CHAPTER 13
THE DANGEROUS INFORMATION TECHNOLOGY INSIDER: PSYCHOLOGICAL CHARACTERISTICS AND CAREER PATTERNS1
Jerrold M. Post
13.1 COMPUTER INFORMATION TECHNOLOGY INSIDERS
13.2 PSYCHOLOGICAL CHARACTERISTICS OF INFORMATION TECHNOLOGY SPECIALISTS
13.3 CHARACTERISTICS OF THE DANGEROUS COMPUTER INFORMATION TECHNOLOGY INSIDER (CITI)
13.4 ESCALATING PATHWAY TO MAJOR COMPUTER CRIME
13.5 STRESS AND ATTACKS ON COMPUTER SYSTEMS
13.6 TYPOLOGY OF COMPUTER CRIME PERPETRATORS
13.7 CONCLUSION AND IMPLICATIONS
13.1 COMPUTER INFORMATION TECHNOLOGY INSIDERS.
In the complex world of information technology, it is people who create the systems and it is people with authorized access, the computer information technology insiders (CITIs), who represent the greatest threat to these systems.
Computer security experts have developed ever more sophisticated technological solutions to protect sensitive information and combat computer fraud. But no matter how sensitive the computer intrusion detection devices, no matter how impenetrable the firewalls, they will be of no avail in countering the malicious insider.
In considering the population of authorized insiders, it is clear just how broad and variegated this category is and that the line between insiders and outsiders is often blurred.
CITIs include:
- Staff employees
- Contractors and consultants
- Partners and customers
- Temporary employees (temps)
- Short term
- Long term
- Former employees
- Employees on notice of dismissal
There is an interesting paradox that the less loyalty expected from a class of workers, the less attention is paid to their security threats. Thus, fairly careful screening, including criminal background checks and credit checks, is usually obtained for staff employees. Except for temps, from whom there is no reason to expect loyalty, little attention generally has been given to personnel security, although they too often have authorized access to the system. For the long-term temp, working side by side with a staff employee, the only differences is that the long-term temp does not have stock options and does not have an attractive benefits package. Is there any reason to expect that the long-term temp will have the same loyalty as the staff employee? Of course not, yet companies characteristically have paid less attention to the security threats presented by the temp than by the staff employee.
Customers and partners with authorized access to the system also represent a potential vulnerability. Former employees often retain their password access or have been able to “social engineer” obtaining access through relationships with employees.
What we sometimes call the about-to-become former employees refers to employees in the interval between when they learn they are about to be laid off and the actual termination of employment, with loss of password access. This interval is extremely dangerous. Once employees learn that their time is short, they must immediately start thinking about themselves and about their next job. How will they demonstrate their worth to the next potential employer? One obvious way would be to demonstrate proprietary material that they have helped design. Moreover, some will become embittered and will want to strike out at the company that does not care about them.
Loyalty will cease at the instant employment is terminated, with obvious implications for information technology (IT) securityso access should be terminated immediately upon announcement. All too often, not wanting to hurt the feelings of employees, or out of carelessness, employees in this vulnerable state retain access. Chapter 45 in this Handbook discusses this issue in more detail.
13.2 PSYCHOLOGICAL CHARACTERISTICS OF INFORMATION TECHNOLOGY SPECIALISTS.
Psychological studies of IT professionals overwhelmingly show a preponderance of introverts. They prefer the internal world of ideas to the outer world of people; they would much prefer curling up with a good book than going to a cocktail party. Because they tend to internalize stress and express themselves online, they pose a management challenge.
13.3 CHARACTERISTICS OF THE DANGEROUS COMPUTER INFORMATION TECHNOLOGY INSIDER (CITI).
Based on a review of more than 100 cases of computer crimes and on interviews with computer security professionals, a psychological pattern associated with vulnerable IT insiders emerges:
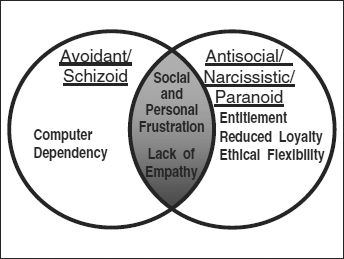
Social and Personal Frustrations
- They have a history of frustrations in their personal and professional relationships, including relationships with coworkers.
- They prefer the predictability and structure of work with computers.
- They have a propensity for anger toward authorities.
- A proportion of them demonstrate the revenge syndrome, and have actually chosen the world of computers with a view toward striking back at the society that has failed to recognize or reward their work.
