CHAPTER 76
EUROPEAN GRADUATE WORK IN INFORMATION ASSURANCE AND THE BOLOGNA DECLARATION1
Urs E. Gattiker
76.1 UNDERGRADUATE AND GRADUATE EDUCATION
76.2 CONVERGENCE OF EDUCATIONAL PROGRAMS
76.3 BACHELOR'S AND MASTER'S IN INFORMATION SECURITY
76.4 COMPUTER SCIENCE: DOES IT ENCOMPASS INFORMATION SECURITY, ASSURANCE, AND SECURITY ASSURANCE?
76.5 BOLOGNA BACHELOR'S DEGREE
76.6 MOVING FROM UNDERGRADUATE TO GRADUATE EDUCATION: BOLOGNA
76.7 EXECUTIVE AND SPECIALIZED MASTER'S DEGREES
76.8 SIMILARITIES AND DIFFERENCES: ARTS AND SCIENCE
76.9 WHAT DO PROGRAMS IN INFORMATION SECURITY TEACH STUDENTS?
76.10 UNDERGRADUATE EDUCATION: POLYTECHNICS AND UNIVERSITY
76.11 INFORMATION ASSURANCE: DEFINING THE TERRITORY
76.12 TEACHING INFORMATION SECURITY: THE MALWARE EXAMPLE
76.13 CONCLUSION OF EUROPEAN INITIATIVES OVERVIEW
76.14 IMPLICATIONS FOR EDUCATION
76.15 IMPLICATIONS FOR MANAGERS
A fundamental fact in computer, information, and network security2 is the impossibility of 100 percent assurance that a computer system is trusted.3 How education can help in achieving the required level of trust considering various stakeholders (e.g., society, consumers, shareholders, and suppliers) is open to discussion. Some have suggested that certification is the answer; others support the notion that information assurance programs can fill the gap. In the latter case, advocates also hope that such programs will provide nations with the professionals required to reduce risks of possible disasters while improving security of critical infrastructure and information in particular.
This chapter focuses on undergraduate and graduate education efforts in the area of computer security in Europe. Specifically, we try to address three issues:
- How the Bologna Declaration is influencing education in information security across Europe
- What focus programs on information security currently have
- How increasing convergence could help or stifle our efforts in better protecting information and critical infrastructure
First, this chapter outlines some of the recent developments in postsecondary education set in motion by the Bologna Declaration of 1999. Next, the chapter presents and discusses the development of the educational programs fitting this new framework. Finally, key findings are summarized, explaining where these efforts might lead us regarding education and training, and we highlight practical implications.
76.1 UNDERGRADUATE AND GRADUATE EDUCATION.
The next sections outline some of the most recent developments regarding undergraduate and graduate education. Space limitations make it impossible to be complete. At this stage, it is important to point out that until quite recently, the postsecondary education system of European countries has been quite diverse and sometimes outright incomprehensible for outsiders. In turn, with globalization and the European Union expanding from 15 member states to 27, some standardization has become necessary. This standardization will result in mutual acceptance of degrees, and make it easier for people wanting to move for work across national borders. Accordingly, Europe has embarked on a journey of convergence regarding undergraduate and graduate education since the Bologna Declaration4 was signed in 1999. By the end of 2006, 45 countries had signed the Bologna accord. Although the accord is scheduled for implementation by 2010, it is unlikely that this deadline will be met. Some have suggested that having more countries and systems sign the accord, such as Asian and Pacific Rim countries, is more important than meeting the 2010 deadline.
76.2 CONVERGENCE OF EDUCATIONAL PROGRAMS.
The Bologna process has done much to move university and college education forward into a framework that is comparable across Europe. For instance, the Bologna Declaration enables both technical colleges and universities to offer undergraduate and graduate programs leading to undergraduate or graduate degrees, such as a master. The Bologna system has also resulted in countries requiring their universities to have their programs approved by accreditation agencies.
The European Commission has tried to make these programs and efforts more comparable for prospective students, employers, and policy makers by funding various projects including but not limited to Tuning Educational Structures in Europe.5 This project focuses on developing tools that help in comparing educational structures and content of studies across universities and countries. Such work is intended to facilitate the comparability of curricula in terms of structures, programs, and actual teaching (e.g., workload, hours of study per week, type of assignments, etc.).6
In theory, it is estimated that there are about 30 hours of work per unit of credit. Considering 30 units are given per semester, using the European Credit Transfer and Accumulation System (ECTS) adds up to 900 hours a semester (30 credit points × 30 hours). If a semester lasts 16 weeks, the student has about 55 hours of school work per week, on average. Considering that many hold part time jobs as well, ranging from as little as 5 hours up to 20 hours a week, the work and study week would be long and intense. In reality, however, only a few prestigious institutions will be able to attract students who pass strict admission requirements.7 Also, students submitting to such rigor and time demands will represent a relatively small group of the total undergraduate and graduate student populations.8
Much has been accomplished and many things more will be accomplished to ensure that program convergence occurs. A European Computer Education Association (ECEA) was supposed to be established with the help of funding from the European Commission. However, so far the association has been stillborn.9 Moreover, as of this writing (August, 2008), a tuning assessment of computer science programs across Europe has yet to be begun.10 The 2007 Bologna ministerial summit in London11 indicated that Europe has accomplished quite a few important milestones. More must be accomplished, however, to reach the 2010 target date for Bologna Declaration implementation in full across most of the 46 countries that signed up by May, 2007. (Several countries outside of Europe have joined and signed the declaration as well.)
76.3 BACHELOR'S AND MASTER'S IN INFORMATION SECURITY.
This section addresses how the convergence in undergraduate and graduate education might affect training and education regarding computer science and information security in particular (see also Section 76.2 and Exhibit 76.1) for greater detail.
