As seen earlier, adb is a command-line tool that helps you to communicate with a device to retrieve information. Using adb, you can extract data from all of the files on the device or just the relevant files in which you are interested. This is the most widely used technique as part of logical extraction.
To access an Android device through adb, the USB debugging option must be enabled. From Android 4.2.2, due to secure USB debugging, the host connecting to the device should also be authorized. If the device is locked and USB debugging is not enabled, try to bypass the screen lock using the techniques explained in Chapter 8, Android Forensic Setup and Pre-Data Extraction Techniques.
As a forensic examiner, it's important for you to know how the data is stored on the Android device and to understand where important and sensitive information is stored so that the data can be extracted accordingly. Application data often contains a wealth of user data that may be relevant to the investigation. All files pertaining to applications of interest should be examined for relevance, as will be explained in Chapter 10, Android Data Analysis and Recovery. The application data can be stored in one of the following locations:
- Shared preferences: This stores data in key-value pairs in a lightweight XML format. Shared preference files are stored in the shared_pref folder of the application /data directory.
- Internal storage: This stores data that is private and is present in the device's internal memory. Files saved to the internal storage are private and cannot be accessed by other applications.
- External storage: This stores data that is public in the device's external memory, which does not usually enforce security mechanisms. This data is available in the /sdcard directory.
- SQLite database: This data is available in the /data/data/PackageName/ database. It is usually stored with the .db file extension. The data present in a SQLite file can be viewed using the SQLite browser (https://sourceforge.net/projects/sqlitebrowser/) or by executing the necessary SQLite commands on the respective files.
Every Android application stores data on the device using one or more of the preceding data storage options. So, the Contacts application would store all of the information about the contact details in the /data/data folder under its package name. Note that /data/data is a part of your device's internal storage, where all of the apps are installed under normal circumstances. Some application data will reside on the SD card and in the /data/data partition. Using adb, we can pull the data present in this partition for further analysis using the adb pull command. Once again, it's important to note that this directory is only accessible on a rooted phone.
SMS data location on old devices: /data/com.android.providers.telephony/databases/smsmms.db and SMS data location on Nougat devices: /user_de/0/com.android.providers.telephony/databases/smsmms.db.
On a rooted phone, the adb pull command on the databases folder of the Dropbox app can be executed as follows:

Similarly, on a rooted phone, the entire /data folder can be pulled in this manner. As shown in the following screenshot, the complete /data directory on the Android device can be copied to the local directory on the machine. The entire data directory was extracted in 97 seconds. The extraction time will vary depending on the amount of data residing in /data:
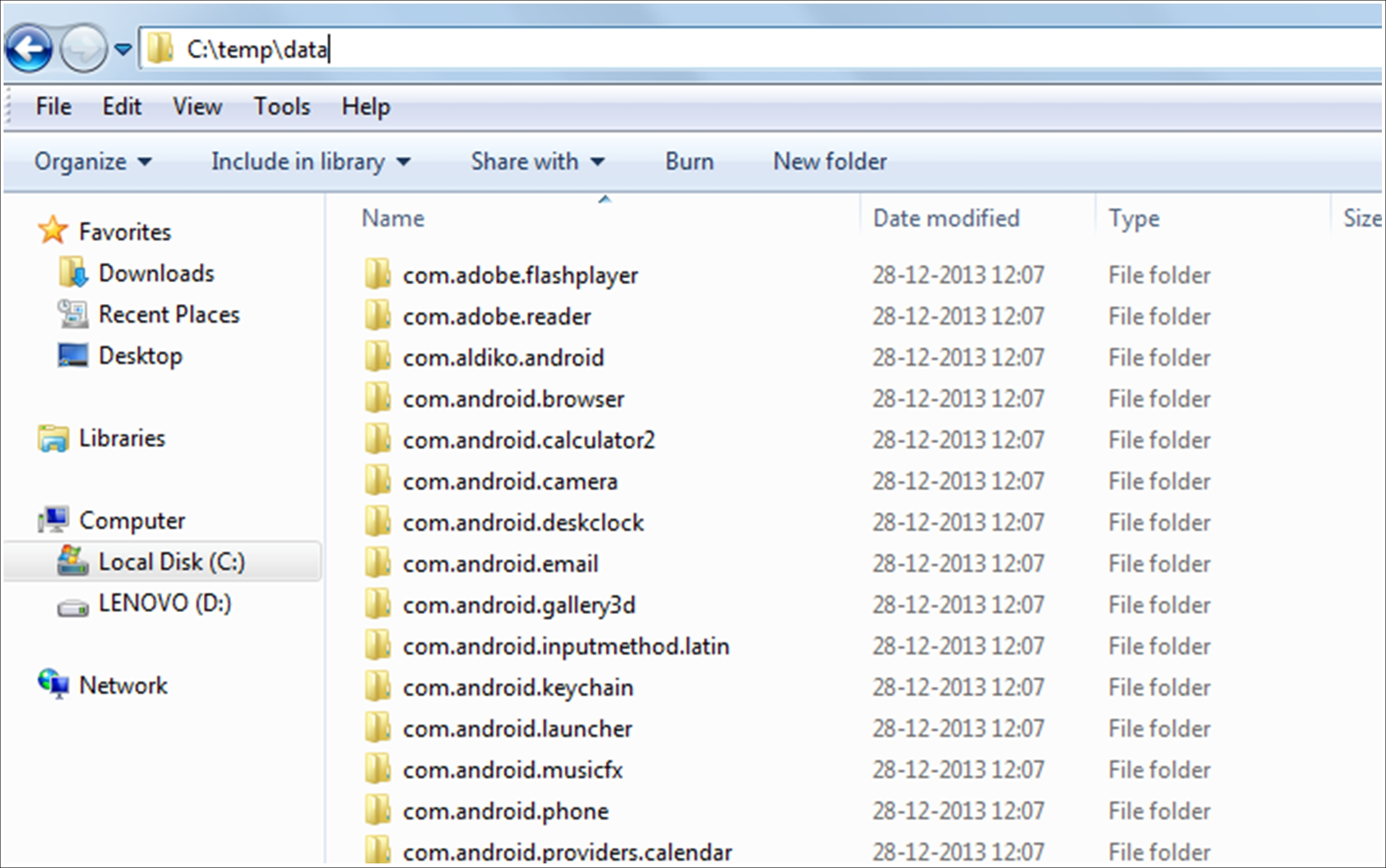
On a non-rooted device, a pull command on the /data directory does not extract the files, as shown in the following output, since the shell user does not have permission to access those files:
The data copied from a rooted phone through the preceding process maintains its directory structure, hence allowing an investigator to browse through the necessary files to gain access to the information. By analyzing the data of the respective applications, a forensic expert can gather critical information that can influence the outcome of the investigation. Note that examining the folders natively on your forensic workstation will alter the dates and times of the content. You should make a copy of the original output to use for a date/time comparison.