Computer Dependency
- Online activity significantly interferes with, or replaces, direct social and professional interactions.
- They prefer the virtual world to the real world.
- Online relationships may constitute an avenue for influence, manipulation, or recruitment.
Ethical “Flexibility”
- A survey revealed that 6 to 7 percent believed that hacking, sabotage, and espionage were acceptable, reflecting an attitude that if the security was inadequate, if it was not “tied down,” it was theirs to play with.
- Perhaps reflecting their socialization, there was a notion that the computer was a toy, that data were not real. A U.S. Government computer crime expert observed that children would not dream of breaking into their neighbors' mailboxes but would think it was fun to break into their electronic mailboxes.
- The consequences did not seem serious.
Reduced Loyalty
- Organizational loyalty is challenged by a high degree of turnover.
- Employee loyalty is more to the cadre of IT professionals than to their employers.
Entitlement
- A belief that one is special, entitled to corresponding recognition, privileges, and exceptions, often reinforced by employers.
- Their grandiosity covers fragile egos.
- They are prone to anger and revenge when their specialness is not recognized.
Lack of Empathy
- They have no regard for the impact of their actions on others, or no ability to appreciate the consequences of their actions.
These personality traits may be associated with two overlapping personality types, the avoidant/schizoid personality, and the antisocial/narcissistic/paranoid personality, as represented in Exhibit 13.1.
The fact that individuals have many or even all of these personality traits does not mean that they will commit computer crimes. Rather they are particularly vulnerable. Personality disorders are further discussed in Chapter 12 of this Handbook.
13.4 ESCALATING PATHWAY TO MAJOR COMPUTER CRIME.
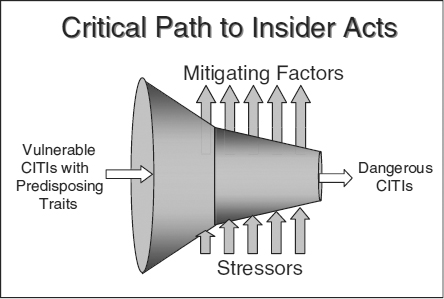
In studying the course of computer crime perpetrators over time, one of the findings is that the majority were loyal at the time they were hired. And whether they went on to become disloyal was a function of the interaction between stressors and mitigating circumstances.
EXHIBIT 13.1 Personality Traits of Vulnerable IT Insiders
When an individual is going through professional stressful circumstances and has a sound marriage, the strength of the marriage and support from a spouse can be crucial in surmounting the professional stress. Similarly, when, for example, an individual is going through a traumatic divorce but has a stable job, the employment context is a mitigating factor that can provide support through difficult personal circumstances. However, individuals undergoing both personal and professional stress at the same time are particularly vulnerable.
This interaction is depicted in Exhibit 13.2.
As an example, an IT specialist at a natural gas plant became distressed when his previous supervisor, who was technically highly proficient and appreciated the quality of the subject's work, was replaced by a manager with no technical competence. At the same time, the subject's wife had a recurrence of breast cancer. The doctor informed them that she required a bone marrow transplant, but the company's health insurance policy stated that this was not a covered procedure because it was considered experimental therapy. At this point, the employee became emotionally disturbed. He felt that the company was killing his wife and that his supervisor did not understand him. A powerful indication was that he had hung an effigy of the supervisor in his backyard and was firing his high-powered rifle again and again at the effigy. But he did not attack the supervisor. Rather, he took the company hostage by taking control of the automated system of the natural gas plant, which in effect was a bomb waiting to explode. This was a case of impending IT violence in the workplace. In our consultation, we met with the company officials and the individual. We persuaded the company to override its usual procedures and ensure that healthcare would be made available to his wife. We suggested that he temporarily accept medical disability himself for the stress he was undergoing. The company was transformed in his mind's eye from a murderous employer that did not care to a helpful company that was concerned and wanted to help him, resolving the crisis. What were negative mitigating factors—a perceived uncaring company—became positive mitigating factors—a company that was concerned and responsive.
EXHIBIT 13.2 Critical Path to Insider Acts
13.5 STRESS AND ATTACKS ON COMPUTER SYSTEMS.
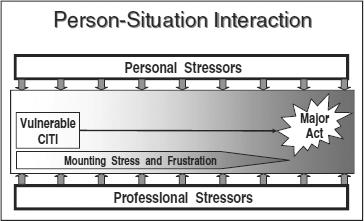
It is often assumed that major computer crime occurs when there is an interaction between a vulnerable employee and stress, and the result is a major attack against the company's information system, as depicted in Exhibit 13.3.
