CHAPTER 33
802.11 WIRELESS LAN SECURITY
Gary L. Tagg
33.1.2 Background and Uses of Wireless LANs
33.2 802.11 ARCHITECTURE AND PRODUCT TYPES
33.2.2 802.11 Network Architecture
33.2.4 Wireless LAN Product Types
33.2.5 Benefits of Wireless Switch/Access Controller Architecture
33.2.6 Security Benefits of Wireless Switch/Access Controller Architecture
33.3 WIRELESS LAN SECURITY THREATS
33.3.1 Comparison between Wired and Wireless
33.3.2 Specific Threats Enabled by Wireless LANs
33.4 ORIGINAL 802.11 SECURITY FUNCTIONALITY
33.4.1 Security Functionality Overview
33.4.2 Connecting to a Wireless Network and Authentication
33.4.3 Defending against the WEP Vulnerability
33.5.1 Structure of the Robust Security Network
33.5.3 Security Association Management
33.5.4 RSNA Key Hierarchy and Management
33.5.5 Temporal Key Integrity Protocol
33.5.6 Counter Mode/CBC-MAC Protocol (CCMP)
33.5.7 Remaining Implementation Issues
33.5.8 Wi-Fi Alliance's WPA and WPA2 Standards
802.11 SECURITY AUDITING TOOLS
33.6.8 Commercial Wireless Auditing Tools
33.8 APPENDIX 33A–802.11 STANDARDS
33.8.1 802.11 and 802.11b: MAC and Physical Layer Specifications
33.8.2 802.11a: 5GHz High-Speed Physical Layer
33.8.3 802.11d: 802.11 Additional Regulatory Domains
33.8.4 802.11e: MAC Enhancements for Quality of Service
33.8.5 802.11F: Inter–Access Point Protocol
33.8.6 802.11g: Higher-Rate Extension to 802.11b
33.8.7 802.11h: Spectrum Managed 802.11a
33.8.8 802.11i: MAC Security Enhancements
33.8.9 802.11j: 4.9Ghz–5GHz Operation in Japan
33.8.10 802.11k: Radio Resource Measurement Enhancements
33.8.12 802.11n: Enhancements for Higher Throughput
33.8.13 802.11p: Wireless Access for the Vehicular Environment (WAVE)
33.8.14 802.11r: Fast Roaming/Fast BSS Transition
33.8.15 802.11s: ESS Mesh Networking
33.8.16 802.11T: Wireless Performance Prediction (WPP)
33.8.17 802.11u: Interworking with External Networks
33.8.18 802.11v: Wireless Network Management
33.8.19 802.11w: Protected Management Frames
33.8.20 802.11y: 3650–3700MHz Operation in the United States
33.8.21 802.1x: Port-Based Network Access Control
33.8.22 Wi-Fi Protected Access (WPA) and WPA2
33.9 APPENDIX 33B: ABBREVIATIONS, TERMINOLOGY, AND DEFINITIONS
33.1 INTRODUCTION.
Corporations and home users have mass adopted IEEE 802.11 as the protocol for wireless local area networks. These networks have benefits over traditional wired networks, such as mobility, flexibility, rapid deployment, and cost reduction. However, as with any networking technology, it creates new opportunities for unauthorized individuals to access the networks and the information carried over them.
The purpose of this chapter is to introduce wireless LAN technologies, the issues, and ways to address them. Reasons driving the adoption of wireless LANs derive from:
- The 802.11 architecture and product types
- The threats to information presented by wireless LAN technology, and how they compare to other networking threats, such as the Internet
- The security functionality provided by the original 802.11 standard, the security weaknesses, and how to mitigate them
- The security functionality provided by the 802.11i security standard, which was developed to address issues with the original standards
The chapter also provides an overview of the open source and commercial tools that hackers use to break into wireless networks: tools that are useful for people wanting to do their own security auditing.
33.1.1 Scope.
The scope of this chapter is the security of ANSI/IEEE standard 802.11 wireless LANs. This chapter does not consider any other wireless systems, such as mobile telephone networks, or other wireless standards, such as HomeRF, Bluetooth, WiMax, or HiperLAN.
33.1.2 Background and Uses of Wireless LANs.
Business has been using wireless LANs for well over 10 years. However, to begin with, the market was fairly small and the technologies proprietary. In the late 1990s and early 2000s, the groundwork was laid for the mass adoption of wireless LANs (WLANs). The starting point was the publication of ANSI/IEEE standard 802.11, which provided a baseline design enabling manufacturers to develop interoperable products at lower costs. The publication of the 802.11b standard in 1999 increased WLAN bandwidth similar to that of traditional Ethernet LANs, making it a possible technical replacement. Following that were the 802.11a and 802.11g standards, increasing bandwidth to 54Mb/s. Work is currently under way on 802.11n, which will provide a throughput of up to 600Mb/s.
33.1.2.1 Business Uses of Wireless LANs.
The main requirements for implementing wireless networks are mobility and cost reduction. Objectives include to:
- Enable staff to access network information via mobile terminals as they move around the office campus. Two examples are warehouse and hospital staff.
- Enable staff to access the network from meeting rooms for both client-facing and internal meetings.
- Enable external consultants and staff from other offices to connect to the network when on site.
- Enable staff to get away from their desks (e.g., to another office, to a rest area, or to an internal cafe) and still be able to access the network.
- Enable managers to take a laptop to the desk of a staff member and show what is on the screen.
- Reduce mobile telecommunications costs by implementing Voice over wireless LANS (VoWLANs).
Public wireless networks (known as hot spots) are now available in city centers, hotels, airports, railway stations, pubs, service stations, restaurants, and coffee shops. These hot spots provide a high-speed connection to the Internet, allowing staff to utilize this normally wasted time between meetings or when waiting for airplanes or public transport. Typical uses include access to and other resources on the corporate LAN, along with general research by surfing the Internet.
Matthew Gast says that a major advantage of wireless LANS is flexibility and rapid deployment.1 A network that runs out of physical LAN connections in a particular area can be a major issue. Running cables is expensive, time consuming, and may require conduits to be fitted within walls, as well as other construction tasks. This can be a big problem for older buildings that have not been designed for today's environment.
Historical buildings often have restrictions on building alterations. It may not be possible to gain authorization for the construction necessary to lay a cable infrastructure. Wireless LANs can overcome this entire issue of having to lay cables. Once the wireless network is built, additional users are easy to add; just plug in a card, install the software, and configure it.
Costs can also be saved by not having to install physical network links between buildings separated by a road, river, railway tracks, or even a city block. With an uninterrupted line of sight between the two buildings, a wireless network link can be set up.
33.1.2.2 Home Use of Wireless LANs.
In recent years, the use of wireless LAN networks has exploded in the home market. The reasons for this are:
- Households increasingly have access to more than one computer because of work laptops being taken home, and the falling price of computers enables families to upgrade.
- The availability of broadband Internet has encouraged people to network their home computers so that all of them can access the Internet.
- Households often have to locate their computers away from the telephone point, for example, in a bedroom or dining room. This means that a cable has to be run across the floor to access the Internet. Broadband modems with built-in wireless LANs are available, removing the need for the cable.
- WLAN equipment is now affordable. A typical PCMCIA or USB wireless LAN card can now be purchased at a fraction of the original cost. The major advantage of wireless LANs is the ease of installation, because no cables have to be run to the remote computers.
33.2 802.11 ARCHITECTURE AND PRODUCT TYPES.
This section provides a brief overview of 802.11 wireless LAN technologies defined in the 802.11 standard, along with available product types and their architectures. A more detailed overview is available in RFC41182 with further information available in additional references.3
33.2.1 802.11 Components.
The core components of the architecture as defined in the 802.11 standard are:
- Stations (Sta). Any device that contains an 802.11 medium access control (MAC) and physical layer (PHY) interface to the wireless medium (i.e., a PC with a wireless LAN card and software).
- Access points (AP). A station that bridges other stations to the distribution system (DS).
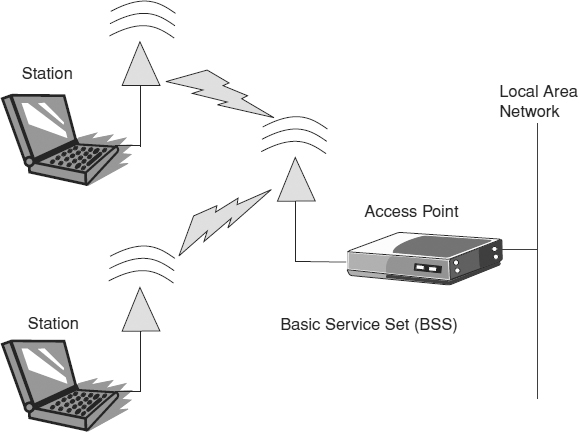
- Basic service sets (BSS). One or more stations communicating with a single access point. These types of networks are also called infrastructure networks. (See Exhibit 33.1.)
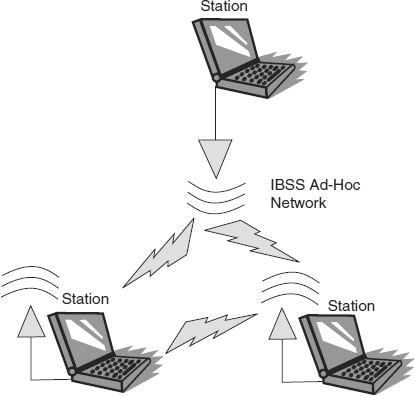
- Independent basic service set (IBSS). An ad hoc network where stations communicate directly with one another without an access point. (See Exhibit 33.2.)
EXHIBIT 33.1 Basic Service Set Network
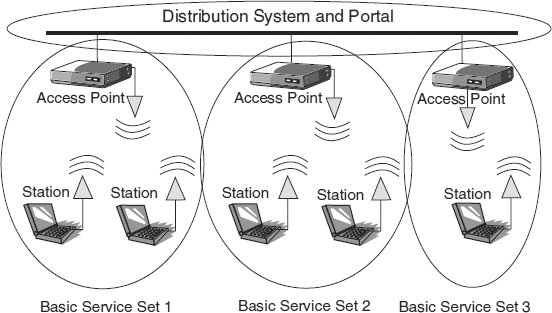
- Extended service set (ESS). A set of one or more interconnected basic service sets (BSSs) and integrated local area networks (LANS) that appears as a single BSS to stations. (See Exhibit 33.3.)
- Distribution system (DS) and portal. The distribution system interconnects access points to create an extended service set. The portal is a logical component that integrates the 802.11 architecture with the wired LAN. (See Exhibit 33.3.)
EXHIBIT 33.2 Independent Basic Service Set (Ad Hoc) Network
EXHIBIT 33.3 802.11 Architecture–Extended Service Set
33.2.2 802.11 Network Architecture.
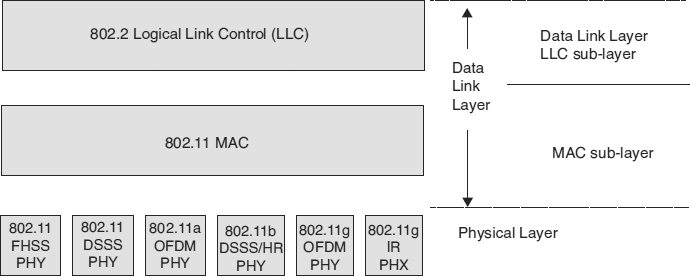
In relation to the OSI 7 layer network reference model,4 802.11 provide services at the physical layer and the data link layer. Within these two layers, 802.11 is itself structured into three layers:
- A physical layer (the radio interfaces for transmission and reception)
- The medium access control (MAC) sublayer, which is a set of services to enable data to be exchanged between devices
- An 802.2 logical link control (LLC) sublayer
The use of the 802.2 LLC allows the rest of the world to see 802.11 devices as Ethernet devices and use the same Ethernet MAC address range as their hardwired cousins. This architecture is shown in Exhibit 33.4.
33.2.3 802.11 Physical Layer.
The 802.11 standards currently define six different physical interfaces with a seventh in development:
- 802.11 Infrared. This is a 2 Mb/s infrared system, but due to line-of-sight limitations, very little development has occurred with this interface.5
EXHIBIT 33.4 802.11 Network Architecture
- 802.11 FHSS. This is a 2 Mb/s radio link using the frequency-hopping spread spectrum (FHSS) algorithm in the 2.4 GHz band. FHSS works by defining 79 1 MHz-wide channels and sending bursts of data over a number of channels, with the system hopping between channels in a defined way.
- 802.11 DSSS. This is a 2 Mb/s radio link using the direct sequence spread spectrum (DSSS) technique in the 2.4 GHz band. The standard defines fourteen 5 Mhz-wide DSSS channels. DSSS works by spreading data over a 22 MHz-wide channel. This technique allows for greater transmission rates than FHSS but means that access points need to be five channels apart to avoid interference, reducing the number of effective channels from 14 to 3.6
- 802.11b DSSS. This is a higher-rate DSSS radio link in the 2.4 GHz band with a maximum throughput of 11 Mb/s.
- 802.11a OFDM. 802.11a uses the 5 GHz frequency band and an encoding technique called orthogonal frequency division multiplexing (OFDM) to increase throughput to 54 Mb/s.
- 802.11g. This standard implements the OFDM encoding in the 2.4 GHz band to increase throughput to 54 Mb/s and is the standard product available in 2008.
- 802.11n. This is a standard under development to increase the throughput up to 600 Mb/s. A number of “pre-n” products are available on the market.
33.2.4 Wireless LAN Product Types.
There are three main types of wireless LAN products available today. The first is where the access point contains all the functionality, including security. These are generally known as fat access points and are used by home and small office and home office (SOHO) users who have a need for a small number of highly functional access points (AP). These “fat” access points were the architecture designed for the original 802.11 standard.
The 802.11 standard is designed primarily for fat access point architecture where all the functionality is in the AP. However, with an extensive WLAN deployment, setting up and managing these access points becomes a major issue. To address this issue, vendors created an alternative architecture based upon light-weight access points (LWAP) and wireless switches. An LWAP is primarily an 802.11 radio that sends all received packets to the wireless switch, which has most of the functionality of traditional fat APs as well as the task of managing the LWAPs. The actual split of functionality between the LWAP and the wireless switch varies depending on the product.
Each wireless switch vendor developed its own proprietary technologies, so the Internet Engineering Task Force (IETF) set up a working group called the Control and Provisioning of Wireless Access Points (CAPWAP).7 The first deliverable from the group was a problem definition statement, or request for comment, published as RFC3390.8 It then published an architecture taxonomy as RFC41189 that defined the architectures and standard terminology. For example, LWAPs are called “wireless termination points” (WTPs) and wireless switches are called “access controllers” (ACs).
