CHAPTER 29
BIOMETRIC AUTHENTICATION
David R. Lease, Robert Guess, Steven Lovaas, and Eric Salveggio
29.2 IMPORTANCE OF IDENTIFICATION AND VERIFICATION
29.3 FUNDAMENTALS AND APPLICATIONS
29.3.2 Properties of Biometrics
29.3.3 Identification, Authentication, and Verification
29.3.5 Data Acquisition and Presentation
29.4 TYPES OF BIOMETRIC TECHNOLOGIES
29.4.2 Facial Scan/Recognition
29.4.6 Other Biometric Technologies
29.5 TYPES OF ERRORS AND SYSTEM METRICS
29.6 DISADVANTAGES AND PROBLEMS
29.6.2 Health and Disability Considerations
29.6.3 Environmental and Cultural Considerations
29.6.5 Attacks on Biometric Systems
29.7 RECENT TRENDS IN BIOMETRIC AUTHENTICATION
29.7.1 Government Advances in Biometric Authentication
29.7.2 Face Scanning at Airports and Casinos
29.7.3 Increased Deployment in the Financial Industry
29.7.4 Biometrics in the Healthcare Industry
29.7.5 Increased Deployment of Time and Attendance Systems
29.8 SUMMARY AND RECOMMENDATIONS
29.1 INTRODUCTION.
Once exclusively the purview of law enforcement, intelligence, and national security agencies, biometrics—the automated recognition of people based on their physiological or behavioral characteristics—is entering the business mainstream as a method of identification and authentication for access to physical and logical infrastructure. Biometric authentication technologies promise substantially improved security, convenience, and portability over other commonly used methods of authentication. Falling costs, improvements in technologies, increased security needs, and changing government regulations also encourage the adoption of biometrics. Notwithstanding these factors, to date relatively few organizations have implemented biometric authentication controls.
29.2 IMPORTANCE OF IDENTIFICATION AND VERIFICATION.
Ensuring the identity and authenticity of persons is a prerequisite to security and efficiency in present-day organizational operations. Intruders can damage physical and logical infrastructure, steal proprietary information, compromise competitive assets, and threaten organizational sustainability. Traditional methods of recognition and identification, wherein one individual identifies another based on his or her voice, physical appearance, or gait, are impractical, inefficient, and inaccurate in the scope of contemporary organizational operations. To address the need for rapid, efficient, and cost-effective authentication, organizations today primarily rely on the two methods of “something you know” and “something you have” (either applied individually or in combination) to verify the identity of persons accessing their physical and/or logical infrastructure. The most robust authentication systems use multiple factors of authentication. These forms of authentication are described in Chapter 28 in this Handbook.
29.3 FUNDAMENTALS AND APPLICATIONS.
Biometrics are based on the measurement and matching of distinctive physiological and/or behavioral characteristics. The former are based on direct measurement of a physiological characteristic of some part of the human body. Examples of physiological biometrics include finger, hand, retina, and iris scans. The latter indirectly measure characteristics of the human body based on measurements and data derived from an action. Commonly used behavioral biometrics include voice and signature scan and keystroke pattern.
29.3.1 Overview and History.
The use of nonautomated biometrics dates back to the beginning of human civilization, when individuals first began identifying other individuals based on certain physical or behavioral characteristics. The concept of biometrics as a means of authentication dates back more than 2,000 years. As early as 300 BC, Assyrian potters used their thumbprint as an early form of brand identity for their merchandise. The use of handwritten signatures (chops) in classical China is another example of an early biometric. In the first instance of a formal, legal biometric authentication system, fingerprints were used to sign contracts during the Tang dynasty (AD 618–906).
The development of contemporary biometric systems can be viewed as an outgrowth of the efforts of forensic scientists and law enforcement agencies to identify and classify criminals in the late nineteenth and early twentieth centuries. In 1882, Alphonse Bertillon introduced a system of body measurements called anthropometry to identify criminals. This system was proven unreliable because the measurements taken were not globally unique. A student of Bertillon, Edmund Locard, later proposed a fingerprint system based on the work of Sir Edmond Galton to identify people by analyzing unique points in fingerprint ridges and pores. Locard's system, which used 12 Galton points, is considered reliable to this day. This methodology underlies fully automated modern biometric including the Integrated Automated Fingerprint Identification Systems (IAFIS) used by law enforcement agencies. Commercial biometric systems (typically relying on hand geometry) designed for use in physical access to buildings, emerged in the 1960s and 1970s.
Biometric methods of identification and identity verification, including automatic fingerprint analysis and facial recognition technologies, have been available and used by some government/public agencies (e.g., law enforcement, intelligence, and national security) and a few private industries (e.g., facial recognition scans in casinos) since the 1960s and 1970s. Notwithstanding the potential benefits and advantages over other authentication methods, biometrics have not been widely applied, particularly in the corporate world. Analysts cite high costs of equipment and implementation, technological problems, vulnerabilities of specific biometrics, lack of standards, and user resistance (notably, concerns over privacy) as reasons for the lack of implementation.
However, in the decades of 1990 and 2000, significant improvements in biometric technologies, a movement toward standardization, changes in regulations requiring organizations to adopt stringent security and privacy controls, and significantly reduced costs have encouraged wider adoption. A number of U.S. Government agencies (e.g., Department of Homeland Security, Department of Transportation, Department of Defense, Customs and Border Protection, Department of Justice, National Library of Medicine) and businesses in certain industries (e.g., healthcare and finance) have significantly increased their use of biometrics during the past few years—a factor that is likely to encourage other organizations to adopt biometrics as well. At least one major computer manufacturer has banked on these rapid developments in biometrics applications. In late 2004, IBM (now Lenovo) began adding fingerprint scanners on its notebook computers, enabling users to increase security by requiring a finger swipe and a password (or just a finger swipe) to access files. Other computer manufacturers and peripheral vendors have added fingerprint scanning to computer keyboards and/or developed standalone fingerprint scanners that connect to computers via a Universal Serial Bus (USB) port.
Some analysts see the 2001 attacks on the World Trade Center and the Pentagon also as a key impetus behind the increased usage of biometrics for authentication and identification. The terrorist attacks have been critical in encouraging adoption not only because they have heightened the security concerns of companies and agencies but also because the impact and implications of the terrorists' attacks seem to have lowered users' resistance to the use of biometrics by employers and government. In other words, in the same way that the threat of global terrorism reduced public objections to possible infringements on civil liberties as a result of implementation of the U.S.A. PATRIOT Act and other security-focused measures, these attacks also appear to have rendered many people less sensitive to the potential privacy-invading implications of biometrics. Boroshok reported that a recent survey sponsored by AuthenTec found that 71 percent of U.S. consumers would pay more for biometric security options in their cell phones and 63 percent of consumers would pay an additional cost for these options to be added to their personal computers.1
The changing security environment has prompted forecasts of rapid growth in biometrics. In 2004, the International Biometric Group (IBG) predicted rapid growth for the biometrics industry over the next several years from revenues totaling under $50 million in 2004 to revenues of almost $200 million in 2008.2 In late 2003, analysts at the San Jose, California–based market research firm Frost and Sullivan predicted that biometric applications from commercial applications (not including the Federal Bureau of Investigation's IAFIS) would jump from $93.4 million in 2001 to $2.05 billion by 2006—up from the $700 million (in 2006) that these analysts predicted prior to the September 11, 2001, attacks. In January 2007, IBG released their most recent projections of market growth for the biometrics industry. They estimate that biometric industry revenues will grow from $3.01 billion in 2007 to over $7.4 billion by 2012.3
Despite rosy projections from industry analysts, adoption of biometric authentication systems continues to lag. Some firms continue to cite cost issues and privacy concerns, while others point to problems surrounding biometric implementation in airports and among government agencies. Overall, surveys of companies indicate that forecasts of dramatic and rapid growth in biometrics implementation may be overstated. Hulme reported that “only 9% of 300 business-technology executives surveyed for the InformationWeek Research Priorities 1Q2003 study say biometric deployment is a key business priority, down from 12% in the same quarter of 2002.”4 A 2003 Forrester Research survey found that only 1 percent of companies had implemented biometric systems, just 3 percent had a biometric system rollout in progress, only 15 percent were testing biometrics, and 58 percent of those surveyed had no plans to try biometrics.
