To complete the steps within this recipe, we need the following:
- We need to create a VPC with public and private subnets by following the Creating a VPC in AWS and Creating subnets in VPC recipes in Chapter 5, Network Security with VPC.
- We need to add an internet gateway and configure the route table by following the Configuring an internet gateway and a route table for internet access recipe in Chapter 5, Network Security with VPC.
- We need to create a security group for our NAT instance. Inbound rules should allow HTTP and HTTPS from the CIDR range of our private subnet. We have allowed ICMP from private subnet instances so that we can ping the instance and our local IP for SSH access:
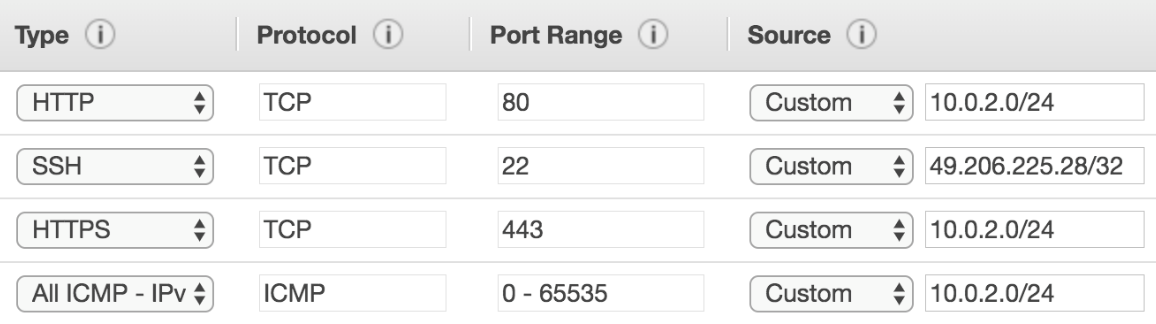
Provide outbound access to ports for HTTP, HTTPS, and ICMP, like so:

The default outbound rules for a security group allow all outbound traffic, and our NAT instances will work fine with those set of rules. However, for added security, we have only provided outbound access to the required ports.
If you have already created a route for a NAT gateway in the main route table, please remove that route and make sure the ping google.com command fails (due to lack of internet access).