They then extended the scope of the working group to develop the CAPWAP protocol so that different vendors' WTPs and ACs could be interoperable.10 This protocol is based on the LWAPP with the communications secured by the Datagram Transport Layer Security Protocol (DTLS).11 DTLS is essentially TLS optimized for user datagram-based protocols such as UDP.
The third classes of WLAN products are known as wireless mesh networks. Traditional fat and LWAPs are all physically connected to the wired network. With wireless mesh networks, the access points connect to each other via the wireless medium and route through each other to get back to services on the wired network. This significantly reduces the cabling required and the deployment costs for wireless networks. In the case of historical buildings, network coverage could be provided without having to install a wired network backbone at all. To establish standards for WLAN meshes, the IEEE has set up the 802.11s working group.
33.2.5 Benefits of Wireless Switch/Access Controller Architecture.
For enterprise use, the LWAP/wireless switch architecture should be the architecture of choice. As well as security benefits that are covered later, it has these general networking benefits:
- Ease of deployment and management. The LWAP just needs to know where to find the wireless switch. Once the LWAP is authenticated, all configuration information is downloaded to it. Wireless switch products also include site survey functionality to help you choose where access points should be located before installation. In the event of a denial-of-service attack, the inbuilt wireless intrusion detection system and intrusion prevention system (IDS/IPS) functionality will notify of the attack, reducing the work required to identify the problem.
- RF management. A wireless LAN switch is in a position to notice holes in net-work coverage, or a clash with a neighboring network, and alter LWAP channels, transmitting power dynamically, to avoid these clashes and fill in for lost or failed access points.
- Load-balancing users. Wireless clients generally associate with access points having the strongest signal. A wireless switch can direct the user to associate with an alternative access point, if the strongest is already highly loaded.
- Simplified guest networking. Guests can be associated with a guest network to provide access to specific services such as Internet access
- Fast roaming. Being a central point, the wireless switch is able to coordinate the roaming between LWAPs. This speeds up the roaming process, enabling the use of real-time applications such as voice and video.
- Layer 3 roaming. Across a big campus, LWAPs themselves will be connected to many different subnets. However, through tunneling mechanisms, the wireless switch can provide a single subnet across the entire wireless network. This speeds up the roaming process and enables a client to retain a single IP address across the entire campus, further supporting the use of voice and video.
- Quality of service (QOS). A wireless LAN switch is able to prioritize traffic centrally, to provide the appropriate QOS for real-time traffic.
- Unification of wired and wireless. The use of LWAPs and wireless switches enables the wireless network to be integrated into the wired network, reducing management overheads.
- AAA accounting. As all traffic passes through a wireless switch, it is able to collate accurate metrics for usage based charging of the wireless network.12
- Integration with older non–wired equivalent privacy (WPA/WPA2) equipment. Some vendors provide virtual private network (VPN) functionality in the wireless switch to provide secure connectivity for older equipment that does not have WPA/WPA2 support and integrate it into the enterprise wireless network.
33.2.6 Security Benefits of Wireless Switch/Access Controller Architecture.
Wireless switch/access controller architectures have these security benefits:
- User and device authentication. Wireless switches are able to authenticate both the user and the device to ensure that only authorized users on approved computers can access the network.
- Access control. Based on the user's identity, the wireless switch can assign the user to a specific VLAN that has access to just the resources required. For example, warehouse staff could be given access to only the inventory management and order processing systems. Guests could be given access to the Internet or public product pages.
- Inbuilt wireless intrusion detection and prevention functionality. The wireless switches are able to analyze every wireless packet received by all LWAPs, allowing the switches to provide intrusion detection and prevention functionality. This ranges from denial-of-service attacks to active attacks as well as to the detection of rogue access points and clients.
- Rogue access point detection. The LWAP can also be used to scan the environment for unauthorized access points. The location of the device can be found by triangulating it from signals received at different access points. Some products can take active measures to remove rogue access points from the network.
33.3 WIRELESS LAN SECURITY THREATS.
This section lists the generic security threats to both wired and wireless networks. It then describes the specific threats made possible by wireless LANs.
Hassler,13 the Dennings,14 and ISO 7498-215 identified these types of threats to networked systems:
- Eavesdropping. Intercepting and reading messages intended for other users. Wireless LANs use radio waves to transport the data between wireless stations and the network. These radio waves easily pass through building walls and onto the street. All that is required to eavesdrop on a wireless LAN is a laptop or handheld PC, a wireless LAN card, and some free software available via the Internet.
- Masquerading. Sending or receiving messages using another user's identity. An attacker who can eavesdrop on a wireless network may be able to collect enough information to join the network and to masquerade as a legitimate user.
- Message modification. The content of messages captured by an attacker could be altered without it being detected and then retransmitted, resulting in an unauthorized effect.
- Replaying. Repeating all or part of a message to produce an unauthorized effect. For example, replaying an authentication message to obtain unauthorized access to a network.
- Denial of service (DoS). Preventing authorized users of a network from accessing resources. For example, flooding the networkwith messages to prevent others from using it. See Chapter 18 of this Handbook for a full description.
- Exploiting flaws in design, implementation, or operation. Using program bugs, poor security system design, and configuration errors to achieve unauthorized access to resources. This topic is covered in depth in Section 33.4.
- Cracking. Using brute force or dictionary attacks to guess the values of passwords, or of cryptographic keys. See Chapter 7 for a detailed discussion.
33.3.1 Comparison between Wired and Wireless.
A vulnerability is a weakness that allows a threat to occur to an asset, such as data traveling over a network. For threats to occur on a wired network, the vulnerability is a physical connection to the network. With the mass adoption of the Internet, a physical connection is available to all Internet-connected networks. This allows people from outside the physically controlled areas of an organization's buildings to access the corporate LAN.
Wireless networks also extend the network outside of the physical controls of the building because the network uses radio waves to transport data. People such as Rob Flickenger16 and Peter Shipley17 have demonstrated how high-gain aerials, such as parabolic dishes, can enable stations to connect to a wireless LAN over a distance of 25 miles. Several people have modified household satellite television aerials to achieve similar results.18 But there is no need now to home-build high-gain aerials as they are available commercially for as little as U.S. $69.19 Because wireless networks and the Internet allow people to connect to the network from outside the physically controlled area of an organization's buildings, it might be of interest to compare the vulnerabilities presented by the two technologies and how they control these vulnerabilities.
Corporate networks are usually protected from the Internet by firewalls and technologies such as virtual private networks. These technologies control access to the resources that are available via the Internet, using tokens and strong cryptography to authenticate users and to encrypt the information while traveling over the Internet. The main reasons for installing wireless LANs are to allow staff to gain access from areas that do not have physical network connections and to access the network's resources while moving about the premises. Wireless LANs are typically connected directly to the LAN, allowing unauthorized people in the street, car park, or even on a hill 20 miles away to access the LAN. A popular pastime for hackers is “war-driving,” where people roam the streets searching for wireless networks they can connect to.
Another key difference between Internet connections and wireless networks is the operational management. Internet connections are normally managed by the networking group that has skilled people managing the security of the connection. Wireless LANs, however, are often installed by unqualified nonnetwork staff. This operational vulnerability is a key issue with wireless LANs, because they are consumer items, bought at relatively low cost, that can be easily and improperly attached to the LAN by nonnetworking professionals.
33.3.2 Specific Threats Enabled by Wireless LANs.
Section 33.4 describes in detail the security functionality provided by 802.11 wireless products and the issues; this section provides a brief overview of the technical threats.
There have been two security systems produced for 802.11 WLAN equipment. The first security system was in the original 802.11 standard,20 which has been completely broken. The security mechanisms in this system are easily overcome obstacles to breaking into a wireless LAN.
The second “enhanced” security system is specified in the 802.11i standard, which specifies a much stronger set of security mechanisms. However, for compatibility with existing equipment, 802.11i includes the original broken security mechanisms. New equipment, when delivered, is usually not configured to use the new security mechanisms. For these reasons, this chapter covers both the previous and new security systems, so that security professionals have full details on WLAN technology issues.
A summary of the security issues found in the original security specification shows that:
- Wireless networks are available outside of the physically controlled areas because the network uses radio waves.
- Networks broadcast their existence, providing all the information required to associate to the network.
- Devices are authenticated rather than users. Stolen devices or keys copied from devices can be used to connect to the network.
- The original authentication protocols can be broken (e.g., by spoofing of shared key authentication).
- Authentication is a one-way protocol. The client does not authenticate the access point, allowing rogue attacks.
- The original privacy protocol (WEP) has been compromised (IV reuse, FMS attack).21
- The message integrity check vector (ICV) is a linear algorithm that can be defeated through bit-flipping attacks.
- Messages can be replayed without this being detected.
- Administrators implement wireless products with their default settings, causing the network to be either completely open or open to the use of default keys.
- Wireless LANs use the same set of keys for all users. This allows wireless LAN users to eavesdrop on one another.
- Public wireless LAN services (hot spots) in airports, hotels, and coffee shops are a threat to the confidentiality of business and personal information.
The next sections describe some specific threats enabled by wireless LANs.
33.3.2.1 War-Driving.
It is generally agreed that Peter Shipley invented war-driving in late 2000. It involves people using some form of transport (usually walking or driving), a laptop or handheld PC, a wireless LAN card, and software, to detect and break into wireless networks. When Peter first started war-driving, he found that over 60 percent of wireless networks were installed using the default configuration and that only 15 percent were using encryption (WEP).22 Additionally, the vast majority of the wireless LANs were installed directly on the network backbone rather than in an untrusted, guarded network segment such as a DMZ. This meant that over 85 percent of wireless LANs were facilitating unauthorized access to the core network.
Since Shipley's original work, there have been a good number of surveys conducted, –all reporting similar findings.23 The recent U.K. Government DTI survey of information security breaches in 2006 found that:
- 24 percent of U.K. businesses (59 percent of large organizations) have implemented wireless networks; this is a similar adoption from the last survey in 2004.
- The number of wireless networks without any controls has been reduced from 53 percent in 2004 to 20 percent in 2006.
- The number using encryption has increased from 16 percent in 2004 to 58 percent in 2006, with 78 percent of large organizations using encryption.24
Although the situation is better than in 2004, even after all the publicity on wireless LAN security, 42 percent of U.K. organizations are still not implementing basic controls such as encryption to protect the confidentiality of information and are still not preventing unauthorized access to the network.
From a consumer perspective, anyone who lives in a built-up area can detect quite a few neighbors' wireless networks, some of which will be unprotected. Of the networks that are protected, WEP still appears to be the protocol used to secure the network, even though a more secure system has been available for several years. As will be covered in detail later, WEP can be easily broken, even in a network with very little traffic.
33.3.2.2 War-Chalking.
Back in 2002, war-drivers began to mark on the pavement or a wall the presence of a wireless network. This activity, known as war-chalking, appears to have died out. Even the home domain www.warchalking.org is no longer active.25
33.3.2.3 Dealing with War Drivers.
Most organizations have video surveillance of the outside of their buildings. The physical security department should be briefed to recognize war-drivers and should have procedures for dealing with them. War-drivers only become a real threat when they try to access a network, but to do that they need to be stationary and normally close to the physical premises. War-drivers on foot stand out like sore thumbs because they are usually working on a laptop. Less obvious will be war-drivers in a car because they can be parked unobtrusively. Security procedures should require a review of parked cars, and the appropriate staff should be briefed to recognize war-drivers. The most dangerous war-drivers are those who can sit in a public place, such as a pub or coffee shop, and attack a network. The only defense against these people is a properly designed and secured network.
33.3.2.4 Threats Presented by Laptops with 802.11.
As already covered, wireless networks have been mass-adopted in the consumer market. Low-end laptops now come with wireless as standard. Even if an organization does not have a wireless network, some staff are going to be using it at home, and the laptop's WLAN facility is likely to be active while in the office. The Windows XP WLAN client is constantly monitoring for networks and will often automatically connect to any open access points, or other laptops, to form a peer-to-peer network.
The original 802.11 standard does not authenticate the access point to the client, making it vulnerable to attack from rogue access points. Wireless clients generally are configured to join any network they come across, which makes it very easy for attackers to perform.
Even if the client is tied down to a particular network, the laptop will be regularly sending “probe requests” searching for its home wireless network and providing the name of the network in the probe. An attacker can capture these probes and configure an open source program to emulate the home access point and connect to the client. A typical program for this is the Linux-based driver called HostAP, available from http://hostap.epitest.fi/. Once connected, the attacker can scan the laptop. If there are any unprotected file shares or other vulnerable services, then software could be installed onto the laptop, giving access to the corporate network.
An example service that could be exploited is the Microsoft ActiveSync Service for the current generation of Windows Mobile PDAs. The ActiveSync service provides a proxy service for the PDA to access the main network for e-mail and browsing. ActiveSync can be configured to connect over a WLAN,26 so if any staff have done this, they may be inadvertently providing a wireless proxy server onto the network.
The attack is even simpler if the station belongs to an IBSS network. All the attacker has to do is run Windows XP, which will show the attacker the network and give him or her the option to join it. The attacker can then use Windows networking to search for available file shares. Many people share their C: drive without realizing what they have done. Even with the firewall in Windows XP SP2, people often configure it to provide access to file shares.
33.3.2.5 Threats from Neighbors.
Most businesses do not occupy an entire building; instead they share the premises with other companies and sometimes with residential apartments. Our cities are densely populated, so even if a building is not shared, wireless networks could still be detected in adjacent buildings. In the case of high-rise buildings, there could be a direct line of sight between buildings spanning some distance; this could enable occupants to connect to one another's networks. Hobbyists are using these characteristics of wireless LANs to create wireless community networks and to share Internet connections.27
The main risk is to wireless networks that have been installed in their default, insecure state because anyone within range could automatically connect to that network. As a scenario, two businesses occupy the same building and both have WLANs. Business 1 uses WEP and business 2 does not. When an employee of business 1 first powers on a computer, Windows XP networking will display a dialog box showing the available wireless networks, and asking which network the user wants to join. The employee of business 1 unaware that the second network is not his business's network could inadvertently join business 2's network. Windows will then automatically connect the employee to the wrong network. The main impact of this scenario is the improper use of Internet bandwidth, however, should business 1 be a competitor to business 2, the consequences could be much more severe.
This scenario also applies to residents in or near the building; they could have their own wireless network, or bring home their work laptop with inbuilt wireless, and easily join any unprotected network. Residents are likely to be most interested in using a fast Internet connection in the evenings. However, if a neighbor participates in peer-to-peer file sharing networks, the impact could be serious. It might start with a loss of bandwidth, with worst-case scenarios being civil or criminal action if the network appears to be hosting copyrighted or illegal material, such as child pornography. The resident could also have the skills to be more seriously abusive of a network, making it a source of spam, or even directly attacking its systems.