76.4 COMPUTER SCIENCE: DOES IT ENCOMPASS INFORMATION SECURITY, ASSURANCE, AND SECURITY ASSURANCE?
The scientific discipline of computer science is sometimes called informatics in Europe and may include but not be limited to such subfields as security engineering,12 security assurance,13 and information assurance.14 In turn, acquiring a degree in security engineering might include skills, knowledge, and understanding in such areas as cryptography and access controls as well as the nuts and bolts of other protection technologies.15
Four challenges warrant special mention:
- The term “information assurance” is a relatively recent usage and definitions provided for the term vary widely.
- The term is not widely used in Europe in university or applied settings.
- Regardless of the Bologna efforts for convergence, entrance requirements at leading engineering and science schools for studying information security still differ.
- What is being taught in these programs is influenced by faculty and their particular expertise and interests.
The term “information assurance” is rarely used except in business, where the influence of globalization may have resulted in use of the term. Unlike the United States, with the Department of Homeland Security, Europe has no agency that is funding centers of excellence regarding IA or information security. Hence, the economic incentive to label a program accordingly does not exist.
The U.S. Department of Homeland Security provides a strong economic incentive with easy money for university programs or courses that accelerate the further commercialization of academia, by training in information security and related subjects. In spite of the lack of an economic incentive for universities in Europe, information security is of considerable interest to industry, policy makers, and society. As a result, ambitious curricula in these areas have sprung up. Some programs also have very specific entrance requirements. In particular, the mathematical knowledge that students entering a program must have is spelled out and generally tested.16
76.5 BOLOGNA BACHELOR'S DEGREE.
So what does the Bologna Declaration do for education at the university level in computer science and information security specifically? In short, the Bologna Declaration stipulates these requirements for the bachelor's degree:
- A bachelor-level degree is earned at an institution of higher education and requires between three and four years of full-time study, or 180 to 240 ECTS credits.
- The degree can be fulfilled at both traditional universities and at nonuniversity institutions of higher education.
- The title of each degree program should note the details (profile) and its learning outcomes and should be included in the diploma supplement issued to the student.
- Bachelor-type programs must prepare students for further study. Most important is that these programs should be freestanding and not regarded as part of a longer curriculum. This allows students to change disciplines and/or pursue graduate studies at another institution. Admission to second-cycle (graduate) degree programs requires successful completion of first-cycle (undergraduate) degrees.
Point 4 is of particular interest. It suggests, similar to North America, that the student can fulfill entrance requirements for a graduate program in information security by having acquired an unrelated undergraduate degree. It also points out that the institution can, however, demand proof of proficiency in certain areas. This could be demonstrated by having attended and attained ECTS credits in certain courses (e.g., mathematics) and by passing an exam before being allowed to register in the graduate program.
It is important to understand that to meet all graduation requirements for a bachelor's degree as part of the Bologna system, the student must have acquired 180 ECTS17 credit points; some countries may require 240 ECTS. These are obtained over a three-year or four-year period using the semester system (i.e., 30 units according to the European Credit Transfer System each semester). Unlike a North American undergraduate degree, the first year with its general distribution requirements is not part of the university education in Europe, if 180 ECTS are required for graduation. In fact, students have taken and successfully passed these types of courses during their high school program (see Exhibits 76.1 and 76.2).
EXHIBIT 76.1 Information Assurance and Security Assurance: ECTS Credit Points Programs
Today, a majority of students will continue with their master's studies right after having completed their undergraduate program. Also, the master's program attended will most likely be at the same institution where they did their undergraduate studies (e.g., Denmark, Finland, France, Germany, Italy, Slovenia and Switzerland). The Bologna system allows for two broad types of master's programs:
- Consecutive master programs offer a direct continuation from a corresponding bachelor's program (i.e., where one has specialized in computer science). Students have the option to choose specialization streams, whereby a major and minor focus can be attained. Ninety ECTS credit points are required of which about 30 ECTS are taken by a thesis project of about 6 months' duration. In total, the study program should take three semesters or 18 months. Sometimes more in-depth projects delay the student at the end so graduation requirements are met after 24 months.
- Specialized master's programs offer interdisciplinary studies, and often students have not taken an undergraduate degree in exactly the same area. In such courses, 120 ECTS credit points are required of which about 30 ECTS are taken up by a thesis project of about 6 months' duration. Usually these programs take four semesters and last about 24 months.
76.6 MOVING FROM UNDERGRADUATE TO GRADUATE EDUCATION: BOLOGNA.
Based on point 4 in Section 76.5, a bachelor's program that the student attended full time for three or four years should not be regarded as part of a longer curriculum. Hence, the student should be allowed to change disciplines and pursue graduate studies in another discipline (see also Section 76.7).
This poses a challenge for developing curriculums that deal with computer science at the graduate level and information security or information assurance in particular. Depending on a student's undergraduate degree at a university, his or her education in computer science may differ substantially. For instance, following the Bologna system, the first year of study in a bachelor-type course exposes students to material that they require for successful completion of the program. For computer science, this might include courses in mathematics and introduction to computer science. The second year may require students to take several core courses in computer science.
EXHIBIT 76.2 Information Assurance and Security Assurance: Graduate Programs

As shown in Exhibit 76.1, some computer science programs define 70 ECTS for the foundation courses in computer science; a further 20 ECTS credits must be taken in the area of mathematics and statistics.18 These are the minimum requirements.
The third year is taken up for specialization by taking courses as part of one's major (about 40 ECTS) as well as getting credit (about 10 ECTS or more) for doing an undergraduate thesis that focuses on a topic relevant to the major. Hence, after students have acquired all the basics in computer science and mathematics, they may then specialize in information security19 or cryptography.20 Naturally, specialization options, at least in part, depend upon the expertise and focus of the particular program and its staff and their research interests.
