Windows 8 Metro applications would inevitably talk to services hosted either in cloud or in an on-premise hosting environment providing access to resources for consumers using the Metro client application. Access to services from Windows 8 Metro client applications can be made secure using Windows Azure Access Control Services (Azure ACS 2.0). In Chapter 4, Cloud-based Identity with Azure Access Control Service, we have explored the steps to perform identity delegation using Azure ACS 2.0. In this recipe, we will take a look at the steps to create a Windows 8 Metro application. We will then configure it to receive a security token issued by Azure ACS and use it to access resources from a Service Provider.
The prerequisites to walk through the "how-to steps" are as follows:
- Visual Studio 11 Developer Preview (can be downloaded from http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=27543) running on Windows 8 Developer Preview (you can download from your MSDN subscription).
- Windows Azure account with Azure ACS namespaces appropriately configured.
- The Relying Party application must be appropriately configured in ACS. This application will act as a Service Provider for the Windows 8 Metro client application. This should be fairly familiar to you having done it in Chapter 4, Cloud-based Identity with Azure Access Control Service.
- For our example, we will use Yahoo as the Identity Provider. It should be configured in ACS.
In addition to the preceding prerequisites, you would also need to be familiar with Windows 8 Metro application development using XAML (plus C#) and JavaScript. We will also use Task Based Asynchronous Programming (TAP) concepts in this recipe. You can learn more about this pattern in the document available at the following URL:
For creating and configuring a Windows 8 Metro application, follow these steps:
- In the Start screen in Windows 8, click on the Microsoft Visual Studio 11 Developer Preview application:
- Create a new Visual Studio 11 C# Windows Metro style application and name it
MetroAcsApplication:
- In the just created
MetroAcsApplicationproject open theMainPage.xamlfile and create a button (captionedLogin)and a textbox (with nametxtStatus)to display a "Success / Failure" message post the authentication process. - Open the
MainPage.xaml.csfile and add aprivatemethodGetAuthenticationResultAsync:private async Task GetAuthenticationResultAsync(string ipURL) { try { var result = await WebAuthenticationBroker.AuthenticateAsync( WebAuthenticationOptions.Default, new Uri(ipURL)); txtStatus.Text = (result.ResponseStatus == 0) ? "Success" : "Failure"; } catch (Exception e) { txtStatus.Text = e.Message; } }Note that
GetAuthenticationResultAsyncis not an ordinaryprivatemethod. It uses the TAP pattern in .NET Framework 4.5 to asynchronously carry out the authentication process. - Call the
GetAuthenticationResultAsyctask from the button-click event handler of the Login button:private async void Button_Click(object sender, RoutedEventArgs e) { Task getLoginUrl = GetIdentityProviderLoginUrlAsync("Yahoo"); txtStatus.Text = "Loading Provider..."; await getLoginUrl; Task authenticate = GetAuthenticationResultAsync(loginUrl); txtStatus.Text = "Authenticating.."; await authenticate; } - Compile and run the application. Click on the Login button. You will be redirected to the Identity Provider for authentication:
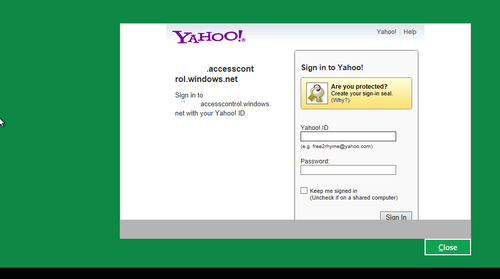
- You have now successfully implemented access control in your Metro application with Azure ACS.
The most important item to note in the steps is the usage of WebAuthenticationBroker (Windows.Security.Authentication.Web). It is a WinRT ( http://en.wikipedia.org/wiki/Windows_Runtime) object that starts an asynchronous authentication operation with a call to the method AuthenticateAsync.
The returned result contains the following three properties:
Rich client applications such as Windows 8 Metro Applications do not have the ability to federate in passive mode such as in a web browser. Web Authentication Broker mediates to allow rich client applications delegate identity to providers such as Azure ACS and then use the retrieved token to make a request to the Service Provider specifying the token in the Request Header. To retrieve the ACS token, you must specify a valid call-back URI to the AuthenticateAsync method. The call-back URI will receive the ACS token (SWT or SAML). The following diagram illustrates this scenario:
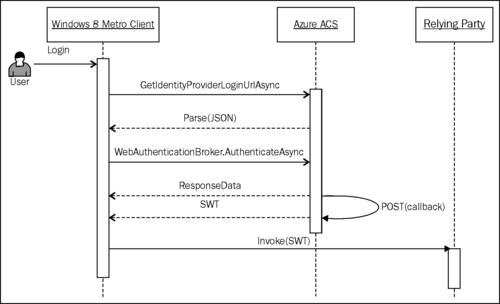
Information regarding the identity providers (name, logo, login URL, logout URL, and so on) registered in ACS is published in JSON format. The login URL for an identity provider can be retrieved by parsing the JSON string fetched by making a GET request to https://{0}.accesscontrol.windows.net/v2/metadata/IdentityProviders.js?protocol=wsfederation&realm={1}version=1.0.
WinRT exposes the PasswordVault class (Windows.Security.Credentials) that can be used to store a PasswordCredential object. This is particularly useful if you need to authenticate more than once and you don't want to be redirected every time to the identity provider. Use the ResponseData property to retrieve the credential information and store it in PasswordVault.
Vittorio Bertocci did a great talk on Identity and Access Management in the Build Conference. You can learn more about it at http://channel9.msdn.com/Events/BUILD/BUILD2011/SAC-858T. The demos used in the talk are packaged as samples with the Windows Azure Toolkit for Windows 8 which can be installed from http://watwindows8.codeplex.com/. You will need to run the setup script after extracting the contents of the Toolkit to make sure that all the dependencies are installed and the Visual Studio templates are appropriately configured.
