Autopsy is one of the best tools for filesystem examinations. Unfortunately, iOS parsing is not provided in Autopsy, but it still may be useful for filesystem images. Autopsy can be downloaded from http://sleuthkit.org/autopsy/. When using Autopsy, the Android Analyzer module will parse some application data from the device. Let's look at how to use Autopsy for Android image analysis.
To use Autopsy, download the software and install it on a Windows machine and follow these instructions. Make sure that you are always using the latest version:
- Launch Autopsy.
- Create a new case:
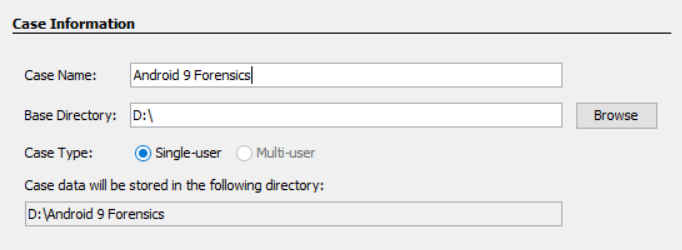
- Select Next and then click on Finish.
- Navigate to your image file and select Next.
- Select the modules that you wish to run. Keyword Search and Android Analyzer will be the most fruitful for an Android device:
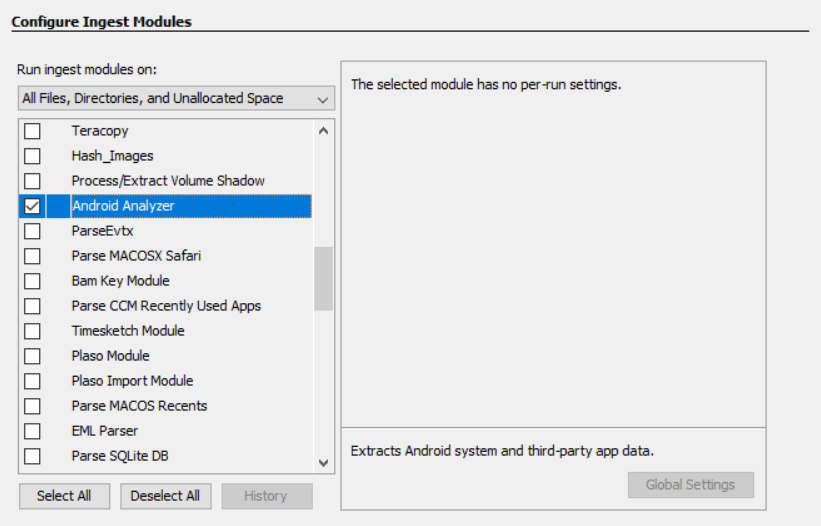
Ingest Modules are tools built into Autopsy that can be run when the case has started or at any point afterward. The default modules in this version of Autopsy are as follows:
- Recent Activity: This extracts recent user activity such as web browsing, recently used documents, and installed programs.
- Hash Lookup: This identifies known and notable files using supplied hash databases, such as a standard NSRL database. It also allows importing custom hash databases.
- File Type Identification: This matches file types based on binary signatures.
- Archive Extractor: This extracts archive files (.zip, .rar, .arj, .7z, .gzip, .bzip2, and .tar). It automatically extracts these file types and puts their contents into the directory tree.
- EXIF Parser: This ingests JPEG files and retrieves their EXIF metadata.
- Keyword Search: This performs file indexing and periodic search using keywords and regular expressions in lists. It allows the loading of custom keywords/lists.
- Email Parser: This module detects and parses mbox and pst/ost files and populates email artifacts in the blackboard.
- Extension Mismatch Detector: These are flag files that have a non-standard extension based on their file types.
- E01 Verifier: This validates the integrity of E01 files.
- Android Analyzer: This extracts Android system and third-party app data.
- Interesting Files Identifier: This identifies interesting items, as defined.
Also, you can install third-party modules for Autopsy. Some of them are really useful for Android forensics. A good example is Parse SQLite DB by Mark McKinnon. This module parses any SQLite database it finds and imports it into the extracted content. This and other modules can be downloaded from this GitHub: https://github.com/markmckinnon/Autopsy-Plugins
Autopsy provides access to filesystem data faster than any commercial or open source tool available. Knowing where to go from there is the hard part. So, again, start with anything that is in the extracted content and then dive into the filesystem to examine the files discussed in this book and any relevant application data, as shown in the following screenshot:

Once you have identified applications of interest, start with what is parsed and then examine the relevant database, cache, and preference files. Autopsy includes basic SQLite Viewer that can be used for triage purposes. If you need to run queries, we recommend using DB Browser for SQLite or browsers included in commercial products, for example, Belkasoft Evidence Center, especially if you want to analyze data from free lists and unallocated space.
Android Analyzer can decode some artifacts automatically, for example, contacts, calls, and SMS. The following screenshot shows the results of the decoded SMS messages:

Now, we will be looking at some more methods of extracting data.