29.3.2 Properties of Biometrics.
The contemporary meaning of biometrics emphasizes its automated aspects, which allow for deployment on a large scale. The most widely cited definition of biometrics is some variation of “the automatic identification of a person based on his or her physiological or behavioral characteristics.”5 The term “biometrics” generally is used as a noun to refer to the automatic recognition of persons based on their physical or behavioral characteristics. The term “biometric” can be used as a noun in reference to a single technology or measure (e.g., finger scan is a commonly used biometric) or as an adjective, as in “a biometric system uses integrated hardware and software to conduct identification or verification.”6
Biometrics have long been touted as a possible solution to the problems and vulnerabilities of other commonly used methods of authentication and identification. They represent sophisticated versions of the traditional means of identification, such as a guard allowing access to a user whom the guard recognizes by sight. Biometrics commonly are defined as automated methods of recognition/verification/identification of individuals based on some measurable physiological or behavioral characteristics, such as fingerprints, hand geometry, facial shape, iris pattern, voice, signature, and the like.
Whereas identification (ID) badges and keys authenticate the user based on something the user possesses, and passwords/personal identification numbers (PINs) authenticate the user based on what the user knows, biometrics allows authentication and identity verification based on who the user is. Because biometric methodologies of authentication actually base identification on physiological or behavioral “pieces” of the user, biometrics represents the only form of authentication that directly authenticates the user.
Biometrics have a number of other obvious advantages over other commonly used authentication methods. Unlike an ID badge or a USB key, one cannot easily lose or misplace a fingerprint or other biometric measures. Likewise, unlike the case with passwords and PINs, one does not need to remember and one is not subject to forgetting a physiological or behavioral characteristic. Although biometric measures can be compromised, in general, a biometric is much more difficult to manipulate by stealing, forging, sharing, or destroying than other commonly used authentication tools. Biometrics also provide considerable convenience, as opposed to the hassle of memorizing dozens of passwords.
Although the initial costs are quite high, the implementation of biometric systems typically results in much lower administrative costs than other access methodologies due to fewer calls to the help desk for technical support to reset passwords, no need to issue replacement ID badges, and so on. For these and other reasons, biometrics are viewed as providing better security, increased efficiency, and more reliable identity assurance than other commonly used methods of authentication/identification based on what a user possesses or what a user knows.
In theory, almost any human physiological and/or behavioral characteristic can be used as a biometric measure. However, to fit within a viable, potentially accurate, and practical biometric system, the biometric used should also satisfy four other requirements offered by Jain7 and Bolle, Cornell, Pankanti, Ratha, and Senior:8
- Universality. Every person should have the biometric characteristic.
- Uniqueness. No two persons should be the same in terms of the biometric characteristic. Jain proposed the somewhat lower standard of distinctiveness, defined as “any two persons would be sufficiently different in terms of the characteristic.”9
- Permanence. The biometric should be relatively invariant over a significant period of time.
- Collectability. The biometric characteristic should lend itself to quantitative measurement in a practical manner.
Bolle, Connell, Pankanti, Ratha, and Senior argued that the biometric should also have a fifth attribute: acceptability, defined as “the particular user population and the public in general should have no strong objections to the measuring/collection of the biometric.”10 Jain argued that a practical biometric system should consider two other attributes: (1) performance, which is “the achievable recognition accuracy and speed, the resources required to achieve the desired performance, as well as the operational and environmental factors that affect the performance,” and (2) circumvention, which “reflects how easily the system can be fooled using fraudulent methods.”11
29.3.3 Identification, Authentication, and Verification.
In this chapter, we describe the process of providing a user identifier (ID) and data to bind the user of the ID with that ID as authentication. However, the process of establishing whether the proffered combination of ID and authentication data reliably confirms the identity of the user is called verification.
Identification systems answer the question: Whom do you claim to be? and involve establishing a person's claimed identity. Verification systems answer the question: Are you who you claim to be? and involve confirming or denying an individual's claimed identity using knowledge, tokens, biological characteristics, or behavioral patterns that are reliably tied and restricted to the authorized user of the ID.
In verification systems, the user claims an identity (e.g., a Windows username, a given name, an ID number) and provides biometric data (e.g., finger scan), which are compared against the user's enrolled biometric data. The answer returned by the system is that of “match” or “no match.”
Biometric verification systems are referred to as 1:1 (one-to-one) systems because, while they may contain thousands or even millions of biometric records, they are “always predicated on a user's biometric data being matched against only his or her own enrolled biometric data.”12 Biometric verification systems do not provide “pure” biometric authentication because they rely on a combination of authentication modes—specifically biometric data compared against a unique identifier (e.g., ID number, user name).
Biometric identification systems, however, can be viewed as pure biometric authentication because identification is based only on biometric measurements. Whereas verification is referred to as a 1:1 system, identification systems often are referred to as 1:N (one-to-N or one-to-many) systems because an individual's biometric information is compared against multiple (N) records. Verification systems return an answer of match or no match; identification systems, however, return an identity (e.g., a name or ID number) as an answer.
Identification systems are further divided into “positive” (designed to find a match for a user's biometric information in a database of biometric information, such as tracking individuals in a prison release program) and “negative” (designed to ensure that a person's biometric information is not present in the database, such as preventing people from enrolling more than once in large-scale benefits programs). Although biometric identification systems are generally classified as 1:many applications, a scaled-back version of identification known as 1:few, a system that focuses on identification search against a small number of users is sometimes deployed.
Biometric identification systems are more difficult to design and implement than verification systems because of the extensive biometric database search capabilities needed. Additionally, identification systems are more subject to error than verification systems, because many more matches must be conducted, matches that increase the opportunity for error. Verification systems are overall much faster (often rendering a match/no match decision within less than a second) and more accurate than identification systems. Verification systems, as opposed to identification systems, predominate in private sector applications, particularly for computer and network security applications. Verification systems also predominate in applications designed to authenticate rights-to-access to buildings and rooms, although sometimes identification systems are also deployed in high-security environments. Identification systems are often found in public sector applications, such as law enforcement (e.g., parole and prison administration, forensics, etc.), large-scale public benefits programs, intelligence, and national security applications.
29.3.4 Application Areas.
Although there are many potential applications for biometrics, the primary ones can be divided into four categories: systems security (logical access systems), facilities access (physical access systems), ensuring the uniqueness of individuals, and public identification systems. The common thread among these four applications is that they all rely on individuals enrolled in the systems. The significance of whether individuals are enrolled or not enrolled will be explained in Section 29.3.5.
29.3.4.1 Security (Logical Access Systems).
Logical access systems “monitor, restrict, or grant access to data or information.”13 Examples include accessing a computer or network or accessing an account. In these systems, biometrics replace or complement PINs, passwords, and tokens. The volume and value of electronic commerce plus the value of sensitive and personal information transported and/or stored on networks and computers make the use of biometrics to secure logical access a much more robust industry segment than physical security.
The use of biometric technologies for logical access control is still very much in its infancy. The most common biometric approach is to use fingerprint readers, either with a stand-alone USB reader or with a reader embedded in a laptop. Manufacturers are beginning to incorporate the Trusted Platform Module (TPM) chip in new laptops to support a variety of cryptographic applications. In combination with biometric devices like fingerprint readers, the TPM chip can allow applications like Microsoft's BitLocker to apply biometric access control to encrypted volumes on a hard drive. Such technologies are still new enough to suffer problems with backward compatibility and intervendor support, but they offer the promise of much more secure logical access.
29.3.4.2 Facilities Access (Physical Access Systems).
Facilities access systems “monitor, restrict, or grant movement of a person or object into or out of a specific area.”14 In these systems, biometrics replace or complement keys, access cards, or security cards, allowing authorized users access to rooms, vaults, and other secure areas. Physical access systems often are deployed in major public infrastructure settings, such as airports, security checkpoints, and border facilities, in order to monitor and restrict movements of unauthorized or suspicious persons. In addition to entry to secure rooms, physical access systems, when applied in business settings, include time-and-attendance systems by combining access to a location with an audit of when the authentication occurred.
