PREFACE
Computers are an integral part of our economic, social, professional, governmental, and military infrastructures. They have become necessities in virtually every area of modern life, but their vulnerability is of increasing concern. Computer-based systems are constantly under threats of inadvertent error and acts of nature as well as those attributable to unethical, immoral, and criminal activities. It is the purpose of this Computer Security Handbook to provide guidance in recognizing these threats, eliminating them where possible and, if not, then to lessen any losses attributable to them.
This Handbook will be most valuable to those directly responsible for computer, network, or information security as well as those who must design, install, and maintain secure systems. It will be equally important to those managers whose operating functions can be affected by breaches in security and to those executives who are responsible for protecting the assets that have been entrusted to them.
With the advent of desktop, laptop, and handheld computers, and with the vast international networks that interconnect them, the nature and extent of threats to computer security have grown almost beyond measure. In order to encompass this unprecedented expansion, the Computer Security Handbook has grown apace.
When the first edition of the Handbook was published, its entire focus was on main-frame computers, the only type then in widespread use. The second edition recognized the advent of small computers, while the third edition placed increased emphasis on PCs and networks.
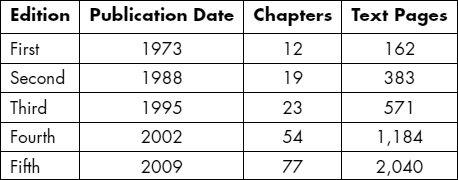
The fourth edition of the Computer Security Handbook gave almost equal attention to mainframes and microcomputers.
This fifth edition has been as great a step forward as the fourth. With 76 chapters and the work of 86 authors, we have increased coverage in both breadth and depth. We now cover all 10 domains of the Common Body of Knowledge defined by the International Information Systems Security Certification Consortium (ISC)2:
- Security Management Practices: Chapters 10, 12, 13, 14, 15, 19, 10, 31, 43, 44, 45, 46, 47, 48, 49, 50, 51, 54, 55, 62, 63, 64, 65, 66, 67, 68, 74, 75, 76
- Security Architecture and Models: Chapters 1, 2, 3, 8, 9, 24, 26, 27, 51
- Access Control Systems and Methodology: Chapters 15, 19, 28, 29, 32
- Application Development Security: Chapters 13, 19, 21, 30, 38, 39, 52, 53
- Operations Security: Chapters 13, 14, 15, 19, 21, 24, 36, 40, 47, 53, 57
- Physical Security: Chapters 4, 13, 15, 19, 22, 23, 28, 29
- Cryptography: Chapters 7, 32, 37, 42
- Telecomm, Networks, and Internet Security: Chapters 4, 5, 6, 13, 14, 15, 16, 17, 18, 20, 21, 24, 25, 26, 27, 30, 31, 32, 33, 34, 35, 41, 48
- Business Continuity Planning: Chapters 22, 23, 56, 57, 58, 59, 60
- Law, Investigations, and Ethics: Chapters 11, 12, 13, 31, 42, 61, 63, 64, 69, 70, 71, 72, 73
In addition to updating every chapter of the fourth edition, we have added chapters on:
- History of Computer Crime
- Hardware Elements of Security
- Data Communications and Information Security
- Network Topologies, Protocols, and Design
- Encryption
- Mathematical Models of Information Security
- The Dangerous Information Technology Insider: Psychological Characteristics and Career Patterns
- Social Engineering and Low-Tech Attacks
- Spam, Phishing, and Trojans: Attacks Meant to Fool
- Biometric Authentication
- Web Monitoring and Content Filtering
- Virtual Private Networks and Secure Remote Access
- 802.11 Wireless LAN Security
- Securing VoIP
- Securing P2P, IM, SMS, and Collaboration Tools
- Securing Stored Data
- Writing Secure Code
- Managing Software Patches and Vulnerabilities
- U.S. Legal and Regulatory Security Issues
- The Role of the CISO
- Developing Classification Policies for Data
- Outsourcing and Security
- Expert Witnesses and the Daubert Challenge
- Professional Certification and Training in Information Assurance
- Undergraduate and Graduate Education in Information Assurance
- European Graduate Work in Information Assurance and the Bologna Declaration
We have continued our practice from the fourth edition of inviting a security luminary to write the final chapter, “The Future of Information Assurance.” We are pleased to include a stellar contribution from Dr. Peter G. Neumann in this edition.
SEYMOUR BOSWORTH
Senior Editor
January 2009
