAP server can add an SRV record, indicating that it can handle LDAP requests for a particular zone. SRV records can be very useful for AD DS because domain controllers can advertise that they handle Global Catalog requests, as illustrated in Figure 9.5.
NOTE
Because SRV records are a relatively new addition to DNS, they are not supported by several down-level DNS implementations, such as UNIX BIND 4.1.x and NT 4.0 DNS. It is, therefore, critical that the DNS environment that is used for Windows Server 2016’s AD DS has the capability to create SRV records. For UNIX BIND servers, version 8.1.2 or later is recommended.
Mail Exchanger (MX) Records
A Mail Exchanger (MX) record indicates which resources are available for Simple Mail Transfer Protocol (SMTP) mail reception. MX records can be set on a domain basis so that mail sent to a particular domain will be forwarded to the server or servers indicated by the MX record. For example, if an MX record is set for the domain companyabc.com, all mail sent to [email protected] will be automatically directed to the server indicated by the MX record.
Pointer (PTR) Records
Reverse queries to DNS are accomplished through the use of Pointer (PTR) records. In other words, if a user wants to look up the name of a resource that is associated with a specific IP address, he would do a reverse lookup using that IP address. A DNS server would reply using a PTR record that would indicate the name associated with that IP address. PTR records are most commonly found in reverse lookup zones.
Canonical Name (CNAME) Records
A Canonical Name (CNAME) record represents a server alias, and allows any one of a number of servers to be referred to by multiple names in DNS. The record essentially redirects queries to the A record for that particular host. CNAME records are useful when migrating servers and for situations in which friendly names, such as mail.companyabc.com, are required to point to more complex server-naming conventions, such as sfoexch01.companyabc.com.
Other DNS Record Types
Other, less-common forms of records that might exist in DNS have specific purposes, and there might be cause to create them. The following is a sample list, but is by no means exhaustive:
![]() AAAA—Maps a standard IP address into a 128-bit IPv6 address. This type of record will become more prevalent as IPv6 is adopted. See Chapter 11, “DHCP, IPv6, IPAM” for more details on IPv6.
AAAA—Maps a standard IP address into a 128-bit IPv6 address. This type of record will become more prevalent as IPv6 is adopted. See Chapter 11, “DHCP, IPv6, IPAM” for more details on IPv6.
![]() ISDN—Maps a specific DNS name to an ISDN telephone number.
ISDN—Maps a specific DNS name to an ISDN telephone number.
![]() KEY—Stores a public key used for encryption for a particular domain.
KEY—Stores a public key used for encryption for a particular domain.
![]() RP—Specifies the person responsible for a domain.
RP—Specifies the person responsible for a domain.
![]() WKS—Designates a particular well-known service.
WKS—Designates a particular well-known service.
![]() MB—Indicates which host contains a specific mailbox.
MB—Indicates which host contains a specific mailbox.
Understanding DNS Zones
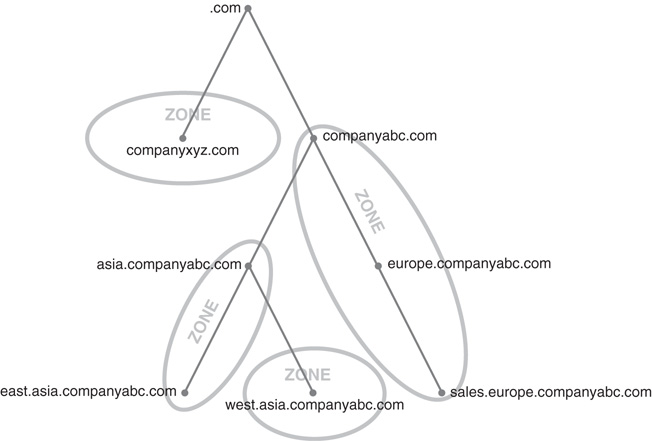
A zone in DNS is a portion of a DNS namespace that is controlled by a particular DNS server or group of servers. The zone is the primary delegation mechanism in DNS and is used to establish boundaries over which a particular server can resolve requests. Any server that hosts a particular zone is said to be authoritative for that zone, with the exception of stub zones, which are defined later in this chapter in the “Stub Zones” section. Figure 9.6 illustrates how different portions of the DNS namespace can be divided into zones, each of which can be hosted on a DNS server or group of servers.
It is important to understand that any section or subsection of DNS can exist within a single zone. For example, an organization might decide to place an entire namespace of a domain, subdomains, and subsubdomains into a single zone. Or specific sections of that namespace can be divided up into separate zones. In fact, the entire Internet namespace can be envisioned as a single namespace with . as the root, which is divided into a multitude of different zones.
NOTE
A server that is installed with DNS but does not have any zones configured is known as a caching-only server. Establishing a caching-only server can be useful in some branch office situations because it can help to alleviate large amounts of client query traffic across the network and eliminate the need to replicate entire DNS zones to remote locations.
Forward Lookup Zones
A forward lookup zone is created to, as the name suggests, forward lookups to the DNS database. In other words, this type of zone resolves names to IP addresses and resource information. For example, if a user wants to reach dc1.companyabc.com and queries for its IP address through a forward lookup zone, DNS returns 172.16.1.11, the IP address for that resource.
NOTE
There is nothing to stop the assignment of multiple RRs to a single resource. In fact, this practice is common and useful in many situations. It might be practical to have a server respond to more than one name in specific circumstances. This type of functionality is normally accomplished through the creation of CNAME records, which create aliases for a particular resource.
Reverse Lookup Zones
A reverse lookup zone performs the exact opposite operation as a forward lookup zone. IP addresses are matched up with a common name in a reverse lookup zone. This is similar to knowing a phone number but not knowing the name associated with it. Reverse lookup zones are usually manually created and do not always exist in every implementation. Creating a new zone using the Configure a DNS Server Wizard, as in the example earlier in this chapter, can automatically create a reverse lookup zone. Reverse lookup zones are primarily populated with PTR records, which serve to point the reverse lookup query to the appropriate name.
Primary Zones
In traditional (non-Active Directory-integrated) DNS, a single server serves as the master DNS server for a zone, and all changes made to that particular zone are done on that particular server. A single DNS server can host multiple zones, and can be primary for one and secondary for another. If a zone is primary, however, all requested changes for that particular zone must be performed on the server that holds the master copy of the zone.
Secondary Zones
A secondary zone is established to provide redundancy and load balancing for the primary zone. Each copy of the DNS database is read-only, however, because all record keeping is done on the primary zone copy. A single DNS server can contain several zones that are primary and several that are secondary. The zone-creation process is similar to the one outlined in the preceding section on primary zones, but with the difference being that the zone is transferred from an existing primary server.
Stub Zones
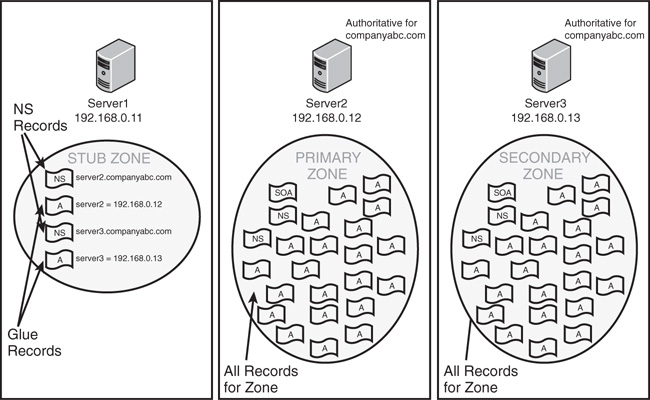
The concept of stub zones is unique to Microsoft DNS. A stub zone is essentially a zone that contains no information about the members in a domain but simply serves to forward queries to a list of designated name servers for different domains. A stub zone subsequently contains only NS, SOA, and glue records. Glue records are essentially A records that work in conjunction with a particular NS record to resolve the IP address of a particular name server. A server that hosts a stub zone for a namespace is not authoritative for that zone.
As shown in Figure 9.7, the stub zone effectively serves as a placeholder for a zone that is authoritative on another server. It allows a server to forward queries that are made to a specific zone to the list of name servers in that zone.
You can easily create a stub zone in Windows Server 2016 after the need has been established for this particular type of functionality. To create a stub zone, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Select Action, New Zone.
7. Click Next on the Welcome page.
8. Select Stub Zone from the list of zone types. Because this zone will not be AD integrated, uncheck the Store the Zone in Active Directory check box if it is checked, and then click Next to continue.
9. Type in the name of the zone that will be created, and click Next to continue.
10. Select Create a New File with This File Name and accept the defaults, unless migrating from an existing zone file. Then click Next to continue.
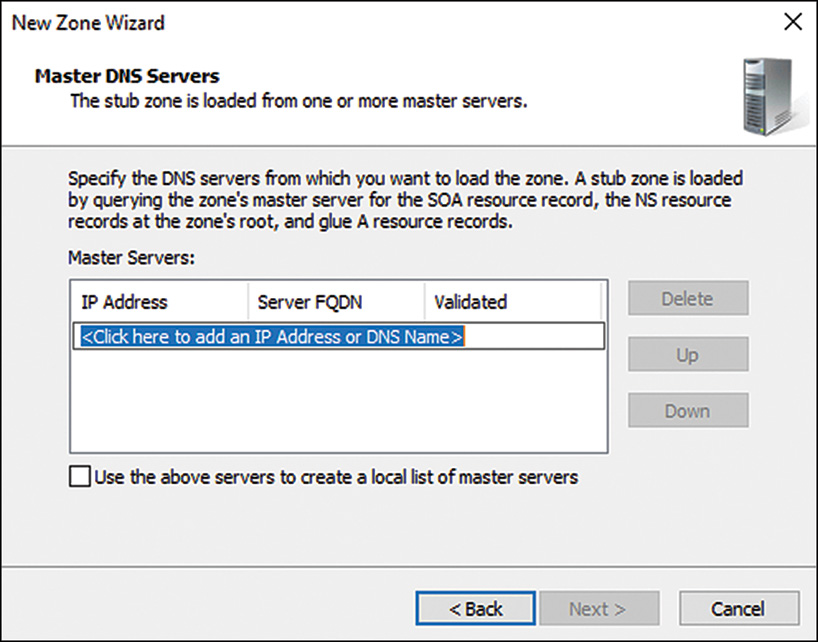
11. Type in the IP address of the server or servers from which the zone records will be copied. Press Enter for each server entered, and they will be validated, as shown in Figure 9.8. Click Next to continue.
12. Click Finish on the Summary page to create the zone.
The newly created stub zone will hold only the SOA, NS, and glue records for the domain at which it is pointed.
Performing Zone Transfers
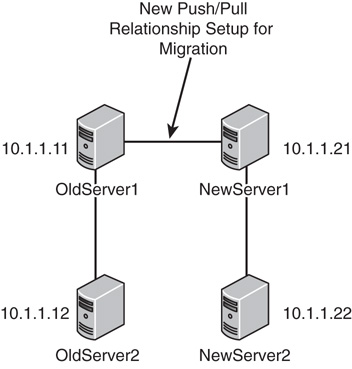
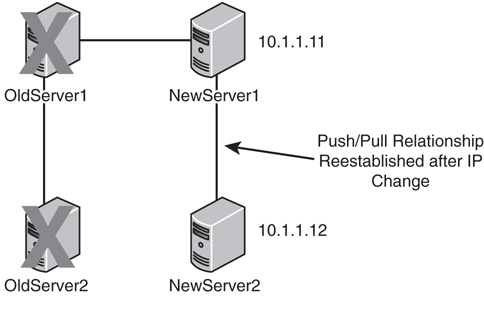
Copying the DNS database from one server to another is accomplished through a process known as a zone transfer. Zone transfers are required for any non-Active Directory-integrated zone that has more than one name server responsible for the contents of that zone. The mechanism for zone transfers varies, however, depending on the version of DNS. Zone transfers are always pulled by the secondary servers from the primary servers.