The undergraduate curriculum often entails a practical component, such as doing lab exercises (e.g., being an administrator of a Linux server and being asked to harden the server to protect it against simulated and real attacks from fellow students) as well as doing an internship at a company.
As also outlined in Exhibits 76.1 and 76.2, people who acquire a bachelor's diploma in computer science have successfully completed 140 ECTS credits in computer science, including courses in mathematics. A specialist in cryptography may have acquired 70 ECTS credits or more as well as writing a thesis on cryptography.
Students who decide to pursue a Consecutive Master's in cryptography at the University of Leuven or Aarhus will enter the program already having a good amount of knowledge in the field (i.e., at least 70 ECTS related to or directly covering cryptography). In contrast, students who take a Specialized Master in cryptography (see Exhibit 76.1) and study cryptography (i.e., likely 120 ECTS) do not have the same amount of knowledge and understanding about cryptography as those entering a Specialized Master's program in cryptography. In fact, unless the entering students bring a substantial background in mathematics, as demonstrated by having ECTS credits from undergraduate math courses and/or passing an entrance exam, the program cannot be as mathematics intensive as otherwise possible.
Put differently and as outlined in Exhibit 76.2, having 120 ECTS in cryptography or security engineering is surely different from bringing 270 ECTS to the table. In addition, programs offering courses for a Specialized Master accept students with vastly different backgrounds. This surely will not result in having a student population that is highly skilled in advanced mathematics, unless this is part of very specific prerequisites, without which students will not be accepted. Exhibit 76.2 suggests that a student may specialize in eight different types of programs of study leading to a Master in Information Security degree. Naturally, within each program, there are nuances and differences in the curriculum that affect the skills and knowledge that students will acquire. However, these go beyond the scope of this chapter.
76.7 EXECUTIVE AND SPECIALIZED MASTER'S DEGREES.
Specialized Master's degrees usually require students to complete the requirements for the degree within three years after starting the program. Most programs require full-time study. Funding requirements have resulted in quite a few executive-type master's programs being offered throughout Europe. Generally such programs (e.g., education, executive management, information security officer) require students to attend blocks of training. For instance, a block may start Wednesday night and finish late afternoon Saturday. Some parts of the program may be taught during evenings throughout the year. In addition, most of these programs charge hefty fees to allow universities to make a profit or at least recover costs, since public funding for such programs is nonexistent or very limited.
At this time, it is not possible to compare the quality of executive-type programs to specialized programs. Unless there is a calibration of some sort regarding assignments and readings, executive-type programs will always be perceived as watered-down Specialized Master's programs.
76.8 SIMILARITIES AND DIFFERENCES: ARTS AND SCIENCE.
The Bologna Declaration's greatest achievement so far has been the move toward a two-cycle structure of bachelor's and master's programs all in lieu of the traditional long program that resulted in students receiving a degree after four and a half to five years of study.
Earlier (see Exhibits 76.1 and 76.2) we pointed out that students may acquire an undergraduate degree and either enter the workforce immediately thereafter or continue toward a master's degree. Naturally, graduate study may also be undertaken after some work experience has been acquired. In most instances, students continuing with their studies right after graduation enter what is called a Continuous Masters program. This program enables students to further specialize in the discipline they majored in doing undergraduate work. Alternatively, students can choose to pursue a Specialized Master in an area different from computer science, such as business, to obtain an MBA.
Different paths in training involve different levels of complexity of the material, and of the know-how to be acquired. Moreover, lower complexity involves more procedural knowledge and skills while science requires abstract analytical thinking and declarative knowledge. Undergraduate and graduate education focuses on helping students learn and understand concepts, theories, and foundations of disciplines.
What makes things a bit more complex is that undergraduate degrees may be acquired at different types of institutions that are either more or less applied to the solution of practical problems. Exhibit 76.3 represents an educational pyramid, which separates the various stages based on complexity of the material to be learned. Procedural knowledge is acquired through learning to perform certain tasks whereby practice helps to make one better at these tasks. Declarative knowledge is defined as helping students better understand concepts and theories (the big picture).21
Exhibit 76.3 also shows that the level of complexity in the material to be covered in an educational program increases from vocational training to university-level education. Similarly, and as also outlined in Exhibit 76.2, science that addresses concepts, theories, and models needed to explain and understand phenomena is not necessarily the same as the art of hardening a UNIX box against attackers' efforts to compromise data stored in it.
As illustrated in Exhibit 76.3, a computer operator requires less declarative knowledge about computer science than does a systems administrator. The systems administrator's know-how is very much focused on the system or software he or she is required to work with. Hence, this person's procedural skills about the Microsoft Exchange server may be the basis for enabling him or her to harden that system against attacks. Most likely, this knowledge will not provide the person with the skills to be proficient enough to harden a UNIX or Linux box satisfactorily. Accordingly, skills taught in certification or vocational programs are very context and application specific. This is, of course, appropriate. After completing such training, the individual expects to be able to work with a Microsoft Exchange server, making sure the system runs smoothly and securely.
Exhibit 76.3 also indicates that a technical college or polytechnic offers programs whose primary focus is on application skills and transferability of acquired know-how from the classroom to the work setting. Most certainly, such programs also provide the student with some theoretical knowledge and concepts.
EXHIBIT 76.3 Information Security Education and Training: From Art to Science
This more applied market niche is filled by what is called a university of applied sciences in Germany or Switzerland (called Fachhochschulen), technical colleges in the United Kingdom, and polytechnics (hogeschools) in the Netherlands. Here, subjects are taught that are tailored specifically to industry.
All things being equal, one would expect that the university-type program offers the greatest amount of general-type skills about a subject, including learning about theories and models. However, under pressure to prepare a well-trained as opposed to a well-educated workforce, university education has increasingly focused on practical application-oriented curricula. In turn, the differences in some areas between an undergraduate degree from an applied university compared to a university have become smaller.
76.9 WHAT DO PROGRAMS IN INFORMATION SECURITY TEACH STUDENTS?
As mentioned, environmental pressures have moved European universities to focus more on practical, application-oriented curricula. Hence, as in Canada or Australia, students wanting to embark on a career in information security may finish their bachelor's degree and leave their institution with a backpack of skills and factual knowledge, rather than with a way of thinking that might help one excel in a profession during one's entire work life. Unfortunately, such a skills and knowledge may be quite ephemeral and ever more quickly become obsolete.22
As an academic institution, a university has two primary tasks: education and research. The latter is usually defined as the free and unconstrained pursuit of knowledge. In contrast, applied universities are usually expected to focus on research that could be considered useful by someone else, which is in most cases industry. The result is that undergraduate education, and in some cases even master's programs, can be offered by applied universities and polytechnics or technical colleges. However, the curricula of these institutions have a different focus, as outlined in Exhibit 76.4.23
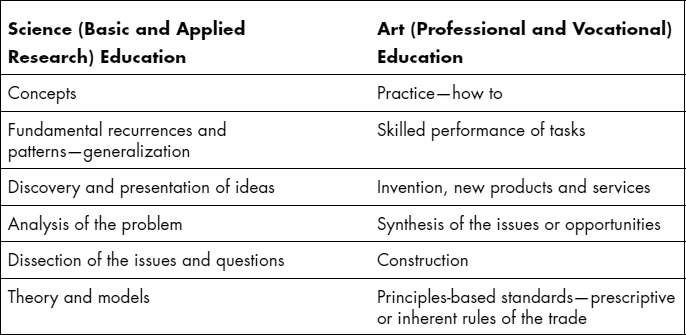
Exhibit 76.4 represents a rudimentary comparison between what could be and is most likely to be taught in a science program at a university and at more professionally focused schools (or what may be called the art of information security). The exhibit suggests that science has different activities at center stage than does art. The latter does not refer to drawings or sculptures but to the useful practices of a field, such as information security. As the right-hand column indicates, professional-type schools are likely to teach more applied skills and knowledge regarding information security that could be grouped under the art of useful practices in the field. However, as Exhibit 76.3 suggests, more applied programs teach both: applied science and the art of the profession.
EXHIBIT 76.4 Information Security and Computer Science: Between Art and Science?
At the other end of this continuum between science and art is certification. For instance, ISACA's Certified Information Systems Auditor certification focuses on training students to follow best practices in the field while providing IS auditing, control, and security services.24 There is surely no theory and science involved in this but only art, best practices, and standards.
Based on Exhibits 76.3 and Exhibit 76.4, one has to conclude that according to its mandate, education in an applied university will remain more applied than in the traditional university program. However, environmental realities have resulted in universities and polytechnics, as well as applied universities, offering some instruction about useful practices or what is called art in Exhibit 76.4.
This text presents an overview of what is happening in the educational landscape in Europe, without evaluating the programs or suggesting that either science or art in teaching information security is better than the other.
76.10 UNDERGRADUATE EDUCATION: POLYTECHNICS AND UNIVERSITY.
Until now, Polytechnics or Universities of Applied Sciences taught the more application-oriented curricula. This made sense, because in some countries, students generally received nine years of formal schooling followed by a three- to four-year apprenticeship. Apprenticeship programs are offered throughout Europe in different forms. Some require attending school for two to three days a week (or in blocks of weeks) while the rest of the time, apprentices work in an organization in the field of the trade under close supervision. In turn, the apprentices acquire a “journeyman” certificate that qualifies them to attend a university of applied sciences to study for an undergraduate degree.25
The challenge here is in choosing between university programs and applied ones that are comparable. Thanks to the Bologna Declaration, students who have a bachelor's degree must ultimately be able to attend a Continuous Master program at a university of their choice. In some countries, Continuous Master and Specialized Master programs are offered at both polytechnics and universities. However, differences will remain because, for instance, the Netherlands has decided that Hogeschools (Polytechnics) will not offer education leading to a Continuous Master's degree. The master's degree can be acquired only at a university. In other countries, polytechnics are free to offer both Continuous Master's and Specialized Master's programs.
76.11 INFORMATION ASSURANCE: DEFINING THE TERRITORY.
Computer science can be described as a systematized body of knowledge together with predictions made by researchers with who validate and test those hypotheses in various contexts. But how does this relate to information assurance?
As mentioned, information assurance is hardly if ever part of a program taught at university level in Europe. The term as such, cannot be found in most curriculum descriptions and brochures. Outsiders could, however, conclude that this is simply a matter of semantics.
We believe that the difference is more than just one of semantics. For instance, the early attempts to define IA in the European context pretty much focused on protecting information assets from threats and attacks against a country's critical infrastructure.26 In 1999, the term “information assurance” might only have implied information assurance of critical infrastructure, it is now widely accepted as such.27 A comprehensive definition of information assurance as might be used in the United States and agreed to by computer science researchers28 is not shared in Europe.
Sometimes less technically inclined individuals may feel that besides semantics, the terms “information assurance” and “security assurance” are synonymous. We do not agree. Information assurance focuses on the ability to access information and to preserve its quality and its security. Hence it centers on the threats to information and the mechanisms we can use to protect it.29
In contrast, security assurance focuses on the correctness, consistency, or completeness of the requirements and implementation of those mechanisms. It uses assurance techniques that provide justification for the mechanisms, and evidence that as implemented and operated, they do meet the security requirements as outlined in the security policy.30 Formal mechanisms may use mathematical proofs to make their case that security requirements have been met.
