In a complex SSO operation, account synchronization can turn out to be a nightmare for developers and administrators alike. In the previous chapter, you have learned how Azure ACS can help isolate identity as a cross-cutting concern in the enterprise. In this recipe, we will showcase the steps to use AD FS as an identity provider in Azure ACS. This will enable reuse of the existing Windows accounts and remove the dependency on third-party identity providers if you are in the enterprise using Active Directory for authentication. As the developers, you are also shielded from writing complex account synchronization routines.
To integrate AD FS 2.0 with Azure ACS 2.0, perform the following steps:
- To configure AD FS 2.0 as an identity provider, go to ACS 2.0 Management Portal and create a new identity provider. Select the WS-Federation identity provider option and click on Next, as shown in the following screenshot:
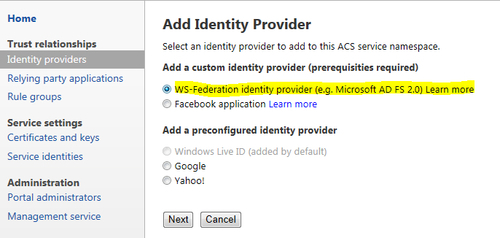
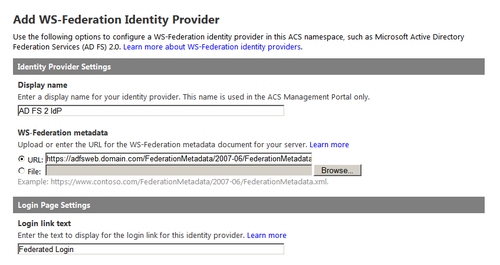
- In the Add WS-Federation Identity Provider page, enter AD FS 2 IdP in the Display name field. Select URL under WS-Federation metadata and enter http://adfsweb.domain.com/FederationMetadata/2007-06/FederationMetadata.xml in the URL field. Also, specify Login link text as Federated Login in our example. Click on Save:
- Next, we need to configure ACS as a relying party in the federation server. To do this, click on Add Relying Party Trust… from the AD FS 2.0 management console Actions pane and specify the ACS URL to establish a trust in the Add Relying Party Trust Wizard:
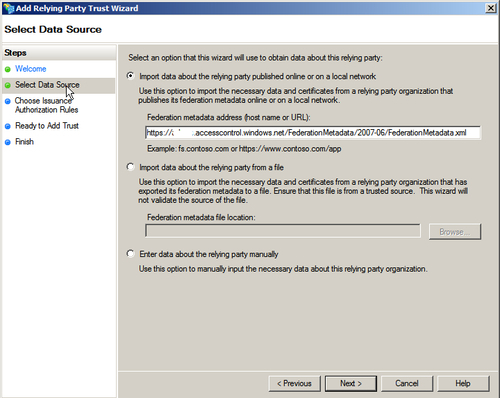
- Once the Add Relying Party Trust Wizard is complete, launch the Claim Rules dialog box and specify a Pass Through claim rule under the Claim Transformation Rules tab. Repeat this step for each of the incoming claims.
Implementing the steps mentioned in the preceding section allows the federation server to be used as an identity provider for ACS relying party applications. You can create a new relying party application in ACS 2.0 Management Portal, associate ADFS 2 IdP as the identity provider and the users will get redirected to the AD FS 2.0 for getting authenticated against Active Directory.
