One of the benefits of open source technology in general and Linux in particular is that it is now mature enough to be used effortlessly across several different networking environments as well as the Internet. With strong support for the standard Internet protocol TCP/IP, Linux can also talk to all of the UNIX flavors, including Mac OS X, Windows (with the help of Samba), NetWare (IPX), and even older protocols such as DECNET and Banyan Vines. Many organizations use Linux as an Internet gateway, allowing many different clients to access the Internet through Linux, as well as communicate via email and instant messaging. This chapter covers network and Internet connectivity, as most networks invariably end up connected to the Internet in some shape or form. You will learn about how to get the basics right, including configuration and management of network cards (NICs) and other network services with Fedora. You will also find out how to manage network services from the command line—again an important lesson in case you are ever confined to a command prompt. We will also look at connectivity options, both for inbound and outbound network traffic and the importance of PPP (Point to Point Protocol). Also included is an overview of graphical management clients for Fedora, which are becoming more and more popular.
The first thing that needs to happen before you can successfully connect to a network or even to the Internet is to create a localhost interface, sometimes also called a loopback interface, but more commonly referenced as lo. The TCP/IP protocol (see “Networking with TCP/IP” later on in this chapter) uses this interface to assign an IP address to your computer and is needed for Fedora to establish a PPP interface.
You should not normally have to manually create a loopback interface as Fedora creates one automatically for you during installation. To check that one is set up, you can use the ifconfig command while working as root to show something similar to this:
# /sbin/ifconfig
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:12 errors:0 dropped:0 overruns:0 frame:0
TX packets:12 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:760 (760.0 b) TX bytes:760 (760.0 b)
What you see in this example is evidence that the loopback interface is present and active. The inet addr is the IP number assigned to the localhost, typically 127.0.0.1 along with the broadcast mask of 255.255.255.0 and that there has been little activity on this interface (RX = receive and TX = transmit). If your output does not look like the one above, you must hand-configure the localhost interface after you finish the rest of this section.
The localhost interface’s IP address is specified in a text configuration file that is used by Fedora to keep record of various network-wide IP addresses. The file is called /etc/hosts and usually exists on a system, even if it is empty. The file is used by the Linux kernel and other networking tools to enable them to access local IP addresses and hostnames. If you have not configured any other networking interfaces then you may find that the file only contains one line:
127.0.0.1 localhost.localdomain localhost
This line defines the special localhost interface and assigns it an IP address of 127.0.0.1. You might hear or read about terms such as localhost, loopback, and dummy interface; all these terms refer to the use of the IP address 127.0.0.1. The term loopback interface indicates that to Linux networking drivers, it looks as though the machine is talking to a network that consists of only one machine; the kernel sends network traffic to and from itself on the same computer. Dummy interface indicates that the interface doesn’t really exist as far as the outside world is concerned; it exists only for the local machine.
Each networked Fedora machine on a LAN will use this same IP address for its localhost. If for some reason a Fedora computer does not have this interface, edit the /etc/hosts file to add the localhost entry, and then use the ifconfig and route commands as root to create the interface like this:
# /sbin/ifconfig lo 127.0.0.1 # /sbin/route add 127.0.0.1 lo
These commands will create the localhost interface in memory (all interfaces, such as eth0 or ppp0, are created in memory when using Linux), and then add the IP address 127.0.0.1 to an internal (in-memory) table so that the Linux kernel’s networking code can keep track of routes to different addresses.
Use the ifconfig command as shown previously to test the interface.
You should now be able to use ping to check that the interface is responding properly like this (using either localhost or its IP address):
# /bin/ping -c 3 localhost
PING localhost.localdomain (127.0.0.1) from 127.0.0.1 : 56(84) bytes of data.
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=0 ttl=255 time=212
usec
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=1 ttl=255 time=80 usec
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=2 ttl=255 time=50 usec
--- localhost.localdomain ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/mdev = 0.050/0.114/0.212/0.070 ms
The -c option is used to set the number of pings, and the command, if successful (as it was previously), returns information regarding the round-trip speed of sending a test packet to the specified host.
The basic building block for any network based on Unix hosts is the Transport Control Protocol/Internet Protocol (TCP/IP) suite of three protocols. The suite consists of the Internet Protocol (IP), Transport Control Protocol (TCP), and Universal Datagram Protocol (UDP). IP is the base protocol. The TCP/IP suite is packet-based, which means that data is broken into little chunks on the transmit end for transmission to the receiving end. Breaking data up into manageable packets allows for faster and more accurate transfers. In TCP/IP, all data travels via IP packets, which is why addresses are referred to as IP addresses. It is the lowest level of the suite.
TCP is a connection-based protocol. Before data is transmitted between two machines, a connection is established between them. When a connection is made, a stream of data is sent to the IP to be broken into the packets that are then transmitted. At the receiving end, the packets are put back in order and sent to the proper application port. TCP/IP forms the basis of the Internet; without it the Internet would be a very different place indeed, if it even existed!
On the other hand, UDP is a connectionless protocol. Applications using this protocol just choose their destination and start sending. UDP is normally used for small amounts of data or on fast and reliable networks. If you are interested in the internals of TCP/IP, see the “Reference” section at the end of this chapter for places to look for more information.
To understand networking with Linux, you need to know the basics of TCP/IP addressing. Internet IP addresses (also known as public IP addresses) are different from those used internally on a local area network, or LAN. Internet IP addresses are assigned (for the United States and some other hosts) by the American Registry for Internet Numbers, available at http://www.arin.net/. Entities that need an Internet address apply to this agency to be assigned an address. The agency assigns Internet service providers (ISPs) one or more blocks of IP addresses, which the ISPs can then assign to their subscribers.
You will quickly recognize the current form of TCP/IP addressing, known as IPv4 (IP version 4). In this method, a TCP/IP address is expressed of a series of four decimal numbers—a 32-bit value expressed in a format known as dotted decimal format, such as 192.168.120.135. Each set of numbers is known as an octet (eight ones and zeros, such as 10000000 to represent 128) and ranges from zero to 255.
The first octet usually determines what class the network belongs to. There are three classes of networks. The classes are
Class A—. Consists of networks with the first octet ranging from 1 to 126. There are only 126 Class A networks—each composed of up to 16,777,214 hosts. (If you are doing the math, there are potentially 16,777,216 addresses, but no host portion of an address can be all zeros or 255s.) The “10.” network is reserved for local network use, and the “127.” network is reserved for the loopback address of 127.0.0.1. Loopback addressing is used by TCP/IP to enable Linux network-related client and server programs to communicate on the same host. This address will not appear and is not accessible on your LAN.
Note
Notice that zero is not included in Class A. The zero address is used for network-to-network broadcasts. Also, note that there are two other classes of networks, Classes D and E. Class D networks are reserved for multicast addresses and not for use by network hosts. Class E addresses are deemed experimental, and thus are not open for public addressing.
Class B—. Consists of networks defined by the first two octets with the first ranging from 128 to 191. The “128.” network is also reserved for local network use. There are 16,382 Class B networks—each with 65,534 possible hosts.
Class C—. Consists of a network defined by the first three octets with the first ranging from 192 to 223. The “192.” network is another that is reserved for local network use. There are a possible 2,097,150 Class C networks of up to 254 hosts each.
No host portion of an IP address can be all zeros or 255s. These addresses are reserved for broadcast addresses. IP addresses with all zeros in the host portion are reserved for network-to-network broadcast addresses. IP addresses with all 255s in the host portion are reserved for local network broadcasts. Broadcast messages are not typically seen by users.
These classes are the standard, but a netmask also determines what class your network is in. The netmask determines what part of an IP address represents the network and what part represents the host. Common netmasks for the different classes are
Class A—. 255.0.0.0
Class B—. 255.255.0.0
Class C—. 255.255.255.0
Because of the allocation of IP addresses for Internet hosts, it is now impossible to get a Class A network. It is also nearly impossible to get a Class B network (all the addresses have been given out, but some companies are said to be willing to sell theirs), and Class C network availability is dropping rapidly with the current growth of Internet use worldwide. See the following sidebar.
Three blocks of IP addresses are reserved for use on internal networks and hosts not directly connected to the Internet. The address ranges are from 10.0.0.0 to 10.255.255.255, or 1 Class A network; from 172.16.0.0 to 172.31.255.255, or 16 Class B networks; and from 192.168.0.0 to 192.168.255.255, or 256 Class C networks. Use these IP addresses when building a LAN for your business or home. Which class you choose can depend on the number of hosts on your network.
Internet access for your internal network can be provided by a PC running Fedora or other broadband or dial-up router. The host or device is connected to the Internet and is used as an Internet gateway to forward information to and from your LAN. The host should also be used as a firewall to protect your network from malicious data and users while functioning as an Internet gateway.
A PC used in this fashion typically has at least two network interfaces. One is connected to the Internet with the other connected to the computers on the LAN (via a hub or switch). Some broadband devices also incorporate four or more switching network interfaces. Data is then passed between the LAN and the Internet using network address translation, or NAT, better known in Linux circles as IP masquerading. See Chapter 35, “Securing Your Machines,” for more information.
Note
Do not rely on a single point of protection for your LAN, especially if you use wireless networking, provide dial-in services, or allow mobile (laptop or PDA) users internal or external access to your network. Companies, institutions, and individuals relying on a “moat mentality” have often discovered to their dismay that such an approach to security is easily breached. Make sure that your network operation is accompanied by a security policy that stresses multiple levels of secure access, with protection built into every server and workstation—something easily accomplished when using Linux.
Most servers on your network have more than one task. For example, web servers have to serve both standard and secure pages. You might also be running an FTP server on the same host. For this reason, applications are provided ports to use to make “direct” connections for specific software services. These ports help TCP/IP distinguish services so that data can get to the correct application. If you check the file /etc/services, you will see the common ports and their usage. For example, for FTP, HTTP, and Post Office Protocol (email retrieval server), you will see
ftp 21/tcp http 80/tcp www www-http # WorldWideWeb HTTP pop3 110/tcp pop-3 # POP version 3
The ports defined in /etc/services in this example are 21 for FTP, 80 for HTTP, and 110 for POP3. Other common port assignments are 25 for simple mail transport protocol (SMTP) and 22 for secure shell (SSH) remote login. Note that these ports are not set in stone, and you can set up your server to respond to different ports. For example, although port 22 is listed in /etc/services as a common default for SSH, the sshd server can be configured to listen on a different port by editing its configuration file /etc/ssh/sshd_config. The default setting (commented out with a pound sign) looks like this:
#Port 22
Edit the entry to use a different port, making sure to select an unused port number, such as
Port 2224
Save your changes, and then restart the sshd server. (Refer to Chapter 15, “Automating Tasks,” to see how to restart a service.) Remote users must now access the host through port 2224, which can be done using ssh’s -p (port) option like so:
$ ssh -p 2224 remote_host_name_or_IP
Properly organizing your network addressing process grows more difficult as the size of your network grows. Setting up network addressing for a Class C network with fewer than 254 devices is simple. Setting up addressing for a large, worldwide company with a Class A network and many different users can be extremely complex. If your company has fewer than 254 hosts (meaning any device that requires an IP address, including computers, printers, routers, switches, and other devices) and all your workgroups can share information, a single Class C network will be sufficient.
Within Class A and B networks, there can be separate networks called subnets. Subnets are considered part of the host portion of an address for network class definitions. For example, in the 128. Class B network, you can have one computer with an address of 128.10.10.10 and another with an address of 128.10.200.20; these computers are on the same network (128.10.), but they have different subnets (128.10.10. and 128.10.200.). Because of this, communication between the two computers requires either a router or a switch. Subnets can be helpful for separating workgroups within your company.
Often subnets can be used to separate workgroups that have no real need to interact with or to shield from other groups information passing among members of a specific workgroup. For example, if your company is large enough to have its own HR department and payroll section, you could put those departments’ hosts on their own subnet and use your router configuration to limit the hosts that can connect to this subnet. This configuration prevents networked workers who are not members of the designated departments from being able to view some of the confidential information the HR and payroll personnel work with.
Subnet use also enables your network to grow beyond 254 hosts and share IP addresses. With proper routing configuration, users might not even know they are on a different subnet from their co-workers. Another common use for subnetting is with networks that cover a wide geographic area. It is not practical for a company with offices in Chicago and London to have both offices on the same subnet, so using a separate subnet for each office is the best solution.
Subnet masks are used by TCP/IP to show which part of an IP address is the network portion and which part is the host. Subnet masks are usually referred to as netmasks. For a pure Class A network, the netmask would be 255.0.0.0; for a Class B network, the netmask would be 255.255.0.0; and for a Class C network, the netmask would be 255.255.255.0. Netmasks can also be used to deviate from the standard classes.
By using customized netmasks, you can subnet your network to fit your needs. For example, your network has a single Class C address. You have a need to subnet your network. Although this isn’t possible with a normal Class C subnet mask, you can change the mask to break your network into subnets. By changing the last octet to a number greater than zero, you can break the network into as many subnets as you need.
For more information on how to create customized subnet masks, see Day 6, “The Art of Subnet Masking,” in Sams Teach Yourself TCP/IP Network Administration in 21 Days. That chapter goes into great detail on how to create custom netmasks and explains how to create an addressing cheat sheet for hosts on each subnet. You can also browse to the Linux Network Administrator’s Guide and read about how to create subnets at http://www.tldp.org/LDP/nag2/index.html.
Information can get to systems through three types of addresses: unicast, multicast, and broadcast. Each type of address is used according to the purpose of the information being sent, as explained here:
Unicast—. Sends information to one specific host. Unicast addresses are used for Telnet, FTP, SSH, or any other information that needs to be shared in a one-to-one exchange of information. Although it is possible that any host on the subnet/network can see the information being passed, only one host is the intended recipient and will take action on the information being received.
Multicasting—. Broadcasts information to groups of computers sharing an application, such as a video conferencing client or online gaming application. All the machines participating in the conference or game require the same information at precisely the same time to be effective.
Broadcasting—. Transmits information to all the hosts on a network or subnet. Dynamic Host Configuration Protocol (DHCP) uses broadcast messages when the DHCP client looks for a DHCP server to get its network settings, and Reverse Address Resolution Protocol (RARP) uses broadcast messages for hardware address to IP address resolution. Broadcast messages use .255 in all the host octets of the network IP address. (10.2.255.255 will broadcast to every host in your Class B network.)
As stated at the beginning of this chapter, networking is one of the strong points of the Linux operating system. This section covers the classes of devices used for basic networking. Note that this section talks about hardware devices, and not Linux networking devices, which are discussed in the section “Using Network Configuration Tools.”
A computer must have a network interface card (NIC) to connect to a network. Currently, there are several topologies (ways of connecting computers) for network connections. These topologies range from the old and mostly outdated 10BASE-2 to the much newer and popular wireless Wi-Fi or 802.11 networking.
Each NIC has a unique address (the hardware address, known as media access control, or MAC), which identifies that NIC. This address is six pairs of hexadecimal bits separated by colons (:). A MAC address looks similar to this: 00:60:08:8F:5A:D9. The hardware address is used by DHCP (see “DHCP” later in this chapter) to identify a specific host. It is also used by the Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP) to map hosts to IP addresses.
This section covers some of the different types of NIC used to connect to your network.
Token ring networking was developed by IBM. As the name implies, the network is set up in a ring. A single token is passed from host to host, indicating the receiving host’s permission to transmit data.
Token ring has a maximum transfer rate of 16Mbps (16 million bits per second). Unlike 10BASE-2 and 10BASE-5, token ring uses what is called unshielded twisted pair (UTP) cable. This cable looks a lot like the cable that connects your phone to the wall. Almost all token ring NICs are recognized by Linux.
10BASE-T was the standard for a long time. A large number of networks still use it. 10BASE-T also uses UTP cable. Instead of being configured in a ring, 10BASE-T mostly uses a star architecture. In this architecture, the hosts all connect to a central location (usually a hub, which you learn about later in the section titled “Hubs and Switches”). All the data is sent to all hosts, but only the destination host takes action on individual packets. 10BASE-T has a transfer rate of 10Mbps.
10BASE-T has a maximum segment length of 100 meters. There are many manufacturers of 10BASE-T NICs, and most are recognized by Fedora.
100BASE-T was popular around the turn of the millennium, keeping the same ease of administration as 10BASE-T while increasing the speed by a factor of 10. For most networks, the step from 10BASE-T to 100BASE-T is as simple as replacing NICs and hubs. Most 100BASE-T NICs and hubs can also handle 10BASE-T and can automatically detect which is in use. This allows for a gradual network upgrade and usually does not require rewiring your whole network. Nearly every known 100BASE-T NIC and most generic NICs are compatible with Linux, thanks to Donald Becker of http://www.scyld.com/. 100BASE-T requires category 5 unshielded twisted pair cabling.
1000BASE-T—usually referred to as gigabit ethernet—is the accepted standard in enterprise networking, with most NICs being detected and configured correctly by Fedora. Like 100BASE-T NICs, gigabit NICs automatically downgrade if they are plugged in to a slower network. Also like 100BASE-T, gigabit NICs require category 5 unshielded twisted pair cabling; however, many institutions are now deploying category 6 cables because they have much longer range and so are often worth the extra cost. You will find that many newer computers tend to be fitted with gigabit NICs as standard.
Fiber optic is more commonly used in newer and high-end installations because the cost of upgrading can be prohibitive for older sites.
Fiber optics were originally used on fiber distributed data interface (FDDI) networks, similar to token ring in structure except that there are two rings—one is primary, whereas the other is secondary. The primary ring is used exclusively, and the secondary sits idle until there is a break in the primary ring. At this point, the secondary ring takes over, keeping the network alive. FDDI has a speed of 100Mbps and has a maximum ring length of 62 miles. FDDI uses several tokens at the same time that, along with the faster speed of fiber optics, account for the drastic increase in network speed.
As stated, switching to a fiber optic network can be very costly. To make the upgrade, the whole network has to be rewired (as much as U.S. $150 per network connection), and all NICs must be replaced at the same time. Most FDDI NICs are recognized by Linux.
Fiber-related gigabit is termed 1000BASE-X, whereas 1000BASE-T gigabit ethernet uses twisted-pair (see the “Unshielded Twisted Pair” section, later in this chapter).
Wireless has really taken off in the past year or two. Wireless networking, as the name states, works without network cables. Upgrading is as easy as replacing network cards and equipment, such as routers and switches. Wireless networking equipment can also work along with the traditional wired networking using existing equipment.
It might not be practical to upgrade a desktop or large server to wireless just yet if the wiring is already in place. Wireless networking is still generally slower than a traditional wired network. However, this situation is changing with wider adoption of newer protocols, such as 802.11g (supporting the common 802.11b and faster but less popular 802.11a), along with the introduction of more compliant and inexpensive wireless NICs. Some 802.11g NICs work at up to 108Mbps, which appears faster than 100BASE-T wired networking on the surface. However, in practice, it is a great deal slower: Unless your networking environment has paper-thin walls, you can usually halve the reported speed of Wi-Fi network devices. 108Mbps works about half the speed of 100BASE-T.
Over the past few years, wireless networking has really taken off for home users. No longer do you have to go around on your hands and knees, running cables around your home. Instead you can install a central wireless router, and with a couple of wireless NICs and PC cards, you can have a safe and secure wireless network. Thankfully, with each new version of Linux, more and more wireless NICs are compatible. (That said, it is usually better to get brand name wireless NICs, because you have a better chance of compatibility.) Check the http://www.hpl.hp.com/personal/Jean_Tourrilhes/Linux/ web page for more specific hardware compatibility information. More on wireless networking is discussed later in this chapter.
Currently, three types of network cable exist: coaxial, unshielded twisted pair (UTP), and fiber. Coaxial cable (rarely used today) looks a lot like the coaxial cable used to connect your television to the cable jack or antenna. UTP looks a lot like the cable that runs from your phone to the wall jack (the jacks are a bit wider). Fiber cable looks sort of like the RCA cables used on your stereo or like the cable used on your electrical appliances in your house (two separate segments connected together). The following sections discuss UTP and fiber network cable in more detail.
Unshielded twisted pair (UTP) uses color-coded pairs of thin copper wire to transmit data. Six categories of UTP exist—each serving a different purpose:
Category 1 (Cat1)—. Used for voice transmissions such as your phone. Only one pair is used per line—one wire to transmit and one to receive. An RJ-11 plug is used to connect the cable to your phone and the wall.
Category 2 (Cat2)—. Used in early token ring networks. Has a transmission rate of 4Mbps (million bits per second) and has the slowest data transfer rate. An RJ-11 plug is also used for cable connections.
Category 3 (Cat3)—. Used for 10BASE-T networks. It has a transmission rate of 10Mbps. Three pairs of cables are used to send and receive signals. RJ-11 or RJ-45 plugs can be used for Cat3 cables, usually deferring to the smaller RJ-11. RJ-45 plugs are similar in design to RJ-11, but are larger to handle up to four pairs of wire and are used more commonly on Cat5 cables.
Category 4 (Cat4)—. Used in modern token ring networks. It has a transmission rate of 16Mbps and is less and less common as companies are switching to better alternatives. RJ-45 plugs are used for cable connections.
Category 5 (Cat5)—. The fastest of the UTP categories with a transmission rate of up to 1000Mbps. It is used in both 100BASE-T and 1000BASE-T networks and uses four pairs of wire. Cat5 cable came out just as 10BASE-T networks were becoming popular and isn’t much more expensive than Cat3 cable. As a result, most 10BASE-T networks use Cat5 UTP instead of Cat3. Cat5 cable uses RJ-45 plugs.
Category 6 (Cat6)—. Also rated at 1000Mbps, this cable is available in two forms: stranded for short runs (25-meter) and solid for up to 100-meter runs, but which should not be flexed.
