Windows Server 8 will feature Dynamic Access Control, based on claims that are part of the Kerberos token. Claims will be a first class citizen in Windows 8 and administrators will be able to configure them from the Active Directory Domain Services (AD DS) console. In addition to User claims, Windows 8 will have support for Device claims of the device accessing the resource. Dynamic Access Control lets you define claims-based Access Control Policies for a granular level of permission management on system resources. In this recipe, we will explore the steps to create a claims-based Access Control Policy and understand how the forthcoming enhancements .NET Framework 4.5 will leverage the support for claims in Windows Server 8.
The following are the prerequisites for creating a claims-based Access Control Policy:
- Windows Server 8 Developer Preview: You can download this installer from your MSDN account and create a Virtual Machine out of it using Virtual Box.
- Visual Studio 11 Developer Preview: You will need this to explore the changes related to Windows Identity Foundation in .NET Framework 4.5. You can download the preview from http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=27543.
- Active Directory Domain Services: This should be set up in the Windows Server 8 Developer Preview instance. From the Server Manager console, use the Add Roles wizard to add the AD DS role and configure the domain controller.
Follow these steps to create a claims-based Access Control Policy in Windows Server 8 using the Active Directory Domain Services console:
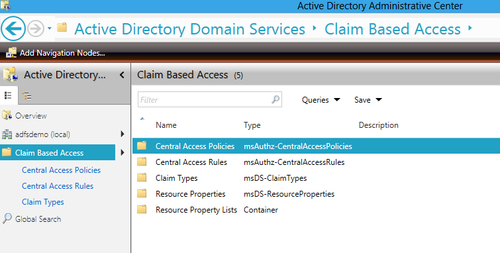
- In the Start screen, click on the Active Directory Administrative Center application:

- In the Active Directory Administrative Center console click on the Claim Based Access navigation node, as shown in the following screenshot:
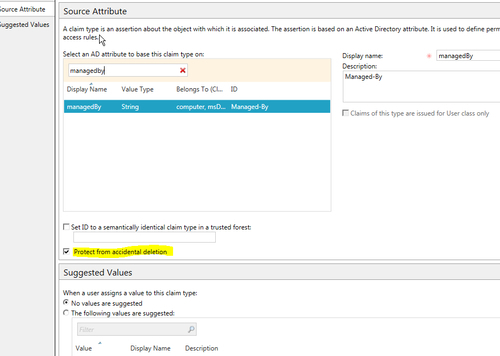
- Right-click on the Claim Types folder and go to New | Claim Type. As shown in the following screenshot, select the managedBy AD attribute from the Source Attribute section and check the Protect from accidental deletion checkbox. Click on OK to save:
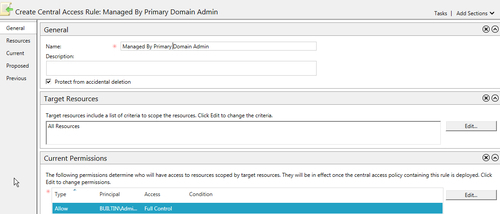
- Create a Central Access Rule by right-clicking on the Central Access Rules folder and then navigating to New | Central Access Rule. In the Create Central Access Rule, page specify the name as Managed By Primary Domain Admin under the General section. Under the Current Permissions section, click on Edit…:
- In the Advanced Security Settings for Current Permissions dialog box, remove all the entries except Administrators and click on Edit. The Permission Entry for Current Permissions dialog box is displayed. As shown in the following screenshot, add a new condition to check if the device is managed by the primary administrator ( adfsdemoadministrator, in our example):
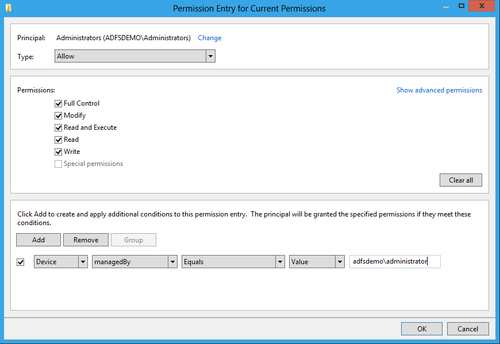
- Click on OK to save the changes. The condition should reflect under Current Permissions:

- Create a new Central Access Policy named Managed By Primary Domain Admin and associate the Managed By Primary Domain Admin Central Access Rule with it, as shown in the following screenshot:
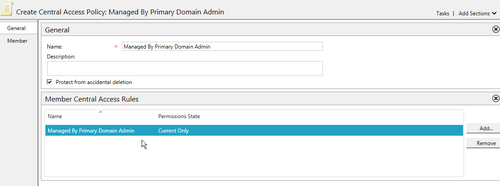
- You have now successfully set up a Central Access Policy.
The Central Access Policy you just created in Active Directory can now be applied to a file share in the file server and the policy will ensure that users will be able to access the files in the share only from devices that are managed by the primary administrator ( adfsdemoadministrator, in our example). The Managed By option can be set while creating a new Computer in Active Directory:
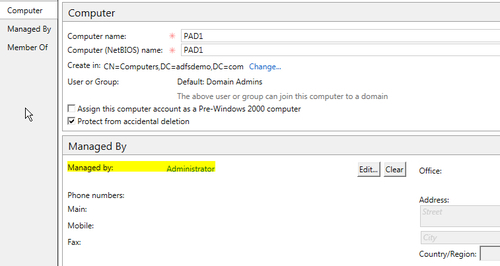
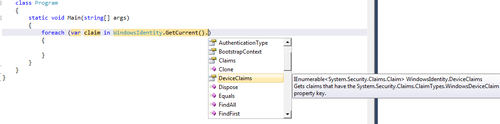
At an application level, .NET Framework 4.5 will have the ability to identify User as well as Device claims sourced from identity attributes in Active Directory, as shown in the following screenshot: