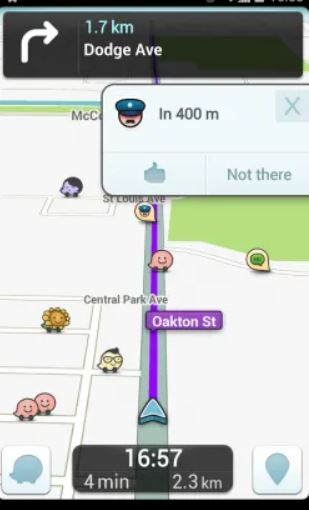
Most users branch out from their standard phone apps for GPS support. This includes getting directions to locations and obtaining maps for areas of interest. Common GPS applications include Waze and Google Maps. Waze goes beyond just providing directions, as it also alerts the user to road hazards, traffic, and police officers that are to be found along the route they are driving:
Other applications that store location information include Twitter, Instagram, Facebook, and Foursquare. These applications enable a user to alert friends and followers to their location when they create a post or share an image or video. All of these transactions are tracked within the app. Understanding this is key to uncovering additional artifacts that are not reported by your forensic tool.
When examining location information from GPS applications, it is best to assume that you need to manually examine the databases and preference files that are associated with that application. We recommend using your forensic tool to triage the data on the device and then dive deeply into the artifacts, which will be discussed later in this chapter. An example of Waze being parsed by UFED Physical Analyzer can be found in the following screenshot. Here, we can see that the user had 5 favorite locations, 74 mapped locations, and 70 recent directions. All of this information must be manually verified if it pertains to the investigation. This is because the tool cannot determine whether the user typed the address, whether it was suggested, or whether the user even traveled to that location. Proper skills are required by you to tie a user to a specific location, and this takes more than a forensic tool:

We will now analyze some of the popular secure messaging apps.