Fiber optic cable (fiber) is usually orange or red in color. The transmission rate is 100Mbps and has a maximum length of 62 miles. Fiber uses a two-pronged plug to connect to devices. A couple of advantages to fiber are that because it uses light instead of electricity to transmit its signal, it is free from the possibility of electromagnetic interference and is also more difficult to tap into and eavesdrop.
Hubs and switches are used to connect several hosts together on a star architecture network. They can have any number of connections; the common sizes are 4, 8, 16, 24, and 48 connections (ports)—each port has a light that comes on when a network connection is made (link light). Their use enables you to expand your network easily; you can just add new hubs or switches when you need to add new connections. Each unit can connect to the other hubs or switches on the network, typically, through a port on the hub or switch called an uplink port. This enables two hubs or switches, connected by their uplink ports, to act as one hub or switch. Having a central location where all the hosts on your network can connect allows for easier troubleshooting of problems. If one host goes down, none of the other hosts are affected (depending on the purpose of the downed host). Because hubs and switches are not directly involved with the Linux operating system, compatibility is not an issue.
If you are constructing a small to mid-size network, it is important to consider whether you intend to use either hubs or switches. Hubs and switches are visually the same in that they have rows of network ports. However, under the hood, the difference is quite important. Data is sent as packets of information across the network; with a hub the data is transmitted simultaneously to all the network ports, irrespective of which port the destination computer is attached to.
Switches, however, are more intelligent because they can direct packets of information directly to the correct network port that leads to the destination computer. They do this by “learning” the MAC addresses of each computer that is attached to them. In short, using switches minimizes excess packets being sent across the network, thus increasing network bandwidth. In a small network with a handful of computers, the use of hubs might be perfectly acceptable and you will find that hubs are generally cheaper than switches. However, for larger networks of 15 computers or more, you might want consider implementing a switched network.
Tip
Troubleshooting network connections can be a challenge, especially on large networks. If a user complains that he has lost his network connection, the hub is a good place to start. If the link light for the user’s port is lit, chances are the problem is with the user’s network configuration. If the link light is not on, the host’s NIC is bad, the cable is not inserted properly, or the cable has gone bad for some reason.
Routers and bridges are used to connect different networks to your network and to connect different subnets within your network. Routers and bridges both serve the same purpose of connecting networks and subnets, but they do so with different techniques. The information in the following sections will help you choose the connection method that best suits your needs.
Bridges are used within a network to connect different subnets. A bridge blindly relays all information from one subnet to another without any filtering and is often referred to as a dumb gateway. This can be helpful if one subnet in your network is becoming overburdened and you need to lighten the load. A bridge is not very good for connecting to the Internet, however, because it lacks filtering. You really do not want all traffic traveling the Internet to be able to get through to your network.
Routers can pass data from one network to another, and they allow for filtering of data. Routers are best suited to connect your network to an outside network, such as the Internet. If you have a web server for an internal intranet that you do not want people to access from the Internet, for example, you can use a router’s filter to block port 80 from your network. These filters can be used to block specific hosts from accessing the Internet as well. For these reasons, routers are also called smart gateways.
Routers range in complexity and price from a Cisco brand router that can cost thousands of dollars to other brands that can be less than two hundred dollars. You are most likely to come into contact with a router if you have a broadband Internet connection to your home or small office. Users who have DSL connections need a router with a built-in DSL modem to connect to their ISP. It is also very common to have a wireless element built into the router, so you end up with a wired and wireless router with an internal DSL modem.
All the initial network configuration and hardware initialization for Fedora is normally done during installation. At times, however, you will have to reconfigure networking on your system, such as when a host needs to be moved to a different subnet or a different network, or if you replace any of your computer’s networking hardware.
Linux creates network interfaces in memory when the kernel recognizes that a NIC or other network device is attached to the system. These interfaces are unlike other Linux interfaces, such as serial communications ports, and do not have a corresponding device file in the /dev directory. Unless support for a particular NIC is built in to your kernel, Linux must be told to load a specific kernel module to support your NIC. More than 100 such modules are located in the /lib/modules/2.6.XX-XX/kernel/drivers/net directory (where XX-XX is your version of the kernel).
You can initialize a NIC in several ways when using Linux. When you first install Fedora, automatic hardware probing detects and configures your system to use any installed NICs. If you remove the original NIC and replace it with a different make and model, your system will not automatically detect and initialize the device unless you configure Fedora to use automatic hardware detection when booting. If you have enabled the kudzu hardware daemon, (refer to Chapters 7, “Managing Software,” and 15, “Automating Tasks”), it detects the absence of the old NIC and the presence of the new NIC at boot time and prompts you for permission to change your system’s NIC configuration information.
If you do not use automatic hardware detection and configuration, you can initialize network hardware by
Manually editing the
/etc/modprobe.conffile to prompt the system to recognize and support the new hardware upon rebootWrite a script or insert commands into the
/etc/rc.d/rc.localfile to initialize the new hardware upon booting, taking care to avoid software service dependencies; in other words, not attempting remote connections or file system mounting until hardware is initialized and configuredManually load or unload the new device’s kernel module with the
modprobecommand
The following sections explain the first and last of the preceding methods.
You can manually edit the /etc/modprobe.conf file to add a module dependency entry (also known as a directive) to support a new NIC or other network device. This entry includes the device’s name and its corresponding kernel module. After you add this entry, the Linux kernel recognizes your new networking hardware upon reboot. Fedora runs a module dependency check upon booting.
For example, if your system uses a RealTek NIC, you could use an entry like this:
alias eth0 8139too
The example entry tells the Linux kernel to load the 8139too.o kernel module to support the eth0 network device. On the other hand, if you have an Intel Ethernet Pro NIC installed, you would use an entry like this:
alias eth0 eepro100
Other parameters can be passed to a kernel module using one or more option entries, if need be, to properly configure your NIC. See the modprobe.conf man page for more information on using entries. For more specifics regarding NIC kernel modules, examine the module’s source code because no man pages exist (a good opportunity for anyone willing to write the documentation).
Tip
Linux kernel and network tools can be used to diagnose problems or troubleshoot problematic NICs. However, if you browse to Don Becker’s Linux Ethercard Status, Diagnostic and Setup Utilities page at http://www.scyld.com/ethercard_diag.html, you will find more than two dozen hardware-specific utilities for a variety of PCI and legacy ISA Ethernet network cards. These tools can be extremely helpful if you run into trouble during NIC recognition or configuration.
You do not have to use an /etc/modprobe.conf entry to initialize kernel support for your new network device. As root, you can manually load or unload the device’s kernel module using the modprobe command, along with the module’s name. For example, use the following command line to enable the example RealTek NIC:
# modprobe 8139too
After you press Enter, you will see this device reported from the kernel’s ring buffer messages, which can be displayed by the dmesg command. Here’s a portion of that command’s output:
$ dmesg
...
eth0: RealTek RTL8139 Fast Ethernet at 0xce8ee000, 00:30:1b:0b:07:0d, IRQ 11
eth0: Identified 8139 chip type 'RTL-8139C'
eth0: Setting half-duplex based on auto-negotiated partner ability 0000.
...
Note that at this point, an IP address or other settings have not been assigned to the device. Linux can use multiple ethernet interfaces, and the first ethernet device will be numbered eth0, the second eth1, and so on. Each different ethernet device recognized by the kernel might have additional or different information reported, depending on its kernel module. For example,
$ dmesg ... eepro100.c:v1.09j-t 9/29/99 Donald Becker http://cesdis.gsfc.nasa.gov/linux/drive rs/eepro100.html eepro100.c: $Revision: 1.36 $ 2000/11/17 Modified by Andrey V. Savochkin <[email protected]> and others PCI: Found IRQ 10 for device 00:0d.0 eth0: Intel Corporation 82557 [Ethernet Pro 100], 00:90:27:91:92:B5, IRQ 10. Board assembly 721383-007, Physical connectors present: RJ45 Primary interface chip i82555 PHY #1. General self-test: passed. Serial sub-system self-test: passed. Internal registers self-test: passed. ROM checksum self-test: passed (0x04f4518b). ...
In this example, an Intel Ethernet Pro 100 NIC has been recognized. To disable support for a NIC, the kernel module can be unloaded, but usually only after the device is no longer in use. Read the next section to learn how to configure a NIC after it has been recognized by the Linux kernel and how to control its behavior.
If you add or replace networking hardware after your initial installation, you must configure the new hardware. You can do so using either the command line or the graphical configuration tools. To configure a network client host using the command line, you can use a combination of commands or edit specific files under the /etc/sysconfig directory. To configure the hardware through a graphical interface, you can use Fedora’s graphical tool for X11 called system-config-network or the console-based netconfig command. This section introduces command-line and graphical software tools you can use to configure a network interface and network settings on your Fedora system. You’ll see how to control your NIC and manage how your system interacts with your network.
Using the command-line configuration tools can seem difficult if you are new to Linux. For anyone new to networking, the system-config-network graphical tool is the way to go. Both manual and graphical methods require root access to work. If you do not have root access, get it before trying any of these actions. You should not edit any scripts or settings files used by graphical network administration tools on your system. Your changes will be lost the next time the tool, such as system-config-network, is run! Either use a manual approach and write your own network setup script, or stick to using graphical configuration utilities.
Note
The network configuration process described in this section is for client hosts. You cannot perform server network configuration, such as Domain Name System (DNS) and DHCP during installation. (See Chapter 27, “Managing DNS,” for more information on configuring DNS; see the “DHCP” section later in this chapter for more information on that item.)
You can configure a network interface from the command line using the basic Linux networking utilities. You configure your network client hosts with the command line by using commands to change your current settings or by editing a number of system files. Two commands, ifconfig and route, are used for network configuration. The netstat command displays information about the network connections.
ifconfig is used to configure your network interface. You can use it to
Activate or deactivate your NIC or change your NIC’s mode
Change your machine’s IP address, netmask, or broadcast address
Create an IP alias to allow more than one IP address on your NIC
Set a destination address for a point-to-point connection
You can change as many or as few of these options as you’d like with a single command. The basic structure for the command is as follows:
/sbin/ifconfig [network device] options
Table 18.1 shows a subset of ifconfig options and examples of their uses.
Table 18.1. ifconfig Options
Use | Option | Example |
|---|---|---|
Create alias | - |
|
Change IP address |
| |
Change the netmask |
|
|
Change the broadcast |
|
|
Take interface down |
|
|
Bring interface up |
|
|
Set NIC promiscuous mode on [off] |
|
|
Set multicasting mode_on [off] |
|
|
Enable [disable] |
|
|
point-to-point address |
|
|
The ifconfig man page shows other options that enable your machine to interface with a number of network types such as AppleTalk, Novell, IPv6, and others. Again, read the man page for details on these network types.
Note
Promiscuous mode causes the NIC to receive all packets on the network. It is often used to sniff a network. Multicasting mode enables the NIC to receive all multicast traffic on the network.