To reduce the cost of broadband, people are using wireless networks to share asymmetric digital subscriber line (ADSL) connections with their neighbors (often in violation of their terms of service). This practice makes ordinary people aware of the value of illegal access to companies' Internet connections and could be an incentive for a resident to connect to an unprotected corporate network. If a network is protected only by WEP, then this attack is easy for someone located within range, and it is undetectable.
33.3.2.6 Threats Presented by Public Wireless LANs (Hot Spots).
A number of organizations are rolling out public 802.11 wireless networks enabling traveling users to access the Internet and through that the corporate network. By necessity, these networks are completely open and are not encrypted. This allows company information to be captured through the use of unencrypted e-mail, or the PC could be compromised via the Internet connection. An attacker can obtain the PC's IP address by monitoring the wireless network, after which the attacker can then scan the PC for open file shares, or other vulnerable services, from any Internet-connected PC.
This appears to be a real risk. The Register reported in July 2003 that at the 802.11 Planet Expo in Boston, security vendor AirDefense monitored the exhibition and found that only 3 percent of e-mail on day 1 and 12 percent on day 2 of the conference was encrypted.28 AirDefense also detected 149 active scans from war-driving tools, 105 denial-of-service attacks, and 32 attempted man-in-the-middle attacks, 3 of which were successful. This threat is relatively easy to mitigate through the use of VPNs and a personal firewall.
A second attack against hot-spot users takes advantage of 802.11 not authenticating the access point. A program call Airsnarf is a rogue access point utility enabling an attacker to pretend to be a commercial hot spot.29 Airsnarf was developed to demonstrate how usernames and passwords for public hot spots can be easily captured, enabling the attacker to make use of the user's account. If users happen to be on a metered service, they are likely to get a shock when the next bill comes in.
33.4 ORIGINAL 802.11 SECURITY FUNCTIONALITY.
The IEEE 802.11 group of standards has defined two security systems. The original system is defined in the base 802.11-1999 standard30 and defines the WEP protocol. The second security system is defined in the 802.11i standard31 and defines the WPA and WPA2 security systems, which address the issues in the original security system.
Section 33.3 described the high-level threats presented by wireless networks and mentioned that the security functionality provided in the original 802.11 standard has been broken. This section describes in detail the security functionality provided by this standard, along with the issues and how to resolve them.
There are three reasons for covering the original security specification. The first is the amount of legacy equipment still in use that only supports WEP. Second, users still appear to be using WEP in preference to the new 802.11i WPA and WPA2 systems. Third, for backward compatibility, the new security specification includes the original compromised security mechanisms, and the default settings of the new standard are to use these mechanisms.
33.4.1 Security Functionality Overview.
The original 802.11 standard provided this security functionality:
- Authentication via two different algorithms called “open authentication” and “shared-key authentication.”
- Confidentiality/privacy through the “Wired Equivalent Privacy” (WEP) algorithm. This algorithm uses cryptographic keys installed in the station to encrypt the data.
- Integrity through use of an encrypted CRC-32 Integrity Check Value (ICV).
These mechanisms are described in this section, along with their security properties and any weaknesses.
33.4.2 Connecting to a Wireless Network and Authentication.
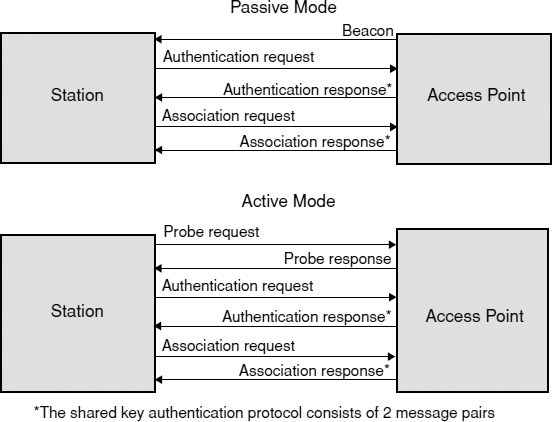
To join a network a station first has to detect the network. There are two ways that wireless stations detect networks: These are known as passive and active modes. In passive mode, stations listen for “beacon frames” that are regularly transmitted by access points in Infrastructure networks and by stations in ad hoc networks. These beacon frames contain sufficient information to identify the network and what is required to join it. In active mode, a station sends out “probe requests,” and network devices reply with a “probe response” that contains similar identification information as the beacon frame. It is common practice for networks to be configured for active mode only and to reply only if the station provides the correct network name. This is done in an attempt to hide the network from unauthorized users.
EXHIBIT 33.5 Connecting to an 802.11 Network
When a station has detected a network, it first must successfully authenticate to the network and then associate to the network as shown in Exhibit 33.5.
Wired LANs depend largely on physical security to prevent unauthorized access to the network. Anyone who can plug a computer into a LAN port can usually get access to the network. Wireless LANs can circumvent these physical controls, so the 802.11 standard provides an authentication service to compensate. The standard provides two authentication algorithms called “open authentication” and “shared-key authentication” in which the station authenticates itself to the access point. Neither authentication protocol mutually authenticates the two parties, so stations are vulnerable to attacks from rogue access points.
This section describes the open and shared-key authentication algorithms and their security properties and weaknesses.
33.4.2.1 Open Authentication.
Open authentication is the default authentication mechanism and is the only required mechanism. The 802.11 standard actually describes the open authentication algorithm as a null algorithm. A station requesting authentication provides its identity (IEEE MAC address) in the authentication request, and the access point sends back a response indicating success or failure. The access point does not attempt to verify the identity of the station, hence the term “null algorithm.”
Most products have an access control list (ACL) in the access point that enables the network administrators to specify the MAC addresses of stations that are allowed to connect. If the station's MAC address is not in the list, then an “authentication failure” response is returned. While providing some protection, this mechanism is not very strong because the MAC address in the wireless adaptor can be easily reprogrammed. All an attacker has to do is listen to traffic and collect a list of authorized MAC addresses, then program one of these addresses into an adaptor. MAC filtering also has management issues that make it difficult to implement.
33.4.2.2 Shared-Key Authentication.
Shared-key authentication is an optional authentication system that uses the WEP algorithm to authenticate the station. Only stations and access points that support WEP can use this protocol.
The protocol consists of four steps:
- The station sends a shared-key authentication request to the access point. This request contains its IEEE MAC address.
- If the access point wishes to continue with the authentication (e.g., it supports WEP and the MAC address is authorized), it uses WEP to generate a random 128-byte authentication challenge string, which is returned in the response to step 1.
- The station copies the challenge text from step 2 into the authentication data area of the step 3 request message and encrypts the message using the WEP algorithm.
- The access point decrypts the step 3 request using WEP, checks the integrity check value (ICV), and, if correct, it compares the challenge string against the string sent in step 2. If the ICV and the challenge string are correct, it sends a “success” response to the station, otherwise it sends a “failure” response.
Security Issues with the Shared-key Authentication Protocol. The designers of the shared-key authentication protocol realized there were security issues with it. To quote Section 8.1.2 of the standard, “During the shared key authentication exchange, both the challenge and the encrypted challenge are transmitted. This facilitates unauthorized discovery of the pseudorandom number (PRN) sequence for the key/IV pair used for the exchange. Implementations should therefore avoid using the same key/IV pair for subsequent frames.”32
Borisov, Goldberg, and Wagner33 took this flaw one step further to completely defeat the protocol. Because the shared-key authentication exchange enables you to establish a key stream, this key stream can be used to correctly encrypt any challenge sent from the access point and pass the authentication system, without knowledge of the actual WEP key.
Additionally, because the challenge is 128 bytes in length, and the standard does not restrict the repeated use of initialization vectors(IVs), an attacker can correctly encrypt any message 128 bytes or less with the known IV/key stream and inject these messages into the network. These messages can be used to invoke known responses (e.g., Pings) to obtain even more matching IVs and key streams in support of a dictionary attack. This type of attack would not be possible if packets were cryptographically authenticated.
Given these issues, shared-key authentication has been deprecated in 802.11i and should not be used.
33.4.2.3 Wired Equivalent Privacy.
Eavesdropping is a threat for wireless technologies so the 802.11 standard specifies the wired equivalent privacy (WEP) option in section 8.2 of the 802.11b standard.34 WEP is also defined in the 802.11i standard to support transition to the new security systems.
33.4.2.3.1 Properties of the RC4 Stream Cipher.
The WEP protocol uses RSA's RC4 stream cipher.35 Stream ciphers like RC4 operate by generating a stream of key bytes that are exclusive-ORed one byte at a time with the plaintext. Unlike block ciphers, there is no error propagation with stream ciphers. If one bit of the ciphertext is altered, then the plaintext bit is altered in a predictable way, and no other bits are affected. This property is the basis of a number of attacks on the WEP protocol.
Stream ciphers are particular vulnerable to known plaintext attacks. If a known text is encrypted, then the key stream can be easily recovered by exclusive-ORing the plaintext with the ciphertext. This key stream can then be reused to recover other plaintexts encrypted with that particular key stream or to insert new messages into the system. This property is also the basis of a number of attacks on the WEP protocol.
33.4.2.3.2 WEP Protocol.
WEP is based on the communicating parties having a shared symmetric key. The 802.11 standard does not specify any key management. As discussed later, this lack of key management is one of the serious problems with WEP.
The WEP encryption protocol consists of:
- A 32-bit cyclic redundancy check (CRC-32) is calculated from the existing data and appended to it. The purpose is to act as an integrity check value (ICV) and enable a receiving station to check that the data were decrypted correctly.
- The extended plaintext data were encrypted using the RSA RC4 algorithm. The key is a concatenation of a 24-bit IV and a shared secret key. RC4 is a stream cipher; it produces a stream of bytes that are exclusive-ORed (XOR) with the plaintext bytes to produce the ciphertext.
- The IV is inserted between the frame header, and the encrypted data and a frame check sequence is calculated (another CRC-32) and appended after the frame body to enable the receiving station to check the integrity of the received frame.
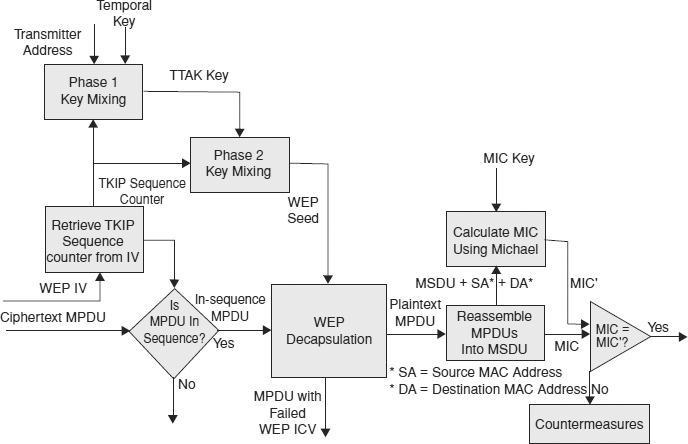
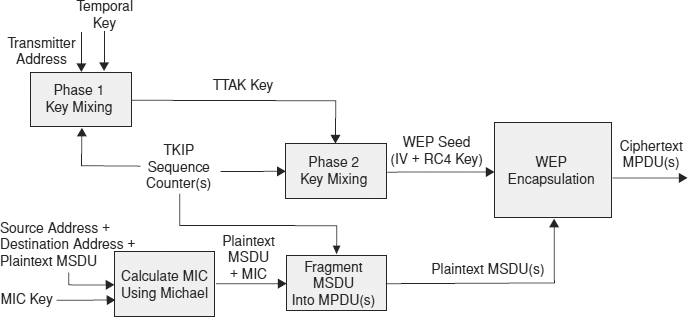
This process is shown in Exhibit 33.6, which is partly based on a figure in Gast.36
33.4.2.3.3 WEP Keys.
The 802.11 standard specifies that each station have four default 40-bit secret keys numbered 0 to 3. When combined with the 24-bit IV, the key length into RC4 is 64 bits.
Products available today have anonstandardizedoptionof 104-bit secretkeys, which when combined with the IV pass a key length of 128 bits into RC4.
33.4.2.3.4 Problems with WEP.
Borisov, Goldberg, and Wagner37 identified these flaws with WEP:
- Key length. The key length defined in the standard is only 40 bits. This is not long enough to prevent brute-force attacks by individuals or corporations. However, this problem is largely overcome with the release of products that support 104-bit secret keys.
EXHIBIT 33.6 WEP Protocol
- Key stream reuse. A well-known weakness with stream ciphers such as RC4, is that if you XOR two ciphertexts encrypted under the same key stream, then the key stream is canceled out. The output is then the two plaintexts XORed together, which is vulnerable to cryptanalysis.
- Key management. The 802.11 standard does not specify how keys should be distributed. This has led to vendors relying on manual key management systems that are a weakness in the system. For more details on the key management issues, see Section 33.4.2.3.5.
- Message modification. The WEP protocol uses a CRC-32 checksum to detect whether a packet has been modified. The message and the checksum are encrypted, which suggests that it should not be possible to alter a packet without it being detected. However,38 has demonstrated that an attacker can make calculated changes to an encrypted message that result in the same checksum. This allows an attacker to modify a message and have it accepted by another station. This is possible because WEP uses a linear rather than a cryptographic integrity check function and because of the bitwise XOR property of stream ciphers. A controlled one-bit change in the ciphertext results in a one-bit change in the plaintext bit.
- Message injection. If an attacker can obtain the ciphertext equivalent of a plain-text, then she can obtain the key stream by XORing the ciphertext with the plaintext. The attacker can then XOR a new message with the key stream, which will be accepted by a station. This flaw is possible because the CRC-32 integrity check is a linear function and can be calculated by an attacker. If each packet had a keyed cryptographic checksum, such as a SHA-1 HMAC39 instead, this attack would not be possible. Additionally, the standard allows the reuse of IVs, enabling an attacker to reuse an identified key stream (which depends on the IV) indefinitely to inject messages into the system.
- IP redirection. This attack uses the message modification attack already described to alter the destination IP address of a captured encrypted packet to that of a host controlled by the attacker on the Internet. The access point will decrypt the packet for the attacker and then forward it to the Internet for delivery.
- Reaction attack against TCP. This attack involves using the message modification technique already described to flip bits in a captured TCP message and resending it to a TCP-based server. If the TCP checksum is incorrect, the message is ignored by the server; if the TCP checksum is correct, then a TCP acknowledgment is sent back. Whether an acknowledgment is sent back leaks one bit of information on the value of the plaintext. This attack can be used to recover virtually all of the plaintext.
