In some cases, the physical acquisition of Windows Phone devices is possible only with advance methods, such as JTAG and chip-off. But thanks to the security researcher known as Heathcliff, it became possible to perform physical acquisition on limited phone models and operating system versions with his tool called WPinternals (https://www.wpinternals.net).
The tool supports the following models of Lumia phones: 520, 521, 525, 620, 625, 720, 820, 920, 925, 928, 1020, and 1320.
As for operating system versions, the following are supported:
- 8.10.12393.890
- 8.10.12397.895
- 8.10.14219.341
- 8.10.14226.359
- 8.10.14234.375
- 8.10.15116.125
- 8.10.15148.160
- 10.0.10512.1000
- 10.0.10536.1004
- 10.0.10549.4
- 10.0.10581.0
- 10.0.10586.11
- 10.0.10586.36
The first step of the acquisition process will be downloading a Windows Full Flash Update (FFU) file and the emergency files for the phone model you are working with:

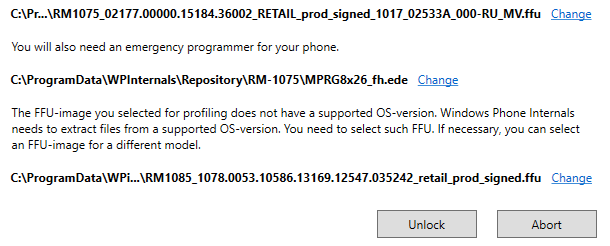
If the downloaded FFU contains an unsupported OS version, then WPinternals will download another FFU to get additional files:
During the unlocking process, the phone may reboot a couple of times, but this is a normal behavior:

Once the profile has been found, the tool flashes the unlocked bootloader:

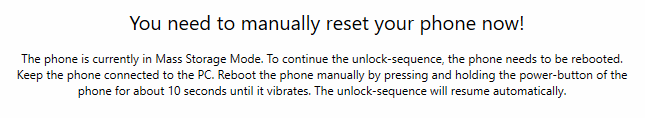
If the device has been flashed successfully, it's put into Mass Storage Mode:
Now, the device can be easily imaged, for example, using FTK Imager:

Now, we will learn how to extract data from SD cards.