If no argument is given, ifconfig displays the status of active interfaces. For example, the output of ifconfig, without arguments and one active and configured NIC, looks similar to this:
# /sbin/ifconfig
eth0 Link encap:Ethernet HWaddr 00:30:1B:0B:07:0D
inet addr:192.168.2.7 Bcast:192.168.2.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:127948 errors:0 dropped:0 overruns:0 frame:0
TX packets:172675 errors:0 dropped:0 overruns:0 carrier:0
collisions:7874 txqueuelen:100
RX bytes:19098389 (18.2 Mb) TX bytes:73768657 (70.3 Mb)
Interrupt:11 Base address:0x2000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:215214 errors:0 dropped:0 overruns:0 frame:0
TX packets:215214 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:68739080 (65.5 Mb) TX bytes:68739080 (65.5 Mb)
The output is easily understood. The inet entry displays the IP address for the interface. UP signifies that the interface is ready for use, BROADCAST denotes that the interface is connected to a network that supports broadcast messaging (ethernet), RUNNING means that the interface is operating, and LOOPBACK shows which device (lo) is the loopback address. The maximum transmission unit (MTU) on eth0 is 1500 bytes. This determines the size of the largest packet that can be transmitted over this interface (and is sometimes “tuned” to other values for performance enhancement). Metric is a number from 0 to 3 that relates to how much information from the interface is placed in the routing table. The lower the number, the smaller the amount of information.
The ifconfig command can be used to display information about or control a specific interface using commands as listed in Table 18.1. For example, to deactivate the first Ethernet device on a host, use the ifconfig command, the interface name, and the command down like so:
# ifconfig eth0 down
You can also configure and activate the device by specifying a hostname or IP address and network information. For example to configure and activate (“bring up”) the eth0 interface with a specific IP address, use the ifconfig command like this:
# ifconfig eth0 192.168.2.9 netmask 255.255.255.0 up
If you have a host defined in your system’s /etc/hosts file (see the section “Network Configuration Files” later in this chapter), you can configure and activate the interface according to the defined hostname like this:
# ifconfig eth0 dogdog.hudson.com up
Read the next section to see how to configure your system to work with your LAN.
The second command used to configure your network is the route command. route is used to build the routing tables (in memory) implemented for routing packets as well as displaying the routing information. It is used after ifconfig has initialized the interface. route is normally used to set up static routes to other networks via the gateway or to other hosts. The command configuration is like this:
/sbin/route [options] [commands] [parameters]
To display the routing table, use the route command with no options. The display will look similar to this:
# /sbin/route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
149.112.50.64 * 255.255.255.192 U 0 0 0 eth0
208.59.243.0 * 255.255.255.0 U 0 0 0 eth0
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
default 149.112.50.65 0.0.0.0 UG 0 0 0 eth0
In the first column, Destination is the IP address (or, if the host is in /etc/hosts or /etc/networks, the hostname) of the receiving host. The default entry is the default gateway for this machine. The Gateway column lists the gateway that the packets must go through to reach their destination. An asterisk (*) means that packets go directly to the host. Genmask is the netmask. The Flags column can have several possible entries. In our example, U verifies that the route is enabled and G specifies that Destination requires the use of a gateway. The Metric column displays the distance to the Destination. Some daemons use this to figure the easiest route to the Destination. The Ref column is used by some UNIX flavors to convey the references to the route. It isn’t used by Linux. The Use column indicates the number of times this entry has been looked up. Finally, the Iface column is the name of the interface for the corresponding entry.
Using the -n option to the route command will give the same information substituting IP addresses for names and asterisks (*) and looks like this:
# /sbin/route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
149.112.50.64 0.0.0.0 255.255.255.192 U 0 0 0 eth0
208.59.243.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
127.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 lo
0.0.0.0 149.112.50.65 0.0.0.0 UG 0 0 0 eth0
The route command can add to the table using the add option. With the add option, you can specify a host (-host) or a network (-net) as the destination. If no option is used, the route command assumes that you are configuring the host issuing the command. The most common uses for the route command are to add the default gateway for a host, for a host that has lost its routing table, or if the gateway address has changed. For example, to add a gateway with a specific IP address, you could use the following:
# /sbin/route add default gw 149.112.50.65
Note that you could use a hostname instead of an IP address if desired. Another common use is to add the network to the routing table right after using the ifconfig command to configure the interface. Assuming that the 208.59.243.0 entry from the previous examples was missing, replace it using the following command:
# /sbin/route add -net 208.59.243.0 netmask 255.255.255.0 dev eth0
You also can use /sbin/route to configure a specific host for a direct (point-to-point) connection. For example, say that you have a home network of two computers. One of the computers has a modem through which it connects to your business network. You typically work at the other computer. You can use the route command to establish a connection through specific hosts using the following command:
# /sbin/route add -host 198.135.62.25 gw 149.112.50.65
The preceding example makes the computer with the modem the gateway for the computer you are using. This type of command line is useful if you have a gateway or firewall connected to the Internet. There are many additional uses for the route command, such as manipulating the default packet size. See the man page for those uses.
The netstat command is used to display the status of your network. It has several parameters that can display as much or as little information as you prefer. The services are listed by sockets (application-to-application connections between two computers). You can use netstat to display the information in Table 18.2.
Table 18.2. netstat Options
Output | |
|---|---|
| Displays the multicast groups configured |
| Displays the interfaces configured by |
| Lists a summary of activity for each protocol |
| Gives verbose output, listing both active and inactive sockets |
| Updates output every second (good for testing and troubleshooting) |
| Gives verbose output for active connections only |
| Displays information from the route cache and is good for looking at past connections |
Several other options are available for this command, but they are used less often. As with the /sbin/route command, the man page can give you details about all options and parameters.
As previously stated, seven network configuration files can be modified to make changes to basic network interaction of your system. The files are
/etc/hosts—. A listing of addresses, hostnames, and aliases/etc/services—. Network service and port connections/etc/nsswitch.conf—. Linux network information service configuration/etc/resolv.conf—. Domain name service domain (search) settings/etc/host.conf—. Network information search order (by default,/etc/hostsand then DNS)/etc/sysconfig/network—. The hostname, IP address, boot activation control, and gateway settings (along with optional IPv6 settings)/etc/sysconfig/network-scripts/ifcfg-eth0—. Network settings for theeth0network device; see the filesysconfig.txtunder the/usr/share/doc/initscripts/directory for details about optional settings
After the first six of these files are modified, the changes are active. As with most configuration files, comments can be added with a hash mark (#) preceding the comment. The last file (/etc/sysconfig/network) requires the networking daemons to be restarted before the file is used. All seven of these files have a man page written about them for more information.
The /etc/hosts file is a map of IP to hostnames. If you are not using DNS or another naming service, and you are connected to a large network, this file can get quite large and can be a real headache to manage. A small /etc/hosts file can look something like this:
127.0.0.1 localhost.localdomain localhost 128.112.50.69 myhost.mydomain.com myhost 128.112.50.169 yourhost.mydomain.com yourhost
The first entry is for the loopback entry. The second is for the name of the machine. The third is another machine on the network. If no naming service is in use on the network, the only host that myhost will recognize by name is yourhost. (IP addresses on the network can still be used.)
If your network is using a naming service, the last line is not needed and can be deleted. However, if myhost connects to yourhost frequently, it might be good to leave the entry so that myhost does not need to consult the naming service each time. This can save time and reduce the strain on the network or the name service server. Edit this file if you need to change your hostname or IP address or if you aren’t using a naming service and a host has been added to your network.
The /etc/services file maps port numbers to services. The first few lines look similar to this (the /etc/services file can be quite long, more than 500 lines):
# Each line describes one service, and is of the form: # # service-name port/protocol [aliases ...] [# comment] tcpmux 1/tcp # TCP port service multiplexer tcpmux 1/udp # TCP port service multiplexer rje 5/tcp # Remote Job Entry rje 5/udp # Remote Job Entry echo 7/tcp echo 7/udp discard 9/tcp sink null discard 9/udp sink null systat 11/tcp users
Typically, there are two entries for each service because most services can use either TCP or UDP for their transmissions. Usually after /etc/services is initially configured, you will not need to change it.
This file was initially developed by Sun Microsystems to specify the order in which services are accessed on the system. A number of services are listed in the /etc/nsswitch.conf file, but the most commonly modified entry is the hosts entry. A portion of the file can look like this:
passwd: files shadow: files group: files #hosts: db files nisplus nis dns hosts: files dns
This tells services that they should consult standard Unix/Linux files for passwd, shadow, and group (/etc/passwd, /etc/shadow, /etc/group, respectively) lookups. For host lookups, the system checks /etc/hosts and if there is no entry, it checks DNS. The commented hosts entry lists the possible values for hosts. Edit this file only if your naming service has changed.
/etc/resolv.conf is used by DNS, the domain name service. (DNS is covered in detail in Chapter 27.) The following is an example of resolv.conf:
nameserver 192.172.3.8 nameserver 192.172.3.9 search mydomain.com
This sets the nameservers and the order of domains for DNS to use. The contents of this file will be set automatically if you use Dynamic Host Configuration Protocol, or DHCP (see the section on “DHCP” later in this chapter).
The /etc/host.conf file lists the order in which your machine will search for hostname resolution. The following is the default /etc/host.conf file:
order hosts, bind
In this example, the host checks the /etc/hosts file first and then performs a DNS lookup. A couple more options control how the name service is used. The only reason to modify this file is if you use NIS for your name service or you want one of the optional services. The nospoof option can be a good option for system security. It compares a standard DNS lookup to a reverse lookup (host-to-IP then IP-to-host) and fails if the two don’t match. The drawback is that often when proxy services are used, the lookup fails, so you want to use this with caution.
Changes to /etc/sysconfig/network will not take effect until you restart the networking daemons or reboot the system. If you use Fedora’s graphical configuration network tools (described in the next section), you should not edit this file. The file might look like this:
NETWORKING=yes HOSTNAME=myhost GATEWAY=192.112.50.99
A GATEWAYDEV setting is also available to associate a specific network device (such as eth0 or eth1 and so on). An additional optional entry to /etc/sysconfig/network is for NIS domain machines and would look like this:
NISDOMAIN=rebel
The network file previously supported a FORWARD_IPV4 value, which determined whether the host forwarded IP packets (usually “yes” for routers). This setting is now saved in /etc/sysctl.conf as a net.ipv4.ip_forward setting, which can be modified if the forwarding changes are required. See the sysctl.conf man page for more information.
As mentioned earlier, if you are new to networking or still becoming proficient with the command line, the graphical configuration tool is your best method for configuring new hardware in Fedora. Like most graphical tools, system-config-network allows you to fill in the blanks; press the proper buttons, and the tool modifies the required files and issues the proper commands. Remember, you must be root to run system-config-network.
There are two ways to start system-config-network: from the command line of an X11 terminal window with the command system-config-network, using the panel’s Run Application menu item, or by clicking the System Setting’s Network menu item from a GNOME or KDE desktop panel menu. (In either case, you are prompted to enter the root password.)
After it is started, system-config-network might ask whether you would like to create a new device. If you have installed Fedora on a computer with an existing network card, however, the screen shown in Figure 18.1 appears after you start system-config-network.