Biometric technologies have been in use for physical access control for some time but still represent a range of possible implementations, from stand-alone fingerprint-reading door locks to complete systems with central storage of biometric templates, logging, and power failure protection. Selecting a system from within such a wide product range must fit into the overall security stance of the facility, particularly in regard to the storage of templates. In a simple stand-alone door system, for example, fingerprint templates would be stored in or near the locking device, and the system might not have any logging features. Unless coupled with surveillance and intrusion alarms anticipating physical compromise, these devices are more appropriate for lower security applications, such as storage facilities where physical key access might not be preventing theft. More centrally connected systems, however, offer greater integration into overall monitoring and control of access but suffer from communication and power issues as they push templates across a network. Selecting a product that interacts well with other parts of the overall access control system is crucial.
29.3.4.3 Ensuring the Uniqueness of Individuals.
Uniqueness biometric identification systems typically focus on preventing double enrollment in programs or applications, such as a social benefits program. The main use of this application occurs in the public sector, although similar systems could be implemented to prevent double enrollment in employee benefits programs.
29.3.4.4 Public Identification Systems.
A final biometric application of note is its use to identify criminals and/or terrorists. Criminals and terrorists can wear disguises, acquire fake documents, and change their names, but biometric data are fairly difficult to forge. In 2004, the United States Department of Defense started the Automated Biometric Identification System (ABIS), which collects biometric data on Iraqi insurgents in a manner compatible with IAFIS. This allows for identification of known repeat offenders and wanted persons. Soldiers also use the Biometric Automated Toolset (BAT) developed by the Army's Language Technology Office to identify persons on the scene of bombing attacks. Anyone present in the area can be cross-referenced with an existing database of insurgents. The BAT is also used to enroll and identify members of the Iraqi army. Although biometric systems hold much promise, it is also important to understand the limitations of current technology.
29.3.5 Data Acquisition and Presentation.
As Jain explains, “A biometric system is essentially a pattern recognition system that operates by acquiring biometric data from an individual, extracting a feature set from the acquired data, and comparing this feature set against the template set in the database.”15 The starting point for the biometric system is enrollment: A user's biometric data are initially collected and processed into a template, the form in which they are then stored for ongoing use. As Woodward, Orlans, and Higgins explain, “Templates are not raw data or the scanned images of a biometric sample, but rather they are an accumulation of the distinctive features extracted by the biometric system.”16 Liu and Silverman describe the template as “a mathematical representation of biometric data. A template can vary in size from 9 bytes for hand geometry to several thousand bytes for facial recognition.”17 Templates are proprietary to each vendor and technology with little or no interoperability between systems. This lack of interoperability is attractive from a privacy perspective but unattractive from the perspective of cost effectiveness and the prospective implementer who is concerned about committing significant investment to a single nonstandardized technology.
The term “presentation” refers to the process by which a user provides biometric data to an acquisition device by looking in the direction of a camera, placing a finger on a pad or sensor, or some other specified physiological exam. For purposes of verification or identification, the user presents biometric data, which are then processed and converted to a template. This template is an extraction of distinctive features and is not adequate for the reconstruction of the original biometric data. The scanned template is then matched against the stored enrollment template(s). Each time a user makes a presentation, a new template is created and matched. It is important to note, especially from the perspective of privacy concerns, that biometric systems do not store raw biometric data; instead they use the data for template creation and, in most cases, discard the biometric data. The biometric system's match/no-match decisions are based on a score, which is “a number indicating the degree of similarity or correlation resulting from the comparison of enrollment and verification templates.”18 Like the templates, the scoring system is based on proprietary algorithms; there is no standard system.
29.4 TYPES OF BIOMETRIC TECHNOLOGIES.
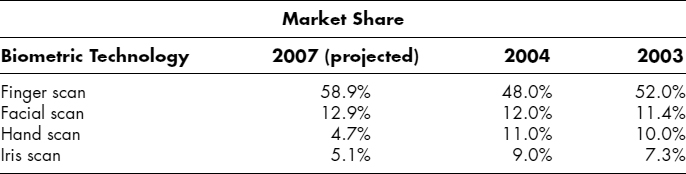
As previously noted, biometrics generally can be grouped into two categories: physiological and behavioral. The International Biometric Group provides data on comparative market share of various biometric technologies. The IBG data focus on market share from commercial and government applications. The top four biometric technologies are all from the physiological category (see Exhibit 29.1).
The fifth most widely deployed biometric technology came from the behavioral category: voice scan, with a projected 3.2 percent share in 2007, down from a 6.0 percent share in 2004 and 4.1 percent in 2003.19 Each of these five biometrics is discussed in detail in the next sections.
29.4.1 Finger Scan.
Finger scan or fingerprint technology is by far the most widely deployed biometric technology. Finger scan's number-one status as a biometric is maintained even if the extensive use of fingerprinting by law enforcement agencies is excluded. The type of fingerprinting employed in commercial biometric systems differs from the one used in law enforcement. In most commercially available biometric applications, the station provides only for the scan of a single finger on one hand, whereas law enforcement agencies often rely on full sets of fingerprints. In addition to being the most widely used biometric, fingerprinting is also one of the oldest and most well researched biometric technologies. Because it is a widely used, well-documented, and mature technology, costs for the deployment of finger-scan-based technologies are relatively low. Single-quantity pricing for a workstation version with associated software can be as low as $150; server versions are currently priced as low as $50 per unit.
EXHIBIT 29.1 Comparative Market Share of Biometric Technologies
Sources: (1) Market share data from International Biometric Group, Biometrics Market and Industry Report 2007–2012 (January 2007). Retrieved February 4, 2007, from www.biometricgroup.com/reports/public/market_report.html.
(2) International Biometric Group, Biometrics Market and Industry Report 2004–2008 (2005). Retrieved June 4, 2005, from www.biometricgroup.com/reports/public/marke_report.html.
(3) J. McHale, “Biometrics: The Body's Keys,” Military & Aerospace Electronics 14, No. 12 (2003): 17–23.
The strengths of finger scan are one of the principal reasons for its popularity and include:
- Wide use.
- Mature technology.
- Low cost.
- High ease of use. (Very little training is required to place a finger on a finger pad.)
- Ergonomic design. (Comfortable to use for most users.)
- Low error incidence. (False match rates are extremely low; crossover error rate is lower than voice scan and facial recognition, higher than hand geometry and iris scan.)
- Fast transaction times. (In most systems, authentication takes less than a second.)
- Capacity to be deployed in a wide range of environments (e.g., on workstations, doorways, indoors/outdoors).
- Ability to increase accuracy levels by enrolling multiple fingers.
- Can provide identification with a high level of accuracy (if properly configured to include multiple enrolled fingers) in addition to verification.
Despite its multiple strengths, finger scan is not without significant weaknesses. As Chirillo and Blaul note, some of this technology's weaknesses stem from the same factors that lend it its strengths. “Because fingerprint technology is one of the oldest and most well-known technologies, a good amount of information is publicly available on how to defeat it.”20 A number of ways exist to foil finger scans and produce a false match (false accept), including the use of a dummy finger constructed of latex or other material, manipulation of the scanner so as to raise the latent print of the person who used the scanner previously, and even use of an actual finger that is no longer attached to a body. (Most finger scanners cannot discriminate between live and dead tissue.) Because of these factors, the security levels of finger scans are not actually as impressive as the low error rates seem to indicate. It should be noted that countermeasures could be taken to overcome the vulnerability of finger scans to fraud. For example, enrolling additional fingers makes fraud more difficult. To reduce the chance that the system will be foiled by synthetic or dismembered fingers, thermal and/or moisture scanners can be added to the sensors to detect finger temperature and moisture levels that would indicate the vitality of the finger.
Other weaknesses include:
- A scanner requires frequent maintenance because screens/sensors tend to retain an obstructing buildup of user skin oil and residue.
- Performance can deteriorate over time, both because of aging of the users (and wearing away of fingertips) and because of the need for system maintenance.
- Finger-scan biometrics are obviously not appropriate for users with missing hands or hand disabilities.
- Performance levels deteriorate among users who have hand tremors because the presentation of biometric data will be distorted.
- Performance levels also deteriorate when users' fingers are either overly dry (a certain amount of normal skin moisture is needed for an accurate reading) or overly moist or oily (as from too much hand lotion).