Security assurance is alive and thriving, albeit under different names. Nonetheless, in Europe, undergraduate education in computer science with an emphasis on information assurance may entail a few courses that serve to cover the IA component, such as CS 447 Computer Forensics, CS 448 Fault Tolerance, CS 449 Survivability, or any CS 404 approved as an IA elective.
It is not clear how these courses relate to protecting systems serving a country's critical infrastructure. In fact, in Europe, infrastructure protection likely includes both computer security and network engineering.31 In the United States, many of the centers of excellence for information security and assurance education offer master's-type programs that would be categorized as Specialized Master's program under the Bologna Declaration. In particular, looking at published entrance requirements for these centers, students attending such programs will most likely not have an undergraduate degree in computer science nor will they meet the stringent mathematics requirements that might be expected for those who enter a Continuous Master's program in information security.32
Research in the IA area indicates that skills and attributes taught in the curriculum of NSA Centers of Academic Excellence in Information Assurance Education may not have as much practical relevance as expected. A study assessing CISSP certification with what is being taught suggests that there is little if not zero association with the skills and attributes employed, or addressed, by information systems security professionals in an information systems security work environment.33
One might say that these programs are not intended to teach what might be called the plumbing trade. Instead, they are supposed to teach students to design, develop, and manage information systems that protect confidentiality, integrity, availability, and so on. Hence both programs and students must focus their attention on the threats to information and on the mechanisms we can use to protect it. In addition to IA, however, security assurance (i.e., focusing on the correctness, consistency, or completeness of the requirements and implementation of those mechanisms) is something one would expect a graduate of any of these programs to understand.
76.12 TEACHING INFORMATION SECURITY: THE MALWARE EXAMPLE.
Teaching students about malware is an area where arguments can get very heated. Undergraduate and graduate education focuses on helping students learn and understand concepts, theories, and foundations of disciplines. Malware epidemics are a clear example that not all may be up to standard regarding the correctness, consistency, or completeness of the requirements and implementation of those mechanisms. The use of code path analysis will surely help in reducing the number of vulnerabilities subject to zero-day exploits.
Training students regarding concepts and theories about malware means that instead of just focusing on how to do things right, university education also addresses how to avoid doing things wrong or what can happen if one does things wrong.
In North America, malware has entered the curriculum of computer science programs in various ways. Most famous is the recent example by the University of Calgary (U of C). There, fourth-year computer science majors meeting certain course prerequisites can apply to take a course addressing malware issues.34 The U of C announcement in summer 2003 created a stir in antivirus vendor circles. Several vendors chose to misquote material and get excited about nothing spectacular. In fact, the teaching objectives in this course are very much in line with what one would expect from an advanced undergraduate course for computer science majors35 in information security.
In reality, theory and practice are symbiotic. Business practices in the commercial world led to the development of several security policy models, such as the Clark-Wilson model. These models in turn help designers of security policies to better understand and evaluate the mechanisms and procedures required to secure their sites. Courses at university that teach virology in computer science focus on building virus-resistant systems that might help reduce the risk of new viruses spreading quickly in vulnerable systems.
The stir created because of the course taught at the U of C came as a surprise to many researchers in Europe, where teaching about virology is a common practice. For instance, most French computing science programs have a course that includes a virology component and/or require students to complete such a course.36 Naturally, these courses are taught within the strict limits of the law and neither propagate virus writing nor allow students to spread viruses. Instead, course materials and exercises try to apply scientific principles to teach students how to engineer systems that could be less vulnerable to viruses. Additionally, such teaching and research also helps students and scientists discover if accepted practices in engineering can, or should, be changed. This teaching and research latter may foster better efforts for safeguarding systems, data, and information against future attacks and new forms of malware.
Although programs carrying the label MSc in information assurance are rare if not nonexistent in Europe, education preparing individuals for work in IA is available. While the U of C experience with the antivirus course may suggest that some vendors want universities to specify their curriculum according to what they think is appropriate, universities should resist these attempts.37 In fact, we hope that in Europe and elsewhere, universities will continue to strive to teach their students higher-order learning and help advance science, theory, and practice and worry less about day-to-day issues that concern security software vendors.
76.13 CONCLUSION OF EUROPEAN INITIATIVES OVERVIEW.
Some have argued that the Bologna accord will herald unprecedented changes in higher education curricula. However, the biggest change the Bologna Declaration has brought to Europe is that it has replaced longer study for one diploma with a two-phase program. As a result, students get a bachelor's degree after three years of study and then can enter the field with a first degree if they wish. After receiving a first degree, students also have the choice to pursue further study in either a Continuous Master or a Specialized Master program.
The second big shift has been the increase in Specialized Master's degrees, which some universities perceive to be a major factor in maintaining their competitiveness in the market, partly because of growth predicted in the market for such degrees. These degrees offer students a chance to improve their knowledge and skills in a particular field. As Exhibit 76.1 illustrates, students entering these programs have a variety of backgrounds ranging from undergraduate degrees in engineering to fine arts, including possibly some work experience after receiving their bachelor's degree. This situation represents a challenge for getting all students to reach the same level of knowledge and skills.
In contrast, students entering a Continuous Master program tend to have an undergraduate degree in the same field (e.g., computing science) or a highly related one (e.g., mathematics). In the latter instance, specialization in information security may take 24 months instead of 18 months (see also Exhibit 76.2). It will be interesting to see if a Specialized Master's diploma will become the norm for chief security officers of larger corporations, or if a Continuous Master's will be preferred. Perhaps people with technical skills will acquire managerial know-how through a Specialized Master's program, such as an MBA program. This would be useful if they wanted to pursue a managerial career such as a C**-level type of executive, who might also be responsible for risk and IT security matters. The particular program that students attend will have a significant impact on their technical knowledge and on their understanding of risks, threats, programming vulnerabilities, and defenses, as well as of human resources.