Primary DNS servers can be configured to notify secondary DNS servers of changes to a zone and to begin a zone transfer. They can also be configured to perform a zone transfer on a scheduled basis. To set up a secondary server to pull zone transfers from a forward lookup zone, follow this procedure:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Right-click the name of the zone and choose Properties.
7. Choose the Zone Transfers tab.
8. Check Allow Zone Transfers and select Only to Servers Listed on the Name Servers Tab. This is normally the default setting.
9. Select the Name Servers tab.
10. Click Add, type in the FQDN of the server that will receive the updates, and click the Resolve button. The server will be validated, as shown in Figure 9.9. Because the server is not yet an authoritative server for the zone, the error message “The server with this IP address is not authoritative for the required zone” appears. This will be done in the next section. The error can be safely ignored. Click OK to save.
11. Click OK to save the changes.
Now that the primary zone on the primary DNS server has been configured to allow transfers, the secondary zone has to be configured on the secondary DNS server. To create the secondary zone and begin zone transfers, complete the following steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Select Action, New Zone.
7. Click Next on the Welcome page.
8. Select Secondary Zone from the list of zone types. Secondary zones cannot be AD-integrated and the options will be grayed out. Click Next to continue.
9. Type in the name of the zone that will be created (this should match the primary zone name), and click Next to continue.
10. Type in the IP address or FQDN of the server or servers from which the zone records will be transferred. Press Enter for each server entered, and they will be validated. Click Next to continue.
If there is an “No IPv6 address was found for the DNS name entered” error, highlight the error and click the Delete button to clear the entry.
11. Click Finish on the Summary page to create the zone.
After the last step, the zone will automatically transfer from the primary DNS server to the secondary DNS server.
Performing Full Zone Transfers
The standard method for zone transfers, which transfers the entire contents of a DNS zone from the primary server to the secondary server, is known as asynchronous zone transfer (AXFR), or full zone transfer. This type of zone transfer copies every item in the DNS database to the secondary server, regardless of whether the server already has some of the items in the database. Older implementations of DNS utilized AXFR exclusively, and it is still utilized for specific purposes today.
Initiating Incremental Zone Transfers
An incremental zone transfer (IXFR) is a process by which all incremental changes to a DNS database are replicated to the secondary DNS server. This saves bandwidth over AXFR replication changes because only the deltas, or changes made to the database since the last zone transfer, are replicated.
IXFR zone transfers are accomplished by referencing a serial number that is stored on the SOA of the DNS server that holds the primary zone. This number is incremented upon each change to a zone. If the server requesting the zone transfer has a serial number of 45, for example, and the primary zone server has a serial number of 55, only those changes made during the period of time between 45 and 55 will be incrementally sent to the requesting server via an IXFR transfer. However, if the difference in index numbers is too great, the information about the requesting server is assumed to be stale, and a full AXFR transfer will be initiated. For example, if a requesting server has an index of 25, and the primary zone server’s index is 55, an AXFR zone transfer will be initiated, as illustrated in Figure 9.10.
Understanding DNS Queries
The primary function of DNS is to provide name resolution for requesting clients, so the query mechanism is subsequently one of the most important elements in the system. Two types of queries are commonly made to a DNS database: recursive and iterative.
Performing Recursive Queries
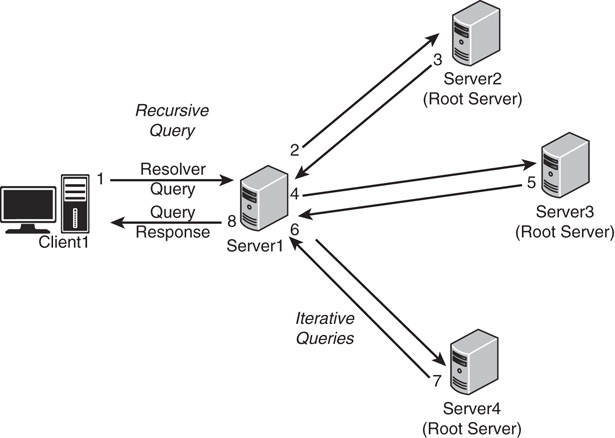
Recursive queries are most often performed by resolvers, or clients, that need a specific name resolved by a DNS server. Recursive queries are also accomplished by a DNS server if forwarders are configured to be used on a particular name server. A recursive query essentially asks whether a particular record can be resolved by a particular name server. The response to a recursive query is either negative or positive. Figure 9.11 shows a common recursive query scenario.
Performing Iterative Queries
Iterative queries ask a DNS server to either resolve the query or make a best-guess referral to a DNS server that might contain more accurate information about where the query can be resolved. Another iterative query is then performed to the referred server and so on until a result, positive or negative, is obtained.
In the example shown in Figure 9.11, Client1 in CompanyABC opens a web browser and attempts to browse to the website for www.microsoft.com. A recursive query is initiated to the default name server; in this case, Server1 is contacted. Because Server1 is authoritative only for the companyabc.com namespace, and no entries exist for microsoft.com, the query is sent to an “upstream” DNS server that is listed in the root hints of the DNS server. That server, Server2, is not authoritative for microsoft.com but sends a referral back to Server1 for Server3, which is a name server for the .com namespace. Server3 knows that Server4 handles name-resolution requests for microsoft.com and sends that information back to Server1. A final iterative query is then sent from Server1 to Server4, and Server4 successfully resolves www to the proper IP address. Server1, with this information in hand, returns Client1’s original recursive query with the proper IP address and Client1’s browser successfully resolves www.microsoft.com.
This type of functionality lies at the heart of the distributed nature of DNS and allows DNS lookups to function as efficiently as they do.
Other DNS Components
Several other key components lie at the heart of DNS and are necessary for it to function properly. In addition, you need to fully understand the functionality of several key components of DNS that are utilized heavily by Microsoft DNS.
Dynamic DNS
Older versions of DNS relied on administrators manually updating all the records within a DNS database. Every time a resource was added or information about a resource was changed, the DNS database was updated manually, normally via a simple text editor, to reflect the changes. Dynamic DNS was developed as a direct response to the increasing administrative overhead that was required to keep DNS databases functional and up-to-date. With Dynamic DNS, clients can automatically update their own records in DNS, depending on the security settings of the zone.
It is important to note that only Windows 2000/XP and higher clients support dynamic updates and that down-level (NT/9x) clients must have DHCP configured properly for them to be updated in DNS. There are, however, security issues associated with this functionality that are detailed in subsequent sections of this chapter and are described further in Chapter 11.
The Time-to-Live Value
The TTL value for a RR is the amount of time (in seconds) that a resolver or name server will keep a cached DNS request before requesting it again from the original name server. This value helps to keep the information in the DNS database relevant. Setting TTL levels is essentially a balancing act between the need for updated information and the need to reduce DNS query traffic across the network.
In the example from the “Performing Iterative Queries” section, if Client1 already requested the IP address of www.microsoft.com, and the information was returned to the DNS server that showed the IP address, it would make sense that that IP address would not change often and could, therefore, be cached for future queries. The next time another client requests the same information, the local DNS server will give that client the IP address it received from the original Client1 query so long as the TTL has not expired. This helps to reduce network traffic and improve DNS query response time.
The TTL for a response is set by the name server that successfully resolves a query. In other words, you might have different TTLs set for items in a cache, based on where they were resolved and the TTL for the particular zone they originated from.
NOTE
The default TTL for manually created records in Windows Server 2016 DNS is one hour. Records created dynamically via Dynamic DNS have a 20-minute default TTL.
The TTL setting for a zone is modified via the SOA record. The procedure for doing this in Windows Server 2016 is as follows:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
7. Find the SOA record for the zone and double-click it.
8. Modify the Minimum (Default) TTL entry to match the TTL you want, as shown in Figure 9.12.
9. Click OK to accept the changes.
Performing Secure Updates
One of the main problems with a Dynamic DNS implementation lies with the security of the update mechanism. If no security is enforced, nothing prevents malicious users from updating a record for a server, for example, to redirect it to another IP address. This is known as DNS poisoning. For this reason, dynamic updates are, by default, turned off on new standard zones that are created in Windows Server 2016. However, with AD-integrated DNS zones, a mechanism exists that allows clients to perform secure dynamic updates. Secure updates utilize Kerberos to authenticate computers and ensure that only those clients that created a record can subsequently update the same record.
If you’re using DHCP to provide secure updates on behalf of DHCP clients, one important caveat is that DHCP servers should not be located on the domain controller, if possible, because of specific issues in regard to secure updates. The reason for this recommendation is that all DHCP servers are placed in a group known as DNSUpdateProxy. Any members of this group do not take ownership of items that are published in DNS. This group was created because DHCP servers can dynamically publish updates for clients automatically, and the clients would need to modify their entries themselves. Subsequently, the first client to access a newly created entry would take ownership of that entry. Because domain controllers create sensitive SRV records and the like, it is not wise to use a domain controller as a member of this group, and it is by extension not wise to have DHCP on domain controllers for this reason. If establishing DHCP on a domain controller is unavoidable, it is recommended to disable this functionality by not adding the server into this group.
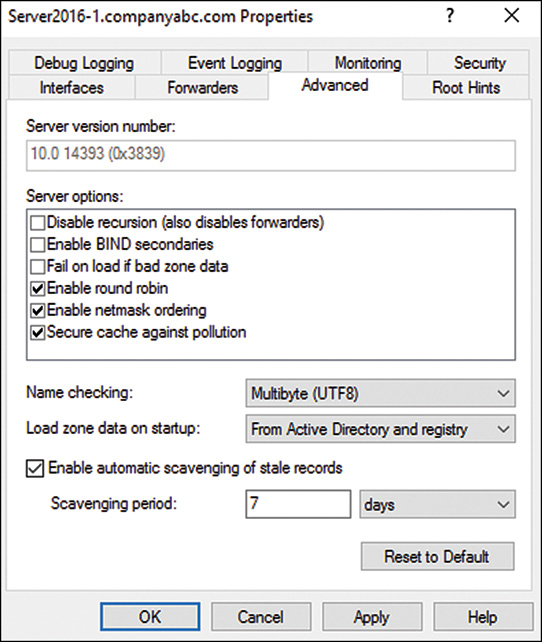
Exploring Aging and Scavenging for DNS
DNS RRs often become stale, or no longer relevant, as computers are disconnected from the network or IP addresses are changed without first notifying the DNS server. The process of scavenging those records removes them from a database after their original owners do not update them. Scavenging is not turned on, by default, but this feature can be enabled in Windows Server 2016 by following these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Right-click the server name and choose Properties.
6. Select the Advanced tab.
7. Check the Enable Automatic Scavenging of Stale Records check box.
8. Select a scavenging period, as shown in Figure 9.13, and click OK to save your changes.
Scavenging makes a DNS database cleaner, but overly aggressive scavenging can also remove valid entries. Therefore, if you’re using scavenging, it is wise to strike a balance between a clean database and a valid one.
Examining Root Hints
By default, a DNS installation includes a listing of Internet-level name servers that can be used for name resolution of the .com, .net, .uk, and like domain names on the Internet. When a DNS server cannot resolve a query locally in its cache or in local zones, it consults the Root Hints list, which indicates which servers to begin iterative queries with.
