Windows Phones may contain removable SD cards. These cards may be secured with a key that prevents the SD card from being removed and used, or accessed via other devices (phones, cameras, computers, and more). This is different from the key that is created if the user encrypts the SD card. Brute-force and dictionary attacks can be run on user-encrypted SD cards in an attempt to access the data. When examining a Windows Phone, it is best to research the device to see whether SD card security will be a factor when acquiring data from the device. If so, simply follow the preceding steps and acquire the SD card data through the phone during forensic extraction. Please refer to the following chart.
For devices where the SD card can be removed, you have two scenarios to consider. If the device is on, should you acquire the phone and the SD card as is? If the device is off, should you remove the SD card and acquire the device using FTK Imager? The answer is, it depends. In forensics, we use this statement frequently, but it remains true. If you leave the device on, it must be isolated from the network to ensure that it is not remotely accessed and immediately acquired, or the battery will drain and, ultimately, the device may power down. If the device is off and you remove the SD card, you must ensure that the card remains tied to the device itself and is acquired both externally and internally to ensure all data is captured. In a normal situation, the following chart suggests the recommended steps to handle SD cards that are found in Windows Phones:

Most commercial forensic tools will offer to extract data from SD cards. Often, the phone extraction process will only extract data residing on the SD card. This is often the case when there is no support for a specific Windows Phone. If the SD card is not recognized by the tool and the data is not extracted, it is likely that the SD card has been encrypted by the user, and the password for the device is different from the password for the SD card. When this occurs, try to crack the passcode and reacquire the device. Note that cracking a passcode on an SD card may not always be possible, but it's worth a shot trying brute-force and dictionary attacks as you would on a standard hard drive or external device.
When acquiring an SD that has been removed from a Windows Phone, FTK Imager is a free and reliable option to create a forensically sound image that can be examined in a variety of tools. To create an SD card image, follow these steps:
- Remove the SD card from the device and make sure to document all identifiers on the card and the phone to ensure that they are not permanently separated.
- Insert the SD card into a write blocker and insert this into your forensic workstation.
- Launch FTK Imager.
- Select File and then Create Disk Image.
- Select Physical Drive:
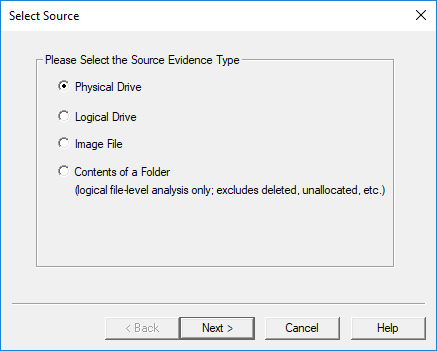
- Use the drop-down list to select the correct device.
- Select Finish.
- Click on Add and select the image type. For this example, Raw (dd) is going to be used as it is supported by most commercial and open source methods for analysis:
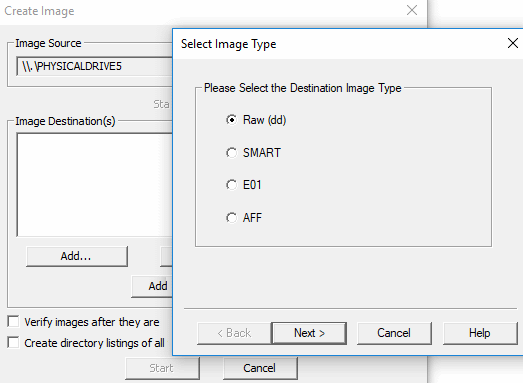
-
Enter the relevant case information and select Next. This can be skipped.
-
Select the image destination:
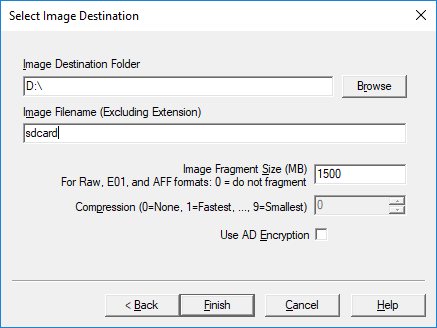
- Select Finish and then select Start. It is recommended that you verify images after they are created.
Once complete, your results will be displayed. We will cover analyzing the SD card data in the following sections.
