Apps that come preinstalled with the phone are stored in the /system/app directory. Third-party applications that are downloaded by the user are stored in the /data/app folder. The following method helps you gain access to the APK files on the device; it works on both rooted and non-rooted devices:
- Identify the package name of the app by issuing the # adb.exe shell pm list packages command.
The following is the output of the preceding command:
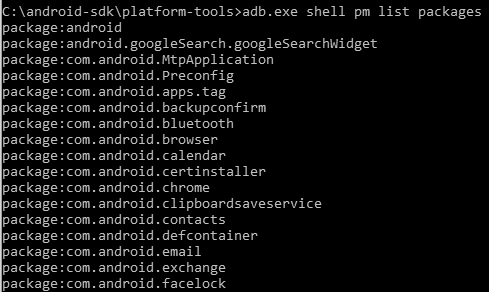
As shown in the preceding command-line output, the list of package names is displayed. Try to find a match between the app in question and the package name. Usually, the package names are very much related to the app names. Alternatively, you can use the Android Market or Google Play to identify the package name easily. The URL for an app in Google Play contains the package name, as shown in the following screenshot:

- Identify the full pathname of the APK file for the desired package by issuing the adb shell pm path command, as follows:
- Pull the APK file from the Android device to the forensic workstation using the adb pull command:
Now, let's analyze the contents of an APK file. An Android package is a container for an Android app's resources and executables. It's a zipped file that contains the following files:
- AndroidManifest.xml: This contains information about the permissions and more.
- classes.dex: This is the class file that's been converted into a dex file by the dex compiler.
- Res: The application's resources, such as the image files, sound files, and more, are present in this directory.
- Lib: This contains native libraries that the application may use.
- META-INF: This contains information about the application's signature and signed checksums for all the other files in the package.
Once the APK file has been obtained, you can proceed to reverse engineer the Android application.