33.4.2.3.5 Key Management.
All stations have four default WEP keys and the possibility of a dedicated mapped key with another station. In practice, most installations use just one key for all stations. This increases the chance of IV collisions allowing IV reuse attacks.
The 802.11 standard does not specify a key management mechanism. To quote paragraph 8.1.2: “The required secret, shared key is presumed to have been delivered to participating stations via a secure channel that is independent of IEEE 802.11.”
This lack of a defined key management system has meant that the vendors have implemented a manual system, which is a major weakness in the system.
33.4.2.3.6 Problems with a Manual Key Management System.
The main problem with manual key management systems is that the keys need to be physically entered into every user's machine. This creates many points where the keys can become known and many people who have the opportunity to know and compromise the secrecy of the keys. In a number of products, the keys are displayed in clear text for users to easily obtain the key values.
The sharing of keys by many people makes it difficult to change the keys, because it has to be coordinated with all the users. In practice, this is very hard to achieve, and the keys are changed infrequently, if ever. This gives an attacker plenty of time to try breaking into the network. Additionally, ex-staff who have knowledge of the keys may be able to connect to the network from outside the building, undermining the normal physical security controls.
33.4.2.3.7 Default WEP Keys.
To ease the key management burden, many suppliers have default WEP keys programmed into the equipment, and many companies just turn WEP on and use these keys. Unfortunately, knowledge of these keys is widespread, see the frequently asked questions (FAQ) from ISS.40 Programs such as Netstumbler and Kismet identify the manufacturer of the equipment. This enables attackers to enter the known keys for a particular supplier and quickly break into the network. This problem is the wireless equivalent of the default account/password problem that affects operating systems, databases, and other software.
33.4.2.4 Fluhrer, Mantin, and Shamir (FMS) Attack.
The issues that Borisov, Goldberg, and Wagner described almost pale into insignificance when compared to the FMS attack. In August 2001 Scott Fluhrer, Itsik Mantin, and Adi Shamir published a paper on weaknesses in the key-scheduling algorithm of RC4 and theorized how this weakness could be used to easily break the WEP protocol.41 Adam Stubblefield, John Ioannidis, and Ariel Rubin then wrote a paper on a successful implementation of this attack.42 They found that it took them only a couple of hours to implement the attack and just a few days to gather off-the-shelf hardware and software to recover a WEP key. They concluded that the WEP key can be recovered using the basic FMS attack by passively collecting about 5 million packets; with optimizations, the number of packets required can be reduced to around 1 million. Since then, open source software in the form of Airsnort and WEPCrack has become available that enables relatively unskilled people to implement these attacks.
33.4.2.5 Developments since the FMS Attack.
In response to the FMS attack, vendors took a number of actions including the dropping of “weak” and “interesting” IVs and the development of a new protocol called Dynamic WEP, which is covered in Section 33.4.3.5.
The dropping of weak IVs did make it a little more difficult to break the WEP key with the existing tools, but three developments since then have totally undermined any security that WEP provides.
First, on August 6, 2004, a hacker with the handle Korek posted code for a new tool called chopper, a new statistical attack against WEP that no longer relied on weak or interesting IVs.43 It also reduced the number of packets required to break WEP from millions to hundreds of thousands. Chopper was very quickly integrated into the Airsnort and Aircrack WEP cracking tools.
Second, Aircrack has been enhanced to simplify the capture and replay of packets. This allows an attacker to capture any encrypted broadcast packets (e.g., ARP requests) and then repeatedly replay them, which the access point dutifully does, creating enough packets to break the WEP key. This means that even a lightly or unused WLAN can still be broken once a suitable broadcast packet is sent.
Third, the Auditor and BackTrack security tool collections at remote-exploit.org. These are bootable Linux ISOs disk images that have all the tools and patched wireless drivers required to break a WEP key. There are also links to movies that show all the commands to type in the correct sequence to achieve this. All that is required is to download the ISO, burn it, boot it up on an existing Windows laptop, and follow the instructions in the movies. This means that script kiddies with very little knowledge can now compromise WEP. Previously, a reasonable knowledge of Linux was required and time had to be spent learning how to do it.
The outcome is that WEP can provide protection for only a very limited time before the network is compromised. For an article covering these developments over the last few years and an overview of wireless hacking tools, refer to the SecurityFocus article written by Michael Mossmann.44
33.4.3 Defending against the WEP Vulnerability.
The best way to defend against the WEP vulnerability is to implement the 802.11i WPA or WPA2 systems described in Section 33.5. However, if this is not possible, then an alternative solution is needed. To help design a solution, Exhibit 33.7 briefly reiterates what the problems are with the current architecture and some possible countermeasures.
There are two types of problems listed in the exhibit: technical shortcomings in the 802.11 protocols and implementation and operational problems.
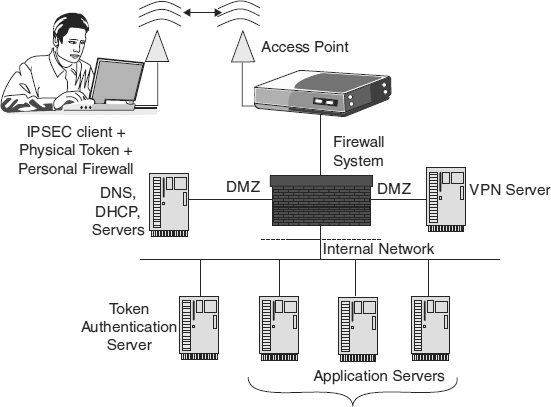
Exhibit 33.8 shows a high-level technical architecture that can overcome the technical shortcomings. Wireless LANs have properties similar to Internet connections, in that they allow individuals outside the physical control of an organization to connect to the network. Therefore, a good solution for securing wireless networks is one based on an IPSEC or SSL VPN to encrypt and authenticate packets and to defeat replay attacks. The VPN terminates in the corporation's untrusted DMZ. Once the VPN is established, the user is authenticated using a physical token, such as RSA's SecurlD or PKI credentials on a smartcard. Then and only then is the user granted access to the internal network. This solution works for internal use as well as for connecting via public wireless LANs and the Internet. An organization can usually leverage its existing Internet remote access VPN system.
EXHIBIT 33.7 802.11 Problems and Countermeasures
EXHIBIT 33.8 High-Level Technical Architecture for Wireless LANs
33.4.3.1 Additional Key Controls.
Three additional key security controls do not in themselves address the WLAN issues but need to be implemented to help maintain a secure environment. These controls are needed even when using the new 802.11i security system.
The first is effective patch management; even with a firewall, the wireless PC can be compromised at the application layer, for example, via browser vulnerabilities. Second, a regularly updated antivirus and antispyware solution is needed to detect and prevent malware from gaining control of a PC. Last, when providing remote access to wireless clients, only systems that are compliant with security policy should be allowed to connect to the network. That is, they must be firewalled, patched, and have up-to-date virus and spyware definitions. If not, there is an increased risk of viruses and Trojan horses accessing the network.
33.4.3.2 VPN and WEP.
One point for a brief discussion is whether to use WEP with a VPN. From a data confidentiality perspective, WEP is not required because the data are protected by the VPN. However, if WEP is not used, then any war-drivers who detect the network will see it as being unprotected and could start trying to break in. The devices at risk are the network infrastructure (access points, routers, switches, etc.) and the DNS and DHCP servers, although they are protected to a certain extent by the firewall and choke routers. The main threat is a denial-of-service attack, which could bring down the wireless network.
By turning on WEP, you will deter the majority of war-drivers and protect your network infrastructure from most attacks.
33.4.3.3 Access Point Configuration.
It is common to configure access points so that they do not publish their SSID in beacons and do not respond to broadcast probe requests. This is done in an attempt to hide the network from unauthorized users.
The effect of these controls is that the Windows XP wireless client and some basic war-driving tools, such as Netstumbler, will not see your network, preventing computers from accidentally joining your network. However, these controls do not provide any protection from a serious war-driver who will locate your network by capturing and processing the data traffic rather than depending on broadcast probe requests. It is possible that these controls just make it harder for authorized users to join the network, without having any real security benefit. Provided you are running a secure system, any attempt to join the network will be rejected.
33.4.3.4 Access Point Location.
Access point location is a simple but effective technique to prevent an outsider detecting your WLAN. If the access point is located in the middle of the room, the signal will be weaker outside. Additionally, if you are on the first or second floor of a building, substantial obstacles between the access point and the street would significantly degrade the signal. If the access point is placed on an outside-facing wall, the signal is likely to be broadcast strongly outside the building onto the street.
I was able to confirm this behavior during an authorized building scan for wireless networks. One building had an access point mounted on a street-facing wall on the fourth floor. This access point could not be detected on the third or fifth floors, even when I was directly below or above it. But I was able to pick up the access point from the street four floors below while sitting on a bench across the road.
33.4.3.5 Dynamic WEP.
One of the responses by vendors to the breaking of WEP was the introduction of dynamic WEP keys, which are established as part of the 802.1x authentication exchange. In this system, every wireless station has its own WEP key that the access point regularly changes, eliminating the use of static WEP keys. This is a standard option in the Windows XP wireless client and is selected via the “This key is provided for me automatically” WEP option.
How good is the dynamic WEP key system? Does it address the security issues with WEP and enable it to be used safely? There is no doubt that it is a massive improvement over static WEP keys and significantly reduces the risk of passive attacks against WEP. However, this system does not address active attacks, which can determine a WEP key in just a few minutes.45
If dynamic WEP is the best choice available, it should be used in preference to static WEP, but since it also can be broken, plans should be made to migrate to something stronger. Additionally, equipment supporting 802.1X might be upgradeable to WPA and possibly WPA2, which is highly desirable.
33.4.3.6 Conclusion on WEP.
WEP is fundamentally broken. While tactical solutions have been devised to mitigate specific attacks, new attacks have rapidly followed, taking advantage of the underlying cryptographic flaws and bypassing the mitigating controls. The best thing to do is to use WPA or WPA2, or to encrypt the data using another trusted protocol, such as IPSEC or SSL, before transmission.
33.4.3.7 Resolving the Implementation and Operational Problems.
It is not possible to completely secure a network against intrusion. Through mistakes, carelessness, ignorance, or new types of attack, outsiders at some point will penetrate the network. The first step to resolving these operational issues is an overall security policy that secures each host on an internal network in its own right. Therefore, access to the network would not immediately provide access to business applications or the computers hosting them.
The trend in networking today is to interconnect with partners' networks and with public networks such as the Internet, and to allow staff to connect directly to the LAN via the Internet, using technologies such as the VPNs. A wireless LAN is just another means, with vulnerability that enables authorized and unauthorized individuals to connect to the network.
Wireless LAN products, as they come out of the box, are configured to be insecure, and surveys have shown that a large number of sites install them in this default insecure configuration. Even if WEP is turned on, often the system uses widely known default keys.
This is normal human behavior; operating systems and software in general tend to be delivered and installed in an insecure configuration. System administrators have to take action to secure their systems, such as setting password policy and changing the default account names and passwords. The same techniques that are used to secure computer systems need to be applied to wireless networks:
- Issue a corporate policy on wireless LANs. Without a policy, the organization has no framework to control WLAN usage.
- Publicize and enforce the policy. Unless people are aware that a policy exists and that it is actively enforced via procedures and regular audits, the policy will be ineffective.
- Develop an approved WLAN architecture, configuration standards, and operating procedures that allow the technology to be quickly and securely implemented and used.
33.4.3.8 Remote Access and Public Wireless Access Points (Hot Spots).
WPA and WPA2 are good solutions for connecting to wireless networks, but data sent by remote access via a home wireless network, remote offices, and public access points will not be protected on the wired network or on the Internet. Even WPA/WPA2 only secures wireless transmissions locally. For securing non-WPA equipment, the best practice is to use the same VPN-based solution. Once connected to the access point, the VPN provides a secure tunnel to the organization.
The one threat a VPN cannot mitigate is a rogue hot spot. Upon connection to the access point, the VPN is not yet established and is unable to provide protection. This is a fundamental flaw in the current system, and vendors need to establish an interim solution for this until the 802.11u working group provides a standardized solution.
Going forward, the wireless switch vendors are working to do away completely with the need for VPNs by implementing secure protocols between the LWAPs and the access controllers. Establishing a secure wireless network in a remote branch office will be as simple as shipping an access point to the remote office and plugging it into the network. The story is the same for mobile staff: Given a trusted access point, users connect it to their broadband/cable router at home or to the Ethernet connection in the hotel room, and a secure connection is established.
This could be the beginning of a significant change of paradigm, particularly with the emergence of products that are bringing together wired and wireless networks. In the end, it may not matter where you are or how you are connecting. If you have a trusted device, and individual credentials, it will be easy to connect securely to a corporate network.
Before this can happen, there must be much research to be sure that the loss or theft of an access point, and of the protocols and architecture, will not put the corporate network at risk. Even though users and access points are authenticated, and their credentials are revoked in the event of loss, staff may not return access points when they leave an organization. Knowing who has which particular access point so it can be revoked is another problem.
33.5 IEEE 802.11I.
In June 2004, the IEEE released the 802.11i standard to improve the security of 802.11 networks. This standard can be downloaded free of charge from the IEEE Web site.46
The standard is designed for both personal and enterprise users. Enterprise use is based on the 802.1X protocol to provide authentication and to establish a security context. A “personal” profile, using a preshared key (PSK) based on a password, is provided for consumers and SOHO users who do not have the necessary 802.1X authentication infrastructure The PSK option is vulnerable to a dictionary attack; more information is provided in Section 33.5.7.
33.5.1 Structure of the Robust Security Network.
The new security system is called Robust Security Network (RSN) and establishes Robust Security Network Associations (RSNAs). Equipment implementing RSNA algorithms will be called RSNA-capable; earlier equipment is called pre-RSNA. The standard includes the original pre-RSNA algorithms as well as the new RSNA algorithms. A network that supports both RSNA and pre-RSNA equipment is called a transition security network (TSN) and is intended to facilitate migration to the new standard. Use of TSN is not recommended because the network can be compromised via the pre-RSNA equipment.
The core protocol underlying RSNA is IEEE 802.1X. RSNA builds on this protocol to provide these security features:
- Enhanced mutual authentication mechanisms that can authenticate users as well as the network client. The access point is also authenticated to the client station, defeating rogue access point and man-in-the-middle attacks.
- Key management algorithms
- Cryptographic key establishment
- Cryptographic message integrity codes to defeat the bit-flipping attacks possible in the original standard.
