Day 10. Basic ACL Configuration
CCENT 100-101 ICND1 Exam Topics
![]() Configure and verify ACLs in a network environment.
Configure and verify ACLs in a network environment.
![]() Configure and verify ACLs to filter network traffic (Basic).
Configure and verify ACLs to filter network traffic (Basic).
![]() Configure and verify ACLs to limit Telnet and SSH access to the router.
Configure and verify ACLs to limit Telnet and SSH access to the router.
Key Topics
Yesterday, we reviewed ACL concepts. Today, we focus on ACL configurations.
Configuring Standard Numbered ACLs
Standard IPv4 ACLs, which are numbered ACLs in the range of 1 to 99 and 1300 to 1999 or are named ACLs, filter packets based on a source address and mask, and they permit or deny the entire TCP/IP protocol suite. Configuring an ACL requires two steps:
Step 1. Create the ACL.
Step 2. Apply the ACL.
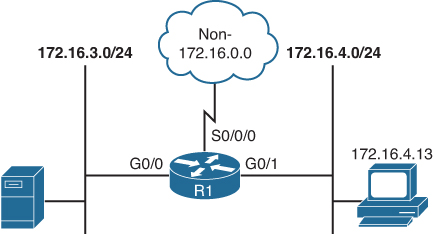
Let’s use the simple topology shown in Figure 10-1 to demonstrate how to configure both standard and extended ACLs.
Standard Numbered ACL: Permit Specific Network
Create an ACL to prevent traffic that is not part of the internal networks (172.16.0.0/16) from traveling out either of the Gigabit Ethernet interfaces.
Step 1. Create the ACL.
Use the access-list global configuration command to create an entry in a standard IPv4 ACL:
R1(config)# access-list 1 permit 172.16.0.0 0.0.255.255
The sample statement matches any address that starts with 172.16.x.x. You can use the remark option to add a description to your ACL.
Step 2. Apply the ACL.
Use the interface configuration command to select an interface to which to apply the ACL. Then use the ip access-group interface configuration command to activate the existing ACL on an interface for a specific direction (in or out):
R1(config)# interface gigabitethernet 0/0
R1(config-if)# ip access-group 1 out
R1(config-if)# interface gigabitethernet 0/1
R1(config-if)# ip access-group 1 out
This step activates the standard IPv4 ACL 1 on both the interfaces as an outbound filter.
This ACL allows only traffic from source network 172.16.0.0 to be forwarded out on G0/0 and G0/1. Traffic from networks other than 172.16.0.0 is blocked with the implied “deny any.”
Standard Numbered ACL: Deny a Specific Host
Create an ACL to prevent traffic that originates from host 172.16.4.13 from traveling out G0/0. Create and apply the ACL with the commands shown in Example 10-1.
Example 10-1 ACL Preventing Traffic Originating from a Specific Host
R1(config)# access-list 1 deny 172.16.4.13 0.0.0.0
R1(config)# access-list 1 permit 0.0.0.0 255.255.255.255
R1(config)# interface gigabitethernet 0/0
R1(config-if)# ip access-group 1 out
This ACL is designed to block traffic from a specific address, 172.16.4.13, and to allow all other traffic to be forwarded on interface G0/0. The first statement can also be written with the keyword host replacing the 0.0.0.0 wildcard mask as follows:
R1(config)# access-list 1 deny host 172.16.4.13
In fact, starting with Cisco IOS Software Release 12.3, you can enter the following:
R1(config)# access-list 1 deny 172.16.4.13
The second statement can be written with the keyword any replacing the source address 0.0.0.0 and wildcard mask 255.255.255.255 as follows:
R1(config)# access-list 1 permit any
Standard Numbered ACL: Deny a Specific Subnet
Create an ACL to prevent traffic that originates from the subnet 172.16.4.0/24 from traveling out the G0/0 interface. Create and apply the ACL with the commands shown in Example 10-2.
Example 10-2 ACL Preventing Traffic Originating from a Specific Subnet
R1(config)# access-list 1 deny 172.16.4.0 0.0.0.255
R1(config)# access-list 1 permit any
R1(config)# interface g0/0
R1(config-if)# ip access-group 1 out
This ACL is designed to block traffic from a specific subnet, 172.16.4.0, and to allow all other traffic to be forwarded out G0/0.
