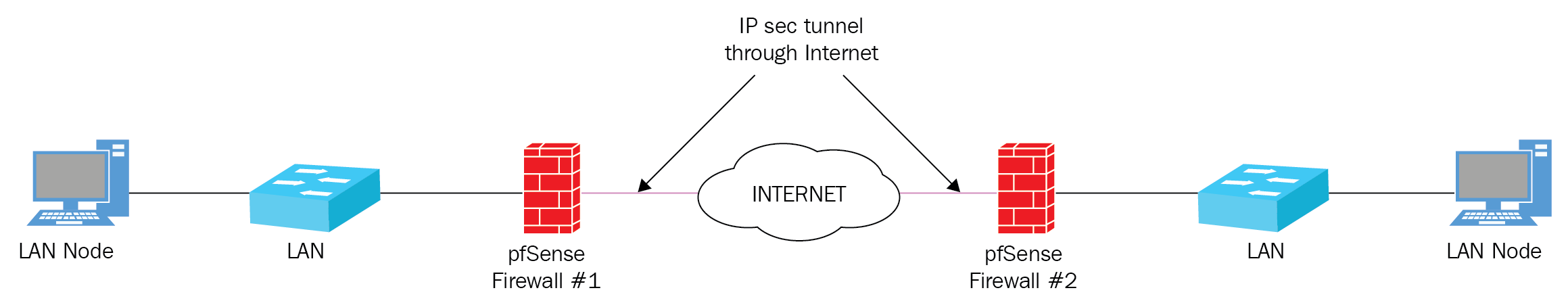
As mentioned earlier, a VPN tunnel can be peer-to-peer or client-server, and in this example, we will simulate a VPN tunnel that might be set up if we had to connect two facilities—likely run by the same company—that both have their own private networks, but are separated by a considerable distance. There are two pfSense firewalls at the boundary of each private network and the internet; therefore, the endpoint for each tunnel will be the firewall's WAN interface, and the configurations at either end will be identical. Setting up our site-to-site IPsec tunnel involves creating Phase 1 and Phase 2 entries, adding firewall rules to allow IPsec traffic, and repeating the process on the second firewall. We will begin by outlining the steps needed to create the Phase 1 and Phase 2 entries:
- Navigate to VPN | IPsec. On the default tab, click the Add P1 button.
- In the General Information section of the Edit Phase 1 page, change Key Exchange to IKEv2.
- Set Remote gateway to the IP address of the second pfSense firewall.
- Enter a brief description in the Description edit box.
- Enter a key in the Pre-Shared Key edit box.
- Set the Hash Algorithm to SHA256.
- All other values can be kept as their defaults. Click on the Save button.
- When the page reloads, click on the Show Phase 2 Entries button. In the Phase 2 section, there should be an Add P2 button. Click on this button.
- In the General Information section of the page, keep Local Network set to LAN.
- Set Remote Network to the LAN subnet and CIDR of the remote network's LAN.
- Enter a brief description in the Description edit box.
- In the Phase 2 Configuration (SA/Key Exchange) section, make sure AES256-GCM is selected as an Encryption Algorithm.
- Select SHA256 as the Hash Algorithm.
- Click on the Save button when done.
This completes the process of configuring the Phase 1 and Phase 2 entries, but we must still add a firewall rule to allow IPsec traffic. Having covered firewall rules in Chapter 6, Firewall and NAT, this should be easy:
- Navigate to Firewall | Rules and click on the IPsec tab.
- Click on one of the Add buttons at the bottom of the page to add a rule.
- On the Edit page for the rule, select Network in the Source drop-down box. Enter the subnet and CIDR of the remote network. This should be the same as the information entered for Remote Network in the Phase 2 configuration.
- All other values can be kept as their defaults. Click on the Save button.
Now, all that is left to do is to repeat the process on the second firewall:
- Navigate to VPN | IPsec on the second firewall and set up the Phase 1 configuration. The settings should be identical to the other firewall, with the exception that the Remote gateway should be set to the first pfSense firewall.
- Create the Phase 2 entry on the second firewall. Again, the settings should be identical to the settings on the first firewall, but make sure the Remote Network is set to the subnet and CIDR of the network behind the first firewall.
- Create an IPsec firewall rule on the second firewall. This should be identical to the rule created on the first firewall.
Now that we have configured IPsec, and have completed configuration on each side, we should be able to establish a connection between the firewalls. To do this, from either firewall, navigate to Status | IPsec. On the landing page, there will be a table with all available IPsec configurations; click on the Connect VPN button that corresponds to the newly-created configuration. Within seconds, the IPsec tunnel should be up. The Status column should change from Disconnected to ESTABLISHED, to reflect the current state of the tunnel. Navigate to Status | IPsec on the other firewall. The table on that page should also read ESTABLISHED in the Status column.
Now that the tunnel is established, we should be able to access resources on the LAN side of the remote connection as if they were local resources. The only limitations will be our bandwidth, latency, and the processing overhead of maintaining the tunnel.