- There is a small but significant failure to enroll (FTE) rate even among a population with hands and without disabilities. The FTE rate for finger scans is estimated at 2 to 10 percent and is attributed to persons with genetically indistinct prints, scarred fingers, dry skin, and fingerprints worn down by age and/or manual labor.
Perhaps the biggest weakness of finger scan, however, has nothing to do with the accuracy and reliability of the technology. Instead, it relates to user acceptance. Because of the association of finger scans with law enforcement and criminality, often such scans are not readily accepted by users who dislike the technology's “taint” with forensic applications and who may worry that finger-scan biometric data will be used for other purposes.
According to Chirillo and Blaul, “Another reason fingerprint technology is not highly accepted is that it may require individuals to share or touch the same device that others touch.”21
29.4.2 Facial Scan/Recognition.
Bolle, Connell, Pankanti, Ratha, and Senior note that “face appearance is a particularly compelling biometric because it is one used every day by nearly everyone as the primary means for recognizing other humans. Because of its naturalness, face recognition is more acceptable than other biometrics.”22 However, user acceptance of facial scans drops significantly when users discover that it has been used covertly. As Imparato observes, “Of all the biometric technologies currently in use, face recognition is arguably the most controversial.”23 Like finger scans, face recognition relies on the identification of unknown face images by comparison to a database of (known) face templates. Face recognition is used overtly in access control where it is used for one-to-one identification. This application yields relatively high performance because the environment is highly controlled and input data are predictable. Face recognition may also be used covertly in surveillance where it is used to locate people in crowds (one to many), albeit with mixed results. For example, the city of Virginia Beach, Virginia, has employed a face recognition system to identify known (preenrolled) felons for over five years but has yet to identify a single criminal. A variety of facial recognition technologies, ranging from single image, video sequence, three-dimensional image, near infrared, to facial thermograms, are available.
Facial recognition offers these benefits:
- It has the capacity to leverage existing image acquisition equipment, such as digital cameras, Web, video, and the like.
- Because facial recognition is a software-based technology, it is often unnecessary to purchase new hardware, especially given the number of Closed Circuit Television (CCTV) and surveillance cameras in broad use.
- The lack of need for specialized hardware can help keep the cost of this technology down, assuming that high software costs do not counterbalance the savings from the hardware.
- It is the only biometric capable of identification at a distance without the subject's cooperation or even awareness.
- It is easy to use. All that is required is that the user (or target) look at the camera.
- It does not require the user to touch any device (a major objection for some users with finger scans and hand scans).
- When deployed in verification situations, facial scans have extremely low failure-to-enroll rates. (Unlike fingerprints, human faces are almost always distinctive.)
- They are capable of enrolling static images (e.g., photographs on driver's licenses), a factor that makes it possible to implement very large scale enrollments at a relatively low cost and in a brief amount of time.
Facial recognition systems have a number of serious weaknesses too. The predominant weakness (which derives from a combination of the technology's other weaknesses) is the low accuracy and high error rate of this biometric. Whether deployed covertly or overtly, facial recognition has the lowest accuracy rate among all five top biometrics.
Evidence of the technology's low accuracy rate comes from a study at Palm Beach (Florida) International Airport that showed that the system failed more than 50 percent of the time to match the 15 employees who had enrolled in the database for a trial run. Out of 958 pass-throughs, the system matched the employees' faces just 455 times. Some studies suggest that accuracy improvements can be made in facial recognition systems, but these improvements will come at a very high cost. For example, a facial recognition software package from Visionics FaceIt resulted in impressively low error rates, as long as lighting conditions were perfect. The software costs $30,000 for a three-camera system.
Other weaknesses include:
- False matches (false accepts) routinely occur in the case of twins, andmost systems are insensitive enough for someone skillful at disguise and impersonation to trick the system into a false match.
- More likely than false matches, however, are false nonmatches (false rejects), which can occur as a result of facial expressions; changes in hairstyle, makeup, facial hair, significant changes in body weight, eyeglasses, and age-related facial changes.
- The acquisition environment can have a dramatic impact on facial recognition system accuracy. In particular, lighting, either too bright or too dim, can dramatically increase the error rate.
- The perceived threat to privacy. Overtly deployed facial recognition technologies (e.g., used for identification and access) are generally judged relatively unobtrusive and meet with a high level of user acceptance. However, covertly deployed systems, such as those used for surveillance, pose significant threats to privacy. This threat is generally viewed as much more serious than that posed by the other top biometrics.
29.4.3 Hand Geometry Scan.
Hand geometry scans refer not to handprints or to any analogy of fingerprints but rather to the geometric structure (or geometric invariants) of the human hand. Nanavati, Thieme, and Nanavati explain that “hand-scan technology utilizes the distinctive aspects of the hand—in particular, the height and width of the back of the hand and fingers—to verify the identity of individuals.”24 The leading hardware maker for this technology, Recognition Systems, Inc. (RSI), has a basic hand scanner that takes upward of 90 measurements from three to four enrollments to create a user template that includes length, width, and thickness, plus surface area of the hand and fingers. Newer systems include temperature-sensing mechanisms to ensure “live” subjects. All the components of a hand scan system (acquisition hardware, matching software, storage components) reside within a standalone device. Hand scans are a well-established biometric technology (they have been in widespread use since the 1970s), but compared to other leading biometrics, hand scans tend to be much more limited in their range of applications. Hand scans are used exclusively for verification rather than for identification because the hand measurements are not distinctive or specific enough to allow for identification applications. For this reason, hand scans are used mostly for physical access and time-and-attendance applications. In the latter case, they are used as a way to eliminate the problem of “buddy-punching” whereby one employee punches in or out for a coworker who is not present.
Hand scan technology has changed very little since it was first introduced over 30 years ago, so its strengths and weaknesses are well established. The principal strengths of the hand scan include:
- Operates in very challenging environments. (The equipment is typically unaffected by light, dust, moisture, or temperature.)
- Established and reliable technology.
- Ease of use. (Users simply stick their hand in the unit; placement matters little.)
- Resistance to fraud compared to other biometrics. (It would be difficult and time consuming to substitute a fake sample.)
- Small template size (as low as 9 bytes; much smaller than other biometrics, allowing for storage of thousands of templates in a single unit).
- Based on a relatively stable physiological characteristic.
- High level of user acceptance and lack of attached stigma.
Problems reported in using hand scans include:
- Limited accuracy (which in turn limits its use to verification not identification). The relatively low accuracy of hand scan (higher than facial recognition and behavioral biometrics but lower than finger and iris scans) is a result of the general lack of physical variety expressed in the hand as well as the relatively small number of features measured by hand scan.
- Comparatively large form factor (This limits the technology's deployment in computer-oriented applications that require hardware with a smaller footprint.)
- Some people resent forced contact with possibly unclean surfaces.
- Ergonomic design limits its use by some populations (e.g., the disabled).
- Comparatively high cost. At $1,500 to $2,000 per unit, hand scanners cost significantly more than finger scanners. Nanavati, Thieme, and Nanavati note that the higher price of hand scanners “may be attributable to the lack of competition in the hand scan market.”25
29.4.4 Iris Scan.
Iris scan technology uses the unique pattern formed by the iris—the colored part of the eye bounded by the pupil and the sclera—to identify or verify the identity of individuals. The iris pattern is unique, for even in the same individual, no two irises are alike. The uniqueness of iris patterns has been likened to that of multilayered snowflakes. The unique aspects of the iris make it an ideal biometric for high-security applications; enrolling both irises from the same individual can enhance the level of security. In addition to high-security physical access applications, iris scan technology has been used in automated teller machines (ATMs) and banking kiosks.
The most important strength of iris biometrics is its accuracy, the most critical weakness of facial scanning. Of all the leading biometrics, iris technology has the lowest error rate and the highest level of overall accuracy. Other strengths of this biometric include:
- Ability to be used both for verification and for identification.
- Stability of its biometric characteristics over a lifetime.
- Relative difficulty to fake or spoof because it is an internal biometric.
- The fact that the iris is minimally subject to outside influences when compared to biometrics like fingerprints and faces.