Click the DNS tab to configure your system’s DNS settings, hostname, or DNS search path. Click the Hosts tab, and then either click the New or Edit button (after selecting a host) to create or edit an entry in your system’s /etc/hosts file, for example, to add the IP addresses, hostnames, and aliases of hosts on your network. See Figure 18.2 for an example of editing a host entry.
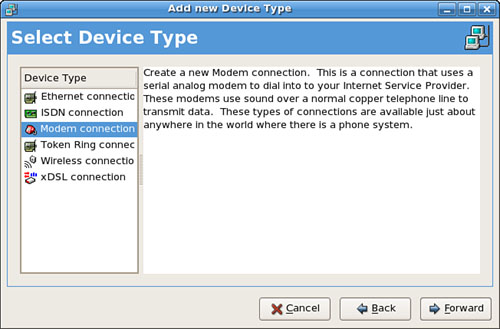
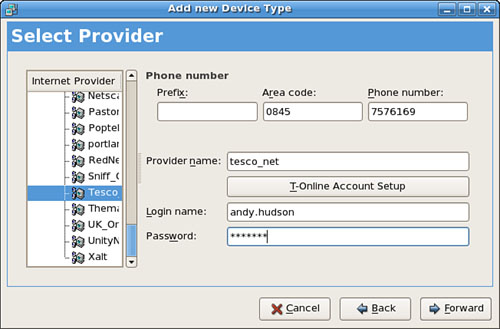
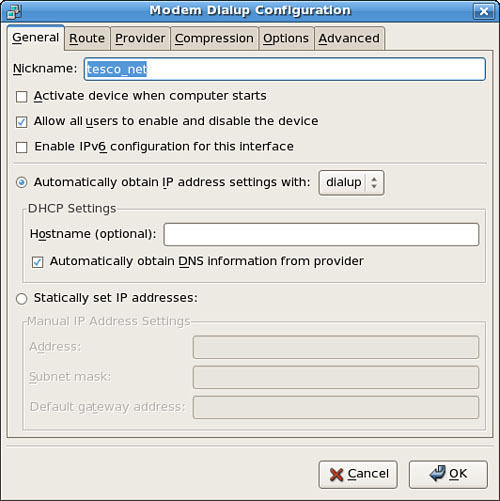
Click the Devices tab, and then either click New or select an existing setting and click Edit to automatically or manually set up an ethernet device. Figure 18.3 shows the Add New Device Type dialog box with all necessary information in place for a static, or fixed, IP address assignment. Choose how your card will get its configuration, manually from Dynamic Host Control Protocol (see the next section) or from Bootp. Just fill in the blanks as needed.
When you finish configuring your NIC or editing an IP address or assignment scheme for a NIC, save your changes using the File menu’s Save menu item. Note that you can also use the Profile menu (as shown previously in Figure 18.1) to create different network configurations and IP address assignments for your installed NICs. This is handy if you want to create, for example, a different network setup for home or work on a laptop running Fedora.
As its name implies, Dynamic Host Configuration Protocol (DHCP) configures hosts for connection to your network. DHCP allows a network administrator to configure all TCP/IP parameters for each host as he connects to the network after activation of a NIC. These parameters include automatically assigning an IP address to a NIC, setting name server entries in /etc/resolv.conf, and configuring default routing and gateway information for a host. This section first describes how to use DHCP to obtain IP address assignment for your NIC, and then how to quickly set up and start a DHCP server using Fedora.
Note
You can learn more about DHCP by reading RFC2131 “Dynamic Host Configuration Protocol.” Browse to http://www.ietf.org/rfc/rfc2131.txt.
DHCP provides persistent storage of network parameters by holding identifying information for each network client that might connect to the network. The three most common pairs of identifying information are
Network subnet/host address—. Used by hosts to connect to the network at will
Subnet/hostname—. Enables the specified host to connect to the subnet
Subnet/hardware address—. Enables a specific client to connect to the network after getting the hostname from DHCP
DHCP also allocates to clients temporary or permanent network (IP) addresses. When a temporary assignment, known as a lease, elapses, the client can request to have the lease extended, or, if the address is no longer needed, the client can relinquish the address. For hosts that will be permanently connected to a network with adequate addresses available, DHCP allocates infinite leases.
DHCP offers your network some advantages. First, it shifts responsibility for assigning IP addresses from the network administrator (who can accidentally assign duplicate IP addresses) to the DHCP server. Second, DHCP makes better use of limited IP addresses. If a user is away from the office for whatever reason, the user’s host can release its IP address for use by other hosts.
Like most things in life, DHCP is not perfect. Servers cannot be configured through DHCP alone because DNS does not know what addresses that DHCP assigns to a host. This means that DNS lookups are not possible on machines configured through DHCP alone; therefore, services cannot be provided. However, DHCP can make assignments based on DNS entries when using subnet/hostname or subnet/hardware address identifiers.
Note
The problem of using DHCP to configure servers using registered hostnames is being addressed by Dynamic DNS which, when fully developed, will enable DHCP to register IP addresses with DNS. This will allow you, for example, to register a domain name (such as imalinuxuser.com) and be able to easily access that domain’s web server without needing to use static IP addressing of a specific host. The largest hurdle to overcome is the security implication of enabling each host connecting to the system to update DNS. A few companies, such as http://www.dyndns.org/, are already offering Dynamic DNS services and have clients for Linux.
During installation, you can instruct the Fedora installer to save DHCP settings for your NIC. After installation, you can also use the system-config-network client to edit the TCP/IP configuration information required to properly initialize and configure your NIC to connect your system to the local network and Internet. When you select a dynamic, or DHCP-assigned IP addressing scheme for your NIC, the broadcast address is set at 255.255.255.255 because dhclient, the DHCP client used for IP configuration, is initially unaware of where the DHCP server is located, so the request must travel every network until a server replies.
DHCP-specific information is simply saved as a BOOTPROTO=dhcp entry for your NIC under the /etc/sysconfig/network directory (in settings and scripts for a specific device, such as eth0).
Other settings specific to obtaining DHCP settings are saved in the file named dhclient.conf under the /etc directory and are documented in the dhclient.conf man page. More than 100 options are also documented in the dhcp-options man page.
However, using DHCP is not that complicated. If you want to use DHCP and know that there is a server on your network, you can quickly configure your NIC by using the dhclient like so:
# dhclient
Internet Software Consortium DHCP Client V3.0pl2
Copyright 1995-2001 Internet Software Consortium.
All rights reserved.
For info, please visit http://www.isc.org/products/DHCP
Listening on LPF/lo/
Sending on LPF/lo/
Listening on LPF/eth0/00:a0:24:aa:f5:17
Sending on LPF/eth0/00:a0:24:aa:f5:17
Sending on Socket/fallback
DHCPREQUEST on eth0 to 255.255.255.255 port 67
DHCPACK from 192.168.2.254
save_previous /etc/yp.conf
save_previous /etc/resolv.conf
bound to 192.168.2.253 -- renewal in 9906 seconds.
In this example, the first ethernet device, eth0, has been assigned an IP address of 192.168.2.253 from a DHCP server at 192.168.2.54. The renewal will take place in about two hours and 45 minutes.
Installation of the DHCP client and server might be easiest during the initial install of Fedora, but you can also use RPMs later on, or download and build the source code yourself. The RPMs are available on your Fedora DVD or from a mirror FTP site (refer to Chapter 7 for more information). This section describes configuring the dhclient and setting up and running the dhpcd daemon.
As previously mentioned, DHCP use for an installed NIC is easily accomplished when installing Fedora on your host (read more about installation in Chapter 3, “Installing Fedora”), and during the network step of installation, you can choose to have DHCP initiated at boot time. If you choose to do this (and choose to install the DHCP client package), the DHCP client, dhclient, sends a broadcast message that the DHCP server replies to with networking information for your host. That is it; you’re done.
If you choose to install from source, you will have to (as root) download and install the server packages that include dhclient. Unpack the source file, run ./configure from the root of the source directory, run make, and then run make install. This should put the DHCP client binaries where they will start at the correct time in the boot process.
You can however, fine-tune how dhclient works, and where and how it obtains or looks for DHCP information. You probably will not need to take this additional effort; but if you do, you can create and edit a file named dhclient.conf, and save it in the /etc directory with your settings. A few of the dhclient.conf options include
timeouttime;—. How long to wait before giving up trying (60 seconds is the default)retrytime;—. How long to wait before retrying (five minutes is the default)select-timeouttime;—. How long to wait before selecting a DHCP offer (zero seconds is the default)reboottime;—. How long to wait before trying to get a previously set IP (10 seconds is the default)renewdate;—. When to renew an IP lease, wheredateis in the form of<weekday> <year>/<month>/<day> <hour>:<minute>:<second>, such as4 2004/1/1 22:01:01for Thursday, January 4, 2004 at 10:01 p.m.
See the dhclient.conf man page for more information on additional settings.
Again, the easiest way to install the DHCP server on your computer is to include the RPMs at install time or to use RPMs if you have installed your machine without installing the DHCP server RPMs. If you are so inclined, you can go to the Internet Software Consortium (ISC) website and download and build the source code yourself (http://www.isc.org/).
If you decide to install from a source downloaded from the ISC website, the installation is very straightforward. Just unpack your tar file, run ./configure from the root of the source directory, run make, and finally, if there are no errors, run make install. This puts all the files used by the DHCP daemon in the correct places. If you have the disk space, it is best to leave the source files in place until you are sure that DHCP is running correctly; otherwise, you can delete the source tree.
Configuring your network with DHCP can look difficult, but is actually easy if your needs are simple. The server configuration can take a bit more work if your network is more complex and depending on how much you want DHCP to do.
Configuring the server takes some thought and a little bit of work. Luckily, the work involves editing only a single configuration file, /etc/dhcpd.conf. To start the server at boot time, use the service, ntsysv, or system-config-services commands.
The /etc/dhcpd.conf file contains all the information needed to run dhcpd. Fedora includes a sample dhcpd.conf in /usr/share/doc/dhcp*/dhcpd.conf.sample. The DHCP server source files also contain a sample dhcpd.conf file.
The /etc/dhcpd.conf file can be looked at as a three-part file. The first part contains configurations for DHCP itself. The configurations include
Setting the domain name—.
option domain-name "example.org"Setting DNS servers—.
option domain-name-servers ns1.example.org, ns2.example.org(IP addresses can be substituted)Setting the default and maximum lease times—.
default-lease-time 3600andmax-lease-time 14400
Other settings in the first part include whether the server is the primary (authoritative) server and what type of logging DHCP should use. These settings are considered defaults and can be overridden by the subnet and host portion of the configuration in more complex situations.
Note
The dhcpd.conf file requires semicolons (;) after each command statement. If your configuration file has errors or runs improperly, check for this.