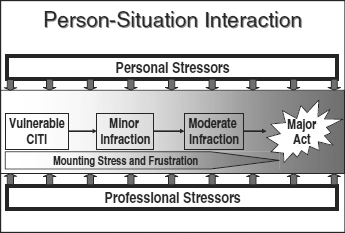
In fact, careful review of case studies of computer crime reveals a much more gradual time course, as reflected in Exhibit 13.4.
Typically, there is first a minor infraction, either overlooked or not dealt with for fear of upsetting a valued employee. Appropriate intervention at this stage, by management counseling, could save a valued employee from further infractions. But if stress continues to mount, a moderate infraction probably will occur. At this point, appropriate management intervention, could involve placing the employee on probation, with no access to sensitive systems, or termination. Such precautions could prevent a major act, but all too often management does not deal with escalating infractions of these “special” employees until a major destructive act occurs.
EXHIBIT 13.3 Person-Situation Interaction
EXHIBIT 13.4 Person-Situation Interaction, Escalating in Fractions
13.6 TYPOLOGY OF COMPUTER CRIME PERPETRATORS.
There is in fact a broad spectrum of computer crime perpetrators, with a range of motivations. These include:
- Explorers. Motivated by curiosity, they rarely purposefully do severe damage. They want to test their own abilities, and seek to penetrate compartments to which they do not have authorized access. They lack judgment concerning unmarked files. They are often picked up by systems administrators, but with no clear policy, they rarely suffer adverse consequences.
- Good Samaritans. They hack episodically to fulfill their responsibilities more effectively. They do not see this as a violation. The ends justify the means. They hack the system to save the day, to fix it in emergency situations. Their rationale is that they are testing the system's security.
- Machiavellians. These people covertly hack to advance their own careers, increase their own status, damage rivals, or establish future business. Examples include: a consultant who steals proprietary data; a subordinate who frames a boss; an employee who destroys a rival group's network card and plants a time bomb to establish a consulting job; and an IT specialist with a yen for foreign travel. His international company experienced outages with its systems in Rio de Janeiro, Hong Kong, and Paris that only he was able to resolve. Until the company realized that he was responsible for creating these problems, he was flying around the world first class, collecting frequent flier miles and large bonuses for his excellent work.
- Career thieves. Career thieves, unburdened by conscience, see the computer as tools for their criminal schemes.
- Moles. These people join a company or organization to commit espionage on behalf of a company or foreign government. An interesting example in the corporate world concerned a systems analyst who went to Bloomberg's Financial Systems to steal their sophisticated financial reporting software for a start-up company.
- Hackers. These people usually have a prior history of hacking and demonstrate a need to defy authorities. They derive significant satisfaction from their victories and have a need to show off and impress their peers. They are particularly dangerous when they are members of a hacking group.
- Hacker subtype: Golden parachuters. They have inserted a logic bomb or other system booby trap in expectation of a generous severance package or consulting fee. They are rarely reported, for the company calculates it is less expensive to agree to their terms while avoiding damage to their reputation. In one case, a company had hired an IT specialist, deferring a customary background search because of their immediate need for his technical skills. When they did run a criminal background check, they discovered that he had been convicted five times for computer fraud. When they informed him they could not continue to employ him, he responded, “I wondered how long it would take you to catch up with me. Let me tell you what I have done,” and then proceeded to describe the logic bomb he had inserted. “And for only $500,000 and a promise of non-prosecution, I will be glad to take care of this problem for you.” The company capitulated.
- Exceptions. Such people consider themselves special, deserving of extraordinary recognition, and above the rules. They often deflect blame to others. But beneath their arrogant, grandiose exterior they have very fragile self-esteem and are easily wounded.
- Exception subtype: Proprietors. Proprietors feel they own the system they have developed and are entitled to special privileges. They will hack to maintain control of what they deem to be their systems and will hack to deter rivals. They will resist turning over source code and backups. They may create problems only they can solve. An example concerns a high-powered programmer for a national bank, who had developed a complex national management system. Very well compensated, for the previous 18 months, with overtime, he had earned some $500,000. When a new supervisor realized there was no one backing him up, she instructed him to turn over the source code to a deputy. These flaming e-mail exchanges ensued over several months:
April:
Hacker: “His experience [referring to the designated backup] was ZERO. He does not know ANYTHING about our reporting tools. Until you fire me or I quit, I have to take orders from you…. Until he is a trained expert, I won't give him access. If you order me to give him root access, then you permanently have to relieve me of my duties on that machine. I can't be a garbage cleaner if someone screws up… I won't compromise on that.”
