The WIF runtime provides a feature called the Claims to Windows Token Service (c2WTS) that allows the RP application to impersonate a Windows user by extracting the User Principal Name (UPN) claim from open security token standards such as SAML. This is often needed in SSO scenarios where a service needs to be accessed on an external computer. The c2WTS is installed as a Windows service and is invoked by the WIF runtime using Net Named Pipes (IPC) .
The c2WTS can be configured with the token handler using the Microsoft.IdentityModel configuration section or on-demand by calling the UpnLogon (Microsoft.IdentityModel.WindowsTokenService) method. In this recipe, we will learn about the steps to configure the c2WTS and see how it can be used to implement impersonation and provide security for static content.
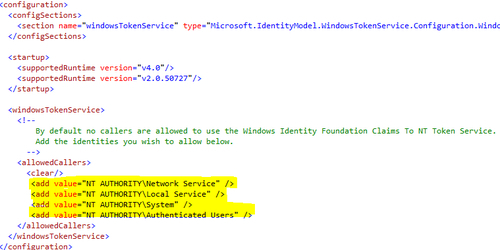
The c2WTS service must be configured for the list of allowed callers. Open the c2wtshost.exe.config file located under the %ProgramFiles%Windows Identity Foundationv3.5 folder and uncomment the<allowedCallers> section content, as shown in the following screenshot:
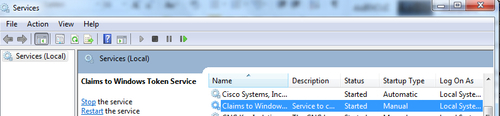
- Start the Claims to Windows Token Service from the Services console:
- Open the
IdentityManagementsolution and add reference to theSystem.DirectoryServices.AccountManagementassembly in theWebSTSproject. - Open the
Default.aspx.csfile and include the following code in theButton1_Clickevent handler to add a UPN claim.try { claims.Add(WSIdentityConstants.ClaimTypes.Upn, "[email protected]"); } catch (PrincipalServerDownException) { //Do not add this claim if you are disconnected from AD }Notice that the
PrincipalServerDownExceptionobject is exposed by theSystem.DirectoryServices.AccountManagementassembly and the exception is thrown if you are not connected to the AD. - Open the
Default.aspxpage in theWebRPproject and include a couple ofLabelcontrols inside the<form>tag to display the Current and Impersonate user:<body> <form id="form1" runat="server"> <div style="padding-left:80%"> Welcome <asp:Label ID="lblLoginMessage" runat="server"></asp:Label>! You are Impersonating <asp:Label ID="lblImpersonationMessage" runat="server"></asp:Label> </div> </form> </body>
- Open the
Default.aspx.csfile in theWebRPproject and write the following code in theCreateChildControlsmethod (inside theforeachloop):if (item.Key == WSIdentityConstants.ClaimTypes.Upn) { try { var windowsIdentity = S4UClient.UpnLogon(item.Value); using (WindowsImpersonationContext context = windowsIdentity.Impersonate()) { lblImpersonationMessage.Text = WindowsIdentity.GetCurrent().Name; context.Undo(); } lblLoginMessage.Text = WindowsIdentity.GetCurrent().Name; } catch (SecurityAccessDeniedException) { lblLoginMessage.Text = "Access Denied"; lblImpersonationMessage.Text = "Impersonation Failed"; } }The preceding code checks if the claims retrieved from the token have a claim of type UPN. It then generates an impersonation context.
- Compile the solution and run the
WebSTSproject. On clicking on the Create Token button, you will be redirected to theDefaultpage of theWebRPapplication and the Current and Impersonated users will be displayed on the page, as shown in the following screenshot: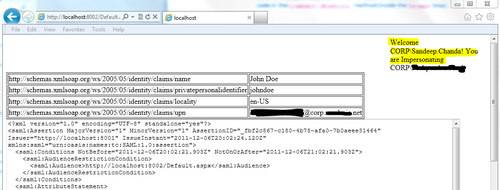
The WIF runtime invokes the c2WTS on the UpnLogon method call using IPC. The UpnLogon method returns a WindowsIdentity instance for the UPN claim value and then the Impersonate method with the WindowsIdentity instance is used to create an impersonation context.
The Undo method of the WindowsImpersonationContext class ends the impersonation and sets the context back to the current Windows identity (as evident from the WindowsIdentity.GetCurrent method call).
For an on-demand impersonation, similar results can be achieved by creating a WindowsIdentity object using the UPN value, however, the c2WTS provides a more robust and generic implementation with the mapToWindows configuration attribute and also supports the rehydrating of the Windows identity from the UPN in a cookie-mode secure conversation.
Static content such as the .htm files are not protected by the Federation Authentication Module. The c2WTS can be invoked to map the claims security token to a Windows token and prevent unauthorized access to the entire application including static content. The following configuration changes are required to be made to the security token handler configuration under the Microsoft.IdentityModel section:
<securityTokenHandlers> <add type="Microsoft.IdentityModel.Tokens.Saml11.Saml11SecurityTokenHandler, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35"> <samlSecurityTokenRequirement mapToWindows="true" useWindowsTokenService="true" /> </add> </securityTokenHandlers>