The next part of the dhcpd.conf deals with the different subnets that your DHCP server serves; this section is quite straightforward. Each subnet is defined separately and can look like this:
subnet 10.5.5.0 netmask 255.255.255.224 {
range 10.5.5.26 10.5.5.30;
option domain-name-servers ns1.internal.example.org;
option domain-name "internal.example.org";
option routers 10.5.5.1;
option broadcast-address 10.5.5.31;
default-lease-time 600;
max-lease-time 7200;
}
This defines the IP addressing for the 10.5.5.0 subnet. It defines the IP address ranging from 10.5.5.26 through 10.5.5.30 to be dynamically assigned to hosts that reside on that subnet. This example shows that any TCP/IP option can be set from the subnet portion of the configuration file. It shows which DNS server the subnet will connect to, which can be good for DNS server load balancing, or which can be used to limit the hosts that can be reached through DNS. It defines the domain name, so you can have more than one domain on your network. It can also change the default and maximum lease time.
If you want your server to ignore a specific subnet, the following entry can be used to accomplish this:
subnet 10.152.187.0 netmask 255.255.255.0 {
}
This defines no options for the 10.152.187.0 subnet; therefore, the DHCP server ignores it.
The last part of your dhcp.conf is for defining hosts. This can be good if you want a computer on your network to have a specific IP address or other information specific to that host. The key to completing the host section is to know the hardware address of the host. As you learned in “Hardware Devices for Networking,” earlier in this chapter, the hardware address is used to differentiate the host for configuration. Your hardware address can be obtained by using the ifconfig command as described previously. The hardware address is on the eth0 line labeled "Hwaddr".
host fantasia {
hardware ethernet 08:00:07:26:c0:a5;
fixed-address fantasia.fugue.com;
}
This example takes the host with the hardware address 08:00:07:26:c0:a5 and does a DNS lookup to assign the IP address for fantasia.fugue.com to the host.
DHCP can also define and configure booting for diskless clients like this:
host passacaglia {
hardware ethernet 0:0:c0:5d:bd:95;
filename "vmunix.passacaglia";
server-name "toccata.fugue.com";
}
The diskless host passacaglia will get its boot information from server toccata.fugue.com and use vmunix.passacaglia kernel. All other TCP/IP configuration can also be included.
Caution
Remember, only one DHCP server should exist on a local network to avoid problems. Your DHCP might not work correctly on a LAN with hosts running outdated legacy operating systems. Often Windows NT servers will have the Windows DHCP server installed by default. Because there is no configuration file for NT to sort through, that DHCP server configures your host before the Linux server if both machines are on the same LAN. Check your NT servers for this situation and disable DHCP on the NT server; afterward, your other DHCP-enabled hosts should configure correctly. Also, check to make sure that there are no conflicts if you use a cable or DSL modem, wireless access point (WAP), or other intelligent router on your LAN that can provide DHCP.
A whole host of options can be used in dhcpd.conf: Entire books are dedicated to DHCP. The most comprehensive book is The DHCP Handbook, available at http://www.dhcp-handbook.com/. You can define NIS domains, configure NETBIOS, set subnet masks, and define time servers, or many other types of servers—to name a few of the DHCP options you can use. The preceding example will get your DHCP server and client up and running.
The DHCP server distribution contains an example of the dhcpd.conf file that you can use as a template for your network. The file shows a basic configuration that can get you started with explanations for the options used.
As stated earlier, Linux has had support for wireless networking since the first standards were developed in the early 1990s. With computers getting smaller and smaller, the uses for wireless networking increased; meanwhile, the transmission speeds are increasing all the time. There are several different ways to create a wireless network. The following sections introduce you to several Linux commands you can use to initialize, configure, and manage wireless networking on your Fedora system.
The Linux kernel that ships with Fedora provides extensive support for wireless networking. Related wireless tools for configuring, managing, or displaying information about a wireless connection include
iwconfig—. Sets the network name, encryption, transmission rate, and other features of a wireless network interfaceiwlist—. Displays information about a wireless interface, such as rate, power level, or frequency usediwpriv—. Usesito set optional features, such as roaming, of a wireless network interfaceiwspy—. Shows wireless statistics of a number of nodes
Support varies for wireless devices—most likely in the form of a PCMCIA adapter—although some USB wireless devices now work with Linux. In general, Linux wireless device software (usually in the form of a kernel module) supports the creation of an ethernet device that can be managed by traditional interface tools such as ifconfig—with wireless features of the device managed by the various wireless software tools.
For example, when a wireless networking device is first recognized and initialized for use, the driver will most likely report a new device:
wvlan_cs: WaveLAN/IEEE PCMCIA driver v1.0.6 wvlan_cs: (c) Andreas Neuhaus <[email protected]> wvlan_cs: index 0x01: Vcc 3.3, irq 3, io 0x0100-0x013f wvlan_cs: Registered netdevice eth0 wvlan_cs: MAC address on eth0 is 00 05 5d f3 1d da
This output (from the dmesg command) shows that the eth0 device has been reported. If DHCP is in use, the device should automatically join the nearest wireless subnet and be automatically assigned an IP address. If not, the next step is to use a wireless tool such as iwconfig to set various parameters of the wireless device. The iwconfig command, along with the device name (eth0 in this example), will show the status:
# iwconfig eth0
eth0 IEEE 802.11-DS ESSID:"GreyUFO" Nickname:"Prism I"
Mode:Managed Frequency:2.412GHz Access Point: 00:02:2D:2E:FA:3C
Bit Rate:2Mb/s Tx-Power=15 dBm Sensitivity:1/3
RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
Link Quality:92/92 Signal level:-11 dBm Noise level:-102 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:4 Missed beacon:0
This example shows a 2Mbps connection to a network named GreyUFO. To change a parameter, such as the transmission rate, use a command-line option with the iwconfig command like so:
# iwconfig eth0 rate 11M
Other options supported by the iwconfig command include essid, used to set the NIC to connect to a specific network by named; mode, used to enable the NIC to automatically retrieve settings from an access point or connect to another wireless host; or freq, to set a frequency to use for communication. Additional options include channel, frag, enc (for encryption), power, and txpower. Details and examples of these options are in the iwconfig manual page.
You can then use the ifconfig command or perhaps a graphical Fedora tool to set the device networking parameters, and the interface will work as on a hardwired LAN. One handy output of the iwconfig command is the link quality output, which can be used in shell scripts or other graphical utilities for signal monitoring purposes (refer to Chapter 15 for an example).
The ads are starting to crop up on TV: This cellular service allows you to check your email anywhere your cellular phone can reach; that cellular company provides news and other information via the Internet to your phone. Personal digital assistants have cellular add-ons or even built-in options.
For example, if your laptop has a cellular modem, you can use it to dial in to your network. This is not truly wireless networking if the network dialed in to is wired, but it illustrates how far-reaching wireless networks can go. As long as your cellular service follows you, you can dial in to any network you have access to (be it home or office) from any location in the world to check your email and use it to send electronic files to your associates. And many newer cell phones can be used as a modem by attaching a cable from the phone to a serial or USB port on a laptop. As with most devices, the majority of brand-name PCMCIA cards work with Linux. A lot of generic equipment (such as serial I/O cards) should work, but you are taking a chance if the card is not supported (see the section “Managing PCMCIA” in Chapter 4, “Post-Installation Configuration”).
Advantages of wireless networking are its mobility and potential range. If you have a large enough antenna network, your network can stretch many miles. This would be an expensive network, but one that would easily break out of the brick and mortar confines of the office.
Wireless networking would also be a great advantage to college campuses to eliminate the need to tear through walls to install cabling because more and more students expect to have a network connection in their dorm rooms. Wireless networking cards are becoming more reasonable in price and can easily be issued to each student as he requires them.
Home networkers can also benefit from wireless networking. For those who cannot make wired network modifications to their homes, wireless networking removes the unsightly wires running along baseboards and ceilings that are required to connect computers in different rooms. With a wireless home network, you are not even confined to inside the house. Depending on the transmit power of your router, you can sit out in your backyard and watch clouds drifting by as you type away. Wireless routers are coming down in price with each passing day.
Choosing the right types of wireless devices is an important decision. The next sections discuss some of the basic differences between current protocols used for wireless networking.
The Institute of Electrical and Electronics Engineers (IEEE) started to look seriously at wireless networking in 1990. This is when the 802.11 Standard was first introduced by the Wireless Local Area Networks Standards Working Group. The group based the standard roughly around the architecture used in cellular phone networks. The wireless network is controlled by a base station, which can be just a transmitter attached to the network or, more commonly these days, a router.
Larger networks can use more than one base station. Networks with more than one base station are usually referred to as distribution systems. A distribution system can be used to increase coverage area and support roaming of wireless hosts. You can also employ external omnidirectional antennas to increase coverage area, or if required, use point-to-point, or directional antennas to connect distant computers or networks. Right now, the least expensive wireless Linux networks are built using devices (such as access points or NICs) supporting 802.11b, although prices are rapidly dropping for faster 802.11g devices.
An early standard, 802.11a, offers greater transmission rates than 802.11b, and a number of 802.11a wireless NICs are available (some products provide up to 72Mbps, but will not work with 802.11b devices). Wireless networking devices based on 802.11g, which has the speed improvement of 802.11a and is compatible with 802.11b, are more widely available. Other wireless protocols include Bluetooth, which provides up to 720Kbps data transfers. Bluetooth is intended for short-range device communications (such as for a printer) and supports a typical range of only 10 meters. Bluetooth is unlike IrDA, which requires line-of-sight (devices that are aimed at each other). Bluetooth use conflicts with 802.11 networks because it also uses the 2.4GHz band. You can find out more by browsing to http://www.bluetooth.com/.
The 802.11 standard specifies that wireless devices use a frequency range of 2400–2483.5MHz. This is the standard used in North America and Europe. In Japan, however, wireless networks are limited to a frequency range of 2471MHz–2479MHz because of Japanese regulations. Within these ranges, each network is given up to 79 nonoverlapping frequency channels to use. This reduces the chance of two closely located wireless networks using the same channel at the same time. It also allows for channel hopping, which can be used for security.
Fedora supports Internet connections and the use of Internet resources in many different ways. You will find a wealth of Internet-related software included with this book’s version of Fedora, and you can download hundreds of additional free utilities from a variety of sources. To use them, you must have a working Internet connection.
In this section, you learn how to set up an Internet connection in Fedora Core Linux using a modem and Point-to-Point Protocol (PPP) as well as other connection methods, including digital subscriber line (DSL) and cable modem services. Just a few years ago, getting a dial-up connection working was difficult—hence, an entire chapter of this book was devoted to it. Nowadays, as long as you have a hardware modem, dial-up configuration is simple. The Fedora developers and the wider Linux community have made great progress in making connectivity easier.
Although many experienced Linux users continue to use manual scripts to establish their Internet connectivity, new users and experienced system administrators alike will find Fedora’s graphical network configuration interface, the Internet Connection Wizard, much easier to use. You learn how to use the Internet Connection Wizard in this chapter, as well as how to configure Fedora to provide dial-in PPP support. The chapter also describes how to use Roaring Penguin’s DSL utilities for managing connectivity through a cable modem connection.