The Hints file should be updated on a regular basis to ensure that the servers listed are still relevant. This file is located in \%systemroot%system32DNScache.dns and can be updated on the Internet at the following address:
ftp://ftp.internic.net/domain/named.cache
At the time of writing, the latest root hints file, or root name servers, was dated Jun 8, 2011. The contents are shown in Listing 9.1. You can see the root server names (for example, A.ROOT-SERVER.NET) and their A records (for example, 192.41.0.4).
LISTING 9.1 Root Hints File Contents
; This file holds the information about root name servers needed to
; initialize cache of Internet domain name servers
; (e.g. reference this file in the "cache . <file>"
; configuration file of BIND domain name servers).
;
; This file is made available by InterNIC
; under anonymous FTP as
; file /domain/named.cache
; on server FTP.INTERNIC.NET
; -OR- RS.INTERNIC.NET
;
; last update: Jun 8, 2011
; related version of root zone: 2011060800
;
; formerly NS.INTERNIC.NET
;
. 3600000 IN NS A.ROOT-SERVERS.NET.
A.ROOT-SERVERS.NET. 3600000 A 198.41.0.4
A.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:BA3E::2:30
;
; FORMERLY NS1.ISI.EDU
;
. 3600000 NS B.ROOT-SERVERS.NET.
B.ROOT-SERVERS.NET. 3600000 A 192.228.79.201
;
; FORMERLY C.PSI.NET
;
. 3600000 NS C.ROOT-SERVERS.NET.
C.ROOT-SERVERS.NET. 3600000 A 192.33.4.12
;
; FORMERLY TERP.UMD.EDU
;
. 3600000 NS D.ROOT-SERVERS.NET.
D.ROOT-SERVERS.NET. 3600000 A 128.8.10.90
D.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2D::D
;
; FORMERLY NS.NASA.GOV
;
. 3600000 NS E.ROOT-SERVERS.NET.
E.ROOT-SERVERS.NET. 3600000 A 192.203.230.10
;
; FORMERLY NS.ISC.ORG
;
. 3600000 NS F.ROOT-SERVERS.NET.
F.ROOT-SERVERS.NET. 3600000 A 192.5.5.241
F.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2F::F
;
; FORMERLY NS.NIC.DDN.MIL
;
. 3600000 NS G.ROOT-SERVERS.NET.
G.ROOT-SERVERS.NET. 3600000 A 192.112.36.4
;
; FORMERLY AOS.ARL.ARMY.MIL
;
. 3600000 NS H.ROOT-SERVERS.NET.
H.ROOT-SERVERS.NET. 3600000 A 128.63.2.53
H.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:1::803F:235
;
; FORMERLY NIC.NORDU.NET
;
. 3600000 NS I.ROOT-SERVERS.NET.
I.ROOT-SERVERS.NET. 3600000 A 192.36.148.17
I.ROOT-SERVERS.NET. 3600000 AAAA 2001:7FE::53
;
; OPERATED BY VERISIGN, INC.
;
. 3600000 NS J.ROOT-SERVERS.NET.
J.ROOT-SERVERS.NET. 3600000 A 192.58.128.30
J.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:C27::2:30
;
; OPERATED BY RIPE NCC
;
. 3600000 NS K.ROOT-SERVERS.NET.
K.ROOT-SERVERS.NET. 3600000 A 193.0.14.129
K.ROOT-SERVERS.NET. 3600000 AAAA 2001:7FD::1
;
; OPERATED BY ICANN
;
. 3600000 NS L.ROOT-SERVERS.NET.
L.ROOT-SERVERS.NET. 3600000 A 199.7.83.42
L.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:3::42
;
; OPERATED BY WIDE
;
. 3600000 NS M.ROOT-SERVERS.NET.
M.ROOT-SERVERS.NET. 3600000 A 202.12.27.33
M.ROOT-SERVERS.NET. 3600000 AAAA 2001:DC3::35
; End of File
You can see the root hints for a Windows Server 2016 DNS server by doing the following:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Right-click the server name and choose Properties.
6. Select the Root Hints tab.
The name servers should match those in the root hints file retrieved from the InterNIC FTP site.
Understanding the Role of Forwarders
Forwarders are name servers that handle all iterative queries for a name server. In other words, if a server cannot answer a query from a client resolver, servers that have forwarders simply forward the request to an upstream forwarder that will process the iterative queries to the Internet root name servers. Forwarders are often used in situations in which an organization uses the DNS servers of an Internet service provider (ISP) to handle all name-resolution traffic. Another common situation occurs when Active Directory’s DNS servers handle all internal AD DNS resolution but forward outbound DNS requests to another DNS environment within an organization, such as a legacy UNIX BIND server.
In conditional forwarding, queries that are made to a specific domain or set of domains are sent to a specifically defined forwarder DNS server. This type of scenario is normally used to define routes that internal domain resolution traffic will follow. For example, if an organization controls the companyabc.com domain namespace and the companyxyz.com namespace, it might want queries between domains to be resolved on local DNS servers, as opposed to being sent out to the Internet just to be sent back again so that they are resolved internally.
Forward-only servers are never meant to do iterative queries, but rather to forward all requests that cannot be answered locally to a forwarder or set of forwarders. If those forwarders do not respond, a failure message is generated.
If you plan to use forwarders in a Windows Server 2016 DNS environment, you can establish them by following these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Right-click the server name and choose Properties.
6. Select the Forwarders tab.
7. Click Edit to create forwarders.
8. Type in the IP address or FQDN of the server or servers that will be forwarders. Press Enter for each server entered, and they will be validated. Click OK when you have finished.
9. If this server will be configured only to forward, and to otherwise fail if forwarding does not work, uncheck the Use Root Hints If No Forwarders Are Available check box.
10. Click OK to save the changes.
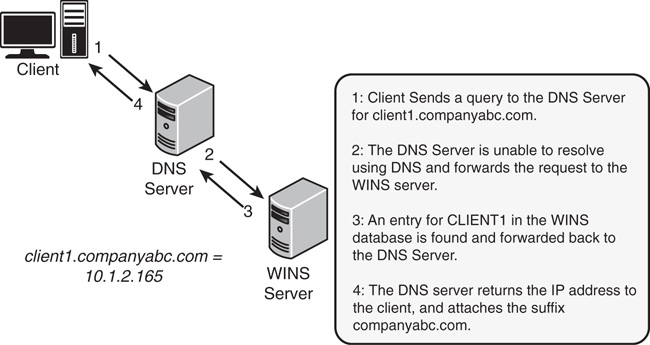
Using WINS for Lookups
In environments with a significant investment in WINS, the WINS database can be used in conjunction with DNS to provide for DNS name resolution. If a DNS query has exhausted all DNS methods of resolving a name, a WINS server can be queried to provide for resolution. This method creates WINS RRs in DNS that are established to support this approach.
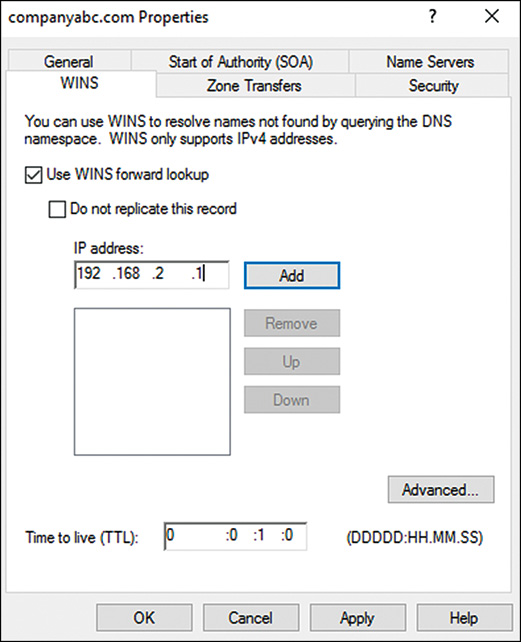
To enable WINS to assist with DNS lookups, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Expand the Forward Lookup Zones nodes.
6. Select the zone node.
7. Right-click the zone in question and choose Properties.
8. Choose the WINS tab.
9. Check the Use WINS Forward Lookup check box.
10. Enter the IP address of the WINS servers, click the Add button, and then click OK to save the changes.
Understanding the Evolution of Microsoft DNS
Windows Server 2016’s implementation of AD DS continues to support the advanced feature set that Windows 2000 DNS introduced and was expanded again in Windows Server 2003 and later. Several key functional improvements were added, but the overall design and functionality changes have not been significant enough to change any Windows 2008 design decisions that were previously made regarding DNS. The following sections describe the functionality introduced in Windows 2000 and later supported all the way to Windows Server 2016.
Active Directory-Integrated Zones
The most dramatic change in Windows 2000’s DNS implementation was the concept of directory-integrated DNS zones, known as AD-integrated zones. These zones were stored in Active Directory, as opposed to a text file as in standard DNS. When the Active Directory was replicated, the DNS zone was replicated as well. This also allowed for secure updates, using Kerberos authentication, as well as the concept of multimaster DNS, in which no one server is the master server and all DNS servers contain a writable copy of the zone.
Windows Server 2016, like Windows Server versions before it, utilizes AD-integrated zones, but with one major change to the design: Instead of storing the zone information directly in the naming contexts of Active Directory, it is stored in the application partition to reduce replication overhead. You can find more information about this concept in the following sections.
Dynamic Updates
As previously mentioned, dynamic updates, using Dynamic DNS (DDNS), allow clients to automatically register, update, and unregister their own host records as they are connected to the network.
Unicode Character Support
Introduced in Windows 2000 and supported in Windows Server 2016, Unicode support of extended character sets enables DNS to store records written in Unicode, or essentially multiple character sets from many different languages. This functionality essentially allows the DNS server to utilize and perform lookups on records that are written with nonstandard characters, such as underscores, foreign letters, and so on.
NOTE
Although Microsoft DNS supports Unicode characters, it is a best practice that you make any DNS implementation compliant with the standard DNS character set so that you can support zone transfers to and from non-Unicode-compliant DNS implementations, such as UNIX BIND servers. This character set includes a–z, A–Z, 0–9, and the hyphen (-) character.
DNS in Windows Server 2016
The Windows Server 2016 support for basic BIND version of DNS help to further establish DNS as a reliable, robust name-resolution strategy for Microsoft and non-Microsoft environments. An overall knowledge of the increased functionality and the structural changes will help you to further understand the capabilities of DNS in Windows Server 2016.
Application Partition
Perhaps the most significant feature in Windows Server 2016 DNS implementation, Active Directory-integrated zones are stored in the application partition of the AD. For every domain in a forest, a separate application partition is created and is used to store all records that exist in each AD-integrated zone. Because the application partition is not included as part of the Global Catalog, DNS entries are no longer included as part of global catalog replication.
With the application partition concept, replication loads are now reduced while important zone information is delegated to areas of the network where they are needed.
Automatic Creation of DNS Zones
The Configure a DNS Server Wizard, as demonstrated in “Installing DNS Using the Add Roles Wizard” section, allows for the automatic creation of a DNS zone through a step-by-step wizard. This feature greatly eases the process of creating a zone, especially for Active Directory. The wizard can be invoked by right-clicking the server name in the DNS Manager and choosing Configure a DNS Server.
