Day 11. ACL Concepts
CCENT 100-101 ICND1 Exam Topics
![]() Describe the types, features, and applications of ACLs.
Describe the types, features, and applications of ACLs.
Key Topics
One of the most important skills a network administrator needs is mastery of access control lists (ACLs). Administrators use ACLs to stop traffic or permit only specified traffic while stopping all other traffic on their networks. Standard and extended ACLs can be used to apply a number of security features, including policy-based routing, quality of service (QoS), Network Address Translation (NAT), and Port Address Translation (PAT).
You can also configure standard and extended ACLs on router interfaces to control the type of traffic that is permitted through a given router. Today, we review ACL concepts, including what they are, how a router uses them to filter traffic, and what types of ACLs are available.
ACL Operation
A router’s default operation is to forward all packets as long as a route exists for the packet and the link is up. ACLs can be used to implement a basic level of security. They are not, however, the only security solution a large organization would want to implement. In fact, ACLs increase the latency of routers. So if the organization is very large with routers managing the traffic of hundreds or thousands of users, you more than likely will use a combination of other security implementations that are beyond the CCENT and CCNA scope.
Defining an ACL
An ACL is a router configuration script (a list of statements) that controls whether a router permits or denies packets to pass based on criteria found in the packet header. To determine whether a packet is to be permitted or denied, it is tested against the ACL statements in sequential order. When a statement matches, no more statements are evaluated. The packet is either permitted or denied. There is an implicit deny any statement at the end of the ACL. If a packet does not match any of the statements in the ACL, it is dropped.
Processing Interface ACLs
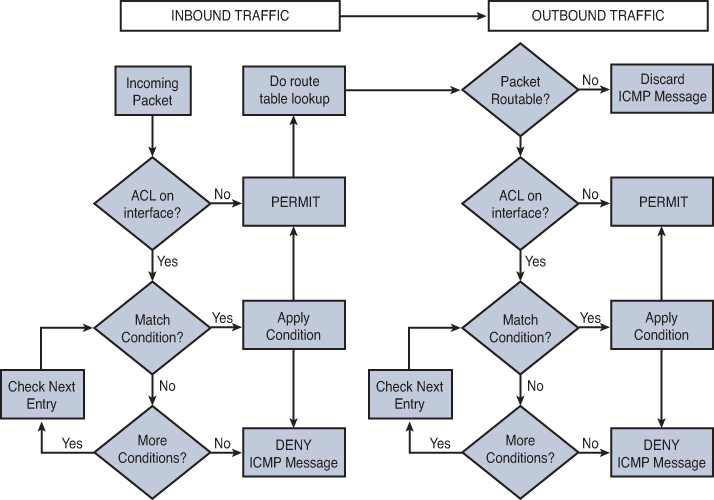
ACLs can be applied to an interface for inbound and outbound traffic. However, you need a separate ACL for each direction. The flow chart in Figure 11-1 details the steps a router takes when evaluating an ACL on inbound and outbound interfaces.
For inbound traffic, the router checks for an inbound ACL applied to the interface before doing a route table lookup. Then, for outbound traffic, the router makes sure that a route exists to the destination before checking for ACLs. Finally, if an ACL statement results in a dropped packet, the router sends an ICMP destination unreachable message.
The choice of using an inbound or outbound ACL is easy to make if first, you place yourself inside the router—be the router. From such a stance, you can visualize processing a packet coming into a router interface (inbound), making a decision on what to do with the packet (Is there an inbound ACL? Is there a route to the destination?), and forwarding the packet (What is the outbound interface? Is there an ACL on the interface?).
List Logic with IP ACLs
An ACL is a list of commands that are processed in order from the first statement in the list to the last statement. Each command has different matching logic that the router must apply to each packet when filtering is enabled. ACLs use first-match logic. After a packet matches one line in the ACL, the router takes the action listed in that line of the ACL and ignores the rest of the ACL statements.