Although Fedora enables great flexibility in configuring Internet connections, that flexibility comes at the price of an increase in complexity. To configure Internet connectivity in Fedora, you must know more about the details of the connection process than you can learn from the information typically provided by your Internet service provider (ISP). In this section of the chapter, you learn what to ask about and how to use the information.
Some ISPs are unaware of Linux or unwilling to support its use with their service. Fortunately, that attitude is rapidly changing, and the majority of ISPs offer services using standard protocols that are compatible with Linux, even if they (or their technical support people) aren’t aware that their own ISPs are Linux-friendly. You just need to press a little for the information you require.
If you are using a dial-up modem account (referred to in Linux as PPP for the Point-to-Point Protocol it uses), your ISP will provide your computer with a static or dynamic IP (Internet Protocol) address. A dynamic IP address changes each time you dial in, whereas a static IP address remains the same. The ISP also might automatically provide your computer with the names of the Domain Name Service (DNS) servers. You need to know the telephone number that your computer will dial in to for making the connection; your ISP supplies that number, too. You will also need a working modem and need to know the device name of the modem (usually /dev/modem).
Note
Most IP addresses are dynamically assigned by ISPs; ISPs have a pool of addresses, and you get whatever address is available. From the ISP’s viewpoint, a small number of addresses can serve a large number of people because not everyone will be online at the same time. For most Internet services, a dynamic IP works well because it is the ISP’s job to route that information to you, and it sits in the middle—between you and the service you want to use. But a dynamic IP address changes, and if someone needs to find you at the same address (if you run a website or a file transfer site, for example), an IP that changes every time you log on will not work well. For that, you need a static IP. Because your ISP cannot reuse that IP with its other customers, it will likely charge you more for a static IP than a dynamic IP. The average consumer doesn’t need the benefit of a static IP, so he is happy paying less for a dynamically assigned IP. Also, the DNS information can be provided automatically by the ISP by the Dynamic Host Configuration Protocol, or DHCP.
If you are using DSL access or a cable modem, you might have a dynamic IP provided through DHCP, or you might be assigned a static IP. You might automatically be provided with the names of the DNS servers if you use DHCP, or you might have to set up DNS manually (in which case, you have to know the IP addresses of the DNS servers).
In all cases, you have to know your username, your password, and for the configuration of other services, the names of the mail servers and the news server. This information can be obtained from your ISP if you specifically ask for it.
Note
The information in this book will help you understand and avoid many connection issues, but you might experience connection problems. Keep the telephone number of the technical help service for your ISP on hand in case you are not able to establish a connection. But be aware that few ISPs offer Linux support, and you might need to seek help from a Linux-savvy friend or a Linux user’s group if your special circumstances cannot be handled from the knowledge you gain from this book. Of course, the best place to look is on the Internet. Use Google’s Linux page (http://www.google.com/linux/) to research the problem and see if any other users have found fixes or workarounds.
Fedora also supports the use of a digital subscriber line service. Although it refers to the different types of DSL available as xDSL, that name includes ADSL, IDSL, SDSL, and other flavors of DSL service; they can all be configured using the Internet Connection Wizard. DSL service generally provides 128Kbps to 8.0Mbps transfer speeds and transmits data over copper telephone lines from a central office to individual subscriber sites (such as your home). Many DSL services provide asymmetric speeds with download speed greater than upload speeds.
Note
DSL service is an “always-on” type of Internet service, although you can turn off the connection under Fedora using the Network Device Control. An always-on connection exposes your computer to malicious abuse from crackers who trawl the Internet attempting to gain access to other computer systems. In addition to the capability to turn off such connections, Fedora provides a firewall to keep crackers out; you configured a simple firewall during the original installation. The firewall can also be configured from the Security Level Configuration tool found in the System Settings menu selection as Security Level.
A DSL connection requires that you have an ethernet network interface card (sometimes a USB interface that is not easily supported in Linux) in your computer or notebook. Many users also configure a gateway, firewall, or other computer with at least two network interface cards in order to share a connection with a LAN. We looked at the hardware and protocol issues earlier in this chapter. Advanced configuration of a firewall or router, other than what was addressed during your initial installation of Fedora, is beyond the scope of this book.
Establishing a DSL connection with an ISP providing a static IP address is easy. Unfortunately, many DSL providers use a type of PPP protocol named Point-to-Point Protocol over Ethernet (PPPoE) that provides dynamic IP address assignment and authentication by encapsulating PPP information inside ethernet frames. Roaring Penguin’s rp-pppoe clients are included with Fedora, and these clients make the difficult-to-configure PPPoE connection much easier to deal with. You can download and install newer versions (see the Roaring Penguin link in the “Reference” section at the end of this chapter).
The basic steps involved in manually setting up a DSL connection using Fedora Linux involve connecting the proper hardware, and then running a simple configuration script if you use rp-pppoe from Roaring Penguin.
First, connect your DSL modem to your telephone line, and then plug in your ethernet cable from the modem to your computer’s network interface card. If you plan to share your DSL connection with the rest of your LAN, you need at least two network cards—designated eth0 (for your LAN) and eth1 (for the DSL connection).
The following example assumes that you have more than one computer and will share your DSL connection on a LAN. First, log in as root, and ensure that your first eth0 device is enabled and up (perhaps using the ifconfig command). Next, bring up the other interface, but assign a null IP address like this:
# /sbin/ifconfig eth1 0.0.0.0 up
Now use the adsl-setup command to set up your system. Type the command like this:
# /sbin/adsl-setup
You will be presented with a text script and be asked to enter your username and the ethernet interface used for the connection (such as eth1). You will then be asked to use “on demand” service or have the connection stay up all the time (until brought down by the root operator). You can also set a timeout in seconds, if desired. You’ll then be asked to enter the IP addresses of your ISP’s DNS servers if you haven’t configured the system’s /etc/resolv.conf file.
After that, you will be prompted to enter your password two times, and have to choose the type of firewall and IP masquerading to use. (You learned about IP masquerading in the “Using IP Masquerading in Fedora” section, earlier in this chapter.) The actual configuration is done automatically. Using a firewall is essential nowadays, so you should choose this option unless you intend to craft your own set of firewall rules—a discussion of which is beyond the scope of this book. After you have chosen your firewall and IP masquerading setup, you will be asked to confirm, save, and implement your settings. You are also given a choice to allow users to manage the connection, a handy option for home users.
Changes will be made to your system’s /etc/sysconfig/network-scripts/ifcfg-ppp0, /etc/resolv.conf, /etc/ppp/pap-secrets, and /etc/ppp/chap-secrets files.
After configuration has finished, use the adsl-start command to start a connection and DSL session, like this:
# /sbin/adsl-start
The DSL connection should be nearly instantaneous, but if problems occur, check to make sure that your DSL modem is communicating with the phone company’s central office by examining the status LEDs on the modem. Because this varies from modem to modem, consult your modem user’s manual.
Check to make certain that all cables are properly attached, that your interfaces are properly configured, and that you have entered the correct information to the setup script.
If IP masquerading is enabled, other computers on your LAN on the same subnet address (such as 192.168.1.XXX) can use the Internet, but must have the same /etc/resolv.conf name server entries and a routing entry with the DSL-connected computer as a gateway. For example, if the host computer with the DSL connection has an IP address of 192.168.1.1, and other computers on your LAN use addresses in the 192.168.1.XXX range, use the route command on each computer like this:
# /sbin/route add default gw 192.168.1.1
Note that you can also use a hostname instead if each computer has an /etc/hosts file with hostname and IP address entries for your LAN. To stop your connection, use the adsl-stop command like this:
# /sbin/adsl-stop
Most ISPs provide dial-up connections supporting PPP because it is a fast and efficient protocol for using TCP/IP over serial lines. PPP is designed for two-way networking; TCP/IP provides the transport protocol for data. One hurdle faced by new Fedora users is how to set up PPP and connect to the Internet. It is not necessary to understand the details of the PPP protocol in order to use it, and setting up a PPP connection is easy. You can configure the PPP connections manually using the command line or graphically during an X session using Fedora’s Internet Configuration Wizard. Each approach produces the same results.
PPP uses several components on your system. The first is a daemon called pppd, which controls the use of PPP. The second is a driver called the high-level data link control (HDLC), which controls the flow of information between two machines. A third component of PPP is a routine called chat that dials the other end of the connection for you when you want it to. Although PPP has many tunable parameters, the default settings work well for most people.
Note
You can check to see whether PPP is installed on your system by running the pppd command as root from a command line with the --help argument, like this:
# pppd --help
That will list the current version number and describe a few available options if PPP is installed.
If PPP isn’t installed on your system, use the rpm command to install the PPP package from the Fedora DVD or use the Packages menu item from the System Settings menu. Chapter 7 covers the details of using rpm and the graphical package manager.
The first step in manually configuring PPP is to log in as root to copy and edit the necessary files. After you are logged in, you use the chat command, the pppd daemon, and several files to configure PPP:
/etc/ppp/ppp-on—. Used to start a PPP connection. This file contains the ISP’s phone number, your username and password, as well as various options such as IP address options, the modem device, and its settings (such as baud rate) for the connection./etc/ppp/ppp-off—. Used to terminate a PPP connection./etc/ppp/ppp-on-dialer—. Used to perform dialing and connection with thechatcommand; this script contains error-handling and negotiation responses between the remote system and thechatcommand script.
Caution
Many software modems will not work with Linux because the manufacturers won’t release programming information about them or provide Linux drivers. An external serial port modem or ISA bus modem will almost always work; USB and PCI modems are still problematic. It is suggested that you do a thorough Google search using your modem’s name and model number to see how others have solved problems with that particular modem. Links to software modem compatibility sites appear at the end of this chapter.
Begin by copying the scripts from the /usr/share/doc/ppp*/scripts directory to the /etc/ppp directory, like so:
# cp -ar /usr/share/doc/ppp*/scripts/ppp-o* /etc/ppp
Using your favorite text editor, edit the ppp-on file (making sure to disable the line wrapping function in your editor—that varies from editor to editor—and line-wrapping inserts carriage returns that cause these scripts to stop working) and change the first four entries to reflect your ISP’s phone number and your username and password, like this:
TELEPHONE=555-1212 # The telephone number for the connection ACCOUNT=hudzilla # The account name for logon PASSWORD=spasm # The password for this account LOCAL_IP=0.0.0.0 # Local IP address if known. Dynamic = 0.0.0.0
Change the values for TELEPHONE, ACCOUNT, and PASSWORD, substituting your ISP’s phone number and your username and password. Change the LOCAL_IP entry to an IP address only if your ISP provides one for use. (Dynamic IPs are typical of dial-up accounts.) Otherwise, leave the entry blank. Next, scroll through the script until you find the dialing setup, which can look like this:
exec /usr/sbin/pppd debug lock modem crtscts /dev/ttyS0 38400
asyncmap 20A0000 escape FF kdebug 0 $LOCAL_IP:$REMOTE_IP
noipdefault netmask $NETMASK defaultroute connect $DIALER_SCRIPT
These lines (actually a single script line) contain modem options for the chat script used in the ppp-on-dialer script and will start the pppd daemon on your computer after establishing a connection. Using a text editor, change the modem device (/dev/ttyS0 in this example) to /dev/modem.