Fix to the “Island” Problem
Earlier versions of the Microsoft DNS had a well-documented issue that was known as the “island” problem, which was manifested by a DNS server that pointed to itself as a DNS server. If the IP address of that server changed, the DNS server updated its own entry in DNS, but then other DNS servers within the domain were unable to successfully retrieve updates from the original server because they were requesting from the old IP address. This effectively left the original DNS server in an island by itself, hence the term.
Microsoft DNS fixed this problem in Windows Server 2003 and above. Windows Server 2016 DNS first changes its host records on a sufficient number of other authoritative servers within DNS so that the IP changes made will be successfully replicated, thus eliminating this island problem. As a result, it is no longer necessary to point a root DNS server to another DNS server for updates, as was previously recommended as a method of resolving this issue.
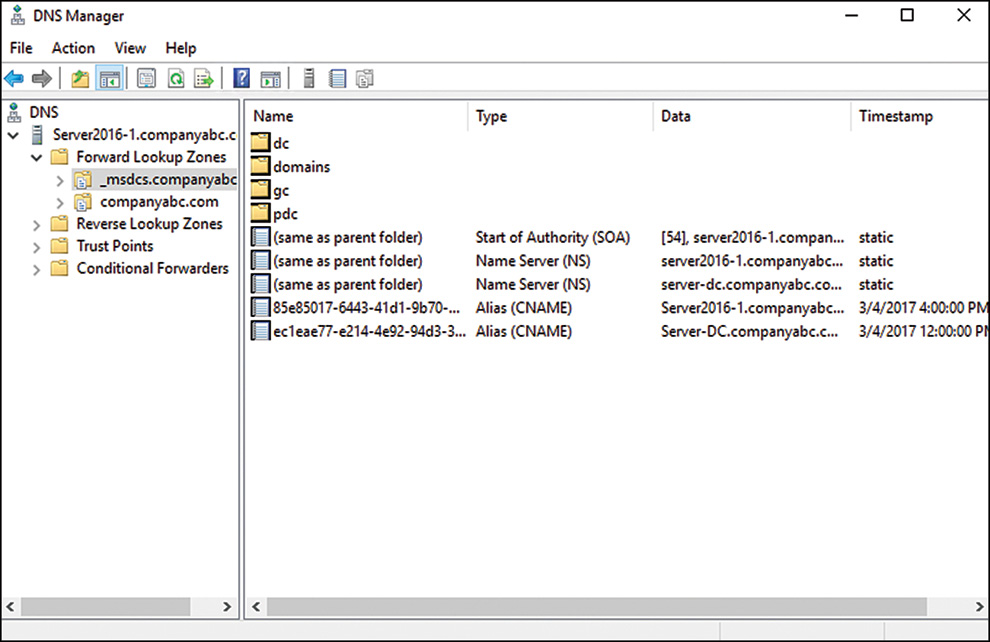
Forest Root Zone for _msdcs
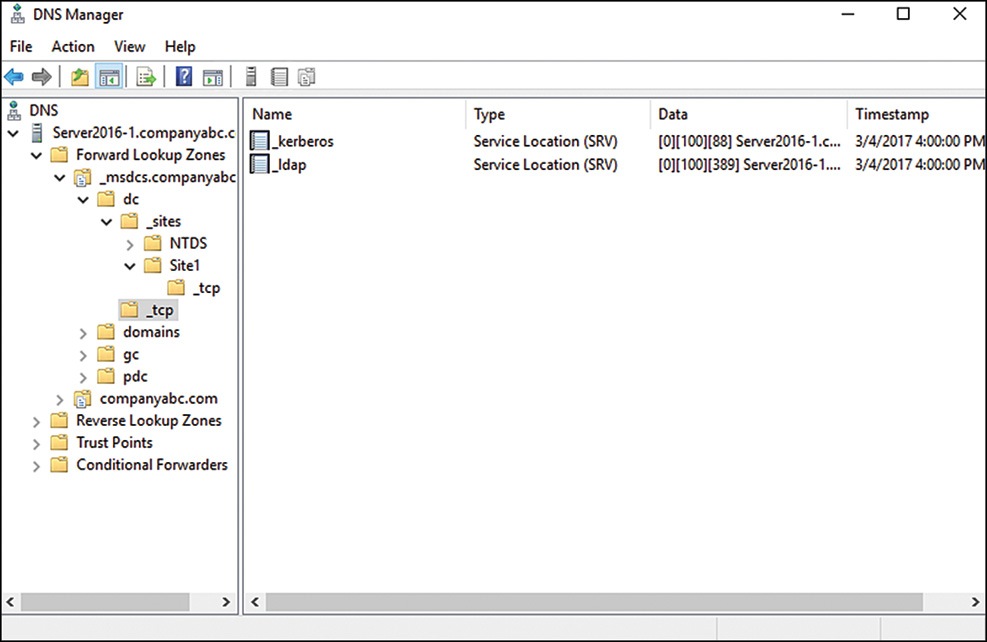
In Active Directory, all client logons and lookups are directed to local domain controllers and Global Catalog servers through references to the SRV records in DNS. These SRV records were stored in a subdomain to an Active Directory domain that is known as the _msdcs subdomain.
In Windows Server 2016, _msdcs is a separate zone in DNS, as shown in Figure 9.14. This zone, stored in the application partition, is replicated to every domain controller that is a DNS server. This listing of SRV records was moved mainly to satisfy the requirements of remote sites. In Windows 2000, these remote sites had to replicate the entire DNS database locally to access the _msdcs records, which led to increased replication time and reduced responsiveness. If you delegate the SRV records to their own zone, only this specific zone can be designated for replication to remote site DNS servers, saving replication throughput and increasing the response time for clients.
DNS in an Active Directory Domain Services Environment
DNS is inseparable from Active Directory. In fact, the two are often confused for one another because of the similarities in their logical structures.
Active Directory uses a hierarchical X.500-based structure that was designed to map into the DNS hierarchy, hence the similarities. In addition, Active Directory utilizes DNS for all internal lookups, from client logons to Global Catalog lookups. Subsequently, strong consideration into how DNS integrates with Active Directory is required for those considering deploying or upgrading AD.
The Impact of DNS on AD DS
Problems with DNS can spell disaster for an Active Directory environment. Because all servers and clients are constantly performing lookups on one another, a break in name-resolution service can severely affect Active Directory functionality.
For this and other reasons, installing a redundant DNS infrastructure in any AD DS implementation is strongly recommended. Even smaller environments should consider duplication of the primary DNS zone, and nearly as much emphasis as is put into protecting the Global Catalog AD index should be put into protecting DNS.
Security considerations for the DNS database should not be taken for granted. Secure updates to AD-integrated zones are highly recommended, and keeping DHCP servers off a domain controller can also help to secure DNS (see previous sections of this chapter for more details on this concept). In addition, limiting administrative access to DNS will help to mitigate problems with unauthorized “monkeying around” with DNS.
AD DS in Non-Microsoft DNS Implementations
AD DS was specifically written to be able to coexist and, in fact, utilize a non-Microsoft DNS implementation as long as that implementation supports dynamic updates and SRV records. For example, AD functions in all versions of UNIX BIND 8.1.2 or higher. With this point in mind, however, it is still recommended that an organization with a significant investment in Microsoft technologies consider hosting Active Directory DNS on Windows Server 2016 systems because functionality and security enhancements provide for the best fit in these situations.
For environments that use older versions of DNS or are not able (or willing) to host Active Directory clients directly in their databases, Active Directory DNS can simply be delegated to a separate zone in which it can be authoritative. The Windows Server 2016 systems can simply set up forwarders to the foreign DNS implementations to provide for resolution of resources in the original zone.
Using Secondary Zones in an AD DS Environment
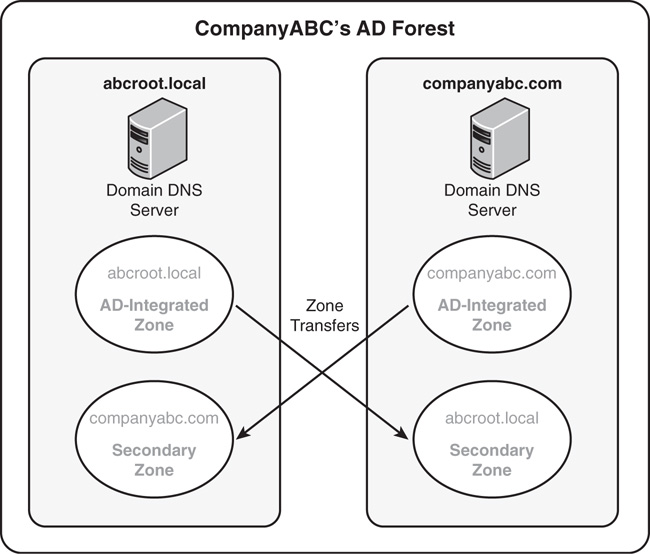
Certain situations in Active Directory require the use of secondary zones to handle specific name resolution. For example, in peer-root domain models, where two separate trees form different namespaces within the same forest, secondaries of each DNS root were required in Windows 2000 to maintain proper forestwide synchronization.
Because each tree in a peer-root model is composed of independent domains that might not have security privileges in the other domains, a mechanism will need to be in place to allow for lookups to occur between the two trees. The creation of secondary zones in each DNS environment will provide a solution to this scenario, as illustrated in Figure 9.15. Windows Server 2016 supports the option of replicating these separate trees to all DNS servers in the forest, reducing the need for secondary zones. Replicating secondary zones outside of a forest is still sometimes necessary, however. Conditional forwarding and stub zones can also be used in certain cases to achieve a similar result without the need for data replication.
SRV Records and Site Resolution
All AD DS clients use DNS for any type of domain-based lookups. Logons, for example, require lookups into the Active Directory for specific SRV records that indicate the location of domain controllers and Global Catalog servers. Windows Server 2016, as previously mentioned, divides the location of the SRV records into a separate zone, which is replicated to all domain controllers that have DNS installed on them.
Subdomains for each site are created in this zone; they indicate which resource is available in those specific sites, as shown in Figure 9.16. In a nutshell, if an SRV record in the specific site subdomain is incorrect, or another server from a different site is listed, all clients in that site are forced to authenticate in other sites. This concept is important because a common problem is that when Active Directory sites are created before they are populated with servers, an SRV record from the hub location is added to that site subdomain in DNS. When a new server is added to those sites, their SRV records join the other SRV records that were placed there when the site was created. These records are not automatically deleted, and they consequently direct clients to servers across slow wide-area network (WAN) links, often making logon times very slow.
In addition to the site containers, the root of these containers contains a list of all domain controllers in a specific domain. These lists are used for name resolution when a particular site server does not respond. If a site domain controller is down, clients randomly choose a domain controller in this site.
GlobalNames Zone
In some cases, using a fully qualified domain name (FQDN) is not convenient for the end users. This is especially true for novice users or in the case of very long domain names. A user entering the uniform resource locator (URL) http://intranet.convergentcomputing.com is quite likely to make a mistake in the typing. The WINS name resolution provides relief from this, in that single-label names can be used instead. This allows the user to type the URL http://intranet and still reach the desired resource.
However, with the advent of IPv6, WINS will no longer be supported as the new addressing is deployed throughout the organization. There are also many advantages of DNS over WINS, including reducing administrative overhead, single name-resolution repository, security, and open standards.
Windows Server 2016 provides a feature that was introduced in Windows Server 2008 to address this problem, specifically the GlobalNames zone (GNZ). This zone provides single-label name resolution via a DNS zone, similar to WINS. The zone is a normal forward lookup zone, albeit with a special name (GlobalNames), and is used by the DNS server in a special way. If the DNS server is unable to resolve an address in its local zones, it will then resolve the single-label address against the GNZ.