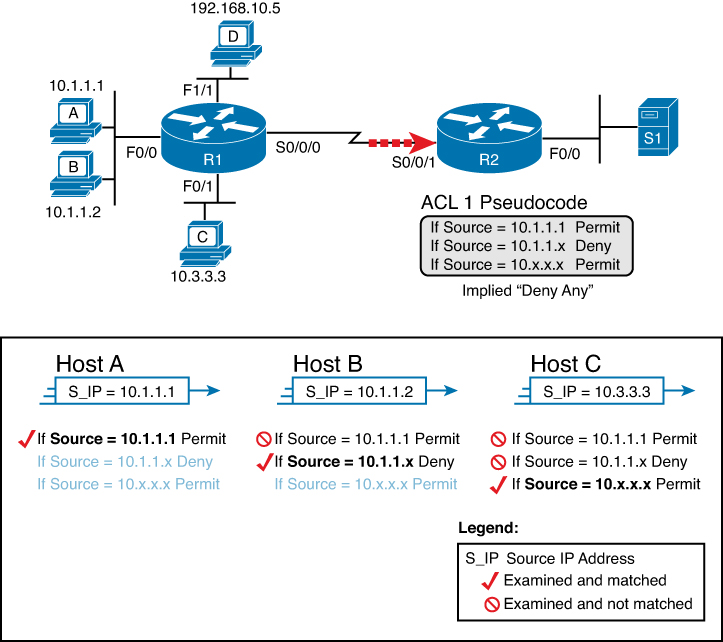
For example, Figure 11-2 shows ACL 1 with three lines of pseudocode. The ACL is applied to R2’s S0/0/1 interface, as indicated by the arrow. Inbound traffic from R1 will be filtered using ACL 1.
The box below the topology shows the logic for how packets from each host source address (labeled S_IP in the figure) is processed. Notice that after a match is made for Host A and Host B, the condition is applied (Host A is permitted and Host B is denied), and no further statements are evaluated. Host C matches the last statement in the list and is permitted.
Host D does not match any of the items in the ACL, so the packet is discarded. The reason is that every IP ACL has an implied “deny any” at the end of the ACL.
Planning to Use ACLs
Because an ACL can be used to filter traffic, it is important that you thoroughly plan the implementation of an ACL before actually configuring it.
Types of ACLs
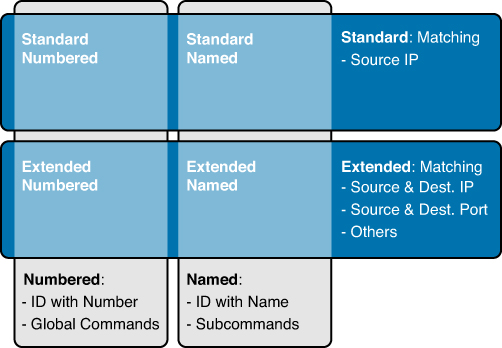
ACLs can be configured to filter any type of protocol traffic, including other network layer protocols such as AppleTalk and IPX. For the CCNA exam, we focus on IPv4 ACLs, which come in the following types:
![]() Standard ACLs: Filter traffic based on source address only
Standard ACLs: Filter traffic based on source address only
![]() Extended ACLs: Can filter traffic based on source and destination address, specific protocols, as well as source and destination TCP and UDP ports
Extended ACLs: Can filter traffic based on source and destination address, specific protocols, as well as source and destination TCP and UDP ports
You can use two methods to identify both standard and extended ACLs:
![]() Numbered ACLs: Use a number for identification
Numbered ACLs: Use a number for identification
![]() Named ACLs: Use a descriptive name or number for identification
Named ACLs: Use a descriptive name or number for identification
Although named ACLs must be used with some types of IOS configurations that are beyond the scope of the CCNA exam topics, they do provide two basic benefits:
![]() By using a descriptive name (such as BLOCK-HTTP), a network administrator can more quickly determine the purpose of an ACL. This is particularly helpful in larger networks, where a router can have many ACLs with hundreds of statements.
By using a descriptive name (such as BLOCK-HTTP), a network administrator can more quickly determine the purpose of an ACL. This is particularly helpful in larger networks, where a router can have many ACLs with hundreds of statements.
![]() Reduce the amount of typing you must do to configure each statement in a named ACL, as you will see in the section “Configuring Named ACLs” in Day 10, “Basic ACL Configuration.”
Reduce the amount of typing you must do to configure each statement in a named ACL, as you will see in the section “Configuring Named ACLs” in Day 10, “Basic ACL Configuration.”