Caution
You can use /dev/modem only if Fedora’s kudzu utility has recognized and configured the computer’s modem. (If /dev/modem does not exist, use the ln command to create the file as a symbolic link pointing to the correct serial port.) To create the symlink (from /dev/ttyS2, for example):
# ln -s /dev/ttyS2 /dev/modem
If your modem was not automatically detected and the /dev/modem link configured, it is possible that you have a software modem, also known as a Winmodem or HSF modem (refer to the earlier note).
Set the baud rate (38400 in the default case) to the desired connection speed—most likely 115200 or 57600. When finished, save the file.
Next, use the chmod command to make these scripts executable, like this:
# chmod +x /etc/ppp/ppp-o*
To debug or check the progress of your modem connection, dialing, and connection to your ISP, monitor the syslog messages by using the tail command with its -f “loop forever” option, like this:
# /sbin/tail -f /var/log/messages
To connect to your ISP, run the ppp- script:
# /etc/ppp/ppp-on
Use the ppp-off script to stop the PPP connection like so:
# /etc/ppp/ppp-off
You can also move the ppp-on and ppp-off scripts to a recognized $PATH, such as /usr/local/bin. Enabling use of these scripts by normal users will entail changing permissions of the serial port and other files (which can be a security problem because unauthorized users can access it).
Tip
If your modem is installed and working, you can access it using a terminal program such as minicom, which usually is not installed by default. After you install it from the .rpm file or from source code, start it the very first time with the -s argument to configure it:
$ minicom -s
Set the serial port to that of your modem, and then save the configuration. You can then use minicom to communicate with your modem using the AT command set and see its responses.
If you do not want to go to that trouble, you can use the echo command to send commands to the modem, but the modem won’t be capable of responding to you. For example, the AT&W command can be sent as follows:
# echo "AT&W" > /dev/modem
The Fedora Modem Configuration Wizard can be used to set up the many kinds of network connection types that exist. Fedora provides wizards for the following connections:
IPSec (VPN) connection (Virtual Private Network using Crypto IP Encapsulation)
Ethernet connection
ISDN connection
Modem connection
Token ring connection
Wireless connection
xDSL connection
The example provided here uses the wizard to configure a modem connection—the most commonly encountered home network connection. The other types are configured in essentially the same manner.
From the System menu, select the Administration sub-menu and click Network to open up the Network configuration tool. Enter the root password to gain access to the tool and click New in the toolbar to start the wizard. Select Modem Connection from the list of options, shown in Figure 18.4 and click Forward.
Select Modem Connection in the Device Type list, and then click the Forward button. You are then asked to select a provider, designate a name for the service, enter your ISP’s phone number, and enter your username and password on the remote system, as shown in Figure 18.5. A dialing prefix (to disable call waiting, for example) can be added in the Prefix field. Additional special settings are also included for PPP users in various countries with different ISPs, as shown by the country flags on the left.
Enter the telephone number of your ISP’s remote computer’s modem. Enter a country code if needed, along with an area code and telephone number. Note that some areas require a 10-digit number for local telephone service. When finished, click the Forward button. You’ll then be able to confirm the settings. Click the Finish button to create the interface. When you are done, you will see a new ppp0 entry in the Network Configuration window, as shown in Figure 18.6.
To edit the new connection identified as ppp0, select the interface, and then click the Edit button. A configuration dialog appears as shown in Figure 18.7 Each tab presents an easy-to-use interface for setting dial-up options.
This window can be reached later from the System Settings menu as the Network menu item. Fedora also provides a simple control interface via the System Tools menu as the Network Device Control menu item, as shown in Figure 18.8.
Launch a PPP connection by selecting the ppp0 interface and then clicking the Activate button.
You can also use the ifup command manually (only as root) to bring up the connection like this:
# /sbin/ifup ppp0
To close the connection manually, use ifdown:
# /sbin/ifdown ppp0
If you named the dial-up connection something other than ppp0, use that name instead. Because we named ours Cavtel, we can bring it up manually with
# /sbin/ifup Cavtel
The Internet Configuration Wizard does not offer any Help dialogs, but the Linux Documentation Project at http://www.tldp.org/ offers many in-depth resources for configuring and troubleshooting these connections. The Internet search engine Google is also an invaluable tool for dealing with specific questions about these connections. For many other useful references, see the “Reference” section at the end of this chapter.
Here are a few troubleshooting tips culled from many years of experience:
If your modem connects and then hangs up, you are probably using the wrong password or dialing the wrong number. If the password and phone number are correct, it is likely an authentication protocol problem.
If you get connected but cannot reach websites, it is likely a domain name resolver problem, meaning that DNS is not working. If it worked yesterday and you haven’t “adjusted” the associated files, it is probably a problem at the ISP’s end. Call and ask.
Always make certain that everything is plugged in. Check again—and again.
If the modem works in Windows, but not in Linux no matter what you do, it is probably a software modem no matter what it said on the box.
If everything just stops working (and you do not see smoke), it is probably a glitch at the ISP or the telephone company. Take a break and give them some time to fix it.
Never configure a network connection when you have had too little sleep or too much caffeine; you will just have to redo it tomorrow.
If you want to access your high-speed Internet connection when you are away from home, a simple dial-up PPP service can be quickly configured on your Fedora system by configuring Linux to answer a call from a remote modem and start PPP. This is handy if you have high-speed access at home and need to use it while you are on the road. For example, our DSL connection is made through the telephone lines to our home. While at our winter vacation home, that DSL connection is not available. With a dial-in server, we use the modem in our laptop to dial home and the dial-up server connects us to the Internet (as well as our home LAN); it is like a private ISP. Not everyone will want to configure a dial-in PPP server to do this, but it does illustrate the kind of power that Linux offers a user.
You will need a second phone line (for convenience, it is not really necessary), a serial port, and an attached modem. The modem must be set to answer incoming calls using the AT commands specific to the modem you are using (consult its manual), and with the configuration saved using the AT&W modem command. A line-monitoring application such as agetty, getty, or mgetty is then used to watch the serial port by editing an entry in the system’s initialization table, /etc/inittab. You then create a special user account and script to configure Fedora Core Linux to automatically start the pppd daemon and PPP service after a user logs in.
Many modems can use a modem string such as ATE1Q0V1&C1&S0S0=1&W to auto answer calls, but this varies by modem manufacturer. Some terminal monitors, such as uugetty, have configuration files that automatically set up the modem for a particular serial port and use an entry in /etc/inittab that looks like this:
3:2345:respawn:/sbin/uugetty ttyS1 38400 vt100
This entry assumes that a modem is attached to /dev/ttyS1.
Other commands, such as agetty, can directly configure a modem port and might use an /etc/inittab entry like this:
3:2345:respawn:/usr/local/bin/agetty -w -I 'ATE0Q1&D2&C1S0=1�15' 115200 ttyS1 vt100
If you would prefer to use the mgetty command, which is included with Fedora Core, use an entry like this:
3:2345:respawn:/sbin/mgetty -a -n 1 -D ttyS1
You will also need to edit the file /etc/mgetty+sendfax/mgetty.config to set connection speeds and whether data, fax, or data-only or fax-only connections are to be allowed.
The next step is to create a user named ppp and then to assign a password to it. Although it is possible to allow remote users to log in and start pppd from the command line (assuming that you have set pppd to SUID root), the pppd daemon can be started automatically by creating a short shell script and then assigning the shell script to the user for the default shell in the user’s /etc/passwd entry, like this:
ppp:x:500:500::/home/ppp:/usr/local/bin/dopppdoppp
Made executable with chmod +x it would contain the following:
exec /usr/sbin/pppd -detach
Using this approach, pppd will start automatically after the ppp dial-in user connects and logs in (perhaps using the ppp-on scripts or other clients on the remote computer). The file options under the /etc/ppp directory should include general dial-in options for PPP service on your system, and specific options files (such as options.ttyS1 for this example) should be created for each enabled dial-in port. For example, /etc/ppp/options could contain
asyncmap 0 netmask 255.255.255.0 proxyarp lock crtscts modem
There are many approaches to providing your own PPP service. IP addresses can be assigned dynamically, or a static IP address can be doled out for a user. For example, /etc/ppp/options.ttyS1 could contain
IPofPPPserver:assignedIPofdialinuser
In this example, the first IP address is for the host computer, whereas the second IP address is assigned to the remote user. For details about configuring PPP for Linux, read the pppd man page or documentation under the /usr/share/doc/pppd* directory. If you’re a Linux developer, browse the source code files ppp_async.c, ppp_deflate.c, ppp_generic.c, and ppp_synctty.c under the /usr/src/linux-2.6/drivers/net directory.
One of the keys to security not mentioned previously is to keep up-to-date with at least the latest stable versions of your software. Each time a new version of a software package comes out, it corrects any known security holes found in the previous release. Also be sure to keep your operating systems patched to the latest patch level. Your network security is only as strong as the weakest host.
Refer to Chapter 7 for details on how to use RPM to update Fedora with newer software packages. See Chapter 39, “Kernel and Module Management,” to learn how to update your Linux kernel (even if you use RPM).
With effort, your system can be secure enough to keep most intruders out. Just keep your software up-to-date and keep yourself informed of potential security threats to your software, and you should be fine.
The following websites and books are great resources for more information on the topics covered in this chapter. Networking is complex. The more you take the time to learn, the easier setting up and maintaining your network will be.
http://fedora.redhat.com/docs—Links to additional documentation for Fedora.
http://www.ietf.org/rfc.html—Go here to search for, or get a list of, Request for Comments (RFC).
http://www.oth.net/dyndns.html—For a list of Dynamic DNS service providers, go to this site.
http://www.isc.org/products/DHCP/dhcpv3-README.html—The DHCP README is available at this site.
http://www.ieee.org—The Institute of Electrical and Electronics Engineers (IEEE) website.
http://www.mozillaquest.com/Network_02/Wireless_Network_Technology_03_Story-01.html—Wireless networking with Red Hat 7.2.
http://crl.cs.uiuc.edu/doc/wireless_redhat.html—Wireless networking using Red Hat Linux at the Computing Research Laboratory (CRL), the information technology support group for the Department of Computer Science at the University of Illinois at Urbana-Champaign.
http://www.sorgonet.com/network/wirelessnoap/—Building a wireless network without using an access point, using Red Hat 8.0.
Sams Teach Yourself TCP/IP Network Administration in 21 Days, Sams Publishing, ISBN: 0-672-31250-6
TCP/IP Network Administration, O’Reilly Publishing, ISBN: 1-56592-322-7
Practical Networking, Que Publishing, ISBN: 0-7897-2252-6
Samba Unleashed, Sams Publishing, ISBN: 0-672-31862-8
The DHCP Handbook, Sams Publishing, ISBN: 0-672-32327-3