The GNZ holds out the promise of finally doing away with WINS and NetBIOS naming.
To configure the GNZ, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Select Action, New Zone.
7. Click Next on the Welcome page.
8. Select Primary Zone and make sure that the Store the Zone in Active Directory check box is checked. Click Next.
9. Select To All DNS Servers in This Forest, and then click Next.
10. Enter the Zone name GlobalNames and click Next.
11. Leave the default Dynamic Update setting and click Next.
12. Click Finish to create the zone.
13. Open a PowerShell command prompt and enter the command Set-DnsServerGlobal NameZone -Enable $true. This command must be run on each DNS server that is expected to resolve global names, regardless of if the zone is replicated to them already.
Now the GNZ is ready to respond to queries. For any server that needs to respond to single-label queries, enter a CNAME record in the GNZ with the appropriate FQDN for the resource. The DNS server will try the GNZ after trying other local zones.
NOTE
The global name-resolution status of a Windows Server 2016 server can be checked with the PowerShell command Get-DnsServerGlobalNameZone. If GNZ is enabled, the Enable will show as True.
Troubleshooting DNS
Much has been written about the complexity of DNS, and even more confusion and misconceptions have been written about it. In truth, however, DNS structure is logical, so you can easily troubleshoot it, if you use the proper tools and techniques. A good grasp of these tools and their functionality is a must for proper name-resolution troubleshooting with DNS.
Using the DNS Event Viewer to Diagnose Problems
As any good administrator knows, Event Viewer is the first place to look when troubleshooting. Windows Server 2016 makes it even more straightforward to use because DNS events compiled from Event Viewer are immediately accessible from the DNS Manager Console. Parsing this set of logs can help you troubleshoot DNS replication issues, query problems, and other issues.
For more advanced event log diagnosis, you can turn on Debug Logging on a per-server basis. It is recommended that this functionality be turned on only as required, however, as this can affect server performance and the log files can fill up fast. To enable Debug Logging, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Right-click the server name and choose Properties.
6. Select the Debug Logging tab.
7. Check the Log Packets for Debugging check box.
8. Configure any additional settings as required, and click OK.
By default, the log file is named dns.log and is saved in The C:WindowsSystem32dns directory. Listing 9.2 shows the debug of the DNS server dc1.companyabc.com of a lookup of the record www.cco.com from the server at 10.1.2.13. You can see from the log that the request was forwarded to the DNS server at 12.222.165.144 and that the results were then sent to the requesting server at 10.1.1.1.
5/28/2016 6:48:32 PM 067C PACKET 000000BDAFD158A0 UDP Rcv 10.1.1.1 3b60
Q [0001 D NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:32 PM 067C PACKET 000000BDB0216410 UDP Snd 12.222.165.144 ebfc
Q [0000 NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:32 PM 067C PACKET 000000BDB0D8FF80 UDP Rcv 12.222.165.144 ebfc
R Q [8084 A R NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:32 PM 067C PACKET 000000BDAFD158A0 UDP Snd 10.1.1.1 3b60
R Q [8081 DR NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:58 PM 067C PACKET 000000BDB0A2B5B0 UDP Rcv 10.1.2.13 0006
Q [0001 D NOERROR] A (3)www(3)cco(3)com(10)companyabc(3)com(0)
5/28/2016 6:48:58 PM 067C PACKET 000000BDB0A2B5B0 UDP Snd 10.1.2.13 0006
R Q [8385 A DR NXDOMAIN] A (3)www(3)cco(3)com(10)companyabc(3)com(0)
5/28/2016 6:48:58 PM 067C PACKET 000000BDB01CFCE0 UDP Rcv 10.1.2.13 0007
Q [0001 D NOERROR] AAAA (3)www(3)cco(3)com(10)companyabc(3)com(0)
5/28/2016 6:48:58 PM 067C PACKET 000000BDB01CFCE0 UDP Snd 10.1.2.13 0007
R Q [8385 A DR NXDOMAIN] AAAA (3)www(3)cco(3)com(10)companyabc(3)com(0)
5/28/2016 6:48:58 PM 067C PACKET 000000BDB0D8FF80 UDP Rcv 10.1.2.13 0008
Q [0001 D NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:58 PM 067C PACKET 000000BDAFD158A0 UDP Snd 128.8.10.90 d511
Q [0000 NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDAFD27B40 UDP Rcv 128.8.10.90 d511
R Q [0080 NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDAFD158A0 UDP Snd 192.55.83.30 9b01
Q [0000 NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDB09D48F0 UDP Rcv 192.55.83.30 9b01
R Q [0080 NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDAFD158A0 UDP Snd 12.222.165.144 c2da
Q [0000 NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDAF446E30 UDP Rcv 12.222.165.144 c2da
R Q [8084 A R NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDB0D8FF80 UDP Snd 10.1.2.13 0008
R Q [8081 DR NOERROR] A (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDB0A2B5B0 UDP Rcv 10.1.2.13 0009
Q [0001 D NOERROR] AAAA (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDB0D8FF80 UDP Snd 12.222.165.144 7b4a
Q [0000 NOERROR] AAAA (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDB0F3BB90 UDP Rcv 12.222.165.144 7b4a
R Q [8084 A R NOERROR] AAAA (3)www(3)cco(3)com(0)
5/28/2016 6:48:59 PM 067C PACKET 000000BDB0A2B5B0 UDP Snd 10.1.2.13 0009
R Q [8081 DR NOERROR] AAAA (3)www(3)cco(3)com(0)
The DNS log can be very detailed and tedious to read, but provides a wealth of information about exactly what the DNS server is doing. You can get even more detail by selecting the Details check box on the Debug Logging tab, which also enables you to see the data that was returned. Logging does add significantly to the load of the DNS server, so it should only be enabled when troubleshooting and disabled immediately afterwards.
Using Performance Monitor to Monitor DNS
Performance Monitor is a built-in, often-overlooked utility that allows for a great deal of insight into issues in a network. With regard to DNS, many critical DNS counters can be monitored relating to queries, zone transfers, memory utilization, and other important factors.
Client-Side Cache and HOST Resolution Problems
Windows 2000 and higher clients have a built-in client cache for name resolution that caches all information retrieved from name servers. When requesting lookups, the client resolver parses this cache first, before contacting the name server. Items remain in this cache until the TTL expires, the machine is rebooted, or the cache is flushed. In cases where erroneous information has been entered into the client cache, it can be flushed by typing ipconfig /flushdns at the command prompt.
By default, all clients have a file named HOSTS that provides for a simple line-by-line resolution of names to IP addresses. This file is normally located in \%Systemroot% System32Driversetc. Problems can occur when these manual entries conflict with DNS, and it is, therefore, wise to ensure that there are not conflicts with this HOSTS file and the DNS database when troubleshooting.
Using the Nslookup Command-Line Utility
The Nslookup command-line utility is perhaps the most useful tool for DNS client troubleshooting. Its functionality is basic, but the information obtained can do wonders for helping to understand DNS problems. Nslookup, in its most basic operation, contacts the default DNS server of a client and attempts to resolve a name that is inputted. For example, to test a lookup on www.companyabc.com, type nslookup www.companyabc.com at the command prompt. Different query types can also be input into Nslookup. For example, you can create simple queries to view the MX and SOA records associated with a specific domain by following these steps, which are illustrated in Figure 9.17:
1. Open a command prompt instance by choosing Start, All Programs, Accessories, Command Prompt.
2. Type nslookup and press Enter.
3. Type set query=mx and press Enter.
4. Type domainname and press Enter.
5. Type set query=soa and press Enter.
6. Type domainname and press Enter.
Nslookup’s functionality is not limited to these simple lookups. Performing an nslookup /? lists the many functions it is capable of. Nslookup is a tool of choice for many name-resolution problems and is a must in any troubleshooter’s arsenal.
Using the Ipconfig Command-Line Utility
Another important tool for DNS resolution problems is the Ipconfig utility, the same utility used for common TCP/IP issues. There are several key functions that Ipconfig offers with regard to DNS. These functions can be invoked from the command prompt with the right parameter, detailed as follows:
![]() ipconfig /flushdns—If you experience problems with the client-side cache, the cache itself can be “flushed” through the invocation of the flushdns flag. This removes all previously cached queries that a client might be storing and is particularly useful if a server name has just changed IP addresses and particular clients have trouble connecting to it.
ipconfig /flushdns—If you experience problems with the client-side cache, the cache itself can be “flushed” through the invocation of the flushdns flag. This removes all previously cached queries that a client might be storing and is particularly useful if a server name has just changed IP addresses and particular clients have trouble connecting to it.
![]() ipconfig /registerdns—The registerdns flag forces the client to dynamically reregister itself in DNS, if the particular zone supports dynamic updates.
ipconfig /registerdns—The registerdns flag forces the client to dynamically reregister itself in DNS, if the particular zone supports dynamic updates.
![]() ipconfig /displaydns—An interesting but not well-known parameter is displaydns. This flag displays the contents of the client-side cache and is useful for troubleshooting specific issues with individual records.
ipconfig /displaydns—An interesting but not well-known parameter is displaydns. This flag displays the contents of the client-side cache and is useful for troubleshooting specific issues with individual records.
Using the Tracert Command-Line Utility
The Tracert utility is a valuable resource that gives you an idea of the path that a DNS query takes when being sent over a network. By directing Tracert at www.microsoft.com, for example, you can get an idea of how many routers and DNS servers the packet is crossing. The way that Tracert works is simple, but actually quite interesting. A DNS query that has a TTL of 1 is sent out. Because all routers are supposed to drop the TTL by 1 on each packet that they process, this means that the first router will refuse to forward the packet and send that refusal back to the originator. The originating machine then increments the TTL by 1 and resends the packet. This time the packet will make it past the first router and get refused by the second. This process continues until the destination is met. Needless to say, using this command-line utility is a simple yet effective way of viewing the path that a DNS query takes as it crosses the Internet.
Using the DNSCmd Command-Line Utility
The DNSCmd utility is essentially a command-line version of the DNS Manager console. Installed as part of the Windows Server 2016 DNS Server role, this utility enables administrators to create zones, modify records, and perform other vital administrative functions via the command line. You can view the full functionality of this utility by typing dnscmd /? at the command line, as illustrated in Listing 9.3.