Globalization has resulted in a convergence of standards,38 and the Bologna Declaration is one of the many results thereof. However, when looking at postsecondary education and information security, convergence should not result in a shift from principles-based standards to prescriptive rules.39 The same must apply for education. Hence, doing a good job in information security must surely be more than checking answers off a multiple-choice test.40 In a recent study across Europe,41 the authors pointed out that information security skills and know-how represent a moving target. The study also concluded that while training at university or technical colleges focuses on more general-type issues, the work in the certification and skills area clearly addresses vendor- and industry-specific concerns.
But not all differences will be eliminated with these efforts. For instance, it remains to be seen if the requirements of Bologna and national governments to have their university programs accredited will result in intellectually stricter criteria. Universities have already shown their adaptability to the new realities by choosing the accreditation agency that suits their needs best. A university may choose one accreditation agency over another for quite rational reasons (e.g., ISNM.de chose ZEvA over ASIIN42 for accrediting its MSc.). ASIIN requires a higher mathematical and science component in the programs it evaluates than ZEvA does. This requirement applies regardless of whether a Continuous or a Specialized Master's degree is being assessed for possible accreditation by the agency. Hence, depending on the national accreditation agency's emphasis, programs it certifies may be similar in name but definitely not in content. Different levels of mathematics required as a prerequisite do change the focus of a master's program in information security quite a bit.
76.14 IMPLICATIONS FOR EDUCATION.
When schools receive accreditation for an MSc. program, they usually broadcast their results. However, the new educational landscape also means that marketing is becoming ever more important for securing additional research funding and scholarships. Hence it is to be expected that schools will avoid pointing out their incoming students' possible weaknesses in mathematical skills but instead focus on their strengths, whatever these might be.43 However, for computer science and its subdomain of information security in particular, some basic knowledge of advanced mathematics can change the focus and depth of a postgraduate program dramatically.
Regardless of how far the Bologna Declaration will standardize university programs in the information security subdomain, vendor- and industry-specific concerns should be considered but not put center stage in education. Too much commercialization may have implications for society as well as for the profession that might not be desirable, nor would an elitist choice be the right one. However, it is clear that there are different types of education to prepare students and graduates for productive careers in information assurance or, as we prefer to call it, information security. Moreover, different types of education have different roles. Universities do not teach their students how to solve problems presented in a variety of job situations. To be ready for a journey that requires lifelong learning, students need to acquire the knowledge and understanding to see things from an original point of view.
Nonetheless, the expression “real world” hides a strong anti-intellectual bias. We have to define what an education focusing on practical application of information security in its curriculum entails. Moreover, information assurance focusing on problem solving might leave our students with piecemeal skills that become obsolete and outdated with the next version of software installed on the organization's servers.
A wonderful example of this issue is the comparison between Viruses Revealed44 (of which this author is a coauthor) and Computer Viruses: From Theory to Applications.45 The former is a practical tour de force for system administrators outlining the art of malicious code and fighting such attacks, while the second, by Filiol, is a gem as far as proofs, concepts, and theories are concerned. Naturally, without understanding some advanced mathematics to follow his case, one is lost after the first chapter if not before. Put differently, while Filiol's work does not advance a reader's quest for better using hands-on tools for protecting the server right now, it does help the reader in better understanding the issues regarding programming and malware. It especially advances comprehension of how viruses evolved and continue to evolve, including cryptoviruses.46
In conclusion, we could say that not every activity must have practical effects that are quantifiable, such as passing a multiple-choice test with 250 questions, to be able to know anything about information security (see the CISSP exam). If universities go too far in providing training that suits vendors, industry, and government, they may err too much on the side of providing students with piecemeal skills that soon become obsolete. Rapid changes in information and wireless technology pose new challenges. Moving toward ubiquitous computing in a nanotechnology environment, moreover, requires educated professionals who are curious and able to do some unorthodox thinking.
If information assurance will ever become an independent academic discipline47—which I do not feel is likely to happen in the European university setting—there must be room for work at different levels of intellectual rigor for the betterment of society.
76.15 IMPLICATIONS FOR MANAGERS.
Information assurance is an important area for training as well as for upgrading the skills of security officers. Without considering security and dependability issues, and without also understanding the development of secure and dependable applications and networks when attending IA training, graduates will be unprepared for the ever-increasing complexity they encounter at work. Accordingly, training and education must also address the managing of risks, reliability, dependability, and security of ever-more complex systems and not focus only on certification based on passing multiple-choice tests. Understanding concepts and being able to transfer them into various settings may be a better preparation for doing well as a security officer than acquiring too many tools and knowledge of facts. Put differently, while we may have standards we should follow, it does not automatically mean that the certification process through an accreditation agency is standardized. In fact, it may differ substantially across agencies, and it may be subjective, according to and reflective of, the preferences held by a team of assessors used by a particular accrediting organization.
Ideally, security and dependability should be considered together and treated seamlessly from the first stages of any system design. However, the current reality is different. The development process for information and communications systems is focused mainly on functional features. Security analysis and secure and dependable development are trailing in professionalism and investment in many areas. This undesirable trend should not be further exacerbated by training that follows the same path. Long-term objectives should not be thrown overboard in the rush to realize an immediate gain.
Education and training tend to concentrate on “how to do things right” and too seldom address “how to avoid doing things wrong.” But managers also have a tendency to focus on what certification the person has and too seldom consider whether candidates have the theoretical grounding to manage rapid change in technology.
Exhibit 76.5 provides a rudimentary checklist for managers and human resource experts to assess differences in candidates from various educational backgrounds who want to work in IT security and risk management.
As the exhibit shows, all else being equal, the more courses in mathematics that were taken in order to meet graduation requirements, the more likely a graduate will be able to handle technical issues. Also, the more ECTS credits taken in a subdiscipline such as security engineering, the greater the in-depth understanding of this area that candidates will bring a new job.
