Before examining an iPhone, it is necessary to identify the correct hardware model and the firmware version installed on the device. Knowing the iPhone's details helps you to understand the criticalities and possibilities of obtaining evidence from an iPhone. For example, in many cases, the device passcode is required in order to obtain a logical image. Depending on the iOS version, device model, and passcode complexity, it may be possible to obtain the device passcode using a brute-force attack.
There are various ways to identify the hardware of a device. The easiest way to identify the hardware of some devices is to observe the model number displayed on the back of the device. To make this task even simpler, you can use Apple's Knowledge Base articles. More information on iPhone models can be found at https://support.apple.com/en-in/HT201296.
The firmware version of an iPhone can be found by accessing the Settings option and then navigating to General | About | Software Version, as shown in the following screenshot. The purpose of the firmware is to enable certain features and assist with the general functioning of the device:

Alternatively, the ideviceinfo command-line tool that is available in the libimobiledevice software library (http://www.libimobiledevice.org/) can be used to identify the iPhone model and its iOS version.
To obtain the iPhone model and its iOS version information on a Windows 10 workstation, follow these steps:
- Download the latest binaries from the following link: https://dev.azure.com/libimobiledevice-win32/imobiledevice-net/_build/results?buildId=419 (click on Artifacts | Binaries to start downloading).
- Unzip the archive with x86 or x64 binaries, depending on your workstation's version.
- Open Command Prompt and change the directory to the one with binaries (use the cd command for this).
- Connect the iPhone to your workstation using a Universal Serial Bus (USB) cable (for the latest iOS versions, the passcode is also required), and run the ideviceinfo command with the -s option, as shown in the following code:
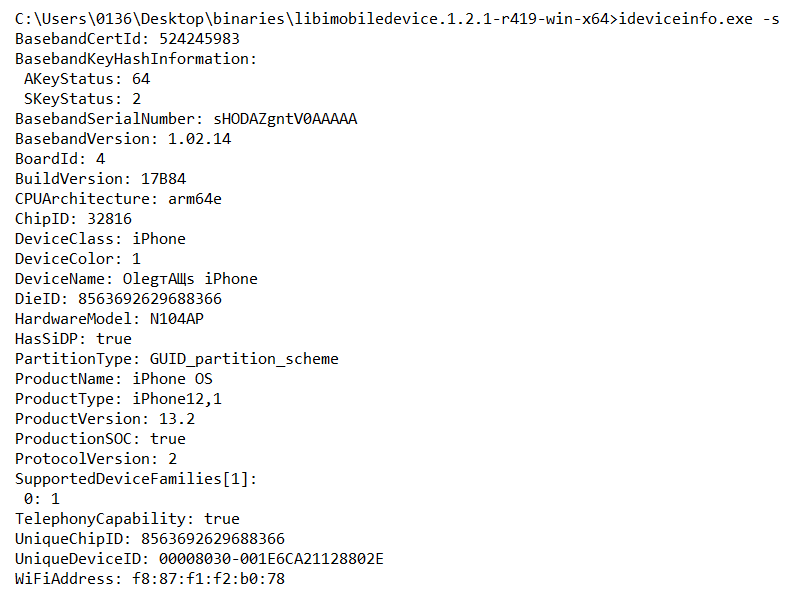
$ ideviceinfo -s
The output of the ideviceinfo command displays the iPhone identifier, its internal name, and the iOS version, as shown in the following screenshot:
Some other tools, such as iExplorer, will provide access to similar iOS device information, as shown in the following screenshot. The methods for recovering iPhone device information will work on iPad devices as well. Here, iExplorer is being used to obtain device information from an iPhone:

Every release of the iPhone comes with improved or newly added features. As previously stated in this chapter, knowing the iPhone's details helps you to understand the criticalities and possibilities of obtaining evidence from it. You must know the model of the device to ensure that the tools and methodologies being deployed support that particular iPhone. Additionally, the internal storage size of the iPhone must be determined to ensure that the evidence container is large enough for the entire forensic image. Most tools will not alert you if there is not enough disk space on the evidence drive until space has run out. This will waste time and force you to acquire the device a second time. Finally, the network capabilities of the device must also be noted so that you can properly isolate the device to prevent remote accessing or wiping during the examination. This will be discussed further in Chapter 3, Data Acquisition from iOS Devices.
Again, some familiarity with iPhone device hardware will aid you in determining how to handle the device during a forensic investigation. Certain models enforce full-disk encryption, while older models do not. Encrypted devices require additional steps during an acquisition—if access is even possible. You must be prepared for all hurdles you may be required to clear during the acquisition and analytical stages of the investigation. In addition to this, knowing the capabilities that the iPhone has—and the initial and current iOS version—makes a difference in the data you will be able to recover from the device. Apple is not consistent with data storage locations across iOS versions. Therefore, you must know the original version installed when the phone was first in use to ensure that the forensic tools do not overlook data that could aid in the investigation.
More information about identifying iPhone models can be found at https://support.apple.com/en-us/HT201296.