Standard Numbered ACL: Deny Telnet or SSH Access to the Router
For traffic into and out of the router (not through the router), filter Telnet or SSH access to the router by applying an ACL to the vty ports. Restricting vty access is primarily a technique for increasing network security and defining which addresses are allowed Telnet access to the router EXEC process. Create and apply the ACL with the commands shown in Example 10-3.
Example 10-3 Access List Allowing One Host Only Remote Access to R1
R1(config)# access-list 12 permit host 172.16.4.13
R1(config)# line vty 0 15
R1(config-line)# access-class 12 in
In this example, only host 172.16.4.13 is allowed to telnet into R1. All other IP addresses are denied implicitly.
Configuring Extended Numbered ACLs
For more precise traffic-filtering control, use extended IP ACLs, which are numbered ACLs in the range of 100–199 and 2000–2699 or are named ACLs, which check for the source and destination IP address. In addition, at the end of the extended ACL statement, you can specify the protocol and optional TCP or UDP application to filter more precisely. To configure numbered extended IPv4 ACLs on a Cisco router, create an extended IP ACL and activate that ACL on an interface. For CCENT exam purposes, the extended ACL command syntax is as follows:
Router(config)# access-list access-list-number {permit | deny} protocol source
source-wildcard [operator port] destination destination-wildcard [operator port]
[established] [log]
Table 10-1 explains the syntax of the command.
Extended Numbered ACL: Deny FTP from Subnets
For the network in Figure 10-1, create an ACL to prevent FTP traffic originating from the subnet 172.16.4.0/24 and going to the 172.16.3.0/24 subnet from traveling out G0/0. Create and apply the ACL with the commands shown in Example 10-4.
Example 10-4 Access List Preventing FTP Traffic from Specific Subnets
R1(config)# access-list 101 deny tcp 172.16.4.0 0.0.0.255 172.16.3.0 0.0.0.255 eq
21
R1(config)# access-list 101 deny tcp 172.16.4.0 0.0.0.255 172.16.3.0 0.0.0.255 eq
20
R1(config)# access-list 101 permit ip any any
R1(config)# interface g0/0
R1(config-if)# ip access-group 101 out
The deny statements block FTP traffic originating from subnet 172.16.4.0 to subnet 172.16.3.0. The permit statement allows all other IP traffic out interface G0/0. Two statements must be entered for the FTP application because port 21 is used to establish, maintain, and terminate an FTP session while port 20 is used for the actual file transfer task.
Extended Numbered ACL: Deny Only Telnet from Subnet
Create an ACL to prevent Telnet traffic that originates from the subnet 172.16.4.0/24 from traveling out interface G0/0. Create and apply the ACL with the commands shown in Example 10-5.
Example 10-5 Access List Preventing Telnet Traffic from a Specific Subnet
R1(config)# access-list 101 deny tcp 172.16.4.0 0.0.0.255 any eq 23
R1(config)# access-list 101 permit ip any any
R1(config)# interface g0/0
R1(config-if)# ip access-group 101 out
This example denies Telnet traffic from 172.16.4.0 that is being sent out interface G0/0. All other IP traffic from any other source to any destination is permitted out G0/0.
Configuring Named ACLs
The named ACL feature allows you to identify standard and extended ACLs with an alphanumeric string (name) instead of the current numeric representations.
Because you can delete individual entries with named ACLs, you can modify your ACL without having to delete and then reconfigure the entire ACL. With Cisco IOS Software Release 12.3 and later, you can insert individual entries using an appropriate sequence number.
Standard Named ACL Steps and Syntax
The following are the steps and syntax used to create a standard named ACL:
Step 1. Name the ACL.
Starting from global configuration mode, use the ip access-list standard name command to name the standard ACL. ACL names are alphanumeric and must be unique:
Router(config) ip access-list standard name
Step 2. Create the ACL.
From standard named ACL configuration mode, use permit or deny statements to specify one or more conditions for determining whether a packet is forwarded or dropped. If you do not specify a sequence number, IOS will increment the sequence number by 10 for every statement you enter:
Router(config-std-nacl)# [sequence-number] {permit | deny} source
source-wildcard [log]
Step 3. Apply the ACL.
Activate the named ACL on an interface with the ip access-group name command:
Router(config-if)# ip access-group name [in | out]
Standard Named ACL: Deny a Single Host from a Given Subnet
For the network shown previously in Figure 10-1, create a standard ACL named TROUBLEMAKER to prevent traffic that originates from the host 172.16.4.13 from traveling out interface G0/0. Create and apply the ACL with the commands shown in Example 10-6.