- Two data privacy protocols:
- Temporal key integrity protocol (TKIP), which is an optional protocol specifically designed so that existing WEP-based hardware can be upgraded to use it.
- Counter mode with CBC-MAC protocol (CCMP), which is mandatory for RSNA compliance. It uses AES in counter mode for confidentiality and CBC-MAC for authentication and integrity. CCMP is a strong protocol that has been designed for long-term data privacy and the next generation of wireless equipment.
RSNA security is structured into two subsystems:
- Security association management consisting of:
- RSNA negotiation procedures to establish a security context
- IEEE 802.1X authentication, replacing IEEE802.11 authentication
- IEEE 802.1X key management to establish cryptographic keys
- Data privacy mechanisms consisting of the two protocols described above.
The sections that follow describe these subsystems.
33.5.2 802.1X Authentication.
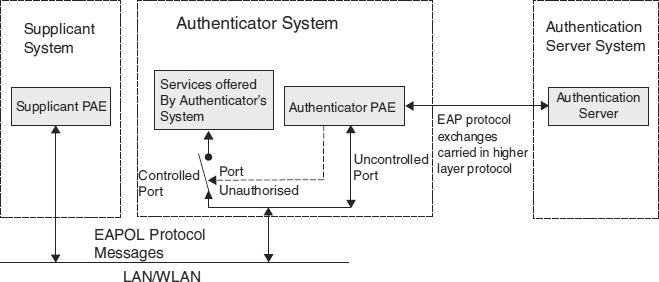
RSNA is based on 802.1X, which provides port-based network access controls for IEEE 802 LAN infrastructures. These infrastructures include Ethernet, token ring, and wireless networks. 802.1X authenticates and authorizes devices attached to a LAN port and will not allow a device to access the network if authentication fails.
802.1X defines three roles:
- Authenticator. The device that authenticates a network device before allowing it to access network resources. In an 802.11 BSS network, the access point is the authenticator.
- Supplicant. The device that wants to access network resources and needs to be authenticated
- Authentication server (AS). The AS performs the actual authentication of the supplicant on behalf of the authenticator. The AS can be located with the authenticator but is commonly an external system, such as a RADIUS server.
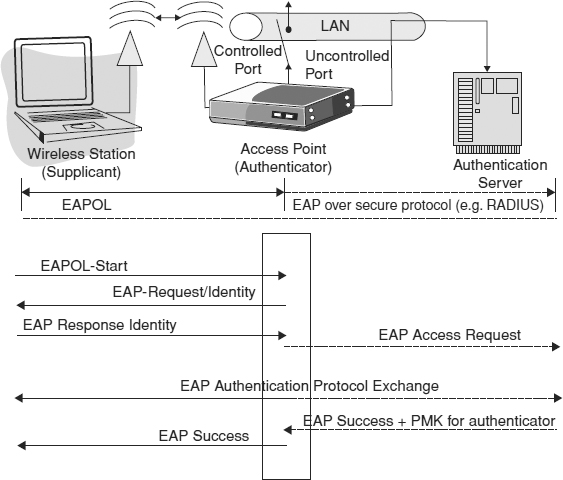
Additionally, 802.1X defines the object “port access entity” (PAE), which operates the authentication algorithms and protocols in the supplicant and authenticator. An overview of the 802.1X architecture47 is shown in Exhibit 33.9.
The authenticator has two logical ports; the first is an uncontrolled port that allows access to required functionality, such as the authenticator PAE. The second port is the controlled port that allows access to the rest of the network. The status of the controlled port is set by the authenticator PAE and is dependent on the outcome of the authentication between the supplicant and the authentication server.
EXHIBIT 33.9 802.1X Architecture
The messages between the supplicant and authenticator use the Extensible Authentication Protocol (EAP) over LAN (EAPOL) protocol defined in 802.1X. Messages between the authenticator and the AS are encoded using EAP and carried in a higher layer protocol such as RADIUS.
33.5.3 Security Association Management.
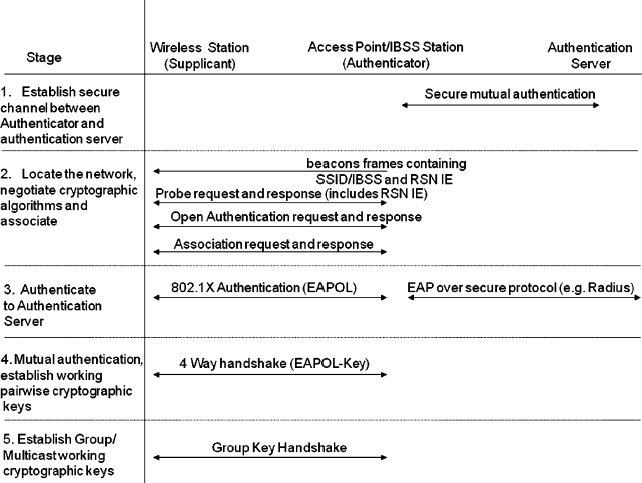
Exhibit 33.10 shows the high-level security association management flow. It consists of five stages that:
- Establish a secure channel between the authenticator and authentication server.
- Locate the network, negotiate cryptographic algorithms, and associate to it.
- Authenticate via 802.1X to the authentication server.
- Mutually authenticate and establish pairwise cryptographic keys.
- Establish group/multicast cryptographic keys.
The sections that follow describe these stages. Two aspects vary the security association flow. The first is whether the wireless network contains an access point (a BSS) or whether it is an IBSS. The second is whether the master cryptographic key is a global preshared key (PSK) or if it is established during the 802.1X authentication protocol. Any variations caused by BSS/IBSS and 802.1X/PSK are described within the sections.
Stage 1. Establish a secure channel between authenticator and authentication server. In this stage the authenticator and AS mutually authenticate one another and establish a secure channel between them using a protocol such as RADIUS, IPSEC, or TLS. This channel is used to securely carry the authentication exchanges between the supplicant and the AS. This stage is not required if the network uses a PSK.
EXHIBIT 33.10 RSNA Security Association Management
Stage 2. Locate the network and associate to it. This stage is mostly the original 802.11 functionality for locating, authenticating, and associating to a wireless network as described in Section 33.4.2. Key differences in an RSN are the beacon frames, probe responses, and association requests containing RSN information elements (RSN IE) that indicate RSNA support, along with the available authentication and privacy protocols.
Stage 3. 802.1X authentication to the authentication server. This stage is not required if the network uses a PSK; in this situation, authentication occurs in stage 4.
The purpose of this stage is mutually to authenticate the supplicant and authentication server (AS) to one another and independently to generate the pairwise master key (PMK) for use in stage 4. The EAP used to achieve this has a number of different methods available; RSN requires the use of EAP methods that mutually authenticate the parties, such as EAP-TLS, EAP-PEAP, and EAP-TTLS, to prevent rogue access point and man-in-the-middle attacks. EAP-MD5 is not suitable or secure for RSN. The messages exchanged between the supplicant and the AS are defined by the EAP method. An overview of this stage is given in Exhibit 33.11.
For a BSS network, the wireless station is the 802.1X supplicant and the access point is the authenticator. The access point relays the authentication messages between the supplicant and the authentication server, which can be either a separate service or built in.
For an IBSS, the station wanting to associate to another station is the supplicant, and the target station is the authenticator. This means that stations in an IBSS can simultaneously be supplicants and authenticators, depending on who initiated the association. Additionally, each IBSS station will need an authentication server unless the network uses pre-shared keys.
EXHIBIT 33.11 802.1X Authentication to Authentication Server
As covered in stage 1, a secure channel has to be established between the authenticator and the authentication server prior to this exchange. This serves two purposes: to protect the integrity and authenticity of the authentication exchange and to allow the AS to securely send the PMK to the authenticator once authentication is complete.
Stage 4. Mutual authentication and establishment of pairwise working keys. Stage 3 established a PMK in both the supplicant and authenticator. If the network uses a PSK, then the PSK is the PMK. This stage, called the four-way handshake and has three purposes:
- To authenticate mutually the supplicant and authenticator to one another by confirming that they both have the same valid PMK
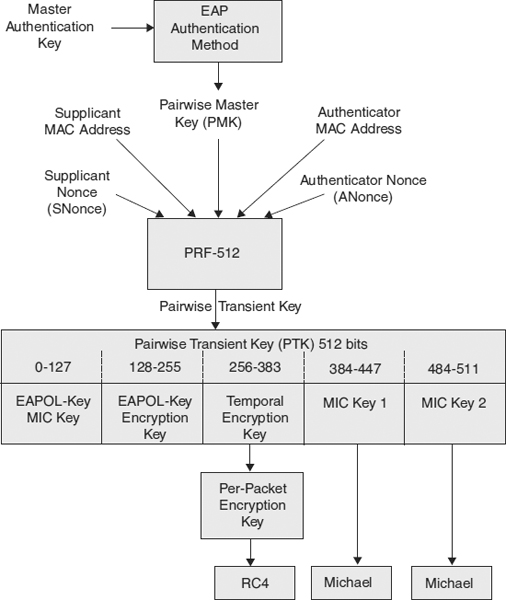
- To generate a pairwise transient key (PTK) from the PMK and fresh temporal keys bound to their MAC addresses
- To synchronize the installation of the keys in both devices
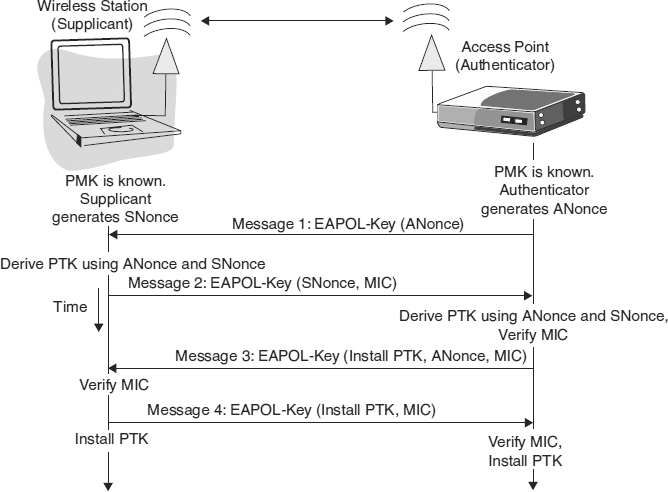
The four-way handshake is implemented by EAPOL-key messages exchanged between the supplicant and the authenticator, and consists of eight steps, as shown in Exhibit 33.12.
- The authenticator and the supplicant both generate nonces48 for use in the authentication protocol. The authenticator's nonce is called ANonce and the supplicant's nonce is called SNonce.
EXHIBIT 33.12 The Four-Way Handshake to Authenticate and Establish PTK
- The authenticator sends an EAPOL-key message containing the ANonce (Message 1).
- The supplicant derives the PTK using the ANonce and SNonce and calculates EAPOL-key encrypting key (KEK) and EAPOL-key message integrity key (MIC).
- The supplicant sends an EAPOL-key message containing the SNonce and a MIC calculated using the EAPOL MIC key (Message 2).
- The authenticator can now derive the PTK because it has both the ANonce and SNonce. It then calculates the EAPOL-key KEK and EAPOL-key MIC key and verifies the MIC in message 2.
- The authenticator sends a message containing the ANonce and a flag instructing the supplicant to install the key. The message is also authenticated by a MIC (Message 3).
- The supplicant verifies the MIC and sends a message to the authenticator confirming the installation of the key. This message is authenticated by a MIC and encrypted using the EAPOL-key KEK (Message 4).
- The authenticator installs the new keys and starts the last stage to establish the group keys.
Stage 5. Establish group/multicast cryptographic keys. In stage 4 the PTK and temporal keys were established. These keys are used to secure an additional message pair in which the authenticator sends the group temporal key (GTK) in an encrypted form to the station. The group keys are used to secure broadcast messages, such as ARP requests and multicast traffic.
In a BSS network, all stations have the same group/multicast key that is sent to each station by the access point. However, for IBSS networks, there is no access point to set a common key so each station has its own group transmit key that it sends to all stations in the IBSS. This is achieved by executing the four-way handshake and group key handshake in both directions.
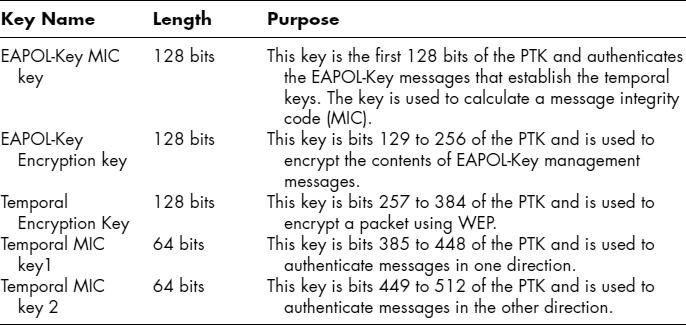
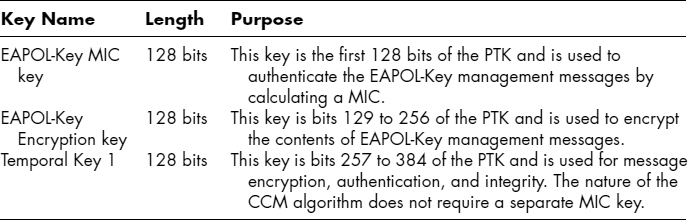
33.5.4 RSNA Key Hierarchy and Management.
RSNA defines a key management system that derives working (temporal) keys from a root master key. The exact key hierarchy varies slightly between TKIP and CCMP but broadly follows the same system. This section describes the key management system and notes the differences between TKIP and CCMP.
There are two key hierarchies: The first contains the pairwise keys that are shared between two wireless devices (e.g., between two stations in an IBSS or between a station and an access point in a BSS); the second hierarchy is the group/multicast keys that are used for network broadcasts, such as ARP requests or multicast traffic.
33.5.4.1 Pairwise Key Hierarchy.
There is a maximum of four levels of cryptographic keys in the pairwise key hierarchy.
- 802.1X authentication keys. These keys exist only if the supplicant and authentication server mutually authenticate one another using preinstalled keys. An example is EAP-TLS, which requires both the supplicant and authentication servers to have PKI credentials. The 802.1X keys are used to establish the pairwise master key (PMK).
- Pairwise master key. The PMK is 256 bits and is either the key established in level 1 or a preshared key (PSK) installed in the devices. The PMK, device MAC addresses, and nonces are fed into a variable-length pseudorandom function (PRF) to generate a pairwise transient key (PTK). The nonces are derived from a 256-bit key counter that is initialized at system start-up from a random number, the time, and the MAC address. The nonce is then incremented every time a key is changed.