EXHIBIT 76.5 Checklist for the Recruiting Process of IT Officers
Overemphasis on certification does not make the type and depth of courses taken easier to discover, and to address in the hiring process. But certification may be a globalization trend, whereby principle-based standards that follow commonsense rules are being replaced by prescriptive rules. The latter are preferred in litigious societies, because they outline what is wrong and what is right and can, in turn, be used to take another party to court, or as a regulator to impose a fine.
As Exhibit 76.5 suggests, the Bologna model does not necessarily make the job of recruiters and human resource specialists easier. At first glance, a degree in computer science with a specialization in information security or assurance from two universities may appear similar. In actuality, it is the ingredients of each that determines their relative excellence.
76.16 NOTES
1. The author would like to thank Eric Filiol (Ecole Supérieure et d'Application des Transmissions, France) for his important suggestions and comments made on an earlier draft of this paper.
2. The term information assurance is not widely used in Europe. Instead, we use the term information security and computer science. Our rationale for this choice is explained later in this chapter.
3. By trusted we mean that the system always operates as expected by design and policy.
4. The Bologna Declaration of June 19, 1999, Joint Declaration of the European Ministers of Education (www.bologna-bergen2005.no/Docs/00-Main_doc/990719BOLOGNA_DECLARATION.PDF). In short, it focuses on four issues:
- Developing a framework that helps increase mobility for learning and teaching while strengthening collaboration across Europe
- Accepting and accrediting degrees and training across national borders
- Structuring tertiary education using two levels based on undergraduate and graduate programs whose completion results in bachelor's and master's degrees
- Introducing the European Credit Transfer System (ECTS) that allows students to transfer credits to another institution in another country
The declaration has resulted in the Bologna type of system distinguishing between graduate and undergraduate courses, thereby facilitating the comparison and mutual acceptance of degrees and certification across national boundaries.
The agreement was launched by European countries and includes states that are not members of the European Union, such as Switzerland and Norway.
5. Tuning Educational Structures in Europe: Tuning Methodology, http://tuning.unideusto.org/tuningeu/index.php?option=content&task=view&id=172&Itemid=205.
6. Tuning Educational Structures in Europe: Student Workload, Teaching Methods and Learning Outcomes: The Tuning Approach, http://tuning.unideusto.org/tuningeu/index.php?option=content&task=view&id=179.
7. Most European countries try to make postsecondary education as affordable as possible by limiting tuition and other fees. In turn, the vast majority of university programs and institutions are government funded. In some cases, private support from alumni, endowments, and third-party research funds can be considerable. For students, this means that tuition and fees may be a couple of hundred euros a semester for a local resident or EU citizen attending a public institution in Denmark. Attending the same program at a publicly funded institution in the United Kingdom may cost ¬ 1,000 or more in fees and tuition per semester. However, with the Bologna Declaration, publicly funded institutions have launched graduate programs that are supposed to be self-financing. In practice, tuition and fees are needed to finance these privately funded programs. Here, a two-year master's program may cost ¬15,000 or more in tuition and fees, excluding living expenses.
8. Students who are not used to paying much to attend university are naturally suspicious of having to pay what they perceive as exorbitant tuition fees. Once students agree to pay such fees, they will challenge the program regarding services and teaching quality. In fact, similar to executive programs, independent learning may no longer be the primary focus. However, supplying students with presentation slides and as some say “chewing out the material for them” could become the key for getting above average teaching evaluations from students. Moreover, students want good grades to land the jobs they might feel they deserve. In such circumstances, grade inflation is just around the corner. As a result, no one wants to get a grade that indicates average performance; everyone expects to receive top grades. In turn, a grade-point-average will become more difficult to interpret because market pressures may in part result in grade inflation.
9. The association ECEA was launched in fall of 2003 (see http://ecet.ecs.ru.acad.bg/ecet/Docs/ireport_2003.pdf).
10. Tuning Educational Structures in Europe: Computing Science, http://tuning.unideusto.org/tuningeu/index.php?option=content&task=view&id=14&Itemid=37.
11. Bologna Process: Towards the European Higher Education Area, www.ond.vlaanderen.be/hogeronderwijs/bologna/.
12. For a definition of the term security engineering, see Urs E. Gattiker, “CyTRAP.eu/RiskIT Labs: Getting the Security Jargon Right—Security Engineering” (2006), http://cytrap.org/RiskIT/mod/glossary/view.php?id=2&mode=entry&hook=402 (requires free registration to log in).
13. For a definition of the term security assurance, see Urs E. Gattiker, “CyTRAP.eu/RiskIT Labs: Getting the Security Jargon Right—Security Assurance” (2006), http://cytrap.org/RiskIT/mod/glossary/view.php?id=2&mode=entry&hook=398 (requires free registration to log in).
14. The term information assurance is defined by Urs E. Gattiker, “CyTRAP.eu/RiskIT Labs: Getting the Security Jargon Right—Information Assurance” (2006), http://cytrap.org/RiskIT/mod/glossary/view.php?id=2&mode=entry&hook=396 (Accessed: May 23, 2006).
15. R. Anderson, Security Engineering (Hoboken, NJ: John Wiley & Sons, 2001).
16. Most of the universities that are members of the IDEA consortium have specific prerequisites regarding math courses. In fact, students may have to pass an entrance examination if they do not appear to have the required knowledge (see http://www.idea.ethz.ch) (Accessed: May 16, 2006).
In France, a prerequisite for most programs in this area is having passed education and exams reaching a certain level of mathematics (e.g., www.supelec.fr or www.cryptis.unilim.fr/). Students must have passed a specified set of courses in mathematics during high school to enter an undergraduate program in computing science or information security. Moreover, additional courses in mathematics must be completed successfully during undergraduate education to meet the prerequisites for a Continuous Master's type of education in computing science.).
