Microsoft Dynamics CRM Server 2011 is claims enabled and allows the users to authenticate through the trusted identity providers such as AD FS 2.0, Windows Azure ACS 2.0, and the federation metadata driven Security Token Services (for example, a custom STS implementation using WCF). In this recipe, we will take a look at the steps to enable the claims-based authentication support in Microsoft Dynamics CRM Server 2011 using the CRM Deployment Manager tool.
Access to a machine running an instance of Microsoft Dynamics CRM Server 2011 is necessary for executing the steps in this recipe. In addition, for the purpose of this recipe, we will assume that you have already configured a trusted identity provider (AD FS 2.0/ACS 2.0/Home-grown STS) with your Microsoft Dynamics CRM Server 2011 instance secure endpoint as a relying party. Your CRM Server must have an HTTPS binding configured for it to be available over a secure endpoint.
To implement claims-based authentication in Microsoft Dynamics CRM Server 2011, perform the following steps:
- Run the Microsoft Dynamics CRM Deployment Manager tool and open the Microsoft Dynamics CRM Properties dialog box. Click on the Web Address tab and select HTTPS as Binding Type.
Review the displayed URLs and click on OK to save the changes, as shown in the following screenshot:

- In the Deployment Manager tool, click on the Configure Claims-Based Authentication… link under the Actions pane. The Configure Claims-Based Authentication Wizard is launched:
- In the Specify the security token service step, specify the trusted Security Token Service metadata URL in the Federation metadata URL field. For the identity providers based on Microsoft's Identity and Access Control Paradigm, this would typically be the URL of the
FederationMetadata.xmlfile. Click on Next, as shown in the following screenshot:
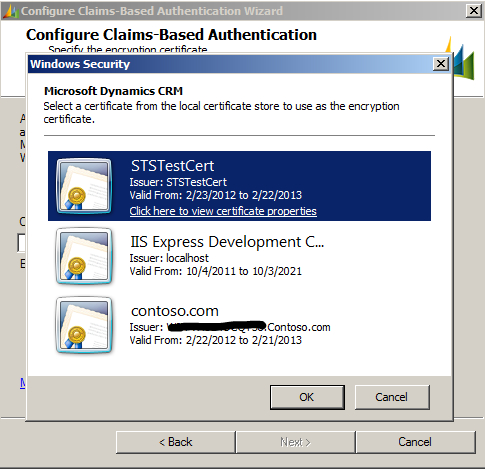
- In the Specify the encryption certificate step, select the STSTestCert certificate. Click on Next, as shown in the following screenshot:
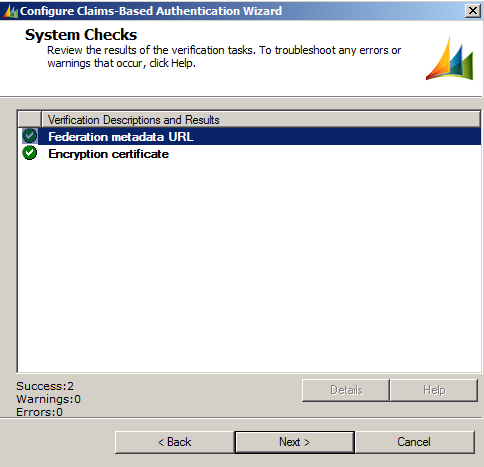
- Verify the changes and click on Next:
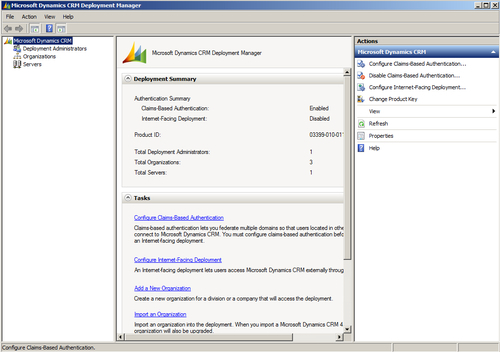
- Complete the wizard. The claims-based authentication is now enabled on your instance of Microsoft Dynamics CRM Server 2011:
After configuring the claims-based authentication in your CRM Server, you will be redirected to the sign-in page of the trusted identity provider instead of the default Windows credential prompt when you try to log in to the CRM Server website. On successful authentication, you will be logged into CRM Server.
Note
The CRM Application Pool account must have the permissions to read the certificate private key. Refer to Chapter 1, Overview of Claims-based Identity, for the steps to grant permission to access the private key information.
Enabling the claims-based authentication can also be scripted using the Microsoft.Crm.PowerShell snap-in for automated deployment. The following PowerShell command can be used for this purpose:
$settings = Get-CrmSetting -SettingType "ClaimsSettings"
$settings.Enabled = 1
$settings.EncryptionCertificate = "Encryption Certificate Name"
$settings.FederationMetadataUrl = "Federation Metadata URL of STS"
Set-CrmSetting $settings
To disable the claims-based authentication, in the Deployment Manager tool, click on the Disable Claims-Based Authentication… link under the Actions pane, as shown in the following screenshot:
In addition to the internal access, claims-based authentication can also be enabled for Internet-Facing Deployment (IFD) of a Microsoft Dynamics CRM Server 2011 instance. To configure IFD for the claims-based authentication, the IFD URL should be registered as a relying party with the trusted identity provider.
A detailed guide on configuring the claims-based authentication for Microsoft Dynamics CRM Server 2011 is available at http://www.microsoft.com/download/en/details.aspx?id=3621. You can learn more about the steps including a detailed walkthrough on configuring Microsoft Dynamics CRM for Outlook to use the claims-based authentication.