- Pairwise transient key. The PTK varies in length from 128 bits to 512 bits and is split up into the required temporal keys. The key lengths and number of keys are dependent on the algorithm. For TKIP, the PTK is 512 bits, and this is split into five temporal keys. For CCMP, the PTK is 384 bits, split into three temporal keys.
- Temporal and per-packet keys. The temporal keys are mixed with variable data such as packet counters, which has the effect of creating a fresh key for every packet. Exhibits 33.13 and 33.14 describe the TKIP and CCMP temporal keys.
Exhibit 33.15 shows the entire key hierarchy for TKIP.
33.5.4.2 Group Key Hierarchy.
The group key hierarchy is similarly structured to the pairwise key hierarchy. The authenticator creates a group master key. This master key, the authenticator's MAC address, and a group nonce (GNonce) are processed by the PRF to produce a group transient key (GTK), which is then split up into temporal keys.
EXHIBIT 33.14 CCMP Temporal Keys
EXHIBIT 33.15 TKIP Key Hierarchy
33.5.5 Temporal Key Integrity Protocol.
The temporal key integrity protocol (TKIP) is a suite of algorithms to resolve the known security issues in WEP for the existing 802.11 equipment already in the field.
To ensure compatibility with the existing base of wireless products, TKIP had to take into account the hardware architecture of the existing wireless products.49 Wireless products have two CPUs: The first is in the MAC chip that implements the wireless protocol, the second is the host CPU.
For access points, the host CPU is a dedicated CPU that runs the access point. For wireless LAN PC cards, the host CPU is that of the host PC. For performance reasons, most MAC chips have a hardware RC4 encryption engine to perform the encryption. To avoid an unacceptable performance impact by moving encryption to the host CPU, TKIP needed to use this existing MAC encryption engine. This required TKIP to continue to use RC4 and WEP, but in a way to overcome the identified problems.
The designers came up with a solution to the issues, and the result was TKIP with this functionality:
- A MAC service data unit (MSDU) is a message to be sent to another station.
- An MSDU may be fragmented into more than one MAC protocol data unit (MPDU). These data units are packets/frames sent by the physical layer.
- When all the MPDUs have been received, the recipient reconstructs the MSDU and passes it up the protocol stack.
- Each MSDU is authenticated and integrity protected, using a keyed cryptographic message integrity code (MIC).
- The source and destination addresses as well as the MSDU plaintext are included in the MIC calculation. This prevents forgery and masquerading attacks.
- Since the strength of the MIC is limited and can be compromised by trial and error, TKIP provides optional countermeasures that stop communications for a period of time (60 seconds) when an invalid MIC is received and then immediately forces a rekey of all stations. The designers estimated that the MIC with countermeasures would resist attack for about one year before an attacker would correctly guess the MIC. However, any measure that automatically interrupts service in response to probes also provides a mechanism for denial-of-service attacks.
- Each TKIP MPDU (packet) has a sequence number encoded in the WEP initialization vector. Any MPDUs that arrive out of order are dropped.
- TKIP mixes a temporal key, the transmitter's address, and a sequence counter in a two-phase protocol to form the RC4 WEP seed. The mixing is done in a way to defeat weak-key attacks.
- RSNA uses 802.1X EAPOL-key messages to regularly change the temporal keys so that RC4 key streams are not reused. The key change is triggered automatically when the sequence counter is close to exhaustion.
These controls largely address the issues identified in the current standard by introducing cryptographic message authentication, by preventing key stream reuse, and by never using a weak IV. However, TKIP is still not considered a strong solution because of the strength of the MIC. TKIP should be used only as an interim measure until existing equipment can be replaced with CCMP-capable equipment. Exhibit 33.16 and Exhibit 33.17 show the TKIP process in the transmitting and receiving stations. The phrase “using Michael” refers to a particular algorithm for generating a message integrity code (MIC).50
33.5.6 Counter Mode/CBC-MAC Protocol (CCMP).
CCMP is the mandatory protocol defined in 802.11i to provide confidentiality, authentication, integrity, and replay protection for the next generation of wireless equipment. It is not possible to upgrade existing equipment to use this protocol.
CCMP uses the Advanced Encryption Standard (AES) encryption in counter mode to provide confidentiality and CBC-MAC (AES-CCM) for message authentication and integrity. The inputs to the algorithm include:
- A 128-bit block cipher encryption key (the temporal key).
- A nonce based on an incrementing packet number that is used only once with the encryption key to encrypt a message. Reusing a nonce to encrypt more than one message destroys its security properties.
EXHIBIT 33.16 TKIP Algorithm in the Transmitting Station
- The message to be encrypted.
- Additional data to be authenticated but not encrypted, such as the packet header containing the source and destination MAC addresses.
33.5.7 Remaining Implementation Issues.
The IEEE 802.11i standard has done a good job addressing the cryptographic flaws in the original standard. However, security is more than good cryptography, and organizations still are likely to be vulnerable if these new wireless networks are not implemented properly.
EXHIBIT 33.17 TKIP Algorithm in the Receiving Station
As an example, the standard still supports the original broken protocols to facilitate transition to the new protocols. In addition, the Wi-Fi Alliance says that the new protocols are not enabled by default in new equipment.51 This means that users who just install the equipment and turn it on will have a completely open network. Additionally, by including the original broken protocols in the new standards, users will still use them, giving attackers the opportunity to compromise the network.
By necessity, the standard supports preshared keys for home use and for smaller organizations that do not have the required authentication server infrastructure. These preshared keys can be entered as a cryptographic key or calculated from a password.
There are three issues with preshared keys. The first is that password based preshared keys are vulnerable to an off-line dictionary attack.52 This means that the use of poor passwords by users enables the network to be compromised. A number of open source tools, such as Aircrack53 and coWPAtty,54 have been developed to automate the attack.
The second issue with preshared keys is that the device is authenticated, rather than the user, and any staff who leave an organization with knowledge of the preshared key may still be able to connect to the network from the outside. The final issue is that the standard states that the installation of preshared keys is outside its scope. This fact suggests that the issue we have today with vendors having poor key management tools, and well-known default keys, could plague the new system too.
The standard focuses heavily on using external authentication servers such as RADIUS to do the authentication and management of the master keys. Unfortunately, home users and smaller organizations are unlikely to have this type of authentication infrastructure. Unless wireless products have built-in user authentication servers, pre-shared keys will dominate, and the usual avenues of attack, such as default keys and bad passwords, could compromise the system.
33.5.8 Wi-Fi Alliance's WPA and WPA2 Standards.
The Wi-Fi Alliance is a nonprofit organization formed to certify the interoperability of 802.11 products. It is also the organization behind the Wi-Fi labels seen on wireless equipment such as the one shown in Exhibit 33.18.
EXHIBIT 33.18 Wi-Fi Alliance Certification Label
The Wi-Fi Alliance was concerned that the security issues surrounding WEP would hinder the adoption of wireless products, so it worked with the IEEE to quickly bring to market a security standard in advance of 802.11i.
This standard is called Wi-Fi Protected Access (WPA). To maintain compatibility with 802.11i, WPA is just a subset of it. The functionality in WPA consists of TKIP so that existing equipment can be upgraded, 802.1X authentication, and the 802.11i key hierarchy and management system. WPA also includes the preshared key option for home users and for small businesses that do not have a RADIUS infrastructure. This preshared key is based on a password and is vulnerable to an off-line dictionary attack as described.
Wi-Fi Alliance also has a second standard called WPA2. This standard is just another name for the completed 802.11i standard, which includes protocols for stronger data protection based on the AES encryption algorithm. Like WPA, there are two versions of the WPA2: WPA2-Personal, which uses a password to authenticate access to the network, and WPA-Enterprise, which uses an authentication server. Like WPA, WPA2 is designed to secure all 802.11 devices, including 802.11b, 802.11a, and 802.11g.
The Wi-Fi Alliance has many white papers available on its Web site (www.wi-fi.org). One paper to read in particular is “Deploying Wi-Fi Protected Access (WPA™) and WPA2™ in the Enterprise,” which provides a good overview of the WPA and WPA2 features along with guidance on how to implement them.
33.6 802.11 SECURITY AUDITING TOOLS.
This section looks at the open source and commercial tools available to help audit a wireless environment and to understand the tools that war-drivers have to attack a network. Exhibit 33.19 lists the main programs available and the platform they run under.
33.6.1 Auditor and BackTrack.
The first step for anyone wanting to setup a DIY wireless auditing system is to download the Auditor security tool collection from www.remote-exploit.org. Auditor is a live Linux distribution with all the required security tools and patched drivers to do wireless security auditing. All that is necessary is to download the ISO, burn it, and boot it up from the CD-ROM on any PC.
It does access-point emulation, client penetration, LEAP/PPTP cracking, packet injection, scanning, and MAC address changing as well as WEP and WPA PSK cracking. Work is under way to replace Auditor with a new distribution called BackTrack.
33.6.2 Kismet.
Kismet is the best open-source wireless auditing tool available, meeting the majority of core requirements. It detects broadcasting and nonbroadcasting access points, and the stations associated to them, as well as stations searching for an access point to connect to. It is a part of the Auditor security distribution and has been well integrated to reduce the configuration issues. Work is in progress on a complete rebuild of the code to improve maintenance and performance.
Being Linux based, Kismet can be cross-compiled for Linux-capable PDAs such as the iPaq and Sharp Zaurus SL-5500.
33.6.3 Netstumbler.
Netstumbler55 is a well-known Windows program used by many war-drivers. The program works by sending out broadcast probe requests (messages searching for wireless networks with which to associate). When an access point receives a probe request, it sends back a probe response containing information that identifies the network. Netstumbler collects this information and displays it in a GUI interface.
EXHIBIT 33.19 802.11 Security Auditing Software
To combat the Netstumbler threat, wireless vendors have implemented a “closed network” option that does not respond to broadcast probe requests. This option is effective in avoiding detection by Netstumbler. Additionally, Netstumbler does not detect network stations. Therefore, it will not tell how many stations there are connected to a network, or whether there are any unattached stations that a rogue access point could associate to and use to attack the network.
These limitations make Netstumbler unsuitable for wireless network auditing purposes.
33.6.4 Airsnort.
Airsnort56 is an open-source Linux program that implements the Fluhrer, Mantin and Shamir,57 and Korek58 optimizations to crack a WEP key. It is not a wireless auditing tool, although it does display a list of access points and captures packets, which can be viewed in tools such as Ethereal to help ensure that a network is properly configured.
33.6.5 CoWPAtty and Aircrack.
CoWPAtty is a tool that does a dictionary attack against the WPA PSK algorithm. CoWPAtty must be provided with a libpcap59 file containing a four-way handshake as well as a dictionary file. The tool then locates the four-way handshake and uses the dictionary to determine the password. The program can be downloaded from http://sourceforge.net/projects/coWPAtty and is included in the Auditor distribution.
Aircrack is a suite of tools that enables the capture of wireless traffic, cracks WEP, injects packets, (aireplay) and performs dictionary attacks against the WPA PSK algorithm. It is being actively developed as aircrack-ng. The program can be downloaded from www.aircrack-ng.org and is included in the Auditor distribution.
33.6.6 Ethereal.
Ethereal is a well-regarded open-source packet capture and analyzer program available on both UNIX and Windows. It is a useful tool to enable a network engineer to check that the wireless network is correctly configured. In particular, it will highlight the presence of clear text traffic (e.g., broadcasts). Ethereal needs to be patched to interface directly with the wireless drivers. To avoid patching, other packet capture tools, such as Airsnort, can be used and then analyzed by Ethereal.
33.6.7 Wellenreiter.
Of all the wireless auditing programs, Wellenreiter is the easiest to get going because it is a Perl program that auto-detects the model of a wireless card and configures itself accordingly.
Wellenreiter has an advantage over Netstumbler in that it detects hidden nonbroad-casting access points. However, it has these shortcomings that limit its usefulness as a wireless auditing tool:
- Wellenreiter only supports 802.11b devices. There is no support for 802.11a or 802.11g.
- It does not list the stations attached to the access points or any unattached stations searching for an access point to connect to.
- It does not provide any signal strength information, so it is hard to track down the source of a signal.
A C++ Opie version is available for running on Linux handhelds such as the iPaq and the Sharp Zaurus. The program can be downloaded from www.wellenreiter.net and is included in the Auditor distribution.
33.6.8 Commercial Wireless Auditing Tools.
Even though Kismet is a respectable tool for wireless auditing, it does not have the functionality of the commercial wireless auditing tools. As well as network management and diagnostic functions, these tools enable an audit of the environment. The available tools include:
- Airmagnet by Airmagnet Inc.
- Airopeek NX by Wildpackets Inc.
- Network Observer by Network Instruments LLC
- Sniffer by Network Associates
33.7 CONCLUSION.
802.11 wireless LAN networks are now a mainstream technology. Approximately a quarter of all businesses have installed them, and consumers have mass-adopted them so they can access their broadband connections from all the PCs at home. Telecommunications companies have rolled out public wireless LAN networks in cities, airports, hotels, railway stations, and coffee shops, enabling broadband access on the move.
Enthusiasts have extended the range of wireless LANs to over 20 miles by modifying old satellite TV dishes and are actively using these to provide broadband access in out-of-the-way places. This technology is here to stay, and its use will become increasingly widespread in homes, businesses, banks, government departments, doctor's offices, and hospitals.
However, wireless technology brings with it risks that need to be managed. The technology, based on radio waves, allows unauthorized individuals outside the physical confines of the home or office to receive these radio signals. It is a hobby for some people to search for wireless networks and to break into them.
Without the proper security controls, unauthorized individuals could connect to the network, compromising sensitive business or personal information such as banking and medical details. The wrong people connecting to a network could inflict huge amounts of damage to the IT systems, even crippling an organization.
The trend in networking today is to interconnect with other partners' networks, and with public networks such as the Internet, and to allow staff to connect directly to the LAN via the Internet, using technologies such as VPNs. A wireless LAN is just another means, with vulnerabilities enabling authorized and unauthorized individuals to connect to the network. These types of risks emphasize the need to secure each host on an internal network from attack.
The 802.11i standard has provided two upgraded security systems to address the security issues with the original system. The first is called TKIP, based on WEP and designed to upgrade existing equipment in the field. This system is also known as WPA.
The second security system is called CCMP. It is based on AES and is designed for new equipment with more powerful processors. It is also known as WPA2. WPA and WPA2 resolve the current identified issues in the original security system. However, they are not panaceas because both systems have a preshared key option, which is vulnerable to an off-line dictionary attack. Additionally, the 802.11i standard still includes the original broken protocols, so organizations could still be vulnerable to attack should administrators or staff install equipment in its default state.