Both numbered and named ACLs can be configured for both standard and extended ACL implementations. Figure 11-3 summarizes the categories of IPv4 ACLs.
ACL Identification
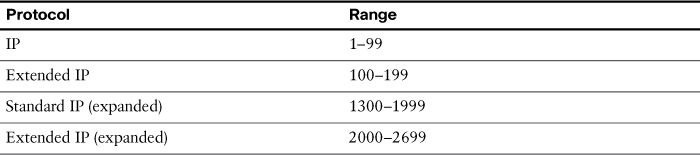
Table 11-1 lists the different ACL number ranges for the IPv4 protocol. The table is not exhaustive. Other ACL numbers are available for other types of protocols that are either rarely used or beyond CCENT and CCNA scope. IPv6 uses only named ACLs.
Named IP ACLs give you more flexibility in working with the ACL entries. In addition to using more memorable names, the other major advantage of named ACLs over numbered ACLs is that you can delete individual statements in a named IP access list.
With Cisco IOS Software Release 12.3, IP access list entry sequence numbering was introduced for both numbered and named ACLs. IP access list entry sequence numbering provides the following benefits:
![]() You can edit the order of ACL statements.
You can edit the order of ACL statements.
![]() You can remove individual statements from an ACL.
You can remove individual statements from an ACL.
![]() You can use the sequence number to insert new statements into the middle of the ACL.
You can use the sequence number to insert new statements into the middle of the ACL.
Sequence numbers are automatically added to the ACL if not entered explicitly at the time the ACL is created. No support exists for sequence numbering in software versions earlier than Cisco IOS Software Release 12.3; therefore, all the ACL additions for earlier software versions are placed at the end of the ACL.
ACL Design Guidelines
Well-designed and well-implemented ACLs add an important security component to your network. Follow these general principles to ensure that the ACLs you create have the intended results:
![]() Based on the test conditions, choose a standard or extended, numbered, or named ACL.
Based on the test conditions, choose a standard or extended, numbered, or named ACL.
![]() Only one ACL per protocol, per direction, and per interface is allowed.
Only one ACL per protocol, per direction, and per interface is allowed.
![]() Organize the ACL to enable processing from the top down. Organize your ACL so that the more specific references to a network, subnet, or host appear before ones that are more general. Place conditions that occur more frequently before conditions that occur less frequently.
Organize the ACL to enable processing from the top down. Organize your ACL so that the more specific references to a network, subnet, or host appear before ones that are more general. Place conditions that occur more frequently before conditions that occur less frequently.
![]() All ACLs contain an implicit deny any statement at the end.
All ACLs contain an implicit deny any statement at the end.
![]() Create the ACL before applying it to an interface.
Create the ACL before applying it to an interface.
![]() Depending on how you apply the ACL, the ACL filters traffic either going through the router or going to and from the router, such as traffic to or from the vty lines.
Depending on how you apply the ACL, the ACL filters traffic either going through the router or going to and from the router, such as traffic to or from the vty lines.
![]() You should typically place extended ACLs as close as possible to the source of the traffic that you want to deny. Because standard ACLs do not specify destination addresses, you must put the standard ACL as close as possible to the destination of the traffic you want to deny so that the source can reach intermediary networks.
You should typically place extended ACLs as close as possible to the source of the traffic that you want to deny. Because standard ACLs do not specify destination addresses, you must put the standard ACL as close as possible to the destination of the traffic you want to deny so that the source can reach intermediary networks.
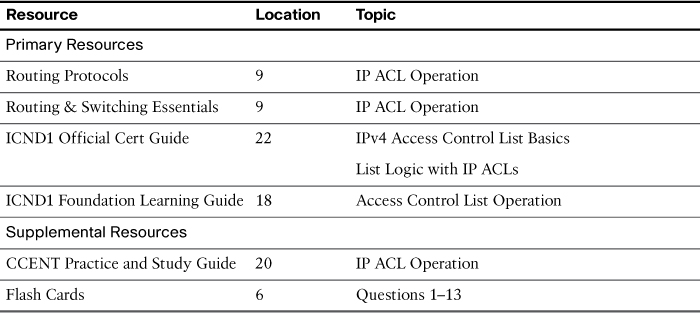
Study Resources
For today’s exam topics, refer to the following resources for more study.