The major weaknesses of the iris biometric concern user perceptions and problems in the user-technology interface. Other weaknesses include:
- Acquisition of the image requires moderate training and attentiveness: Users must stand still and look straight into the scanner with eyes open and unblinking.
- Users often report some physical discomfort with the use of eye-based technology, although less so than with retina scanning technology.
- Anecdotal reports also suggest a fairly high level of user psychological resistance to iris-scanning technology, with some users believing that the scanner will lead to eye damage.
- Can be adversely affected by lighting and other environmental conditions (although not to the extent of facial scanning).
- In some cases eyewear adversely affects performance (although many iris devices can scan people wearing glasses or contact lenses).
- Although the iris is a relatively stable biometric, it is affected by aging and disease.
- Relies on proprietary hardware and software technologies.
- Costs tend to be high compared to finger scanning, hand scanning, and many facial recognition systems.
On the other hand, the per unit cost of the leading hardware/software combination technology has dropped to as low as $300 per seat, still higher than finger scans but significantly lower than the over $5,000-per-seat price seen a few years ago.
29.4.5 Voice Recognition.
Voice recognition biometrics “utilizes the distinctive aspects of the voice to verify the identity of individuals.”26 Voice recognition generally is classified as a behavioral biometric, although it actually combines elements of behavioral and physiological biometrics: “The shape of the vocal tract determines to a large degree how a voice sounds, a user's behavior determines what is spoken and in what fashion.”27 Stated somewhat differently, “voice is a behavioral biometric but is dependent on underlying physical traits, which govern the type of speech signals we are able and likely to utter.”28 Because of comparatively low levels of accuracy and considerable user variability in voice dynamics, this biometric generally is used only for verification, not identification. Commonly deployed voice recognition systems can be divided into two types: text-dependent systems (the speaker is prompted to say a specific thing) and text-independent systems (the authentication system processes any utterances of the speaker), which provide a higher level of security because they are more difficult to spoof and provide better accuracy than text-dependent systems.
Strengths of voice recognition include:
- Capacity to leverage existing telephony infrastructure (as well as built-in computer microphones).
- Low cost when existing infrastructure is used.
- Ease of use.
- Interface with speech recognition and verbal passwords.
- High level of user acceptance. (This biometric does not suffer from the negative perceptions associated with all of the other leading biometrics.)
Weaknesses of voice recognition include:
- More susceptible to replay attacks than other biometrics.
- Accuracy levels are low compared to iris scanning, finger scans, and hand scans.
- Accuracy levels are negatively affected by ambient noise and low-quality capture devices.
- Accuracy, security, and reliability are challenged by individual variations in voice, such as speaking softly or loudly, hoarseness or nasality because of a cold, and so on.
- The stability of the biometric is affected by illness, aging, and other user behaviors including smoking.
29.4.6 Other Biometric Technologies.
The five major biometric technologies just discussed collectively comprise the vast majority of biometric technology under deployment. The only other biometric technologies that even register on market share breakdowns are two of the behavioral type: signature scan (2.4 percent share in 2003) and keystroke scan (0.3 percent share in 2003). Although both of these behavioral biometrics are well accepted (signature scanning more so than keystroke scanning), their usefulness is limited by their lack of accuracy.
Other behavioral biometrics under investigation include gait and lip motion. One physiological biometric that has received considerable attention because of its high accuracy and security rates is retinal scanning. However, most analysts believe that the problems associated with retinal scanning (lack of user acceptance, high cost, difficult and painful acquisition process) outweigh any advantages to this biometric. The consensus seems to be that iris scanning has replaced retinal scanning as the eye scanning biometric of choice.
The use of DNA as a biometric identifier has also been investigated, although it has significant weaknesses including the fact that DNA in body tissues (e.g., epithelial cells) can be obtained surreptitiously and transferred easily for nefarious purposes whereas the official methods of collection (e.g., taking blood samples) are relatively intrusive.
Other physiological biometrics that may prove useful in the future include body odor, skin reflectance, and ear shape.
29.5 TYPES OF ERRORS AND SYSTEM METRICS.
All types of identification and authentication systems suffer from two types of errors: false accepts and false rejects.
29.5.1 False Accept.
Also known as false match, false positive, or type 1 error, false accept is the likelihood, expressed as a percentage, that an imposter will be matched to a valid user's biometric. In some systems, such as those that attempt to secure entry to a weapons facility, a bank vault, or a high-level system administrator account, the false match/false accept rate is the most important metric to watch. In other systems, such as a facial recognition system deployed by a casino in an effort to spot card counters, a high level of false matches may be tolerated.
29.5.2 False Reject.
Also known as false nonmatch, false negative, or type 2 error, false reject is the probability that “a user's template will be incorrectly judged to not match his or her enrollment template.”29 False nonmatches typically result in the user being locked out of the system. These false nonmatches can occur because of changes in a user's biometric data, changes in how the biometric data is presented, and/or changes in the environment. Biometric systems are generally more susceptible to false rejects than they are to false accepts.
29.5.3 Crossover Error Rate.
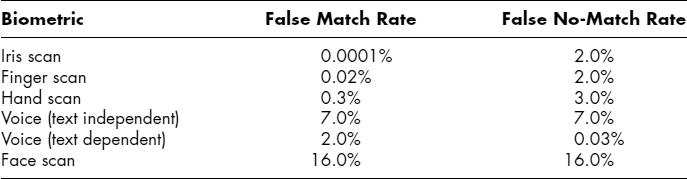
An important metric in biometric systems is the crossover error rate (CER), also known as the equal error rate (EER). This useful metric is the intersection of the false accept and false reject rates. In general, a lower CER indicates the biometric device is more accurate and reliable than another biometric device with a higher CER. Exhibit 29.2 provides a summary of benchmark test-based accuracy/error rates for the five most prevalent biometric technologies. Each biometric technology is rank-ordered from most accurate to least accurate based on CER.
EXHIBIT 29.2 Accuracy/Error Rates of Leading Biometric Technologies
Source: Based on data contained in L. O'Gorman, “Comparing Passwords, Tokens, and Biometrics for User Authentication,” Proceedings of the IEEE 91, no. 12 (2003): 2032.
29.5.4 Failure to Enroll.
Another critical metric in biometric systems is the failure to enroll (FTE). As Ashbourn explains, FTE refers to “a situation whereupon an individual is unable to enroll their biometric in order to create a template of suitable quality for subsequent automated operation.”30 Common reasons for failure to enroll include physical disability and a user whose physiological/behavioral characteristics are less distinctive than average. Nanavati, Thieme, and Nanavati observe that failure to enroll can be a major problem in “internal, employee-facing deployments” in which “high FTE rates are directly linked to increased security risks and increased system costs.”31 A final important metric is the “transaction time.” Transaction time refers to “a theoretical time taken to match the live template against a reference sample.”32
29.6 DISADVANTAGES AND PROBLEMS
29.6.1 General Considerations.
Despite the many advantages over other commonly used authentication systems, the implementation of biometric authentication controls carries a number of risks and disadvantages. Even the most accurate biometric system is not perfect, and errors will occur. The error rates and the types of errors will vary with specific biometrics deployed and the circumstances of deployment. Certain types of errors, such as false matches, may pose fundamental, critical risks to organizational security. Other types of errors—failure to enroll, false nonmatch—may reduce organizational productivity and efficiency and increase costs. Organizations planning biometrics implementation will need to consider the acceptable error threshold. In any event, organizations deploying biometric authentication systems must not be lulled into a belief that they are invulnerable to errors and/or fraud. Certain biometric systems (e.g., iris scanning) are fairly impervious to fraud, while others (especially behavior-based systems) are much more susceptible to it. Facial scanning systems can be foiled with clothing, makeup, eyeglasses, and/or changes in hairstyle. Even relatively stable physiology-based biometrics like fingerprint scans can be defrauded with the use of rubber or gelatin fingers. Matsumoto outlines a gummy finger approach designed to fool even those countermeasures mentioned in section 29.4.1.33 The protein used has a similar galvanic response to flesh and, since it is very thin and attached to a live finger, has the correct temperature. In some cases, blowing warm air over the scanner may even raise the latent print of the intruder's predecessor.