Supervisor: “You seem to have developed a personal attachment to the system servers. These servers and the entire system belong to this institution, not to you.”
The supervisor had in effect identified a proprietor, who acted as if he owned the system. She did not report the flaming e-mail to security or human resources, although she decided to terminate him. In order not to ruffle his feathers, she decided to change him to consultant status.
July:
Hacker: “Whether or not you continue me here after next month (consulting, full time or part time) you can always count on me for quick responses to any questions, concerns or production problems with the system. As always, you'll get the most cost effective and productive solution from me.”
His supervisor was reassured by this message.
Later in July:
Hacker: “I would be honored to work until the last week of August. As John may have told you, there are a lot of things which at times get ‘flaky’ with the system front-end and back-end. Two-week extension won't be enough time for me to look into everything for such a critical and complex system.
“Thanks for all your trust in me.”
On his last day of work, not only the main server but also the backup server crashed. Bank executives implored him to try to fix the problems, but he refused. An independent consulting firm hired to investigate the problems discovered sabotage. They estimated that the programming was so complex that to sabotage the system so thoroughly would have required several months, roughly the interval when his e-mails changed from flaming and obstinate to grateful. In effect, he had switched from being angry online to deciding to do the dirty deed. The ultimate cost to the bank was approximately $10 million.
- Exception subtype: Proprietors. Proprietors feel they own the system they have developed and are entitled to special privileges. They will hack to maintain control of what they deem to be their systems and will hack to deter rivals. They will resist turning over source code and backups. They may create problems only they can solve. An example concerns a high-powered programmer for a national bank, who had developed a complex national management system. Very well compensated, for the previous 18 months, with overtime, he had earned some $500,000. When a new supervisor realized there was no one backing him up, she instructed him to turn over the source code to a deputy. These flaming e-mail exchanges ensued over several months:
13.7 CONCLUSION AND IMPLICATIONS.
The Computer Security Institute, in its 12th Annual Computer Crime and Security Survey of 2007 reported that in the prior year, the percentage of respondents experiencing insider network and e-mail abuse was 59%. For the first time, this exceeded virus incidents, reported at 52%. The annual loss per survey respondent doubled from about $168,000 to $350,000. This is a human problem, as well as a technological problem, and requires an examination of personnel practices. The IT specialist with full access to the company's most sensitive systems must be subject to thorough, specialized re-employment procedures.
To have complete information systems security requires an audit not only of technological security but also of IT personnel security, from pre-employment and hiring procedures through to termination procedures. A policy is what a company does, not what it says. The company that deferred the criminal background check because of the need for the new hire's technical skills violated its stated policies. In effect, the company had a policy that a criminal background check was not required before hiring. When a company announces the layoff of an employee or a reduction in force, affected employees should have their access to sensitive systems immediately cut off. Even minor and moderate infractions must be documented and dealt with, and management must be evaluated on the manner in which they deal with these infractions.
Effective IT security management must ensure that
- The hiring process for employees in sensitive positions should be redesigned.
- Monitoring, detection, and management should be improved.
- Clear information technology policies should be formulated and briefed to incoming employees. An employee cannot be found in violation of a procedure if it is not clearly formulated and communicated.
- Specialized support services for IT employees should be established. For example, IT employees are often reluctant to meet with an Employee Assistance Program (EAP) counselor but may avail themselves of online support services.
- Screening and selection procedures should be augmented, to include online behavior by searching the Web using search engines.
- Termination procedures are formalized.
- Management of CITIs must be strengthened.
- Enforce computer ethics policies and mandated practices.
- Incorporate innovative approaches to the management of at-risk IT personnel.
- Add human factors to computer security audit.
Systematic audits of IT personnel security practices are required to complement the periodic technological audits. A particularly valuable aspect of the IT personnel security audit is the in-depth review of all troublesome cases the company has experienced, in order to identify flaws in its management system.
Even more important may be the study of best practices employed by other organizations to minimize the possibility of future troubles.
13.8 NOTE
1. This chapter is drawn from a major two-year project on the dangerous IT Insider conducted for the Department of Defense for which the author was principal investigator: Insider Threats to Critical Information Systems: Technical Report #2, Characteristics of the Vulnerable Critical Information Technology Insider (CITI), Political Psychology Associates, Ltd., June 1998.