LISTING 9.3 DNSCMD Command Options
Usage: DnsCmd <ServerName> <Command> [<Command Parameters>]
<ServerName>:
IP address or host name -- remote or local DNS server
. -- DNS server on local machine
<Command>:
/Info -- Get server information
/Config -- Reset server or zone configuration
/EnumZones -- Enumerate zones
/Statistics -- Query/clear server statistics data
/ClearCache -- Clear DNS server cache
/WriteBackFiles -- Write back all zone or root-hint datafile(s)
/StartScavenging -- Initiates server scavenging
/IpValidate -- Validate remote DNS servers
/EnumKSPs -- Enumerate available key storage providers
/ResetListenAddresses -- Set server IP address(es) to serve DNS requests
/ResetForwarders -- Set DNS servers to forward recursive queries to
/ZoneInfo -- View zone information
/ZoneAdd -- Create a new zone on the DNS server
/ZoneDelete -- Delete a zone from DNS server or DS
/ZonePause -- Pause a zone
/ZoneResume -- Resume a zone
/ZoneReload -- Reload zone from its database (file or DS)
/ZoneWriteBack -- Write back zone to file
/ZoneRefresh -- Force refresh of secondary zone from master
/ZoneUpdateFromDs -- Update a DS integrated zone by data from DS
/ZonePrint -- Display all records in the zone
/ZoneResetType -- Change zone type
/ZoneResetSecondaries -- Reset secondary
otify information for a zone
/ZoneResetScavengeServers -- Reset scavenging servers for a zone
/ZoneResetMasters -- Reset secondary zone’s master servers
/ZoneExport -- Export a zone to file
/ZoneChangeDirectoryPartition -- Move a zone to another directory partition
/ZoneSeizeKeymasterRole -- Seize the key master role for a zone
/ZoneTransferKeymasterRole -- Transfer the key master role for a zone
/ZoneEnumSKDs -- Enumerate the signing key descriptors for a zone
/ZoneAddSKD -- Create a new signing key descriptor for a zone
/ZoneDeleteSKD -- Delete a signing key descriptor for a zone
/ZoneModifySKD -- Modify a signing key descriptor for a zone
/ZoneValidateSigningParameters -- Validate DNSSEC online signing parameters for a
zone
/ZoneSetSKDState -- Set Active and/or Standby keys for a signing key
descriptor for a zone
/ZoneGetSKDState -- Retrieve dynamic state for a signing key descriptor
for a zone
/ZonePerformKeyRollover -- Trigger a key rollover in a signing key descriptor
for a zone
/ZonePokeKeyRollover -- Trigger a key rollover in a signing key descriptor
for a zone
/ZoneSign -- Signs the zone using DNSSEC online signing
parameters
/ZoneUnsign -- Removes DNSSEC signatures from a signed zone
/ZoneResign -- Regenerate DNSSEC signatures in a signed zone
/EnumRecords -- Enumerate records at a name
/RecordAdd -- Create a record in zone or RootHints
/RecordDelete -- Delete a record from zone, RootHints or cache
/NodeDelete -- Delete all records at a name
/AgeAllRecords -- Force aging on node(s) in zone
/TrustAnchorAdd -- Create a new trust anchor zone on the DNS server
/TrustAnchorDelete -- Delete a trust anchor zone from DNS server or DS
/EnumTrustAnchors -- Display status information for trust anchors
/TrustAnchorsResetType -- Change zone type for a trust anchor zone
/EnumDirectoryPartitions -- Enumerate directory partitions
/DirectoryPartitionInfo -- Get info on a directory partition
/CreateDirectoryPartition -- Create a directory partition
/DeleteDirectoryPartition -- Delete a directory partition
/EnlistDirectoryPartition -- Add DNS server to partition replication scope
/UnenlistDirectoryPartition -- Remove DNS server from replication scope
/CreateBuiltinDirectoryPartitions -- Create built-in partitions
/ExportSettings -- Output settings to DnsSettings.txt in the DNS server
database directory
/OfflineSign -- Offline signing zone files, including key
generation/deletion
/EnumTrustPoints -- Display active refresh information for all trust
points
/ActiveRefreshAllTrustPoints -- Perform an active refresh on all trust points now
/RetrieveRootTrustAnchors -- Retrieve root trust anchors via HTTPS
<Command Parameters>:
DnsCmd <CommandName> /? -- For help info on specific Command
In future versions of Windows, Microsoft might remove dnscmd.exe.
If you currently use dnscmd.exe to configure and manage the DNS server, Microsoft recommends that you transition to Windows PowerShell.
To view a list of commands for DNS server management, type Get-Command -Module DnsServer at the Windows PowerShell prompt. Additional information about Windows PowerShell commands for DNS is available at http://go.microsoft.com/fwlink/?LinkId=217627.
Managing DNS with PowerShell
The PowerShell commandlets are essentially a command-line version of the DNS Manager console. Installed as part of the Windows Server 2016 DNS Server role, this PowerShell module enables administrators to create zones, modify records, and perform other vital administrative functions via the command line exactly as can be done with the traditional DNSCmd tool. DNS configuration and management automation is greatly enhanced with Windows PowerShell, including the following:
![]() Feature parity with the user interface and DNSCmd.
Feature parity with the user interface and DNSCmd.
![]() DNS Server role installation/removal using Windows PowerShell.
DNS Server role installation/removal using Windows PowerShell.
![]() Windows PowerShell client query with DNSSEC validation results.
Windows PowerShell client query with DNSSEC validation results.
![]() Server configuration is enabled for computers running older operating systems.
Server configuration is enabled for computers running older operating systems.
You can view the full functionality of this utility by typing Get-Command -Module DnsServer at the PowerShell command line, as shown in Listing 9.4.
LISTING 9.4 PowerShell DNS Commandlets
CommandType Name ModuleName
----------- ---- ----------
Alias Export-DnsServerTrustAnchor DnsServer
Function Add-DnsServerConditionalForwarderZone DnsServer
Function Add-DnsServerDirectoryPartition DnsServer
Function Add-DnsServerForwarder DnsServer
Function Add-DnsServerPrimaryZone DnsServer
Function Add-DnsServerResourceRecord DnsServer
Function Add-DnsServerResourceRecordA DnsServer
Function Add-DnsServerResourceRecordAAAA DnsServer
Function Add-DnsServerResourceRecordCName DnsServer
Function Add-DnsServerResourceRecordDnsKey DnsServer
Function Add-DnsServerResourceRecordDS DnsServer
Function Add-DnsServerResourceRecordMX DnsServer
Function Add-DnsServerResourceRecordPtr DnsServer
Function Add-DnsServerRootHint DnsServer
Function Add-DnsServerSecondaryZone DnsServer
Function Add-DnsServerSigningKey DnsServer
Function Add-DnsServerStubZone DnsServer
Function Add-DnsServerTrustAnchor DnsServer
Function Add-DnsServerZoneDelegation DnsServer
Function Clear-DnsServerCache DnsServer
Function Clear-DnsServerStatistics DnsServer
Function ConvertTo-DnsServerPrimaryZone DnsServer
Function ConvertTo-DnsServerSecondaryZone DnsServer
Function Disable-DnsServerSigningKeyRollover DnsServer
Function Enable-DnsServerSigningKeyRollover DnsServer
Function Export-DnsServerDnsSecPublicKey DnsServer
Function Export-DnsServerZone DnsServer
Function Get-DnsServer DnsServer
Function Get-DnsServerCache DnsServer
Function Get-DnsServerDiagnostics DnsServer
Function Get-DnsServerDirectoryPartition DnsServer
Function Get-DnsServerDnsSecZoneSetting DnsServer
Function Get-DnsServerDsSetting DnsServer
Function Get-DnsServerEDns DnsServer
Function Get-DnsServerForwarder DnsServer
Function Get-DnsServerGlobalNameZone DnsServer
Function Get-DnsServerGlobalQueryBlockList DnsServer
Function Get-DnsServerRecursion DnsServer
Function Get-DnsServerResourceRecord DnsServer
Function Get-DnsServerRootHint DnsServer
Function Get-DnsServerScavenging DnsServer
Function Get-DnsServerSetting DnsServer
Function Get-DnsServerSigningKey DnsServer
Function Get-DnsServerStatistics DnsServer
Function Get-DnsServerTrustAnchor DnsServer
Function Get-DnsServerTrustPoint DnsServer
Function Get-DnsServerZone DnsServer
Function Get-DnsServerZoneAging DnsServer
Function Get-DnsServerZoneDelegation DnsServer
Function Import-DnsServerResourceRecordDS DnsServer
Function Import-DnsServerRootHint DnsServer
Function Import-DnsServerTrustAnchor DnsServer
Function Invoke-DnsServerSigningKeyRollover DnsServer
Function Invoke-DnsServerZoneSign DnsServer
Function Invoke-DnsServerZoneUnsign DnsServer
Function Register-DnsServerDirectoryPartition DnsServer
Function Remove-DnsServerDirectoryPartition DnsServer
Function Remove-DnsServerForwarder DnsServer
Function Remove-DnsServerResourceRecord DnsServer
Function Remove-DnsServerRootHint DnsServer
Function Remove-DnsServerSigningKey DnsServer
Function Remove-DnsServerTrustAnchor DnsServer
Function Remove-DnsServerZone DnsServer
Function Remove-DnsServerZoneDelegation DnsServer
Function Reset-DnsServerZoneKeyMasterRole DnsServer
Function Restore-DnsServerPrimaryZone DnsServer
Function Restore-DnsServerSecondaryZone DnsServer
Function Resume-DnsServerZone DnsServer
Function Set-DnsServer DnsServer
Function Set-DnsServerCache DnsServer
Function Set-DnsServerConditionalForwarderZone DnsServer
Function Set-DnsServerDiagnostics DnsServer
Function Set-DnsServerDnsSecZoneSetting DnsServer
Function Set-DnsServerDsSetting DnsServer
Function Set-DnsServerEDns DnsServer
Function Set-DnsServerForwarder DnsServer
Function Set-DnsServerGlobalNameZone DnsServer
Function Set-DnsServerGlobalQueryBlockList DnsServer
Function Set-DnsServerPrimaryZone DnsServer
Function Set-DnsServerRecursion DnsServer
Function Set-DnsServerResourceRecord DnsServer
Function Set-DnsServerResourceRecordAging DnsServer
Function Set-DnsServerRootHint DnsServer
Function Set-DnsServerScavenging DnsServer
Function Set-DnsServerSecondaryZone DnsServer
Function Set-DnsServerSetting DnsServer
Function Set-DnsServerSigningKey DnsServer
Function Set-DnsServerStubZone DnsServer
Function Set-DnsServerZoneAging DnsServer
Function Set-DnsServerZoneDelegation DnsServer
Function Show-DnsServerCache DnsServer
Function Show-DnsServerKeyStorageProvider DnsServer
Function Start-DnsServerScavenging DnsServer
Function Start-DnsServerZoneTransfer DnsServer
Function Suspend-DnsServerZone DnsServer
Function Sync-DnsServerZone DnsServer
Function Test-DnsServer DnsServer
Function Test-DnsServerDnsSecZoneSetting DnsServer
Function Unregister-DnsServerDirectoryPartition DnsServer
Function Update-DnsServerTrustPoint DnsServer
The Set-DnsServerGlobalNameZone PowerShell commandlet was used to enable the global names resolution earlier in the chapter.
Secure DNS with DNSSEC
Because DNS does not offer any form of security natively, it is vulnerable to spoofing, man-in-the-middle, and cache poisoning attacks. For this reason, it has become critical to develop a means for securing DNS. DNSSEC was developed to do just that.
There are a series of IETF RFCs that specify the DNSSEC extensions to DNS:
![]() RFC 4033—DNS Security Introduction and Requirements
RFC 4033—DNS Security Introduction and Requirements
![]() RFC 4034—Resource Records for the DNS Security Extensions
RFC 4034—Resource Records for the DNS Security Extensions
![]() RFC 4035—Protocol Modifications for the DNS Security Extensions
RFC 4035—Protocol Modifications for the DNS Security Extensions
![]() RFC 5155—DNS Security (DNSSEC) Hashed Authenticated Denial of Existence
RFC 5155—DNS Security (DNSSEC) Hashed Authenticated Denial of Existence
![]() RFC 5702—Use of SHA-2 Algorithms with RSA in DNSKEY and RRSIG Resource Records for DNSSEC
RFC 5702—Use of SHA-2 Algorithms with RSA in DNSKEY and RRSIG Resource Records for DNSSEC
![]() RFC 5011—Automated Updates of DNS Security (DNSSEC) Trust Anchors
RFC 5011—Automated Updates of DNS Security (DNSSEC) Trust Anchors
There are also several other supporting IETF RFCs. Together, these RFCs modify and extend the DNS protocol. The DNSSEC extensions provide the following:
![]() Origin authority
Origin authority
![]() Data integrity
Data integrity
![]() Authenticated denial of existence
Authenticated denial of existence
In a nutshell, DNSSEC allows clients to know that the DNS information is coming from a valid server, wasn’t changed, and that a given host exists or doesn’t exist. Windows Server 2016 supports all DNSSEC RFCs.