The deployment of commonly used authentication systems (i.e., ID badges, passwords, etc.) requires relatively little training, although one could argue that better training on the development and use of passwords would improve security. This limited need for training is not the case with most of the most commonly used biometric systems. Both systems administrators and users need instruction and training to ensure smooth operation of the system. Some biometric systems are exquisitely sensitive to intra- and interuser variation in presentation and performance. Their effectiveness becomes substantially compromised and error rates substantially increase in cases of significant variation and/or irregular presentation. A related problem concerns user acceptance of the biometric system. Some users may object to the deployment of biometrics due to concerns over privacy and intrusiveness. In other instances, users may object to the deployment of biometrics and avoid optimal interface with the system because of safety and/or health concerns, general fears, and/or cultural and religious beliefs. For example, some individuals may be concerned that biometric systems that require them to touch a finger pad or hand pad will unnecessarily expose them to germs and place them at risk for illness. Some users may fear that eye scans will damage their eyes. Other users may object to eye scans on the basis that the eyes are the window to the soul. Anderson notes that some persons may object to the use of biometrics due to a personal interpretation of religious doctrine.34 Notwithstanding users' beliefs and perceptions about the biometric system, in many cases features or elements related to the users and/or the operating environment will influence the successful implementation and effectiveness of the system.
29.6.2 Health and Disability Considerations.
Individuals with arthritis and/or certain other disabilities and physical limitations may be unable to enroll in systems and subsequently, to align themselves physically in an optimal position with respect to biometric sensors. For example, users with severe hand arthritis may be unable to place their hand firmly as required on the hand geometry sensor, and users with migraines and associated photophobia may find it physically too uncomfortable to look straight into the light sensor for the iris scan. Some disabled people may have to be excluded from biometric systems altogether. Some relatively minor disabilities, such as a slight tremor, may compromise a legitimate user's ability to gain access through certain biometric systems. Variations in physical size can also influence system accuracy. An iris scanner positioned for a standard height range may fail to capture images of either very short or very tall individuals, or in some cases an individual's hands or fingers may be either too large or too small to be read accurately in a hand or finger scanner. Likewise, individuals with neck and back problems may find it difficult to use some biometric devices, depending on the kind of positioning required. Systems that rely on behavioral biometrics such as voice or signature are particularly vulnerable to variations and irregularities in user characteristics. For example, users who speak too softly, too loudly, or too rapidly may cause system errors. Minor changes in users' health can affect some biometric readings. Excessive skin moisture or lack of skin moisture can impact finger scans.
Although one of the ideal properties of a biometric is its universality, in reality not everyone has the characteristic or has it to the same degree. For example, some people are born without distinct fingerprints. In other cases, users may have lost the distinctiveness of their fingerprints because of years of manual labor, use of certain chemicals, scarring, or the aging process. Anderson notes that “people with dark-colored eyes and large pupils give poorer iris codes.”35 Certain eye diseases and metabolic conditions may also reduce or negate the efficacy of eye scan authentication. Age has a significant impact on the user-biometric-system interface. Definite physiological changes are associated with the aging process and can result in poor template matching with the live biometric. In this case, reenrollment may be needed. Fingerprints are affected by the aging process as the skin becomes drier and more brittle; voice patterns change in tonal quality over time; and facial shape or appearance may shift with age. Overall, the acceptability of a biometric system will be lessened if there is the impression that implementation of the system discriminates against, or has an otherwise adverse impact on, the disabled, the ill, ethnic minorities, the elderly, and other protected or traditionally disadvantaged groups of users. Organizations must ensure compliance with the Americans with Disabilities Act when implementing biometric authentication systems. Compliance may involve providing alternative methods of authentication to those affected.
29.6.3 Environmental and Cultural Considerations.
A broad range of factors in the operating environment can also impact the effectiveness and acceptability of biometric systems. User-related cultural, social, and behavioral factors can influence system performance. For instance, the accuracy of facial scans can be compromised by users' changes in hairstyle, facial hair, and headwear as well as by changes in an individual's physical appearance because of significant weight gain or loss. The accuracy of voice/speech recognition systems is affected by the distance between the scanner and the user as well as by the volume of speech. Fingerprint recognition is impeded in cases when users' skin is too dry, whether the condition arises as a result of aging, skin disease, environmental factors, or occupation-related factors, such as frequent hand washing among healthcare professionals. Factors in the surrounding ambient environment may also affect the accuracy of the biometric system. Ambient lighting will influence accuracy and error rate in facial scans and, to a lesser extent, in iris scans. Noise levels can impede the effectiveness of voice recognition systems. Humidity and air temperature can affect the accuracy of fingerprint and hand scans.
29.6.4 Cost Considerations.
Although the cost of biometric system implementation has fallen dramatically in the past few years, it is still a major barrier for many organizations. Costs vary significantly depending on the type of system. Recent reports suggest that newer fingerprint scanners can be purchased for as little as $50 per unit; voice recognition systems can cost in excess of $50,000. However, even the least expensive biometrics systems are likely to cost more than simpler versions of traditional authentication systems. Experts estimate minimum costs, including hardware and software, at $200 or so per user and upward of $150,000 for corporate-wide protection in a medium-sized business. Compounding the cost issues are problems related to the lack of clear standards and the lack of clear interoperability between various biometric authentication systems.
Many of the problems and difficulties with biometrics systems are likely to be corrected or significantly mitigated with technological improvements, better user and administrator training, and good control of environmental conditions. In other cases, problems can be overcome or ameliorated with the use of countermeasures, such as combining different types of biometrics, combining biometrics with traditional authentication systems, and so on. Two major concerns that will continue to loom large and deserve closer examination are biometric identity theft and user privacy.
29.6.5 Attacks on Biometric Systems.
Although biometrics are much less vulnerable to attack than other authentication controls, they are not immune to fraud. Moreover, when a biometric identity is stolen or spoofed, it creates a much bigger problem than that created by the theft of an ID badge, USB key, or password because a biometric cannot be simply canceled and replaced. One of the principal advantages to using biometrics for authentication is their invariability over time. Consequently, when an imposter or intruder defrauds a biometric authentication system and creates a false match error, the entire biometric security system is defrauded and the individual authorized user's biometric integrity is compromised. Likewise, Prabhakar, Pankanti, and Jain note, “One disadvantage of biometrics is that they cannot be easily revoked. If a biometric is ever compromised, it is compromised forever.”36
A number of analysts believe that the ultimate solution to the problem of biometric identity theft lies in the development of “cancelable biometrics.” Researchers at IBM have developed a prototype for the cancelable biometric that incorporates a repeatable distortion of the biometric. Similar in theory to the use of public and private keys for encryption, a unique distortion of the biometric is introduced at each enrollment. Therefore, if a user's biometric is compromised, only the one system is defrauded, not every system in which the user is enrolled.
29.6.6 Privacy Concerns.
The use of biometric authentication controls raises significant privacy concerns, particularly in comparison to conventional authentication methods like passwords and ID badges. User objections to biometrics are often based on privacy concerns, sometimes articulated in terms of the user's sense of the intrusiveness of the biometric system. Anecdotal reports suggest that public perceptions of intrusiveness vary among different biometrics and in how biometrics are implemented. With regard to the latter, Nanavati, Thieme, and Nanavati37 report that there is a greater risk of privacy invasiveness when:
- Deployment is covert (users are not aware of the system's operation) versus overt.
- The system is mandatory versus opt-in.
- The system is used for identification rather than verification.
- It is deployed for an indefinite duration versus fixed duration.
- It is deployed in the public versus the private sector.
- The user is interfacing with the system as an employee/citizen versus an individual/customer.
- An institution, not the user, owns the biometric information.
- The biometric data are stored in a template database versus the user's personal storage.
- The system stores identifiable biometric data versus templates.
A vivid example of the public's lack of acceptance of the covert use of biometric systems comes from the 2001 Super Bowl and the uproar that ensued after the Tampa Police Department deployed facial scanning technology for the purpose of picking out criminal suspects from the audience. In contrast, in the aftermath of the 2001 attacks on the World Trade Center and the Pentagon, there has been fairly widespread public acceptance of the use of facial scanning at airports in the United States.
