From a forensic perspective, it's important to identify the presence of any malware on the device prior to performing any analysis. This is because malware can alter the state of the device or contents on the device, thereby making the analysis or the results inconsistent. There are tools available on the market that can analyze the physical extraction to identify malware. For example, Cellebrite UFED Physical Analyzer has BitDefender's anti-malware technology, which scans for malware. As shown in the following screenshot, once the physical image has been loaded into the tool, the file can be scanned for malware:

Once the scan starts, the BitDefender software tries to unpack the .apk files and looks for infected or malicious files. This process is automatic and the tool points to the malicious apps, as shown in the following screenshot:

The tool simply points out that something malicious is present on the device. The forensic investigator has to then manually confirm whether this is a valid issue by analyzing the respective application. This is where the reverse engineering skills that we discussed in the previous sections need to be leveraged. Once the application has been reverse-engineered and the code has been obtained, it is recommended that you take a look at the AndroidManifest.xml file to find out the app permissions. This will be helpful for understanding where the app stores the data, what resources it is trying to access, and more. For example, a Flashlight application does not need read/write access to your SD card data, or to make a phone call:
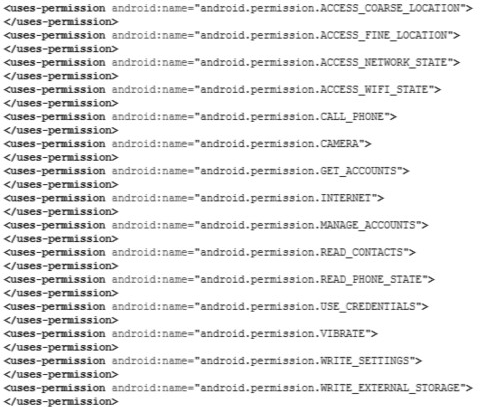
Alternatively, you can also upload the .apk file to VirusTotal, a free service that can be used to analyze suspicious files for malware. VirusTotal will scan your file against 55 antivirus engines. It's also important to note that the tool may not identify a valid case if the details are obfuscated in the .apk file. Hence, as a forensic investigator, it's important to develop the necessary skills to reverse engineer any suspicious apps and analyze the code to identify malicious behavior.
In some investigations, the nature of the malware that is present on a device may also result in arriving at certain crucial conclusions, which may affect the outcome of the case. For example, consider an internal investigation in a corporation that involves sending abusive messages to other employees. Identifying malware on the device that sends the messages would help solve the case.
