The Windows Phone filesystem is more or less similar to the filesystems used in Windows 7, Windows 8, and Windows 10. From the root directory, you can reach different files and folders that are available on this device. From a forensic perspective, the following are some of the folders that can yield valuable data. All the listed directories are located in the root directory:
- Application data: This directory contains data of applications on the phone, such as Outlook, Maps, and Internet Explorer.
- Applications: This directory contains the apps installed by the user. The isolated storage, which is allocated or used by each app, is also located in this folder.
- My Documents: This directory holds different Office documents, such as Word, Excel, or PowerPoint files. The directory also includes configuration files and multimedia files, such as music or videos.
- Windows: This directory contains files that are related to the Windows Phone operating system.
The acquisition method used here will determine the amount of filesystem access that you have to the device. For example, a physical image may provide access to several partitions that can be recovered from the data dump. A Windows Phone 10 device that contains 27 partitions can be seen in the following screenshot. Partitions 26 (MainOS) and 27 (Data) contain the relevant data:

The MainOS partition in the preceding screenshot, partition 26, contains the system data from the Windows Phone. As in all Windows investigations, the system data contains artifacts relevant to investigations.
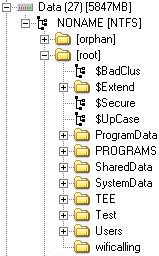
In this example, partition 27 contains the User or Data partition. Depending on the device, the partition numbers may vary. In our example, the Data partition is shown in the following screenshot as partition 27. Here, the SMS, email, application data, contacts, call logs, and internet history were recovered using mobile forensic tools. These methods will be discussed later in this chapter:
Windows Phone also maintains the Windows registry, a database that stores environment variables on the operating system. The Windows registry is basically a directory that stores settings and options for the Microsoft operating system. Windows Phone is no different. When examining a Windows Phone, you will expect to see the NTUSER.dat, SAM, SYSTEM, SOFTWARE, SECURITY, and DEFAULT hives. While these hives may be unique to the phone, they can be examined just like traditional Windows registry hives.
A detailed case investigation is included in a paper by Cynthia Murphy. This involves a criminal case of a home invasion and sexual assault and details the efforts of great minds in the forensic community to uncover artifacts that assisted in closing the investigation. Sometimes, the mobile device is the most important artifact pertaining to the case. For more information, please refer to https://www.sans.org/reading-room/whitepapers/forensics/windows-phone-8-forensic-artifacts-35787. Now that we have looked at the file and folder structure, let's learn how to acquire data using this knowledge.
