For switching role, the non-admin user should be given the AssumeRole permission for the role on the master account. Let's take a look:
- Sign in to the master account as an administrator.
- Create a policy that allows AssumeRole on the child account role, that is, OrganizationAccountAccessRole:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AssumeRoleForChildAccount",
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::380701114427:role/OrganizationAccountAccessRole"
}
]
}
Save this policy as AssumeRolePolicyChild1.
- Attach this policy to our testusergroup group.
- Sign out and sign back in as testuser user.
- Follow the steps in the previous section and enter the following details on the Switch Role screen:
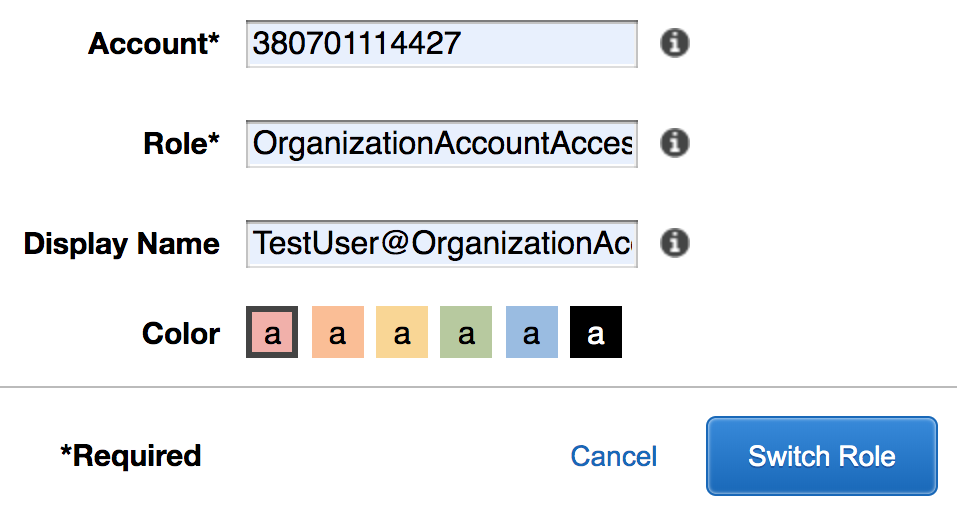
- Click on Switch Role.
This time, we should be able to switch role into the new account. We can verify this from the drop-down menu next to our account name in the taskbar:
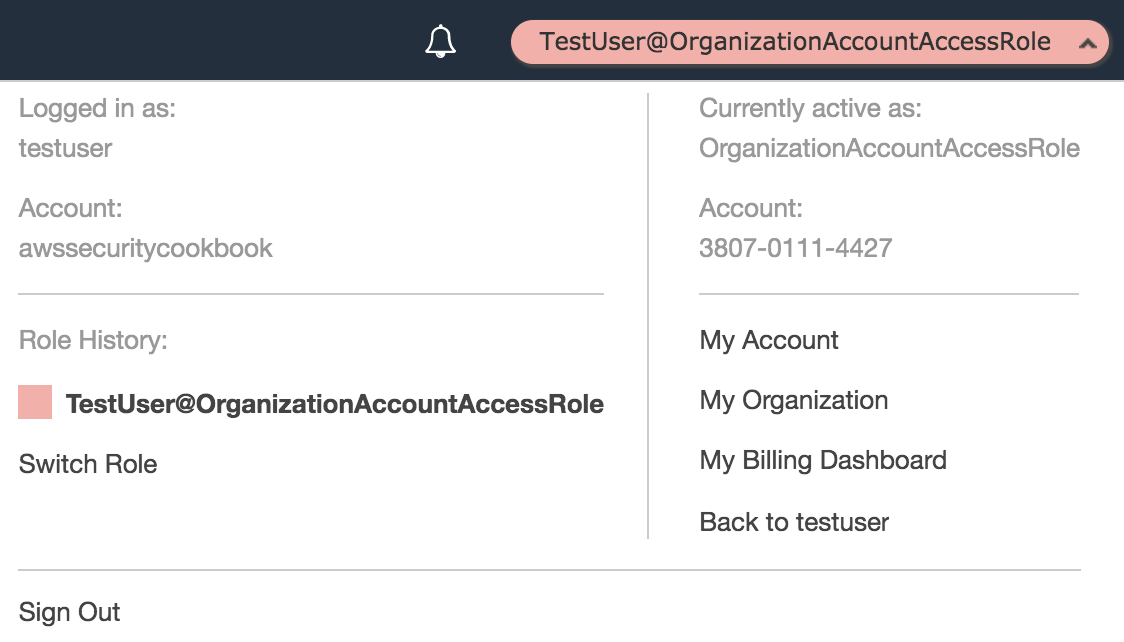
In this recipe, a user with no permission in the master account received full administrator access in the child account. In the real world, administrators will create different roles in different child accounts (for example, Dev, Testing, Prod, and so on) and then the user groups in the master account will be granted access to the respective roles in those accounts.