Users generally view behavior-based biometrics, such as voice recognition and signature verification, as less intrusive and less privacy-threatening than physiology-based biometrics. Facial scanning is viewed as having a high potential for privacy invasion because of the capacity to deploy it without the user's knowledge and participation. Finger scans may be viewed as intrusive and privacy-invasive because of their association with law enforcement functions. The level of intrusiveness of the scanning technique appears to affect users' perception of privacy invasion, with iris scanning provoking more privacy objections than hand scanning. Civil libertarians and users also raise privacy objections over biometric systems that have the potential to uncover additional information about the user beyond the biometric identity. For example, finger scans, because of their capacity to be linked to large law enforcement databases of fingerprints, could be used to reveal information about the user's criminal background. Iris scans have the capacity to reveal confidential medical/health information about the user. Probably one of the most troubling privacy-related aspects of biometrics is the potential for large-scale linkage between biometric systems and the use of biometric data to facilitate large-scale national ID programs. Even though employers may design a biometric system for purely in-house use in order to facilitate verification of employee identities on corporate networks, federal regulations and laws such as the USA PATRIOT Act may eventually compel employers to surrender employees' private biometric data to government authorities.
In summary, the major privacy concerns associated with biometric deployments include:
- Users' loss of anonymity and autonomy
- Risk of unauthorized use of biometric information and/or unauthorized collection of biometric information
- Unnecessary collection of biometric information
- Unauthorized disclosure of biometric information to others
- Systematic reduction of users' reasonable expectation of privacy
- Potential for misuse on the part of overzealous or corrupt government agents
Many of these concerns can be generally lumped under the heading of “function creep” or “mission creep” wherein biometric systems designed for user authentication may, over time, be used for purposes not originally intended. An example of “mission creep” is the use of Social Security Numbers (SSNs) for identification. The original Social Security cards were stamped “Not for Identification.” However, many organizations (including the Internal Revenue Service) use SSNs for identification purposes.
Notwithstanding the privacy risks, supporters of biometric authentication systems argue that, properly deployed and with adequate best practice controls, biometric systems actually can function to enhance and protect privacy. Woodward, Orlans, and Higgins point out that “several newly developed biometric technologies use an individual's physical characteristics to construct a digital code for the individual without storing the actual physical characteristics,” thus creating a sort of biometric encryption that can be used to protect the privacy of an individual's financial, medical, or other data.38 Nanavati, Thieme, and Nanavati argue that “privacy-sympathetic” biometric systems can be designed.39 Such systems would:
- Have limited system scope.
- Eschew use of biometrics as a unique identifier.
- Limit retention of biometric information.
- Limit storage of identifiable biometric data.
- Limit collection and storage of extraneous information, while including “opt-out” provisions for users.
- Enable anonymous enrollment and verification.
- Provide means of correcting and accessing biometric-related information.
- Limit system access.
- Use security tools and access policies to protect biometric information.
- Make provisions for third-party audits.
- Disclose the system purpose and objective.
- Disclose enrollment, verification, and identification processes.
- Disclose policies and protections in place to ensure privacy of biometric information.
- Disclose provisions for system termination.40
In contrast to this view, Alterman argues that the deployment of biometric systems and the use of biometric data for identification and verification are ethically questionable because they always entail a violation of privacy and autonomy. Alterman finds “something disturbing about the generalized use of biometric identification apart from the standard data privacy issue.”41 He maintains that biometric data “has inherent moral value”42 but does not go so far as to argue against any deployment of biometric identification or verification systems. Rather, he maintains that they must be judiciously implemented and deployed only with due consideration to users' privacy concerns.
29.7 RECENT TRENDS IN BIOMETRIC AUTHENTICATION
29.7.1 Government Advances in Biometric Authentication.
Although private sector organizations are increasingly adopting biometric technologies for their authentication needs, the government (public) sector has led investment in biometrics. The 2001 terrorist attacks on the World Trade Center and the Pentagon, and the ensuing USA PATRIOT Act, have encouraged increasing government commitment to biometric technologies. The Department of Defense (DoD), the Department of Homeland Security (DHS), the Immigration and Naturalization Service, and the Department of Transportation are the government agencies most involved in the deployment of biometrics technologies. The DoD's Common Access Card program involves putting biometric technology on a smart ID card. The DoD also recently acquired 1,300 U.are.U. fingerprint43 recognition systems in order to enhance network security at workstations in its offices in the Washington, DC, metropolitan area. The US-VISIT program under the DHS is another government program that incorporates biometrics (including face and fingerprint) into a smart ID card. Another DHS program, the Transportation Worker Identity Credential, incorporates biometric information in an ID card.
29.7.2 Face Scanning at Airports and Casinos.
After the 2001 terrorist attacks on the World Trade Center and the Pentagon, most of the nation's airports moved to incorporate face-scanning technologies into their security systems. Most studies of the effectiveness of these systems, however, have revealed their high error rates and low accuracy rates.
Casinos utilize facial scanning systems to identify professional “advantage players” and cheats. Although this is largely unregulated in the United States, Canadian casinos must notify players regarding the use of such systems. Casinos share data on professionals and cheats. One firm has networked 125 casino surveillance operators in the United States, Canada, Puerto Rico, Aruba, and the Bahamas and provides real-time alerts and other information useful in identifying suspicious players. However, it is unclear as to how such systems may be affected by international law. Article 12 of the United Nations Universal Declaration of Human Rights guarantees that “[n]o one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honor and reputation. Everyone has the right to the protection of the law against such interference or attacks.”44 Whether this system amounts to arbitrary interference or an attack on one's honor has not been addressed by the courts, but a case clearly could be made that covert use of such systems does so. A best practice for any surveillance system is informed consent. Organizations should clearly post notifications about the use of surveillance systems in order to protect themselves from legal challenges.
29.7.3 Increased Deployment in the Financial Industry.
Usually slow to embrace new technologies, the financial industry is one of the leaders in the adoption of biometric authentication controls. Current deployments range from fingerprint scanners securing computer networks for brokers, to facial recognition systems at ATMs to iris scanning for high-security access points. International Biometric Group projected that U.S. financial services firms would spend $672 million in 2007 for various biometric deployments. One of the biggest deployments to date has been United Bankers' Bancorporation (UBB) adoption of U.are.U, a fingerprint recognition system that allows UBB customers to automatically log onto UBB's Web site with finger scans versus passwords. UBB also adopted a fingerprint authentication system for its employees. Wells Fargo, Bloomberg Financial, and Janus Capital Management are other well-known financial firms that have adopted biometric authentication systems for employees and/or customers. Although some financial institutions have selected voice, iris, or facial-scan-based systems, most seem to be choosing finger-scan systems.
29.7.4 Biometrics in the Healthcare Industry.
Spurred in part by new regulations that require healthcare institutions to ensure the privacy and security of patient records, healthcare companies have also been at the forefront in the adoption of biometric authentication. Among the major healthcare organizations that have moved to biometric authentication is the Mayo Clinic, which adopted a fingerprint ID system in 2002. The majority of healthcare institutions that have adopted biometric authentication systems have selected finger-scan ID systems. However, deployment of these systems in healthcare organizations has not met with the same success as seen in the financial services industry. Issues involving the potential transmission of illness via physical contact with the fingerprint scanner are not trivial. Additionally, error rates have been higher and accuracy rates much lower than expected. The major reason behind the high incidence of errors appears to be the particulars of the healthcare environment, especially the characteristics of the hands of the doctors, nurses, and other healthcare workers using these systems. Specifically, system performance appears to be undermined by the chronically dry hands of these workers, a condition resulting from frequent hand washing and the use of alcohol-based hand sanitizers. Another problem has been the resistance to using the fingerprint technology by both nurses and doctors, who feel that it involves a privacy intrusion.
29.7.5 Increased Deployment of Time and Attendance Systems.
An increasing number of companies across many different industries are deploying biometric-based time-and-attendance systems. A shift from the past practice is in the increased use of biometric attendance and tracking systems for white-collar workers. Previously the focus was on blue-collar factory workers. Although some employers are using the traditional hand-scanning systems, there appears to be a shift toward the use of finger-scanning time-and-attendance systems. This shift seems to be related to the more competitive pricing structure for the finger-scanning systems.