Example 10-6 Named ACL Preventing Traffic from a Specific Host
R1(config)# ip access-list standard TROUBLEMAKER
R1(config-std-nacl)# deny host 172.16.4.13
R1(config-std-nacl)# permit 172.16.4.0 0.0.0.255
R1(config-std-nacl)# interface e0
R1(config-if)# ip access-group troublemaker out
Extended Named ACL Steps and Syntax
The following are the steps and syntax used to create an extended named ACL:
Step 1. Name the ACL.
Starting from global configuration mode, use the ip access-list extended name command to name the extended ACL:
Router(config)# ip access-list extended name
Step 2. Create the ACL.
From extended named ACL configuration mode, use permit or deny statements to specify one or more conditions for determining whether a packet is forwarded or dropped:
Router(config-ext-nacl)# [sequence-number] {deny | permit} protocol
source source-wildcard [operator port] destination destination-wildcard
[operator port] [established] [log]
Step 3. Apply the ACL.
Activate the named ACL on an interface with the ip access-group name command:
Router(config-if)# ip access-group name [in | out]
Adding Comments to Named or Numbered ACLs
You can add comments to ACLs using the remark argument in place of the permit or deny. Remarks are descriptive statements that you can use to better understand and troubleshoot either named or numbered ACLs.
Example 10-7 shows how to add a comment to a numbered ACL.
Example 10-7 Adding Comments to a Numbered ACL
R1(config)# access-list 101 remark Permitting John to Telnet to Server
R1(config)# access-list 101 permit tcp host 172.16.4.13 host 172.16.3.10 eq telnet
Example 10-8 shows how to add a comment to a named ACL.
Example 10-8 Adding Comments to a Named ACL
R1(config)# ip access-list standard PREVENTION
R1(config-std-nacl)# remark Do not allow Jones subnet through
R1(config-std-nacl)# deny 172.16.4.0 0.0.0.255
Verifying ACLs
When you finish configuring an ACL, use show commands to verify the configuration. Use the show access-lists command to display the contents of all ACLs, as demonstrated in Example 10-9. By entering the ACL name or number as an option for this command, you can display a specific ACL.
Example 10-9 Verifying Access List Configuration
R1# show access-lists
Standard IP access list SALES
10 permit 10.3.3.1
20 permit 10.4.4.1
30 permit 10.5.5.1
40 deny 10.1.1.0, wildcard bits 0.0.0.255
50 permit any
Extended IP access list ENG
10 permit tcp host 10.22.22.1 any eq telnet (25 matches)
20 permit tcp host 10.33.33.1 any eq ftp
30 permit tcp host 10.33.33.1 any eq ftp-data
Notice in the output from the show access-lists command in Example 10-9 that sequence numbers are incremented by 10—most likely because the administrator did not enter a sequence number. Also notice that this command tells you how many times IOS has matched a packet to a statement—25 times in the case of the first statement in the named ACL ENG.
The show ip interface command displays IP interface information and indicates whether any IP ACLs are set on the interface. In the show ip interface g0/0 command output shown in Example 10-10, IP ACL 1 has been configured on the G0/0 interface as an inbound ACL. No outbound IP ACL has been configured on the G0/0 interface.
Example 10-10 Verifying Access List Configuration on a Specific Interface
R1# show ip interface g0/0
GigabitEthernet0/0 is up, line protocol is up
Internet address is 10.1.1.11/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1500 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Outgoing access list is not set
Inbound access list is 1
Proxy ARP is enabled
<output omitted>
Finally, you can also verify your ACL creation and application with the show running-config command, as shown in Example 10-11.
Example 10-11 Verifying ACL Creation and Application in the Running Configuration
R1# show running-config
Building configuration...
!
<output omitted>
!
interface GigabitEthernet0/0
ip address 10.44.44.1 255.255.255.0
ip access-group ENG out
!
<output omitted>
!
interface Serial0/0/0
ip address 172.16.2.1 255.255.255.252
ip access-group SALES in
!
<output omitted>
ip access-list standard SALES
permit 10.3.3.1
permit 10.4.4.1
permit 10.5.5.1
deny 10.1.1.0 0.0.0.255
permit any
!
ip access-list extended ENG
permit tcp host 10.22.22.1 any eq telnet
permit tcp host 10.33.33.1 any eq ftp
permit tcp host 10.33.33.1 any eq ftp-data
!
<output omitted>