While the 802.11i standard has addressed most of the technical issues in the original standard, there is still a lot of existing equipment installed that cannot be upgraded. For these circumstances, interim measures such as these are needed to secure the existing networks:
- Treat a wireless network like any other untrusted network and use well-researched and understood security mechanisms, such as IPSEC or SSL VPNs, to secure the link layer. Additionally, connect the wireless network to an untrusted zone and strongly authenticate the users before allowing access to the internal network.
- Issue a corporate policy on wireless LANs. Without a policy, the organization has no framework to control wireless LAN usage.
- Publicize and enforce the policy. Unless people are aware that a policy exists and that it is actively enforced via procedures and regular audits, the policy will be ineffective.
- Develop an approved wireless LAN architecture, configuration standards, and operating procedures that allow the technology to be quickly and securely implemented and used.
33.8 APPENDIX 33A–802.11 STANDARDS.
This section provides an overview of the 802.11 family of standards and indicates the standards that are relevant to this chapter. Further details can be found on the Internet home page for the IEEE 802.11 group of standards, www.ieee802.org/11/index/shtml. From this page you can get to the rest of the site, two pages in particular should be highlighted:
- The first contains the working group project timelines.60 As well as the projected dates for each project developing a standard, this page contains links to the approval letters that contain the scope, purpose, and reason for the project, along with additional background information. This page also contains links to the standards for the working groups that have completed their work.
- The second page to highlight is the 802.11 standards download page.61 The standards become available for free download six months after publication under the Get IEEE 802® program.
33.8.1 802.11 and 802.11b: MAC and Physical Layer Specifications.
ANSI/IEEE Std 802.11-1999 is the base wireless LAN standard that is the subject of this chapter.62 The 1999 standard is an update to the original 802.11-1997 standard. The 802.11b standard is a higher-speed physical layer extension to 802.11 that does not specify any extra security functionality.63 Therefore, the security functionality analyzed in this chapter originates from the 802.11-1999 standard.
33.8.2 802.11a: 5GHz High-Speed Physical Layer.
The IEEE/ANSI standard 802.11a-1999 implements a higher-speed physical layer operating in the 5GHz radio band in conjunction with the existing 802.11 MAC. 802.11b operates in the 2.4GHz band and has a maximum speed of 11Mb/s, whereas 802.11a has a maximum speed of 54Mb/s.
802.11a uses the same MAC layer as 802.11b; therefore, it has the same security functionality and vulnerabilities.
Currently, 802.11a does not comply with European requirements so it cannot be freely used in Europe. The 802.11h standard was produced to address these issues.
33.8.3 802.11d: 802.11 Additional Regulatory Domains.
Each country controls the use of the radio spectrum within its jurisdiction, and there are varying levels of conformity between countries. The current 802.11 standard defines operation in only a few regulatory jurisdictions. The purpose of the 802.11d standard is to define the physical layer requirements to allow the use of 802.11 wireless LANs in more countries.
33.8.4 802.11e: MAC Enhancements for Quality of Service.
The IEEE 802.11e standard provides MAC enhancements for quality of service. This enables WLANs to support time-sensitive multimedia applications, such as video and audio on demand, as well as Voice over IP.
33.8.5 802.11F: Inter-Access Point Protocol.
When a user's station roams from one access point to another, there are a series of messages exchanged between the access points so that the station is registered with only one access point at a time and so as to pick up any buffered packets for the station that may not have been delivered while it was moving between locations. The 802.11 standard did not define any standards for these inter–access point communications, resulting in a lack of interoperability between vendors' products.
802.11F specifies the necessary messaging between access points to allow interoperability between products. However, this standard was a trial use recommended practice and has since been withdrawn.
33.8.6 802.11g: Higher-Rate Extension to 802.11b.
The 802.11g standard defined a new physical layer allowing similar data rates as the 802.11a standard (54Mb/s) in the 2.4GHz band but not specifying any extra security functionality.
33.8.7 802.11h: Spectrum Managed 802.11a.
The 802.11h standard enhances the current 802.11 MAC and 802.11a physical specification with spectrum and power management extensions to enable the 802.11a standard to be used in Europe.
33.8.8 802.11i: MAC Security Enhancements.
The 802.11i standard was developed to improve the security of 802.11 wireless networks, in particular to address the issues with WEP. The standard can be downloaded for free from the IEEE Web site,64 and its contents are covered in depth in Section 33.5.
33.8.9 802.11j: 4.9Ghz-5GHz Operation in Japan.
The 802.11j standard enhances the 802.11 standard, to add channel selection for 4.9 GHz and 5 GHz in Japan to conform to the Japanese rules on operational mode, operational rate, radiated power, spurious emissions, and channel sense.
33.8.10 802.11k: Radio Resource Measurement Enhancements.
The purpose of the 802.11k working group is to define and expose radio and network information to facilitate the management and maintenance of wireless LANs. Currently, wireless clients associate to an access point with the strongest signal. This can lead to throughput issues if too many clients are using one access point. Through this standard, wireless clients will know when an access point is overloaded, enabling them to choose an underutilized one instead.
This standard will put information requiring security into the measurement frames. The 802.11w working group has been set up to secure this information. The contents of this standard are not further considered in this chapter.65
33.8.11 802.11m: Maintenance.
The purpose of the 802.11m working group is to incorporate editorial and technical corrections to the existing standards as well as to provide clarifications and interpretations.66
33.8.12 802.11n: Enhancements for Higher Throughput.
The purpose of the 802.11n working group is to define the next-generation physical layer to increase the throughput of wireless LANs up to 600Mbps.67
33.8.13 802.11p: Wireless Access for the Vehicular Environment (WAVE).
To quote the working group's status report, “This Task Group will define enhancements to 802.11 required to support Intelligent Transportation Systems (ITS) applications. This includes data exchange between high-speed vehicles and between these vehicles and the roadside infrastructure in the licensed ITS band of 5.9 GHz.” Practical applications of this standard include road-toll collection, but other applications include information provision, paying for services, or messaging between vehicles.68
33.8.14 802.11r: Fast Roaming/Fast BSS Transition.
The purpose of the 802.11r working group is to develop a standard for fast transitions between access points and to establish the required quality of service before the transition. The primary application for this standard is Voice over Wireless LANs (VoWLAN). It will address the issues with the current standard, where the handover time from one access point to another is measured in hundreds of milliseconds, which could lead to voice degradation and drop-outs.69
33.8.15 802.11s: ESS Mesh Networking.
The purpose of the 802.11s working group is to develop a self-configuring multihop wireless distribution system to provide mesh networking. Conventional access points are physically connected to the core network. This can be costly, especially for outdoor municipal wireless networks and for historical buildings with construction restrictions. With wireless mesh networks, the access points connect directly to each other via the wireless medium and can route through the wireless mesh to access services on the wired network. This significantly reduces the cabling required and deployment costs. In the case of historical buildings, network coverage may be provided without any construction activities.
33.8.16 802.11T: Wireless Performance Prediction (WPP).
The purpose of the 802.11T project is to produce a recommended practice for testing, comparison, and deployment planning of 802.11 WLAN devices based on a common and accepted set of performance metrics, measurement methodologies, and test conditions.70
33.8.17 802.11u: Interworking with External Networks.
The purpose of this project is to develop a standard specifying interworking with external networks. This objective is to improve the user experience with wireless hot spots, addressing issues such as enrollment, network selection, and authorization for roaming.
33.8.18 802.11v: Wireless Network Management.
The purpose of the 802.11v project is to enable the management of attached wireless stations through a layer 2 mechanism. While the 802.11k project is defining standards for retrieving information from stations, this project will provide the ability to configure the stations. This will be particularly useful for situations where stations need to be configured before they are able to setup an IP connection.71
33.8.19 802.11w: Protected Management Frames.
The purpose of the 802.11w project, according to the approval letter, is “to improve the security of some or all 802.11 management frames by defining enhancements such as data integrity, data origin authenticity, replay protection, and data confidentiality.”
While 802.11i improved security for WLAN data frames, it did not provide any additional security for the management frames. These frames include the existing deauthentication and disassociation frames that hackers use today to attack WPA/PSK and to launch DoS attacks as well as including the new management frames being created by standards in development, such as 802.11k and 802.11v. These new standards are introducing network management features, which if not protected could be used to attack the network. For an overview on 802.11w, refer to a Network World article by Epstein.72
33.8.20 802.11y: 3650–3700MHz Operation in the United States.
The 802.11y working group is producing an amendment to the existing 802.11 standard to enable wireless LAN operations in the 3650–3700MHz band for the United States.
33.8.21 802.1x: Port-Based Network Access Control.
802.1X is a published standard to enable the authentication and authorization of network devices before access is provided to the network. 802.1X also enables session keys to be established for the encryption and authentication of frames. This standard is at the heart of the 802.11i security system and is covered in more detail in Section 33.5.2.
33.8.22 Wi-Fi Protected Access (WPA) and WPA2.
WPA is a wireless security standard published by the Wi-Fi Alliance. Its purpose was to address the security issues with current 802.11 wireless products in the interim period until the 802.11i standard was ratified. Strictly speaking, WPA is not an IEEE 802.11 standard; however, WPA is based on stable protocols in a late draft of the 802.11i standard.
WPA2 is the name the Wi-Fi Alliance has given to the strong security mechanisms based on the AES algorithm published in 802.11i. For more information, refer to Section 33.5.8.
33.9 APPENDIX 33B: ABBREVIATIONS, TERMINOLOGY, AND DEFINITIONS.
Most of these abbreviations and definitions originate from the ANSI/IEEE 802.11-1999 standard73 and the 802.11i standard.74
| Abbreviation/Term | Meaning/Definition |
| 802.11 | The ANSI/IEEE standard 802.11, 1999 edition. Wireless LAN medium access control (MAC) and physical layer (PHY) specifications. |
| 802.11a | This extension to the 802.11 standard provides an improved throughput of up to 54Mb/S in the 5GHz frequency band. |
| 802.11b | The ANSI/IEEE 802.11b specification is an extension to the 802.11 standard that specifies a higher-speed physical layer (up to 11Mb/s). The rest of the 802.11 standard is unchanged. |
| 802.11d | This standard extends the original 802.11 standard to define physical layers, allowing 802.11 to operate in additional countries. |
| 802.11e | This standard enhances the current 802.11 MAC to provide quality of service support. |
| 802.11F | This withdrawn standard specifies inter–access point messaging to provide multivendor interoperability. |
| 802.11g | This standard provides an improved throughput of up to 54Mb/s in the 2.4GHz band. |
| 802.11h | This standard provides spectrum and transmit-power enhancements to the 802.11a 5GHz standard for Europe. |
| 802.11i | This standard enhanced the 802.11 MAC to provide improvements in security. This standard defined the WPA and WPA2 security systems. |
| 802.11j | This extension to the original 802.11 standard provides operation in the 4.9Ghz and 5GHz bands in Japan. |
| 802.11k | This standard is in development to facilitate the management of wireless LANs. |
| 802.11m | This standard is a maintenance release to incorporate editorial and technical changes into the existing standards. |
| 802.11n | This is a standard in development to provide higher speeds. Current proposals provide a throughput up to 600Mb/s. |
| 802.11p | This is a standard in development to support intelligent transportation applications, such as road-toll collection. |
| 802.11r | This is a standard in development to provide fast roaming and transition in support of real-time applications, such as voice in wireless LANs. |
| 802.11s | This is a standard in development to provide mesh networking. |
| 802.11T | This is the development of a recommended practice to evaluate wireless LAN performance. |
| 802.11u | This is a standard in development to improve the user experience for public wireless networks. |
| 802.11v | This is a standard in development to manage wireless stations. |
| 802.11w | This is a standard in development to improve the security of 802.11 management frames. |
| 802.11y | This is a standard in development to define a wireless service for the 3650–3700MHz band in the United States. |
| 802.1X | IEEE Std 802.1X-2001 defines port-based network access controls. It provides the means to authenticate and authorize a network device before granting access to network resources.75 |
| Access controller | The CAPWAP term for a wireless switch that controls and manages light-weight access points (LWAPs). |
| Access point (AP) | A specialized wireless station that bridges other wireless stations to the physical wired network or distribution system. |
| Authenticator | An 802.1X component that authenticates a network device before allowing it to access network resources |
| Authentication server (AS) | An 802.1X component that performs the actual authentication of the supplicant on behalf of the authenticator. |
| BSS | Basic service set. A set of stations controlled by a single coordination function (an access point). |
| CAPWAP | Control and provisioning of wireless access points. An IETF initiative to establish standards enabling interoperability between different vendors access points and wireless switches. |
| CBC-MAC | Cipher block chain—message authentication code. A message authentication algorithm based on a symmetric block cipher, where each block chains into the next data block. |
| CCMP | Counter mode with CBC-MAC protocol. A symmetric block cipher mode providing data privacy using counter mode and data origin authentication using CBC-MAC. This is the protocol required for compliance with the WPA2 standard. |
| CRC | Cyclic redundancy check. |
| CRC-32 | A 32-bit CRC used in the 802.11 standard. |
| Distribution system (DS) | A system used to interconnect a set of basic service sets (BSS) to create an extended service set (ESS). |
| DMZ | Demilitarized zone. Refers to a network segment that separates and protects a trusted network from an untrusted one. |
| DSSS | Direct sequence spread spectrum. An 802.11 modulation technique that spreads signal power over a wide band of frequencies. |
| DTLS | Datagram transport layer security. Essentially TLS over UDP. |
| EAP | Extensible authentication protocol defined in RFC 2284.76 |
| EAP-PEAP | Protected EAP. A draft IETF standard by RSA, Microsoft, and CISCO for doing EAP authentication protected by TLS.77 |
| EAP-TLS | EAP–transport layer security defined in RFC 2716.78 |
| EAP-TTLS | EAP–tunneled TLS authentication protocol. A draft IETF standard that tunnels EAP authentication through TLS.79 |
| EAPOL | EAP over LANs. The protocol defined in 802.1X for encapsulating EAP messages exchanged between a wireless station and the access point. |
| ESS | Extended service set. A set of one or more interconnected basic service sets (BSSs) and integrated LANs that appears as a single BSS to wireless stations. |
| Exclusive-Or (XOR) | An add-without-carry logical operation. XOR is used in cryptographic algorithms partly because it is reversible by repeating an operation. A XOR B XOR A will result in B; A XOR B XOR B will result in A |
| FHSS | Frequency-hopping spread spectrum. A transmission method that sends bursts of data over a number of frequencies, with the system hopping between frequencies in a defined way. |
| IBSS | Independent basic service set. An ad hoc wireless network where stations communication directly with one another rather than via an access point. |
| ICV | Integrity check value. A CRC-32 value used by the WEP algorithm to detect changes in the ciphertext and to ensure that the packet has been decrypted correctly. |
| IV | Initialization vector. A 24-bit value prepended to the WEP key, which is used as the seed for the RC4 stream cipher as part of the WEP algorithm. |
| KSA | The key scheduling algorithm of the RC4 stream cipher. |
| LAN | An IEEE 802 local area network. |
| LWAP | Light-weight access point. A type of access point that is essentially an 802.11 wireless radio that passes the received packets to a wireless switch for processing. |
| LWAPP | Light-weight access point protocol. The base protocol chosen for the CAPWAP protocol and used by wireless switches to manage and communicate with access points. |
| MAC | Medium access control. The data link layer in a wireless LAN that enables stations to share a common transmission medium. |
| Mb/s | Megabits per second. |
| MIC | Message integrity code. A cryptographic integrity code to detect changes in a message. |
| Michael | The message integrity code (MIC) for TKIP. |
| MITM | Man in the middle. An MITM attack is one where an attacker can sit between two communicating parties and monitor what is being exchanged, without being noticed. |
| MPDU | MAC protocol data unit. The packets/frames exchanged between stations via the physical layer. |
| MSDU | MAC service data unit. Information that is to be delivered as a unit between MAC service access points (SAP). If an MSDU is too large to fit into one MPDU, then it will be fragmented into multiple MPDUs and reassembled into one MSDU by the receiver. |
| OFDM | Orthogonal frequency division multiplexing. A modulation technique used in the 802.11a and 802.11g standards that works by dividing data into several pieces and simultaneously sending the pieces on many different subchannels. This mechanism enables throughput of up to 54 Mb/s. |
| PAE | Port access entity. An 802.1X object that operates the authentication mechanism in the participants. |
| PKI | Public key infrastructure. |
| PMK | Pairwise master key. A master session key derived from the overall master key. For 802.1X authentication mechanisms (e.g., EAP-TLS), the key is generated during authentication. For preshared key authentication, the PMK is the preshared key (PSK). |
| Port | Network access port. |
| PRF | Pseudorandom function. An RSNA-defined algorithm that is part of the key generation function. |
| PSK | Preshared key. A static cryptographic key that is distributed out of band to all stations in the wireless network. |
| PTK | Pairwise transient key. An RSNA cryptographic key that is the source of working temporal keys that protect wireless messages. |
| RADIUS | Remote authentication dial-in user service, defined in RFC 2865.80 |
| RSN | Robust security network. The name for the new security system implemented in the 802.11i draft standard. An RSN is one that only allows the creation of RSN associations. |
| RSNA | A robust security network association is where two stations have authenticated each other and associated using the four-way handshake protocol. |
| RSN IE | Robust security network information element. The RSN IE is contained in Beacon and probe frames, and lists the supported authentication mechanisms and cipher suites. |
| Supplicant | The 802.1X term for the network device that wants to connect to the network. |
| “The standard” | In this chapter, the term refers to the ANSI/IEEE standard 802.11, 1999 edition. |
| TKIP | Temporal key integrity protocol. A suite of algorithms enhancing the WEP protocol to provide secure operations for existing 802.11 equipment. |
| TLS | Transport layer security defined in RFC 2246 |
| TSN | Transient security network. A TSN can form associations with both RSNA-capable and pre-RSNA stations. |
| UDP | User datagram protocol. An Internet protocol used to send short messages to other systems. UDP does not provide any reliability or ordering guarantees. |
| WEP | Wired equivalent privacy. The protocol defined in the 802.11-1999 standard to encrypt data on a wireless LAN. |
| Wireless LAN | In this chapter, the term refers to 802.11 wireless local area networks using a radio physical layer. |
| WLAN | Wireless local area network. |
| WTP | Wireless termination point. The CAPWAP term for an access point. |
| WPA | Wi-Fi protected access. WPA was the first 802.11 wireless security standard from the Wi-Fi Alliance, using the TKIP security mechanism in the 802.11i standard. |
| WPA2 | Wi-Fi protected access V2. WPA2 is the Wi-Fi Alliance's name for the AES-based CCMP wireless security mechanisms in the 802.11i standard. |
| XOR | Exclusive-OR. |
33.10 FURTHER READING
Anjum, F., and P. Mouchtaris. Security for Wireless Ad Hoc Networks. Hoboken, NJ: John Wiley & Sons, 2007.
Edney, J., and W. A. Arbaugh. Real 802.11 Security: Wi-Fi Protected Access and 802.11i. Boston: Addison-Wesley, 2003.
Gast, M. 802.11 Wireless Networks: The Definitive Guide, 2nd ed. Sebastopol, CA: O'Reilly & Associates, 2005.
Hassler, V. Security Fundamentals for E-Commerce. Norwood, MA: Artech House, 2000.
Laurent-Maknavicius, M., and H. Chaouchi, eds. Mobile and Wireless Networks Security: Proceedings of the Mwns 2008 Workshop. Hackensack, NJ: World Scientific Publishing, 2008.
Makki, S., P. Reiher, K. Makki, N. Pissinou, and S. Makki, eds. Mobile and Wireless Network Security and Privacy. New York: Springer, 2007.
Vacca, J. R.. Guide to Wireless Network Security. New York: Springer, 2006.
Wheat, J., R. Hiser, J. Tucker, A. Neely, and A. McCullough. Designing a Wireless Network. Rockland, MA: Syngress Publishing, 2001.
Xiao, Y., X. Shen, and D-Z. Du, eds. Wireless Network Security. New York: Springer, 2007.
Zhang, Y., J. Zheng, and H. Hu, eds. Security in Wireless Mesh Networks. Boca Raton, FL: Auerbach, 2008.
33.11 NOTES
1. Matthew Gast, 802.11 Wireless Networks: The Definitive Guide, 2nd ed. (Sebastopol, CA: O'Reilly & Associates, 2005).
2. L. Yang, P. Zerfos, and E. Sadot, RFC4118—Architecture Taxonomy for Control and Provisioning of Wireless Access Points (CAPWAP).
3. J. Wheat, R. Hiser, J. Tucker, A. Neely, and A. McCullough, Designing a Wireless Network (Rockland, MA: Syngress Publishing Inc, 2001); ANSI/IEEE Std 802.11, 1999 Edition—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specification.
4. International Organisation for Standardisation, Information Technology, Open Systems Interconnection, Basic Reference Model, Part 2: Security Architecture, ISO IS 7498-2, 1989.
5. Wheat et al., Designing a Wireless Network.
6. Gast, 802.11 Wireless Networks.
7. www.ietf.org/html.charters/capwap-charter.html.
8. B. O'Hara, P. Calhoun, and J. Kempf, RFC3990, Configuration and Provisioning for Wireless Access Points (CAPWAP) Problem Statement.
9. Yang, Zerfos, and Sadot, RFC4118.
10. www.ietf.org/Internet-drafts/draft-ietf-capwap-protocol-specification-01.txt.
11. N. Modadugu and E. Rescorla, “The Design and Implementation of Datagram TLS,” http://crypto.stanford.edu/~nagendra/papers/dtls.pdf.
12. “AAA is an architectural framework for configuring a set of three independent security functions in a consistent manner. AAA provides a modular way of performing the following services: Authentication… Authorization…Accounting….” For further details, see the Cisco AAA Overview: www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scfaaa.html.
13. Vesna Hassler, Security Fundamentals for E-Commerce (Norwood, MA: Artech House, 2000).
14. Dorothy and Peter Denning, Internet Besieged: Countering Cyberspace Scofflaws (ACM Press).
15. International Organisation for Standardisation, Information Technology, Open Systems Interconnection, Basic Reference Model, Part 2. ISO/IEC 9834-2: 1993.
16. www.oreillynet.com/pub/a/wireless/2001/05/03/longshot.html.
17. Peter Shipley, “Open WLANs—The Early Years of WarDriving,” www.dis.org/filez/openlans.pdf.
18. www.trevormarshall.com/biquad.htm.
20. ANSI/IEEE Standard 802.11, 1999 ed., Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specification.
21. S. Fluhrer, I. Mantin, and A. Shamir, “Weaknesses in the Key Scheduling Algorithm of RC4.” http://ftp.cs.cornell.edu/people/egs/615/rc4_ksaproc.pdf.
22. Shipley, “Open WLANs.”
23. “Out of Thin Air: A Wireless Network Security Survey of London,” Orthus Ltd.; The Wireless Security Survey of London—One year on…; www.rsasecurity.com/worldwide/downloads/LondonWirelessSurvey2002.pdf.
24. www.dti.gov.ukindustries/information_security/pdfs/DTIJSBS_2006_tech_report.pdf.
25. For more background see the Wikipedia article: http://en.wikipedia.org/wiki/Warchalking.
26. http://theillustratednetwork.mvps.org/WM2003/ActiveSync/WM2003ActiveSyncConfiguration.html.
27. www.wlan.org.uk/ and www.toaster.net/wireless/community.html.
28. www.theregister.co.uk/content/69/31567.html.
29. http://airsnarf.shmoo.com.
30. ANSI/IEEE Standard 802.11, 1999 ed. Part 11.
31. http://standards.ieee.org/getieee802/download/802.11i-2004.pdf.
32. ANSI/IEEE Standard 802.11, 1999 ed., Part 11.
33. N. Borisov, I. Goldberg, and D. Wagner, “Intercepting Mobile Communications: The Insecurity of 802.11.” ACM, ISBN: 1-58113-422-3.
34. ANSI/IEEE Standard 802.11, 1999 ed., Part 11.
35. Steven Bellovin, “Problem Areas for the IP Security Protocols.” www.cis.upenn.edu/~cis700-2.
36. Gast, 802.11 Wireless Networks papers/probable_plaintext-cryptanalysis-of-ipsec.ps.g2.
37. Borisov, Goldberg, and Wagner, “Intercepting Mobile Communications.”
38. Borisov, Goldberg, and Wagner, “Intercepting Mobile Communications.”
39. H. Krawczyk, M. Bellare, and R. Canetti, “IETF RFC2104, HMAC: Keying Hash functions for Message Authentication ftp://ftp.crt.dfn.de/pub/docs/crypt/bck2.ps.g2.”
40. www.iss.net/wireless/WirelessLAN802_11bSecurityFAQ.htm.
41. Fluhrer, Mantin, and Shamir, “Weaknesses in the Key Scheduling Algorithm of RC4.”
42. A. Stubblefield, J. Ioannidis, and A. Rubin, “Using the Fluhrer, Mantin, and Shamir Attack to Break WEP.” AT&T Labs technical report TD4ZCPZZ August 6th 2001.
43. www.netstumbler.org/showthread.php?p=89692#post89692.
44. “WEP: Dead Again, Part 1” www.securityfocus.com/infocus/1814, and Part 2 www.securityfocus.com/infocus/1824.
45. “WEP: Dead Again, Part 1” and Part 2.
46. http://standards.ieee.org/getieee802/download/802.11i-2004.pdf.
47. www.networkworld.com/news/tech/2006/040306-80211w-wireless-security.html.
48. An arbitrary number used only once; either the product of a random number generator or a unique number that can exist at only one instant, such as the current date and time.
49. Niels Ferguson, “IEEE 802.11-02/020r0—Michael: An Improved MIC for 802.11 WEP” (January 2002) http://grouper.ieee.org/groups/802/11/documents/documentholder/2-020.zip.
50. Niels Ferguson, “IEEE 802.11-02/020r0—Michael: An Improved MIC for 802.11 WEP”.
51. www.wi-fi.org/files/uploaded_files/wp_9_WPA-WPA2%20Implementation_2-27-05.pdf.
52. http://wifinetnews.com/archives/002452.html.
54. http://sourceforge.net/projects/coWPAtty and http://wirelessdefence.org/Contents/coWPAttyMain.htm.
56. http://airsnort.shmoo.com/.
57. Fluhrer, Mantin, and Shamir, “Weaknesses in the Key Scheduling Algorithm of RC4.”
58. “Korek” is the pseudonym of an active hacker who has posted extensively on WEP weaknesses. See, for example, the exchanges at www.netstumbler.org/f49/need-security-pointers-11869/#post89036 and www.netstumbler.org/showthread.php?t=12489.
59. “libpcap is a system-independent interface for user-level packet capture. libpcap provides a portable framework for low-level network monitoring. Applications include network statistics collection, security monitoring, network debugging, etc.” See Sourceforge.net for details: http://sourceforge.net/projects/libpcap/.
60. http://grouper.ieee.org/groups/802/11/802.11_Timelines.htm.
61. http://standards.ieee.org/getieee802/802.11.html.
62. ANSI/IEEE Standard 802.11, 1999 ed., Part 11.
63. ANSI/IEEE Standard 802.11, 1999 ed., Part 11.
64. http://standards.ieee.org/getieee802/download/802.11i-2004.pdf
65. http://grouper.ieee.org/groups/802/11/Reports/tgk_update.htm.
66. http://grouper.ieee.org/groups/802/11/Reports/tgmupdate.htm.
67. http://grouper.ieee.org/groups/802/11/Reports/tgn_update.htm.
68. http://grouper.ieee.org/groups/802/11/Reports/tgp_update.htm.
69. http://grouper.ieee.org/groups/802/11/Reports/tgr_update.htm.
70. http://grouper.ieee.org/groups/802/11/Reports/tgLupdate.htm.
71. http://grouper.ieee.org/groups/802/11/Reports/tgv_update.htm.
72. www.networkworld.com/news/tech/2006/040306-80211w-wireless-security.html.
73. ANSI/IEEE Standard 802.11, 1999 ed., Part 11.
74. http://standards.ieee.org/getieee802/download/802.11i-2004.pdf.
75. IEEE Standard 802.1X-2001, “Port Based Network Access Control.”
76. B. Aboba, L. Blunk, J. Vollbrecht, J. Carlson, and H. Levkowetz, “IETF RFC 3748, PPP Extensible Authentication Protocol (EAP).” http://www.ietf.org/rfc/rfc3748.txt.
77. Palekar, Simon, Zorn, Josefsson, “Protected EAP Protocol (PEAP),” in preparation.
78. Aboba and Simon, “IETF RFC 2716 PPP EAP TLS Authentication Protocol,” http://www.ietf.org/rfc/rfc2716.txt.
79. Blake-Wilson, “EAP-Tunneled TLS Authentication Protocol Funk,” in preparation.
80. C. Rigney, S. Willens, A. Rubens, and W. Simpson, “IETF RFC 2865, Remote Authentication Dial In User Service (RADIUS)” (June 2000). www.faqs.org/rfcs/rfc2865.