EXHIBIT 29.3 Comparison of Leading Biometric Technologies
29.8 SUMMARY AND RECOMMENDATIONS.
There is no universal “best” biometric authentication system. Each of the five leading biometric technologies carries specific advantages and disadvantages. Some biometric technologies are more appropriate for certain applications and environments than their counterparts. An organization in the midst of evaluating potential biometrics authentication implementation must recognize that there will be trade-offs in any selection, such as cost for accuracy, privacy versus user acceptance, and so on, and there are not yet any universal decision factors for selecting a particular biometric technology for a specific application. There is, however, substantial research into many of the advantages and disadvantages of biometrics. Exhibit 29.3 provides a summary comparison of the features of the five leading biometric technologies discussed in this chapter. The features, shown in the extreme left column, were excerpted from various researcher efforts, and the rankings represent an amalgam of the rankings found in the literature.
Although biometric authentication systems promise cost savings and higher levels of security for organizations, they are not a panacea. Many factors affect how well or poorly biometric authentication controls will perform in a given organizational environment. Included among these factors are the users, the administration, the environment, the infrastructure, the budget, the communication system, and the existing security needs. Although many biometric technologies are capable of operating as stand-alone systems, in reality their accuracy and performance levels would be greatly improved by combining them with more conventional authentication methods, such as passwords and keys. Such multifactor systems offer greater security and reliability.
In selecting a biometric authentication system and preparing for an implementation, organizations should focus on the user-technology interface and the conditions in the operational environment that may influence the technology's performance. For example, the healthcare industry's unreflective embrace of finger scan technology illustrates the dangers of failing to heed environmental realities. It is important that organizations consider not only the practical impediments to effective implementation but also the potential psychological impediments, such as user fears about the technology. Ethically, the organization also has the obligation to consider carefully the extent to which the implementation of biometric authentication compromises the privacy rights of users. In making this assessment, management must take into account the possibility that the organization may be compelled to release employees' biometric-related information to government authorities.
A review of the recent literature (2000–2007) on the adoption of biometric technologies in organizations revealed almost no research regarding the factors influencing the decision to implement biometric access technologies. Research into this area could help explain why organizations are reluctant to implement biometric authentication controls. It could also help information technology and security decision makers to determine what aspects of biometric security technologies are of concern to them and accordingly recommend appropriate security solutions for their organizations. Security technology companies can also benefit from this research by knowing what is important to their customer base while introducing new IT security products and/or technologies.
29.9 FURTHER READING
Kaine, A. K. “The Impact of Facial Recognition Systems on Business Practices within an Operational Setting.” 25th International Conference Information Technology Interfaces, June 16–19, 2003, Cavtat, Croatia, pp. 315–320.
Hamilton, D. P. “Workplace Security; Read My Lips: Are Biometric Systems the Security Solution of the Future?” Wall Street Journal, September 29, 2003.
Jain, A. K, P. Flynn, and A. A. Ross, eds. Handbook of Biometrics. New York: Springer, 2007.
NIST Biometrics Resource Center Web site. www.itl.nist.gov/div893/biometrics/.
Ratha, N. K., Connell, J. H., & Bolle, R. M. “Enhanced Security and Privacy in Biometrics-Based Authentication Systems.” IBM Systems Journal 40, No. 3 (2001): 614–634.
Ratha, N., and R. Bolle, eds. Automatic Fingerprint Recognition Systems. New York: Springer, 2003.
Ross, A. A., K. Nandakumar, and A. K. Jain. Handbook of Multibiometrics. New York: Springer, 2006.
Vacca, J. R. Biometric Technologies and Verification Systems. Boston: Butterworth-Heinemann, 2007.
29.10 NOTES
1. J. Boroshok, “Pointing the Finger at Biometrics.” SearchSecurity.com, January 14, 205; retrieved February 4, 2007 from http://searchsecurity.techtarget.com/originalContent/0,289142,sid14_gci1044805,00.html.
2. International Biometric Group, “Biometrics Market and Industry Report 2004–2008” (2005); retrieved June 4, 2005 from www.biometricgroup.com/reports/public/market_report.html.
3. International Biometric Group, “Biometrics Market and Industry Report 2007–2012” (January 2007); retrieved February 4, 2007 from www.biometricgroup.com/reports/public/market_report.html.
4. G. V. Hulme, “Slow Acceptance for Biometrics,” Information Week, February 10, 2003, p. 57.
5. J. Chirillo and S. Blaul, Implementing Biometric Security (Indianapolis, IN: John Wiley & Sons, 2003), p. 2.
6. S. Nanavati, M. Thieme, and R. Nanavati, Biometrics: Identity Verification in a Networked World (Hoboken, NJ: John Wiley & Sons, 2002), p. 11.
7. A. K. Jain, “Biometric Recognition: How Do I Know Who You Are,” IEEE Symposia (2004): 3–5.
8. R. M. Bolle, J. H. Connell, S. Pankanti, N. K. Ratha, & A. W. Senior, Guide to Biometrics (New York: Springer-Verlag, 2004).
9. Jain, “Biometric Recognition,” p. 3.
10. Bolle et al., Guide to Biometrics, p. 6.
11. Jain, “Biometric Recognition,” p. 3.
12. Nanavati et al., Biometrics, p. 12.
13. Nanavati et al., Biometrics, p. 14.
14. Nanavati et al., Biometrics, p. 14.
15. Jain, “Biometric Recognition,” p. 3.
16. J. D. Woodward, N. M. Orlans, and P. T. Higgins, Biometrics (New York: McGraw-Hill/Osborne, 2003), p. 37.
17. S. Liu and M. Silverman, “A Practical Guide to Biometric Security Technology,” IT Pro (January/February 2001): 20.
18. Nanavati et al., Biometrics, p. 20.
19. International Biometric Group, “Biometrics Market and Industry Report 2004–2008.” See also International Biometric Group, “Biometrics Market and Industry Report 2007–2012”; J. McHale, “Biometrics: The Body's Keys,” Military & Aerospace Electronics, 14, No. 12 (December 2003): 17–23.
20. Chirillo and Blaul, Implementing Biometric Security, p. 21.
21. Chirillo and Blaul, Implementing Biometric Security, p. 24.
22. Bolle et al., Guide to Biometrics, p. 36.
23. N. Imparato, “Does Face Recognition Have a Future?” Intelligent Enterprise 5, No. 7 (April 2002): 20.
24. Nanavati et al., Biometrics, p. 99.
25. Nanavati et al., Biometrics, p. 99.
26. Nanavati et al., Biometrics, p. 87.
27. Nanavati et al., Biometrics, p. 87.
28. Bolle et al., Guide to Biometrics. p. 40.
29. Nanavati et al., Biometrics, p. 27.
30. J. Ashbourn, Practical Biometrics: From Aspiration to Implementation (London: Springer-Verlag, 2003), p. 10.
31. Nanavati et al., Biometrics, p. 35.
32. Ashbourn, Practical Biometrics, p. 10.
33. T. Matsumoto, “Importance of Open Discussion on Adversarial Analyses for Mobile Security Technologies: A Case Study for User Identification,” May 14, 2002; retrieved March 17, 2007 from http://crypto.csail.mit.edu/classes/6.857/papers/gummy-slides.pdf.
34. R. J. Anderson, Security Engineering: A Guide to Building Dependable Distributed Systems (Hoboken, NJ: John Wiley & Sons, 2001).
35. Anderson, Security Engineering, p. 274.
36. S. Prabhakar, S. Pankanti, and A. K. Jain, “Biometric Recognition: Security and Privacy Concerns,” IEEE Security & Privacy (March/April 2003): 39.
37. Nanavati et al., Biometrics.
38. Woodward et al., Biometrics. p. 211.
39. Nanavati et al., Biometrics.
40. Nanavati et al., Biometrics.
41. A. Alterman, “‘A Piece of Yourself’: Ethical Issues in Biometric Identification,” Ethics and Information Technology 5, No. 3 (2003): 143.
42. Alterman, “‘A Piece of Yourself,’” p. 145.
43. www.digitalpersona.com/products/UPOS.php
44. United Nations, “Universal Declaration of Human Rights,” December 10, 1948; retrieved March 17, 2007 from www.un.org/Overview/rights.html.