Active Directory DNSSEC support is a critical feature in Windows Server 2016, allowing secure DNS to be extended to Active Directory integrated DNS zones. Windows Server 2016 supports DNSSEC for Active Directory integrated DNS by supporting the following:
![]() Dynamic updates to zone records
Dynamic updates to zone records
![]() Multimaster DNS model for DNSSEC zones
Multimaster DNS model for DNSSEC zones
![]() Use of AD for secure key and trust anchor distribution
Use of AD for secure key and trust anchor distribution
Windows Server 2008 supported DNSSEC for AD-integrated zones, but did not support dynamic updates. This was a critical limiting factor in preventing rollout of DNSSEC to organizations because dynamic updates are a critical feature of AD-integrated zones and AD fault tolerance. Windows Server 2016 support for dynamic updates with DNSSEC allows AD-integrated zones to be fully utilized and organizations to realistically deploy DNSSEC.
Administration on DNSSEC in earlier versions of Windows Server was very manual, required a lot of steps, and required significant expertise. Windows Server 2016 supports the DNSSEC administration with the Zone Signing Wizard, allowing best practices defaults to be easily deployed and DNSSEC signed zones to be easily scaled out. Much of the administrative effort is automated, including the following:
![]() Automated re-signing on static and dynamic updates
Automated re-signing on static and dynamic updates
![]() Automated key rollovers
Automated key rollovers
![]() Automated signature refreshes
Automated signature refreshes
![]() Automated updates of secure delegations
Automated updates of secure delegations
![]() Automated distribution and updating of trust anchors
Automated distribution and updating of trust anchors
The ease of administration and automation brings DNSSEC in Windows Server 2016 to a production-ready capacity.
DNSSEC Components
The DNSSEC relies on signed zones, which is a zone whose records are signed as defined by RFC 4035. A signed zone contains one or more of the new DNSEC record types, which are DNSKEY, NSEC, RRSIG, and DS records. These records allow DNS data to be validated by resolvers.
Zone Signing Key (ZSK) is the encryption key used to sign the zone, essentially a public and private key combination stored in a certificate. The Key Signing Key (KSK) is the key used to sign the ZSK to validate it, essentially a public and private key combination as well.
The DNSKEY record is a DNSSEC record type used to store a public key. The KSK and the ZSK public keys are stored in the DNSKEY records to allow the zone signatures to be validated.
The Next Secure (NSEC) record is a DNSSEC record type used to prove the nonexistence of a DNS name. This allows DNS clients to be sure that if a record is not retrieved in a DNS lookup, the record does not exist in the DNSSEC zone.
The Resource Record Signature (RRSIG) record is used to hold the signature for a DNS record. For each A record, there will be a corresponding RRSIG record. For each NSEC record, there will also be a corresponding RRSIG record.
The Delegation Signer (DS) record is used to secure delegations to other DNS servers and confirm their validity. This prevents man-in-the-middle DNS servers from breaking the security chain during recursive lookups.
A nonvalidating security-aware stub resolver is a security-aware stub resolver that trusts one or more security-aware DNS servers to perform DNSSEC validation on its behalf. All Windows DNS clients are nonvalidating security-aware stub resolvers, meaning they do not actually do the DNSSEC validation.
The Windows DNS client is nonvalidating, meaning that the Windows DNS client does not check to see whether the DNS records are secured but instead implicitly trusts the DNS server. The Windows DNS client flags the DNS request based on the NRPT table and expects the DNS server to perform the check for it. The DNS server returns the results regardless and indicates whether the check for DNSSEC was successful. If the check was successful, the Windows DNS client passes the results to the application requesting the DNS lookup.
NOTE
To really ensure the security of the DNS requests, the DNS client must be able to validate the DNS server. The method of doing this for Windows systems is to use IPsec. To really, really secure DNS, IPsec must be deployed as well.
Important Performance Considerations for DNSSEC
Although DNSSEC introduces important security benefits, there are some impacts to deploying it.
Some impacts to consider when deploying DNSSEC are as follows:
![]() Increased memory requirements—A DNSSEC zone may require as much as five times the memory on the Windows Server 2016 server as an unsigned zone.
Increased memory requirements—A DNSSEC zone may require as much as five times the memory on the Windows Server 2016 server as an unsigned zone.
![]() Increased network traffic—A response to a DNS query against a DNSSEC zone will return additional DNSSEC records as compared to a unsigned zone and will increase the network traffic accordingly.
Increased network traffic—A response to a DNS query against a DNSSEC zone will return additional DNSSEC records as compared to a unsigned zone and will increase the network traffic accordingly.
![]() Increased processor utilization—The additional workload of validating DNSSEC zone data during queries can increase the processor load on the Windows Server 2016 server hosting the DNSSEC zone.
Increased processor utilization—The additional workload of validating DNSSEC zone data during queries can increase the processor load on the Windows Server 2016 server hosting the DNSSEC zone.
![]() Increased number of DNS records—A DNSSEC zone will have up to four times the number of records as an unsigned zone. For large zones, this can be a significant factor.
Increased number of DNS records—A DNSSEC zone will have up to four times the number of records as an unsigned zone. For large zones, this can be a significant factor.
It is important to ensure that adequate server-level resources are available when deploying DNSSEC, especially into existing Windows Server 2016 servers. For well-tuned virtual servers that are running at capacity, the additional workload to support DNSSEC on large zones can be a significant increase.
Configuring a DNSSEC Zone
In this scenario, the zone companyabc.com will be encrypted. The zone is unsecured to start and contains several records, shown in Figure 9.18.
The DNSSEC configuration and management is done using the DNS Manager utility. To sign a DNS zone, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Select the zone to sign.
7. Right-click the zone and select DNSSEC and then Sign the Zone.
8. At the Zone Signing Wizard screen, click Next.
9. Choose the desired setting to sign the zone, then click Next.
10. Review the settings, and then click Next to sign the zone.
11. Click Finish to exit the wizard.
The zone companyabc.com is now encrypted. Figure 9.19 shows the zone records after encryption.
There are four records for each previous entry now:
![]() Standard A Record
Standard A Record
![]() RR Signature (RRSIG) Record for the Standard Record
RR Signature (RRSIG) Record for the Standard Record
![]() Next Secure (NSEC) Record
Next Secure (NSEC) Record
![]() RR Signature (RRSIG) Record for the Next Secure Record
RR Signature (RRSIG) Record for the Next Secure Record
To distribute the trust anchor for the DNSSEC zone, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Select the zone to sign.
7. Right-click the zone and select DNSSEC and then Properties.
8. Select the Trust Anchor tab.
9. Check the Enable the Distribution of Trust Anchors for This Zone box.
10. Click OK to save the changes.
11. Click Yes to confirm the change.
12. Click OK when the setting is complete.
After the setting, there will be a new folder named Trust Points that contains a pair of records for the zone of type DNS KEY. These contain the public key for the trust anchor for the signed zone.
Without any additional configuration, the DNS clients blissfully ignore the DNSSEC for the zone. To have the clients use the DNSSEC properties of the DNS zone, they must be configured to request secure DNS entries. This is done by configuring a Name-resolution Policy Table (NRPT) policy for clients.
The NRPT policy can be configured through group policy. To create a NRPT group policy for the secure.companyabc.com zone, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select Tools and then Group Policy Management.
3. Expand Forest: companyabc.com, Domains, and select companyabc.com.
4. Right-click companyabc.com and select Create a GPO in This Domain, and Link It Here.
5. Enter NRPT Group Policy Object and click OK.
6. Right-click the NRPT Group Policy Object link and select Edit.
7. Expand Computer Configuration, Policies, Windows Settings, and select Name-resolution Policy.
8. In the To Which Part of the Namespace Does This Rule Apply? Field, select Suffix and enter companyabc.com.
9. On the DNSSEC tab, check the Enable DNSSEC in This Rule box.
10. Check the Validation box Require DNS Clients to Check That Name and Address Data Has Been Validated.
NOTE
The wording of this option is precise. The Windows DNS client will check that the DNS server has validated the data, but will not do the validation itself.
11. Figure 9.20 shows how the record should look. Click the Create button to create the record in the Name-resolution Policy Table at the bottom of the screen.
12. Close the GPMC editor to save the changes.
Now, all domain DNS clients will request that DNS servers check the validity of the lookups for domain companyabc.com using DNSSEC.
Reviewing the Windows Internet Naming Service
The Windows Internet Naming Service (WINS) has a long history in Microsoft networks. In the beginning, Microsoft networks were primarily broadcast based, using protocols such as NetBEUI to identify local computers. If a user on a Windows client wanted to find a system by name, the Windows client would send out a broadcast message by name, and if the system was on the same network, it would respond so the two systems could establish a connection and begin communication. The problem with this type of name resolution was that it did not scale beyond multiple subnets, and with today’s networks, broadcast messages can be blocked by local server and workstation firewalls and antimalware software. With the adoption of TCP/IP as an easily routable protocol, the need to translate NetBIOS or Windows computer names to IP addresses became a reality. This need gave rise to the development of WINS.
WINS provided a central database that can be referenced when a client system is looking up another system by hostname, and that is the key difference between WINS and DNS, hostname versus fully qualified name. As an example of this, a server named SERVER10 in the companyabc.com domain would have a WINS record named SERVER10 and a DNS record in the companyabc.com DNS zone named server10.companyabc.com.
Understanding the Need for Legacy Microsoft NetBIOS Resolution
WINS is effectively a simple database of NetBIOS names and their corresponding IP addresses. Some additional information, such as domain name, server type or service type, and so on, can be determined as well, from the 16th byte in a NetBIOS name stored in WINS.
WINS is considered legacy in the Microsoft world because NetBIOS resolution is being phased out in favor of the domain name system (DNS) form of name resolution. However, it is difficult to divorce WINS from modern networks because of the reliance on WINS by down-level (pre-Windows 2000) clients, legacy applications, and even some Microsoft services, such as the Distributed File System (DFS), that utilize NetBIOS resolution by default. Also, many Independent Software Vendors, or ISVs, develop their software for Microsoft networks, but their test networks sometimes only include a single network with no firewalling between systems. When these software applications are deployed on enterprise networks, they can fall short in name-resolution results, and deploying WINS might be the only viable solution.
As mentioned previously in this chapter, the new DNS GlobalNames feature is designed to remove the need for WINS.
Installing and Configuring WINS
As with many services in Windows Server 2016, the installation and configuration process of a WINS server is streamlined through the Add Features Wizard. This wizard automatically installs all necessary services and databases and configures other settings pertinent to a particular service. Although other methods of installation still exist, this method is the preferred approach in Windows Server 2016.
Installing WINS
Installation of WINS on Windows Server 2016 is straightforward, and no reboot is necessary. To install and configure the WINS feature on a Windows Server 2016 computer, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the Dashboard section and click the Add Roles and Features link.
3. Click Next on the Before You Begin page.
4. Leave the default selection Role-Based or Feature-Based Installation and click Next.
5. Select the server from the server pool to add the DNS role to and click Next.
6. Click Next to skip the Roles selection.
7. Select the WINS Server Feature check box, click Add Features button, and then click Next.
NOTE
When the WINS Features box is checked, the Add Roles and Features Wizard does a readiness check to ensure that the target server is ready for the WINS feature.