17. European Credit Transfer System (ECTS) guarantees academic recognition of studies abroad by providing a way of measuring and comparing the student's learning achievements and transferring them from one institution to another.
18. For instance, as described by the University of Aarhus's degree requirements for a bachelor's in computer science, see www.nat.au.dk/default.asp?id=9213&la=DK.
19. The description is one for computer science students who are interested in taking an undergraduate major in information security at an institute of technology; see www.maturanden.inf.ethz.ch/studium/aufbau_struktur.
20. This description is for a three-year bachelor degree in informatics with a focus on cryptographic issues.
21. U. E. Gattiker, “Computer Skills Acquisition: A Review and Future Directions for Research,” Journal of Management 18 (1992): 547–574.
22. S. Santini, “Determining Computing Science's Role,” IEEE Computer 37, No. 12 (December 2004):126&127.
23. This table borrows from U. E. Gattiker, “W21—2005—Book Review—Introduction to Computer Security,” EU IST News, May 25, 2005, http://casescontact.org/euist_view.php?newsID=3650, as well as from P. J. Denning, “Is Computer Science Science?” Communications of the ACM, 48, No. 4 (2005): 27–31.
24. A short description is provided at www.isaca-canberra.org.au/certification.
25. For instance, in Switzerland, attaining the journeyman certificate as electrician will enable the person to attend an undergraduate degree program in electrical engineering. If a person wants to do this at a university, however, he or she has to pass an entrance examination first.
26. For instance, E.A.M. Luiijf, “Information Assurance and the Information Society.” In: U.E. Gattiker, ed., EICAR Best Paper Proceedings (1999), pp. 1–17.
27. For instance, E.A.M. Luiijf, “How to Prepare for the Next Waves of Information Assurance Issues?” Paper presented at the Euro-Atlantic Symposium on Critical Information Infrastructure Assurance. 23–24 March, Riva San Vitale, Switzerland; www.cimap.vt.edu/CIIA/Papers/Session2-5-luiijf.pdf.
28. Gattiker, “CyTRAP.eu/RiskIT Labs: Getting the Security Jargon Right—Information Assurance.”
29. For instance, M. Bishop, Introduction to Computer Security (Boston: Addison-Wesley, 2005), pp. 303–316.
30. Gattiker, “CyTRAP.eu/RiskIT Labs: Getting the Security Jargon Right—Security Assurance.”
31. This is certainly the case in these programs at ENSTA (France);
32. For example, George Mason University, http://www.ise.gmu.edu/academic_info/masters/ms-isa.html.
33. A. L. Fundaburk, “The Education of Information Security Professionals: An Analysis of Industry Needs vs. Academic Curriculum in the 21st Century” (PhD diss., 2004).
34. CPSC 527—Computer Viruses and Malware (was CPSC 599.48); see: http://pages.cpsc.ucalgary.ca/~aycock/virus-info.html. The University of Calgary described the course in summer 2003 (first being taught during fall semester 2003) in this way: “Once again, the University of Calgary's department of computer science explores new territory as it becomes the first institution in Canada to offer a course in computer viruses and malware as part of its undergraduate program. This course is unique—along with covering legal, ethical and computer security issues, it will focus on developing malicious software, such as computer viruses, worms and Trojan horses, that are known to wreak havoc to the tune of billions of dollars worldwide on an annual basis.”
35. J. Aycock and K. Barker, “Viruses 101,” ACM SIGCSE Bulletin 37, No. 1 (2005): 152–155.
36. U. E. Gattiker, “Virology—Preparing Our Students for the Future,” Cytrap blog (December 2006); http://cytrap.eu/blog/?p=130.
37. During fall 2005, the University of Calgary also began teaching a course entitled CPSC 528—Spam and Spyware (was CPSC 599.63); http://pages.cpsc.ucalgary.ca/~aycock/spam-info.html.
38. For more information about this term, see: http://cytrap.org/RiskIT/mod/glossary/view.php?id=2&mode=entry&hook=391 (requires free registration to log in).
39. For more information about this term, see: http://cytrap.org/RiskIT/mod/glossary/view.php?id=2&mode=entry&hook=390 (requires free registration to log in).
40. Certified Information System Security Professional, www.isc2.org/cgi-bin/content.cgi?category=97.
41. P. Weiss, D. Dolan, W. Stucky, and P. Bumann, “ICT-Skills Certification in Europe” (2005), www.cepis.org/.
42. ASIIN is the only German accreditation agency specializing in accrediting degree programs from the fields of engineering, informatics/computer science, the natural sciences, and mathematics (www.asiin.de/english/newdesign/index-ex5.html). ZEva (Germany's first such agency) was launched by the universities of the state of Lower Saxony, with a particular focus in evaluating and accrediting programs with an international focus.
43. ISNM's Master of Science (M.Sc.) in Digital Media received international accreditation by ZevA. Evaluation team was particularly impressed by ISNM's cutting-edge research projects and unique 3 “i”—qualities put into practice on every day of a student's life: international, intercultural, interdisciplinary.” Quoted from www.isnm.de/content/exploring/msc/msc.php.
44. D. Harley, R. Slade, and U. E. Gattiker, (2001). Viruses Revealed (Berkeley, CA: Osborne/McGraw-Hill, 2001).
45. E. Filiol, Computer Viruses: From Theory to Applications (Paris: Springer Verlag, 2005).
46. U. E. Gattiker, “Trend that Matters—Malicious Cryptography—Cryptoviruses Coming Your Way—Have You Paid the Ransom Yet?” EU-Ist News, May 11, 2006; http://casescontact.org/euist_view.php?newsID=4011.
47. Merely labeling something as information assurance does not make it a striving academic discipline. Instead, it could be a label that is needed to secure funding from whatever source funds programs labeled as such.