8. Click Install on the Confirmation page to install the WINS feature.
9. Click Close to exit the Add Roles and Features Wizard.
The DNS role can also be installed locally on a server core installation using PowerShell with the following command:
Install-WindowsFeature –Name WINS
Configuring Push/Pull Partners
If a WINS server in an environment is the sole WINS server for that network, no additional configuration is required other than ensuring that clients will be pointing to the WINS server in their IP configuration. However, if it has been decided that WINS is required, it is a best-practice recommendation to deploy a secondary WINS server to provide redundancy. Unlike DHCP, however, WINS replication partners will replicate their registered entries between each other. WINS replication is established through the designation of WINS push/pull partners.
A push partner for a particular WINS server is the server that “pushes” WINS database information to a receiving or pull partner. A pull partner is a WINS server from which changes are “pulled.” In a nutshell, if Server1 has Server2 configured as a push partner, Server2 must have Server1 configured as a pull partner, and vice versa.
A WINS push/pull topology should roughly map to an organization’s network topology. For example, if an organization is composed of two main offices that serve as network hubs, and several branch offices, each with its own WINS servers, the WINS push/pull topology could look something like Figure 9.21. In many organizations, however, if network connectivity is reliable between locations, it is a best practice to deploy only two WINS servers for the entire organization. This reduces WINS database replication and administration. Remote or branch office WINS servers should only be deployed on networks where network and/or firewall administrators block WINS traffic from remote networks.
Examining WINS Replication
WINS replicates database changes on a set schedule, which can be modified on a per-connection basis. Just as with any network communications, the replication schedule should be modified to fit the particular needs of an organization. If a WAN link is saturated with traffic, it might be wise to throttle back the WINS replication schedule. However, if a link between push/pull partners is robust, a shorter schedule can be established. To establish WINS replication between two WINS servers, follow these steps:
1. Install WINS on two designated servers as previously outlined. For our example, we will use DC1 and DC2.
2. On one of the servers, log on and open the WINS console (Server Manager, Tools, and select WINS). If prompted, click Continue to confirm the action.
3. Expand the WINS server in the console tree, and then choose Replication Partners. The right pane will display any existing replication partners.
4. If the desired replication partner is not already defined, in the console tree, right-click Replication Partners and select New Replication Partner.
5. Enter the name of the desired WINS server and click OK. This adds the designated WINS server as a push/pull partner, meaning that these servers will replicate and synchronize their database with one another.
6. In the WINS console tree, right-click the WINS node and choose Add Server.
7. Type in the name of the WINS server previously defined as a replication partner.
8. After the second WINS server is added to the console, repeat the preceding steps to add the first server as a replication partner.
WINS replication partners need to be defined on both systems before replication will function.
WINS replication partners replicate their database information with one another every 30 minutes by default. If you, the WINS administrator, want to change this replication schedule, complete the following steps:
1. Open the WINS console (Server Manager, Tools, and select WINS). If prompted, click Continue to confirm the action.
2. Expand the WINS server in the console tree, and then choose Replication Partners.
3. Right-click Push/Pull Partner (if one does not exist, it will have to be created) and choose Properties.
4. In the replication partner property pages, select the Advanced tab, and change the replication interval time to the desired length, as indicated in Figure 9.22, and click OK to save the settings.
5. Repeat this process on the other replication partner.
This can also be used to change other partner replication settings, such as number of retries, start replication at service startup, persistent connections, and other pertinent replication information.
Understanding NetBIOS Client Resolution and the LMHOSTS File
A Windows client does not immediately resort to a WINS server to determine the IP address of a NetBIOS name. This knowledge is essential in the troubleshooting of name resolution on a Windows client. Instead, a client first accesses its local NetBIOS cache for resolution. If an IP address changes, this cache might report the old address, impeding troubleshooting. To flush this cache, run nbtstat -R (with an uppercase R) at the PowerShell command line.
In addition to the local cache, clients by default always parse an LMHOSTS file, if one exists, before contacting a WINS server. If the LMHOSTS file contains erroneous information, it will impede proper name resolution. Always check to see whether this file is populated (it is usually located in %Systemroot%System32Driversetc on clients) before beginning to troubleshoot the WINS server.
Planning, Migrating, and Maintaining WINS
As previously mentioned, WINS is necessary in most production environments because the overriding dependencies on NetBIOS that were built in to Windows have not entirely been shaken out. In fresh installations of Windows Server 2016, WINS might not be necessary, but for older, upgraded environments, plans should be made for WINS being around for a few years.
Upgrading a WINS Environment
The WINS service itself is one of the more straightforward services to migrate to a separate set of servers as part of an upgrade to Windows Server 2016. A simple upgrade of the existing WINS server will do the trick for many environments; however, migrating to a separate server or set of servers might be beneficial if changing topology or hardware.
Migration of an existing WINS environment is most easily accomplished through the procedure described in this section. This procedure allows for the migration of an entire WINS database to a new set of servers, but without affecting any clients or changing WINS server settings. Figure 9.23 illustrates a WINS migration using this procedure.
In Figure 9.23, the existing servers, OldServer1 and OldServer2, handle WINS traffic for the entire network of fictional CompanyABC. They are configured with IP addresses 10.1.1.11 and 10.1.1.12, which are configured in all client IP settings as Primary and Secondary WINS, respectively. OldServer1 and OldServer2 are configured as push/pull partners.
The new servers, NewServer1 and NewServer2, are added to the network with the WINS service installed and configured as push/pull partners for each other. Their initial IP addresses are 10.1.1.21 and 10.1.1.22. OldServer1 and NewServer1 are then connected as push/pull partners for the network. Because the servers are connected this way, all database information from the old WINS database is replicated to the new servers, as illustrated in step 1, shown in Figure 9.23.
After the entire WINS database is replicated to the new servers, the old servers are shut down (on a weekend or evening to minimize impact), and NewServer1 and NewServer2 are immediately reconfigured to take the IP addresses of the old servers, as illustrated in step 2, shown in Figure 9.24.
The push/pull partner relationship between NewServer1 and NewServer2 is then reestablished because the IP addresses of the servers changed. The entire downtime of the WINS environment can be measured in mere minutes, and the old database is migrated intact. In addition, because the new servers assume the old IP addresses, no client settings need to be reconfigured.
There are a few caveats with this approach, however. If the IP addresses cannot be changed, WINS servers must be changed on the client side. If you’re using DHCP, you can do this by leaving all old and new servers up in an environment until the WINS change can be automatically updated through DHCP. Effectively, however, WINS migrations can be made very straightforward through this technique, and they can be modified to fit any WINS topology.
Exploring WINS and DNS Integration
DNS can use the WINS database to provide for quasi-DNS resolution of WINS clients. This means that if a name-resolution request is sent to a DNS server to resolve client1.companyabc.com, for example, the DNS server will first look in the companyabc.com zone. If no record exists for client1.companyabc.com, the DNS server will perform a lookup on the WINS database for CLIENT1; if a WINS record exists, the DNS server will take this IP address and send it back to the DNS client as client1.companyabc.com, as illustrated in Figure 9.25.
This functionality must be enabled on the DNS server because it is not configured by default. This feature is configured on a zone-by-zone basis; however, if the forward lookup zone is an AD-integrated zone, each Windows Server 2016 DNS server hosting this zone will copy this WINS setting. To enable WINS resolution on a DNS server, follow these steps:
1. Launch Server Manager from a Windows 2016 server with a full GUI.
2. Select the DNS section. The list of servers in the server pool with the DNS role installed will be shown.
3. Right-click the DNS server to configure and select DNS Manager.
4. Select the DNS server name to configure.
5. Select the Forward Lookup Zones node.
6. Right-click the zone in question and click Properties.
7. Choose the WINS tab.
8. Check the Use WINS Forward Lookup check box.
9. Enter the IP address of the WINS servers to be used for resolution of names not found in DNS, and click Add to save the changes, as illustrated in Figure 9.26.
10. If you are replicating this zone between DNS servers that are not running Windows Server 2016 DNS services, make sure to check the Do Not Replicate This Record box. This prevents the records from being replicated to other servers during zone transfers.
11. Click OK to finish and return to the DNS Manager page.
Summary
DNS has proven itself over time to be a robust, dependable, and extremely scalable solution to name resolution. A key improvement in Windows Server 2016 is the enhanced support of the secure DNS (DNSSEC) functionality. Supporting DNSSEC for Dynamic DNS allows for full support of Active Directory and DNSSEC to deploy to large and small organization.
Whether using DNS for a full-fledged AD DS implementation or simply setting up an Internet DNS presence, Windows Server 2016’s DNS continues on a successful, road-tested base to provide for a functional, reliable, enterprise name-resolution strategy.
Best Practices
The following are best practices from this chapter:
![]() Windows Server 2016 DNS whenever possible to support AD DS. If you must use a non-Windows DNS to host the AD zone, ensure that it supports SRV records, such as with BIND version 8.1.2 or later.
Windows Server 2016 DNS whenever possible to support AD DS. If you must use a non-Windows DNS to host the AD zone, ensure that it supports SRV records, such as with BIND version 8.1.2 or later.
![]() Establish a caching-only server in small branch office situations to alleviate large amounts of client query traffic across the network and to eliminate the need to replicate entire DNS zones to remote locations.
Establish a caching-only server in small branch office situations to alleviate large amounts of client query traffic across the network and to eliminate the need to replicate entire DNS zones to remote locations.
![]() Configure DHCP to dynamically update DNS information for down-level clients if dynamic records are necessary.
Configure DHCP to dynamically update DNS information for down-level clients if dynamic records are necessary.
![]() Identify the sources of dynamically updated information to prevent problems with reliability.
Identify the sources of dynamically updated information to prevent problems with reliability.
![]() Configure a DNS server to point to itself for DNS queries rather than to another DNS server.
Configure a DNS server to point to itself for DNS queries rather than to another DNS server.
![]() Make any DNS implementation compliant with the standard DNS character set so that you can support zone transfers to and from non-Unicode-compliant DNS implementations such as UNIX BIND servers. This includes a–z, A–Z, 0–9, and the hyphen (-) character.
Make any DNS implementation compliant with the standard DNS character set so that you can support zone transfers to and from non-Unicode-compliant DNS implementations such as UNIX BIND servers. This includes a–z, A–Z, 0–9, and the hyphen (-) character.
![]() Use the GNZ to reduce the reliance on WINS in the enterprise.
Use the GNZ to reduce the reliance on WINS in the enterprise.
![]() Turn on Debug Logging on a per-server basis for more advanced DNS event log diagnosis only when required, and turn off this functionality when it’s no longer necessary.
Turn on Debug Logging on a per-server basis for more advanced DNS event log diagnosis only when required, and turn off this functionality when it’s no longer necessary.
![]() When deploying DNSSEC, ensure that sufficient server resources are allocated to support the increased memory, network and processor requirements that signing the zones will create.
When deploying DNSSEC, ensure that sufficient server resources are allocated to support the increased memory, network and processor requirements that signing the zones will create.
![]() Implement redundant WINS servers by configuring servers as push/pull partners.
Implement redundant WINS servers by configuring servers as push/pull partners.
![]() Limit the number of WINS servers on the network to reduce WINS server replication and administration and to simplify WINS troubleshooting.
Limit the number of WINS servers on the network to reduce WINS server replication and administration and to simplify WINS troubleshooting.